Akamai Vs Cloudflare Zero Trust Comparison

In today's increasingly complex and perilous digital landscape, traditional network security models are proving woefully inadequate. Cyberattacks are becoming more sophisticated, and the perimeter-based security approach, which assumes everything inside the network is trusted, is simply no longer viable. This has driven a surge in demand for Zero Trust security solutions, which operate on the principle of "never trust, always verify."
Two of the leading providers in this rapidly evolving market are Akamai and Cloudflare. Both offer comprehensive Zero Trust platforms designed to protect organizations from a wide range of threats. Selecting the right solution requires a thorough understanding of each provider's capabilities, strengths, and weaknesses.
This article provides a detailed comparison of Akamai and Cloudflare's Zero Trust offerings, analyzing their key features, functionalities, and target audiences. It examines their approaches to identity and access management, network segmentation, threat detection, and data protection, helping businesses make informed decisions about their security posture.
Zero Trust: A Foundation for Modern Security
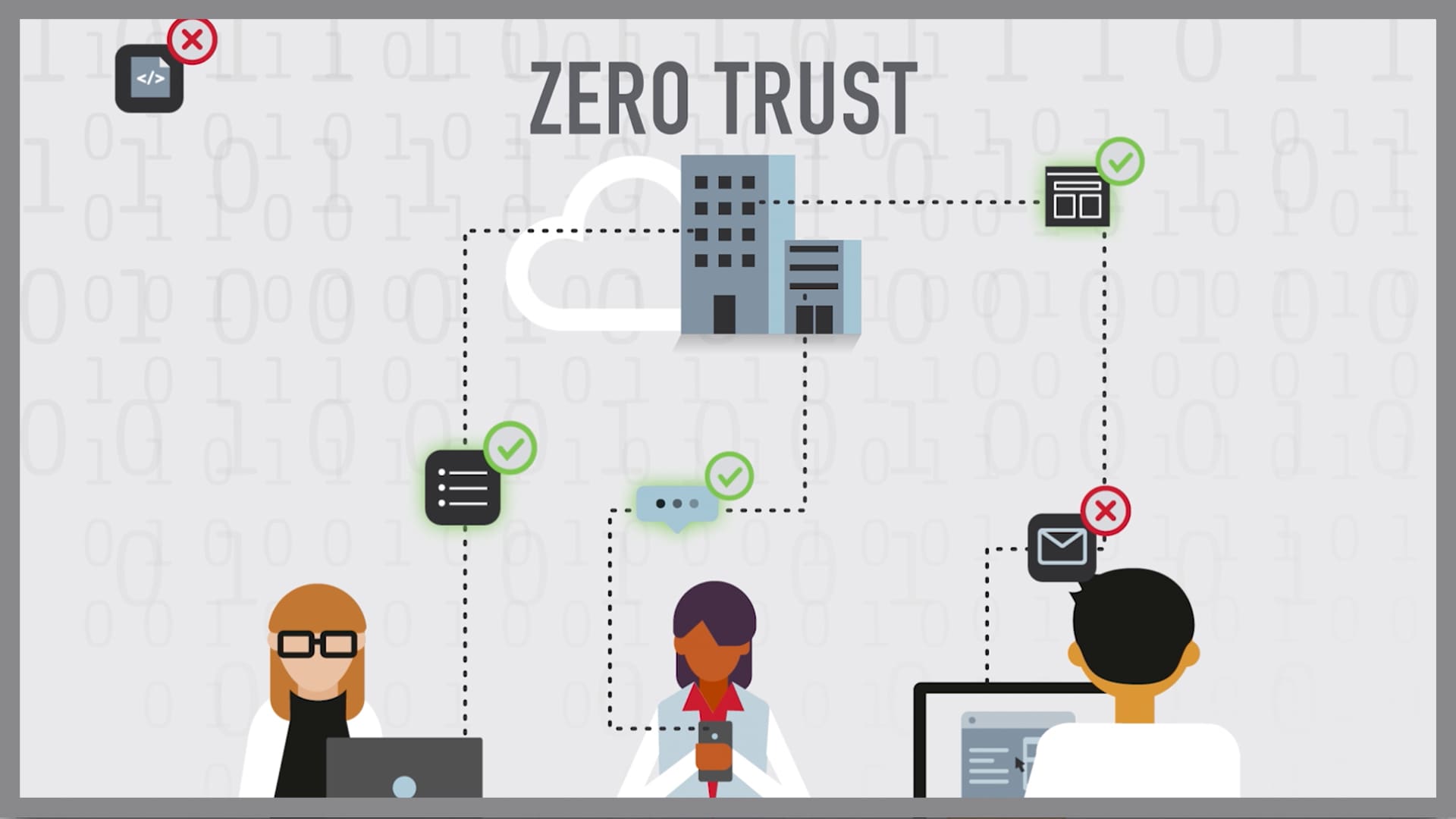
The Zero Trust model is based on the principle that no user or device should be automatically trusted, whether inside or outside the network perimeter. Every access request must be verified before being granted.
