Aplicacion Para Rastrear Celular Sin Que Se Den Cuenta
The digital shadows we cast are growing ever larger, and with them, the anxieties surrounding privacy. Concerns about unauthorized access to personal information have spiked recently, fueled by the proliferation of apps promising the ability to track mobile phones without the owner's knowledge. The ethical and legal quagmire surrounding these “spy apps” is deepening, leaving individuals and institutions grappling with their implications.
At the heart of the controversy lies the promise – and the threat – of covert surveillance. These applications, often marketed as tools for parental control or employee monitoring, claim to offer the capability to track location, monitor communications, and access stored data remotely and invisibly. This article delves into the murky world of these applications, exploring their functionalities, the legal and ethical debates they ignite, and the potential consequences for both users and those being tracked.
Functionality and Accessibility
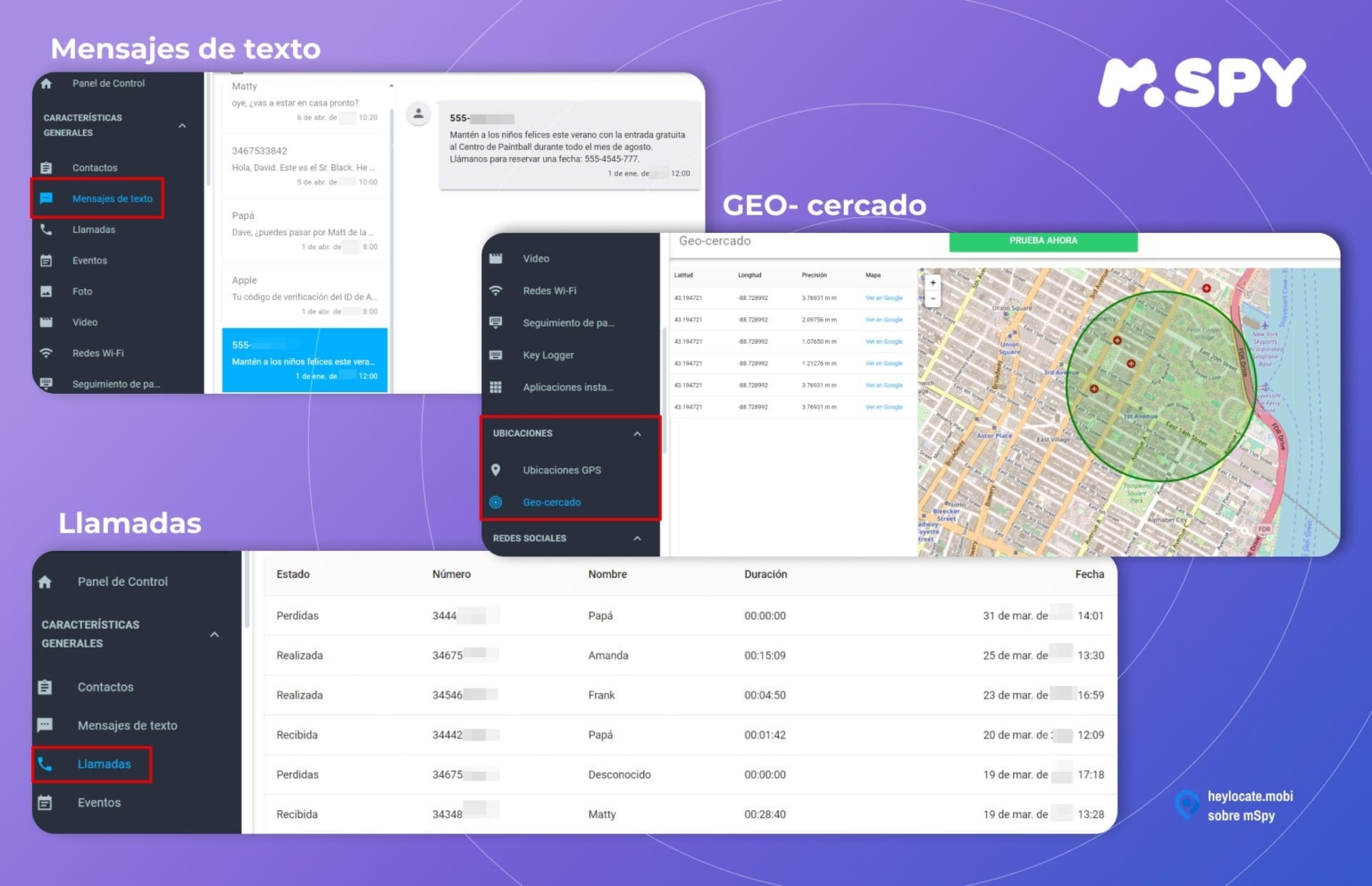
These applications generally operate by requiring installation on the target device, often masked as a routine system update or innocuous utility. Once installed, the app runs in the background, silently collecting data such as GPS location, call logs, text messages, browsing history, and even social media activity. This information is then uploaded to a secure server, accessible to the user who installed the application.
