A Risk Analysis Under The Security Rule Is Completed By

Healthcare providers and business associates across the nation are increasingly prioritizing comprehensive risk analyses as mandated by the Security Rule of the Health Insurance Portability and Accountability Act (HIPAA). These analyses are crucial for safeguarding protected health information (PHI) in an era of escalating cyber threats. The goal is to identify vulnerabilities and implement appropriate security measures.
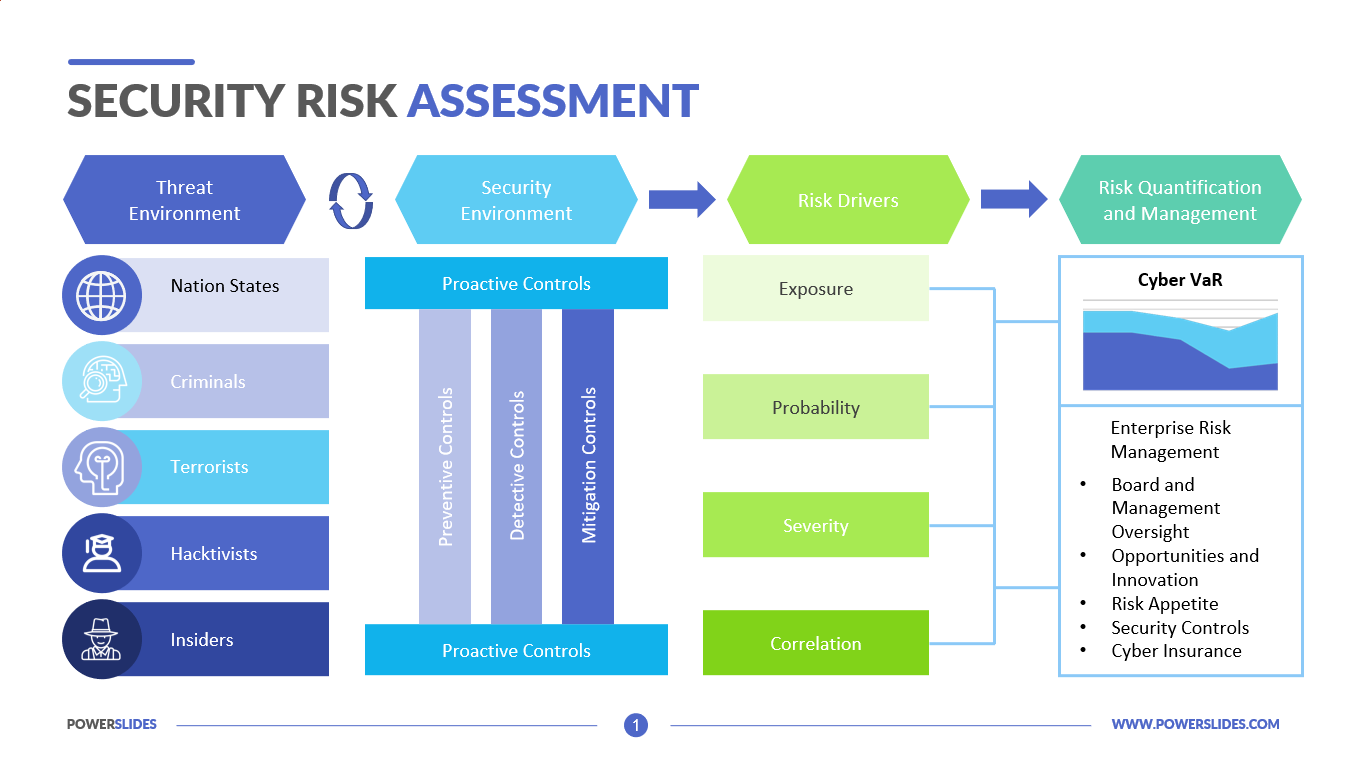
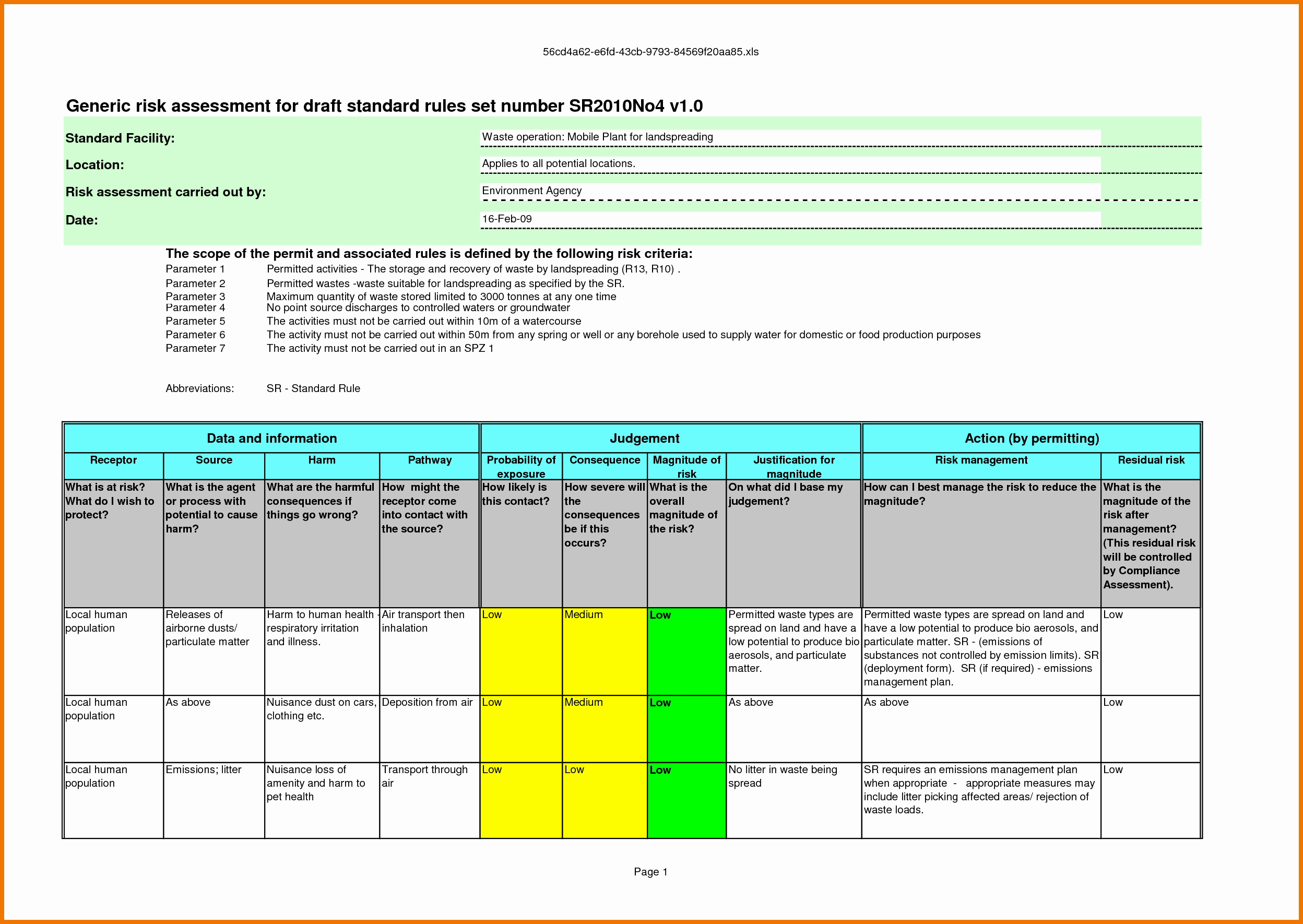
At the heart of HIPAA's Security Rule lies the requirement for covered entities and their business associates to conduct a thorough and accurate assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information (ePHI). This process, known as a risk analysis, serves as the foundation for developing and implementing a robust security management plan. Failing to perform this analysis properly can lead to significant penalties.
A risk analysis, as defined by the U.S. Department of Health and Human Services (HHS), is more than just a compliance checkbox. It is a dynamic and ongoing process. It involves a systematic evaluation of potential risks and vulnerabilities to ePHI held by an organization.