This involves continuous authentication, authorization, and validation based on factors such as user identity, device posture, location, and time of day. Zero Trust also emphasizes microsegmentation, limiting the blast radius of potential breaches by restricting lateral movement within the network.
Organizations are increasingly adopting Zero Trust to mitigate the risks associated with remote work, cloud migration, and the growing number of connected devices. It provides a more granular and adaptive approach to security, enabling businesses to protect their critical assets in a dynamic environment.
Akamai's Zero Trust Offering
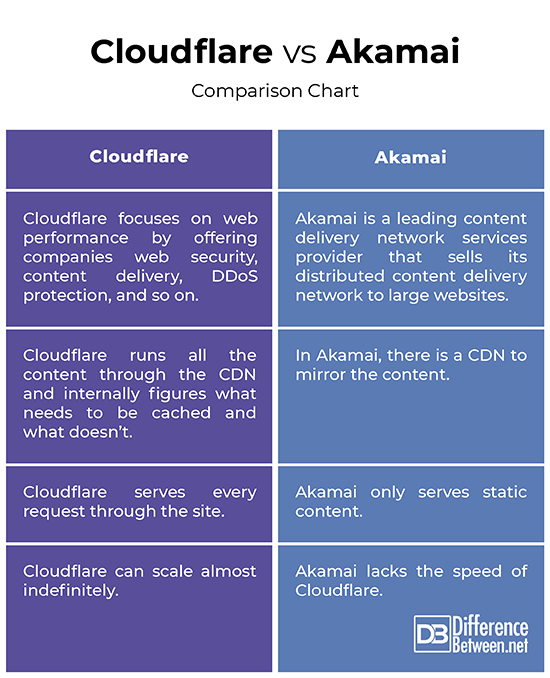
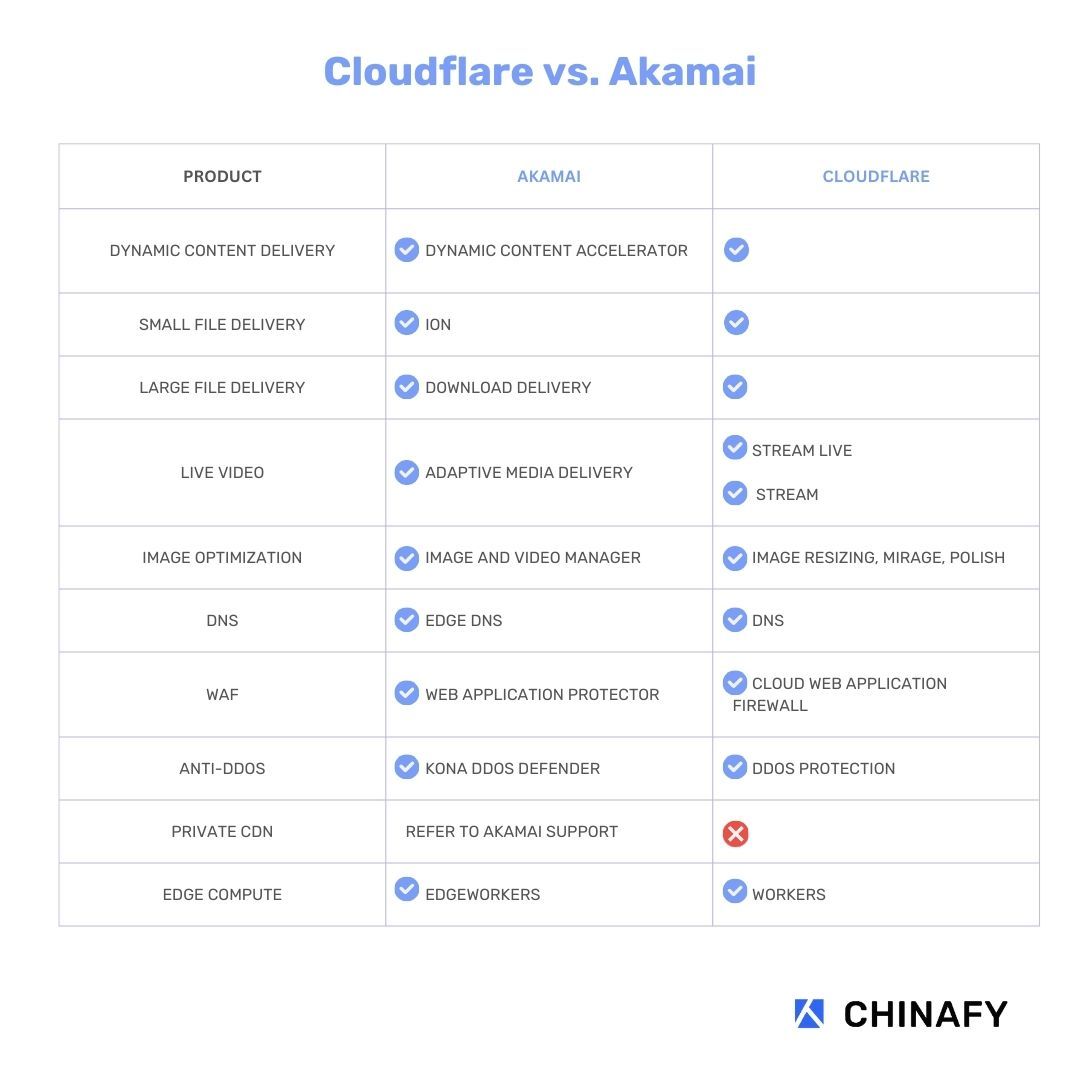
Akamai's Zero Trust platform is built upon its extensive content delivery network (CDN) and security infrastructure. It offers a suite of solutions designed to secure applications, data, and users.
Key components of Akamai's Zero Trust architecture include Akamai Enterprise Application Access (EAA), Akamai Identity Cloud, and Akamai Secure Internet Access (SIA). These solutions provide secure remote access, identity management, and web security capabilities.
Akamai EAA enables organizations to grant secure access to internal applications without the need for a traditional VPN. It uses an identity-aware proxy to authenticate users and authorize access based on defined policies.
Akamai's Strengths
Akamai's strength lies in its mature and robust platform, backed by a global network infrastructure. Its CDN capabilities enhance application performance and availability while providing advanced security features.
Akamai's focus on enterprise-grade security and scalability makes it a suitable choice for large organizations with complex IT environments. The platform integrates well with existing security tools and provides comprehensive reporting and analytics capabilities.
The Akamai Intelligent Edge Platform offers unparalleled scale and resilience, crucial for organizations facing sophisticated DDoS attacks and other volumetric threats. Akamai also has a strong track record in protecting web applications and APIs.
Akamai's Weaknesses
Akamai's Zero Trust solutions can be complex to implement and manage, requiring specialized expertise. The platform's pricing structure may be prohibitive for smaller organizations with limited budgets.
While Akamai offers a broad range of security features, its focus is primarily on web application and network security. It may require integration with third-party tools for comprehensive endpoint security and data loss prevention (DLP).