The ease with which these apps can be acquired and deployed is a significant concern. A simple online search yields a plethora of options, ranging from seemingly legitimate parental control software to outright spyware peddled on clandestine websites. Many offer subscription-based models, lowering the barrier to entry and making sophisticated surveillance tools readily available to a wider audience.
Legal and Ethical Implications
The legal landscape surrounding these applications is complex and varies significantly across jurisdictions. In many countries, installing such software on a device without the owner's explicit consent is a violation of privacy laws, potentially leading to criminal charges. The Electronic Communications Privacy Act (ECPA) in the United States, for example, prohibits the interception of electronic communications without proper authorization.
Beyond legal considerations, the ethical ramifications are profound. The surreptitious nature of these applications erodes trust, potentially damaging relationships between parents and children, employers and employees, and even intimate partners. The constant threat of being monitored can create an atmosphere of fear and anxiety, undermining personal autonomy and freedom.
Perspectives on Usage
Proponents of these applications often frame their use as a necessary measure for protecting vulnerable individuals. Parents may argue that monitoring their children's online activity is essential for safeguarding them from online predators or cyberbullying. Employers might claim that tracking employee communications is necessary to prevent data leaks or ensure productivity.
However, critics argue that such justifications often mask a desire for control and dominance. The lack of transparency inherent in covert surveillance undermines the very principles of trust and respect that are essential for healthy relationships. Furthermore, the data collected by these applications can be easily misused, leading to blackmail, harassment, or even identity theft.
Countermeasures and Prevention
Detecting these applications can be challenging, as they are designed to operate stealthily. However, there are certain telltale signs that a device may be compromised, such as unexplained battery drain, unusual data usage, or the presence of unfamiliar applications. Regular security audits and the use of reputable antivirus software can help mitigate the risk.
Education is also crucial. Users should be aware of the potential risks associated with these applications and take steps to protect their devices from unauthorized access. This includes setting strong passwords, being cautious about clicking on suspicious links, and regularly updating software to patch security vulnerabilities. The Federal Trade Commission (FTC) offers resources and guidance on protecting personal information online.
Moving Forward
The debate surrounding applications designed to track mobile phones without consent is unlikely to subside anytime soon. As technology continues to evolve, so too will the tools and techniques used for surveillance. The key lies in fostering a culture of transparency and respect for privacy. Lawmakers, tech companies, and individuals all have a role to play in ensuring that technology is used responsibly and ethically.
Ultimately, the effectiveness of any countermeasures depends on a collective commitment to safeguarding privacy. This requires not only technological solutions but also a fundamental shift in mindset, one that prioritizes trust, transparency, and respect for individual autonomy over the allure of control and surveillance. The future of privacy hinges on our ability to navigate this complex landscape with wisdom and foresight.