Key Components of a HIPAA Risk Analysis
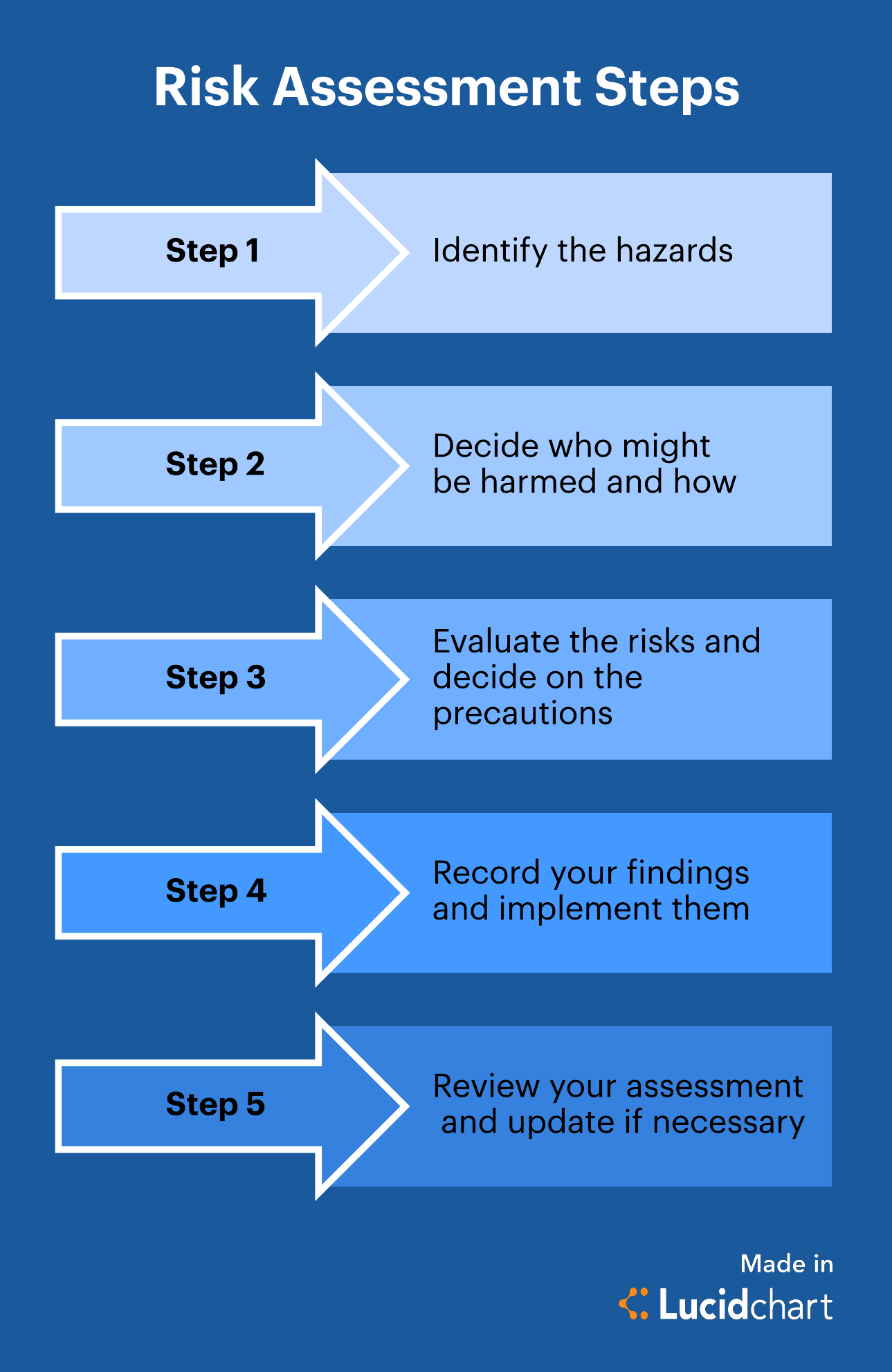
The risk analysis process typically involves several key steps, starting with identifying all potential threats and vulnerabilities. This includes assessing internal threats from employees as well as external threats like malware and hacking. Organizations must also consider physical security risks.