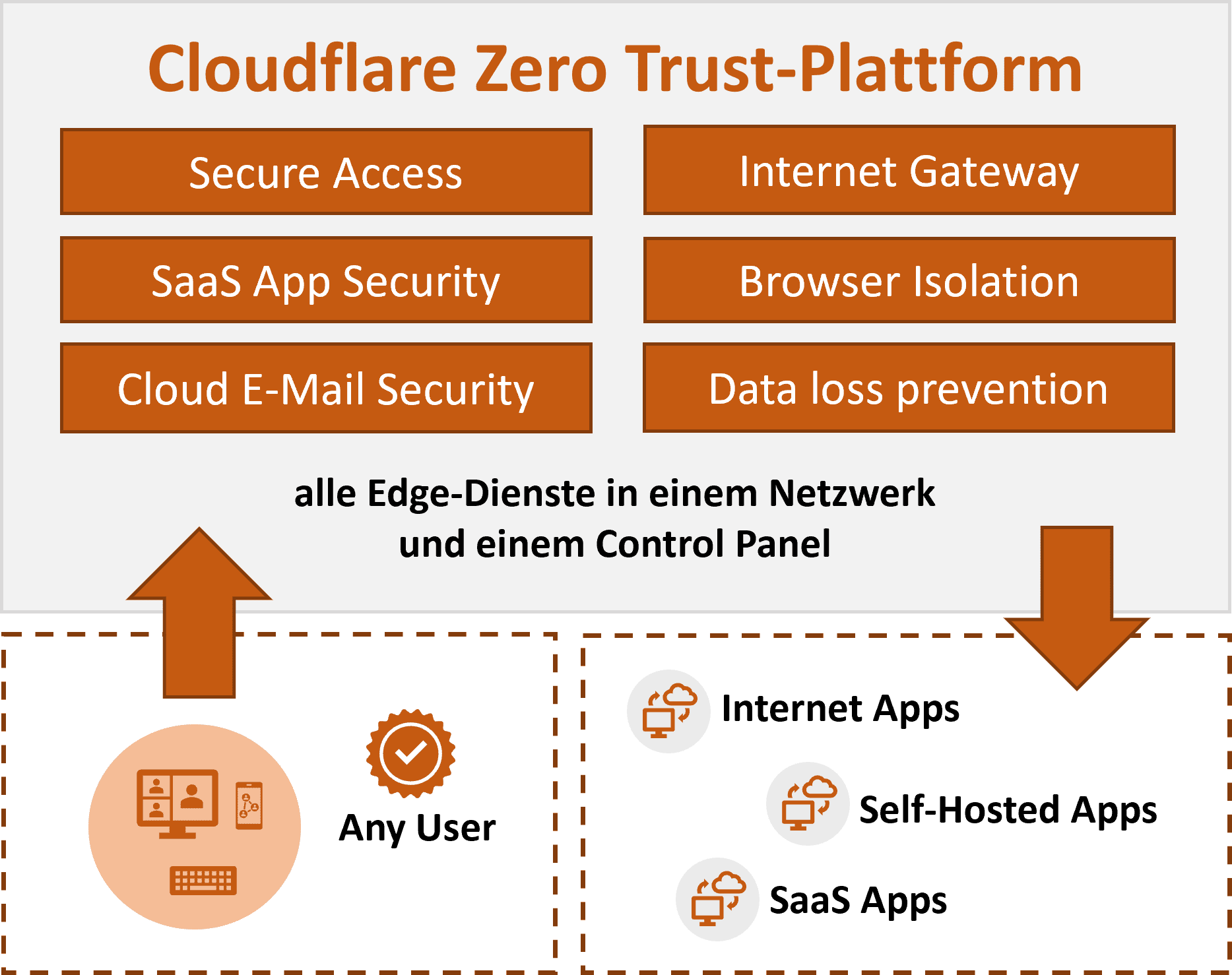
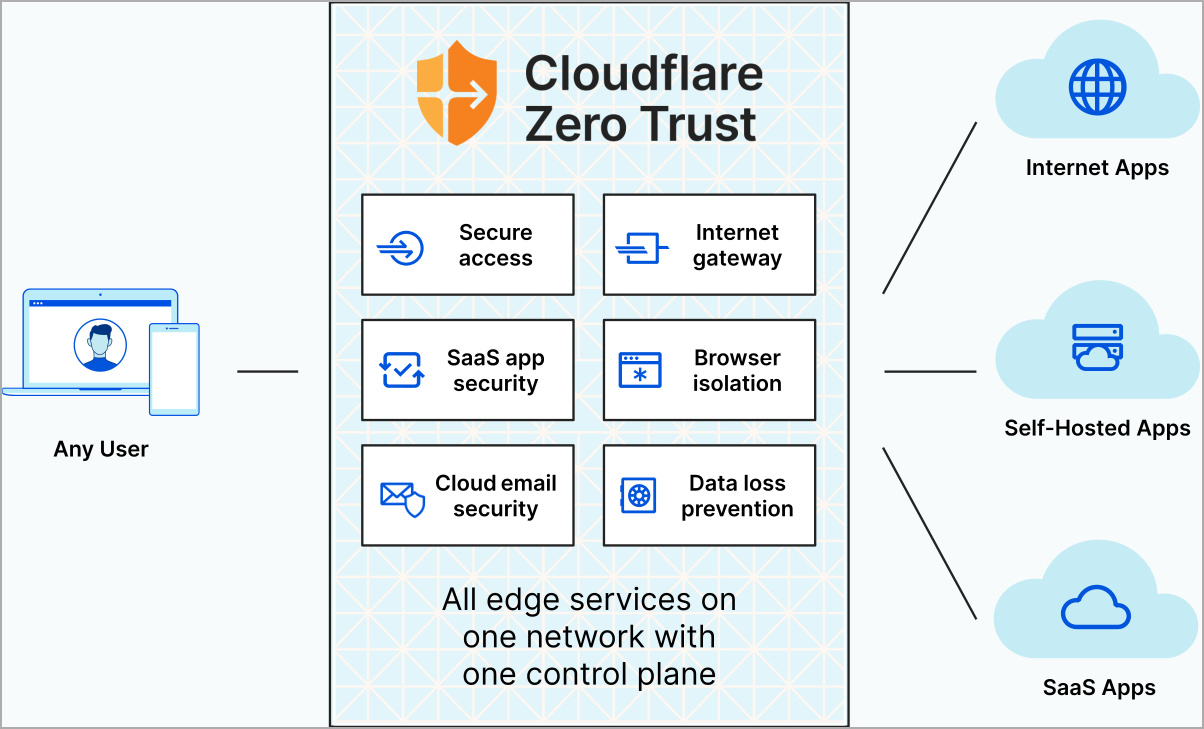
Cloudflare's Zero Trust Offering
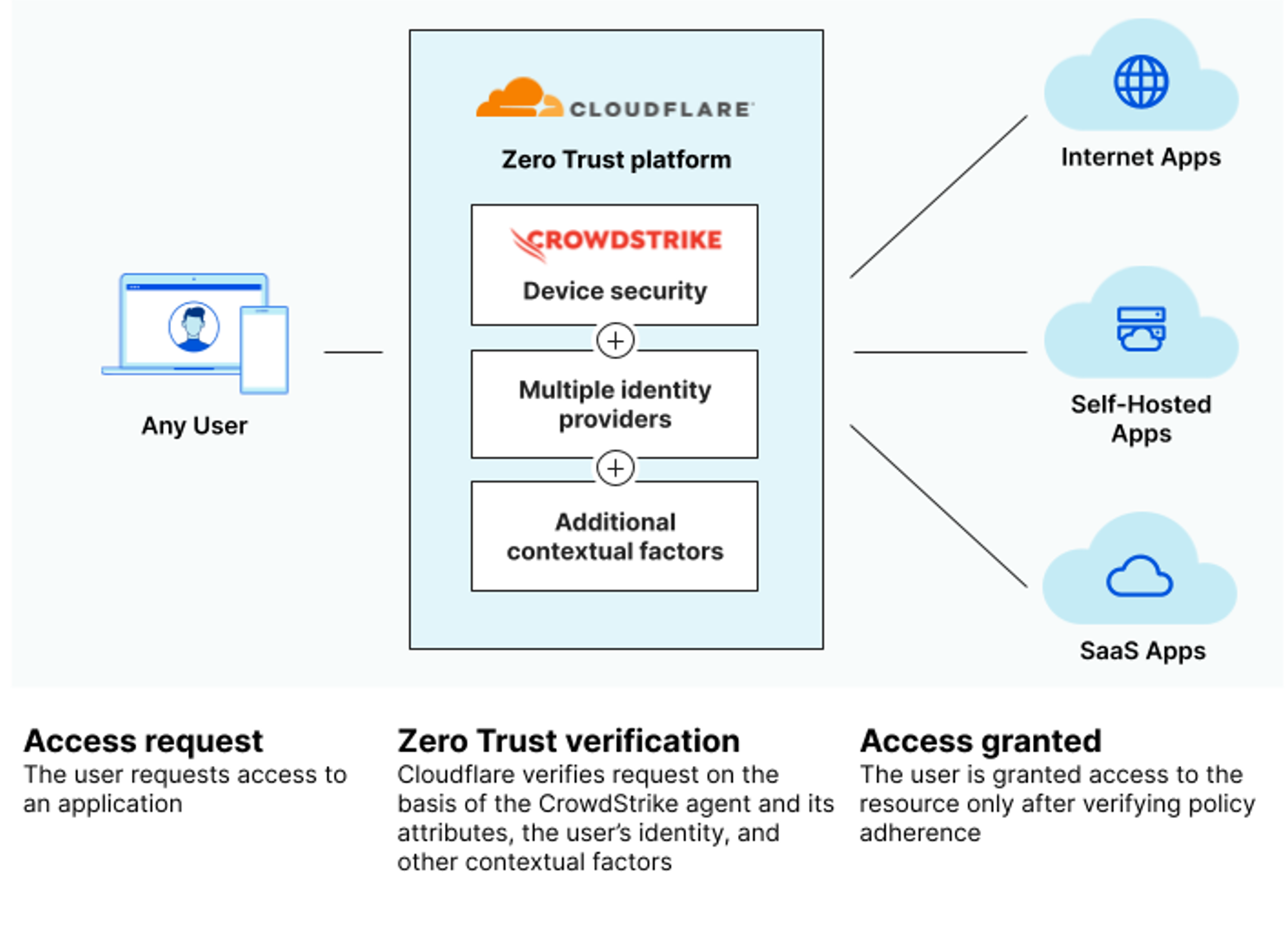
Cloudflare's Zero Trust platform is built on its global cloud network, providing a unified approach to security and performance. It offers a range of services, including secure access, threat intelligence, and data protection.
Key components of Cloudflare's Zero Trust architecture include Cloudflare Access, Cloudflare Gateway, and Cloudflare Browser Isolation. These solutions provide secure remote access, web filtering, and protection against browser-borne threats.
Cloudflare Access enables organizations to secure internal applications without the need for a VPN. It uses a variety of authentication methods, including multi-factor authentication (MFA) and single sign-on (SSO), to verify user identity.
Cloudflare's Strengths
Cloudflare's strengths include its ease of use, rapid deployment, and affordable pricing. The platform is designed to be accessible to organizations of all sizes, from small businesses to large enterprises.
Cloudflare's global network provides excellent performance and availability, while its built-in security features protect against a wide range of threats. The platform integrates seamlessly with other Cloudflare services, such as its CDN and DDoS protection.