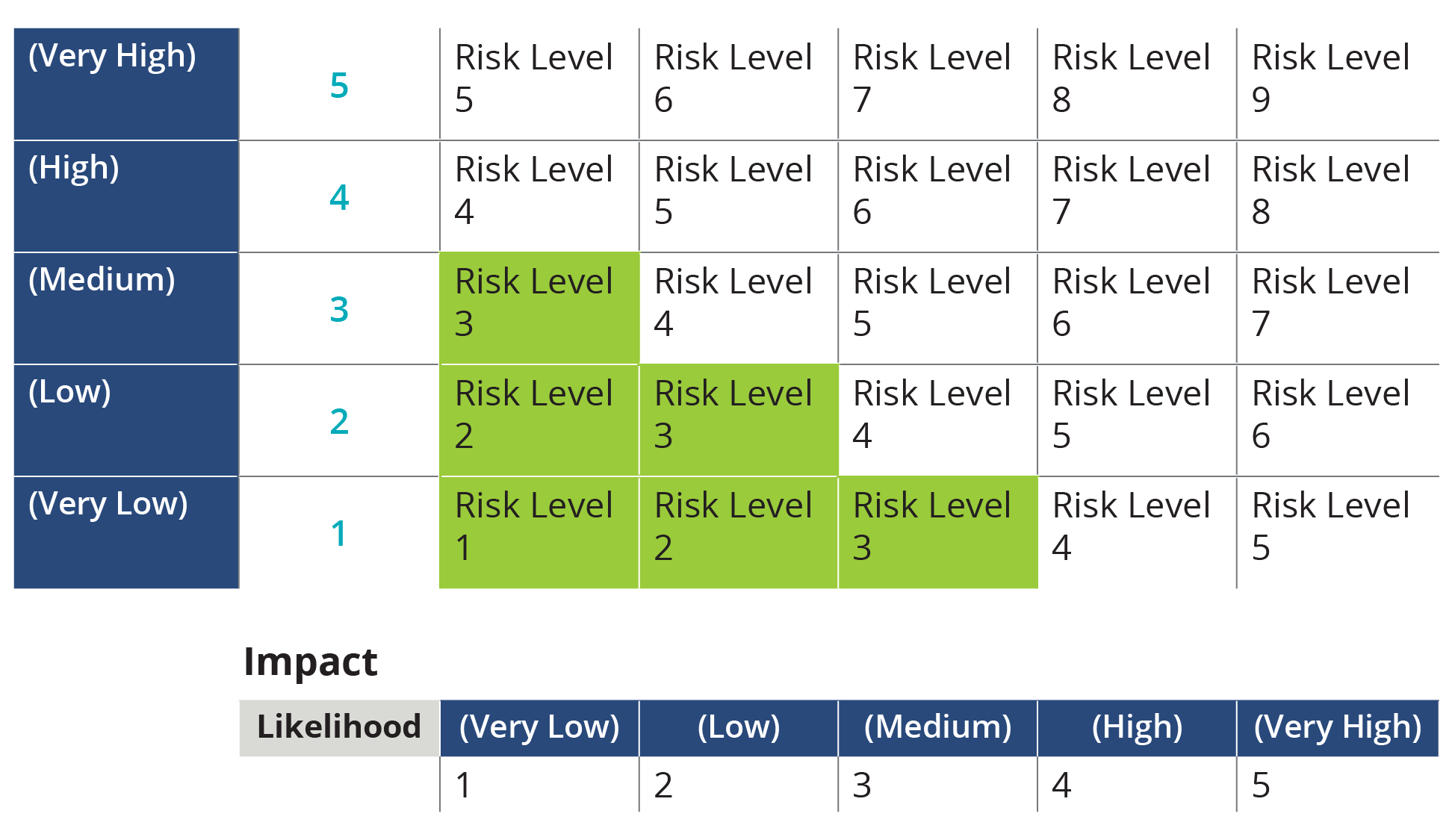
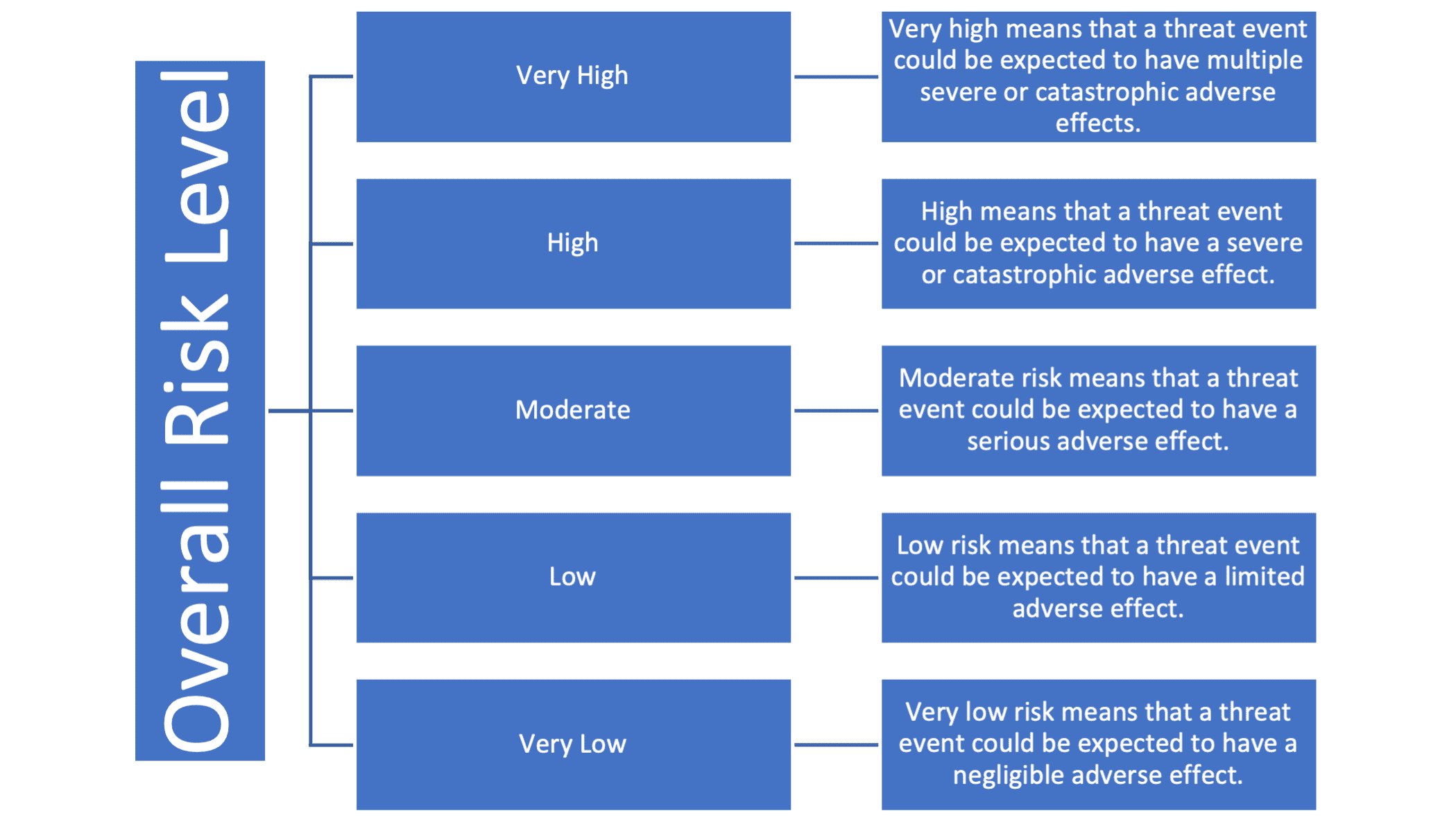
Next, the likelihood of each threat occurring and the potential impact if it were to occur are assessed. This assessment informs the prioritization of risks. The severity of potential consequences must be carefully evaluated.
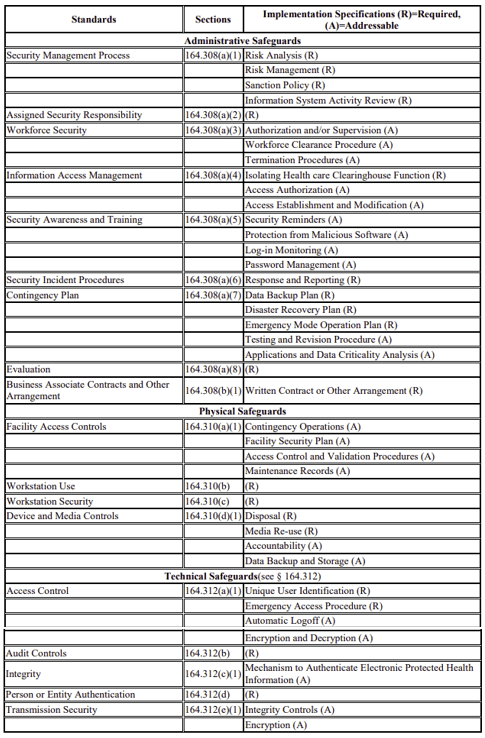
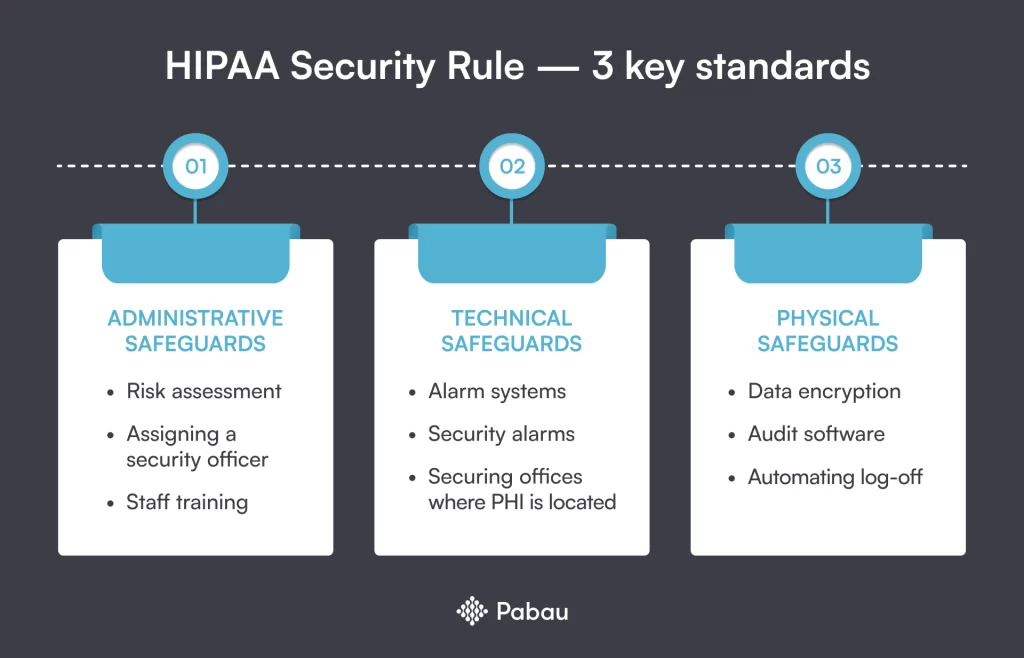
Based on the risk assessment, organizations must then develop a security plan to mitigate identified risks. This plan should include administrative, technical, and physical safeguards. Regular review and updates are critical.
Who is Responsible?
HIPAA's Security Rule applies to both covered entities and their business associates. Covered entities include healthcare providers, health plans, and healthcare clearinghouses. Business associates are entities that perform certain functions or activities on behalf of, or provide services to, covered entities that involve the use or disclosure of ePHI.
This means that even companies that simply handle data related to healthcare, like cloud storage providers or billing services, must comply. Therefore, businesses need to perform their own risk analysis.
Both parties have a legal and ethical responsibility to protect patient information. This responsibility includes protecting patient data both internally and externally.