The browser isolation feature in Cloudflare offers a unique approach to protecting against web-based attacks. It isolates web browsing activity in a remote environment, preventing malicious code from reaching the user's device.
Cloudflare's Weaknesses
While Cloudflare offers a comprehensive suite of security features, its focus is primarily on web security and network performance. It may require integration with third-party tools for more advanced endpoint security and data loss prevention (DLP) capabilities.
Cloudflare's enterprise features, while growing, may not be as mature or feature-rich as those offered by Akamai. Large organizations with complex security requirements may find Akamai to be a better fit.
Key Differences and Considerations
The choice between Akamai and Cloudflare depends on the specific needs and priorities of each organization. Akamai is generally better suited for large enterprises with complex IT environments and stringent security requirements.
Cloudflare, on the other hand, is a more accessible and affordable option for organizations of all sizes. Its ease of use and rapid deployment make it a popular choice for businesses looking to quickly improve their security posture.
When evaluating these solutions, organizations should consider factors such as their budget, IT expertise, security requirements, and performance needs. A thorough assessment of these factors will help them choose the Zero Trust platform that best meets their specific needs.
The Future of Zero Trust
The Zero Trust security model is poised to become the standard for modern cybersecurity. As organizations continue to embrace cloud computing and remote work, the need for a more granular and adaptive approach to security will only grow.
Both Akamai and Cloudflare are actively investing in their Zero Trust platforms, adding new features and functionalities to meet the evolving needs of their customers. The competition between these two leading providers will drive innovation and make Zero Trust security more accessible to organizations of all sizes.
Ultimately, the success of Zero Trust depends on widespread adoption and effective implementation. Organizations must invest in training and education to ensure that their employees understand the principles of Zero Trust and how to apply them in their daily work.