The Significance of a Thorough Risk Analysis
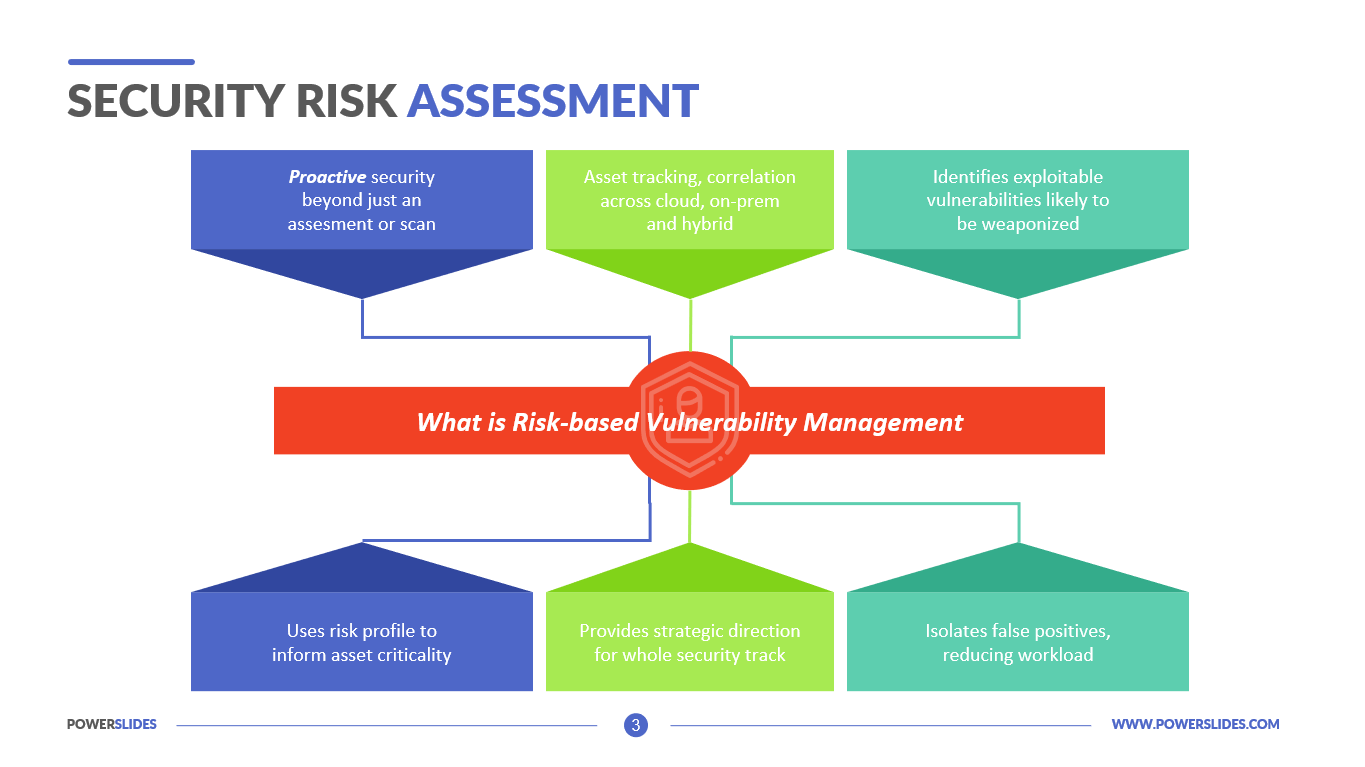
A well-executed risk analysis is not only a legal requirement but also a crucial tool for protecting patient privacy and ensuring business continuity. It allows organizations to proactively identify and address vulnerabilities before they can be exploited.
Failing to conduct a proper risk analysis can expose organizations to significant financial penalties. Furthermore, data breaches can result in reputational damage and loss of patient trust. HHS's Office for Civil Rights (OCR) actively investigates HIPAA violations.
Beyond avoiding penalties, a risk analysis helps organizations improve their overall security posture. It helps to develop a more secure and resilient infrastructure. This promotes patient confidence and streamlines processes.
Real-World Impact
Consider a small medical practice using an outdated electronic health record (EHR) system. Without a proper risk analysis, the practice may not be aware of vulnerabilities within the system. A hacker could exploit those vulnerabilities to gain access to patient records.
This could result in a data breach, leading to significant financial and reputational damage. Furthermore, patient trust can be damaged.
By conducting a thorough risk analysis, the practice could identify the vulnerabilities and implement appropriate security measures, such as updating the EHR system or implementing stronger access controls. The practice will strengthen the overall security.
Tools and Resources
Several resources are available to help organizations conduct a HIPAA risk analysis. HHS provides guidance and tools on its website. There are also various third-party software solutions available.
These tools can help streamline the process and ensure that all required elements are addressed. These tools can significantly assist organizations in meeting their responsibilities.
The National Institute of Standards and Technology (NIST) also offers frameworks and guidelines that can be used to conduct a risk analysis. Organizations can use these guidelines to conduct a risk analysis.
Conclusion
In conclusion, completing a risk analysis under the Security Rule is not merely a compliance exercise. It is a critical step in protecting patient privacy and ensuring the security of ePHI. The process includes identifying, prioritizing, and mitigating risks.
By embracing a proactive and comprehensive approach to risk analysis, healthcare providers and business associates can significantly reduce their vulnerability to cyber threats and maintain the trust of their patients.
Prioritizing risk analysis should be considered a continuous process to protect data effectively. This process should be reviewed regularly and updated in a timely manner.