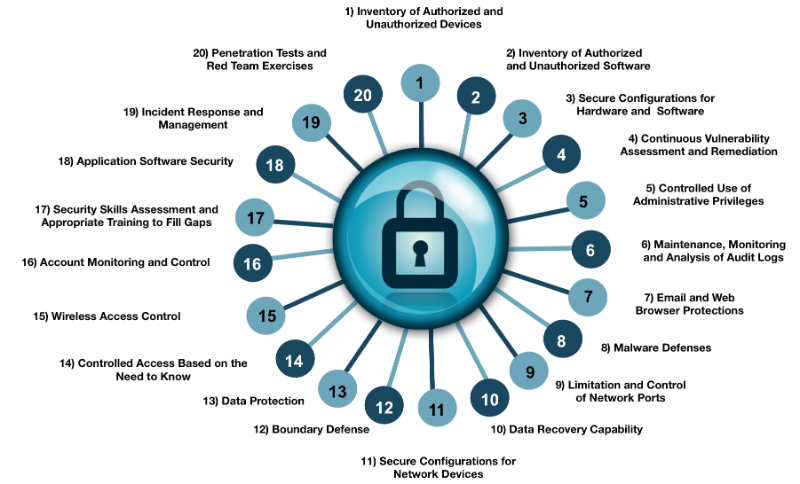
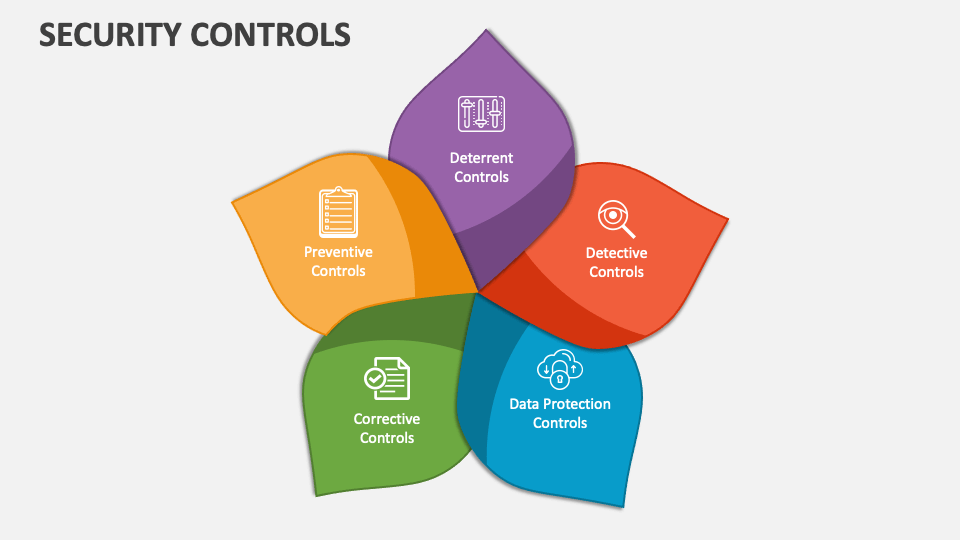
Computer Safety Control Settings Are Most Often Used To
Urgent warnings are being issued as new data reveals computer safety control settings are most frequently employed to manage screen time, eclipsing concerns about online security and data privacy.
This alarming trend underscores a significant disconnect between perceived threats and actual user behavior, leaving individuals vulnerable to sophisticated cyberattacks and data breaches. The focus on time management, while valid, overshadows critical security measures necessary for navigating today's digital landscape safely.
Dominant Use Case: Screen Time Management
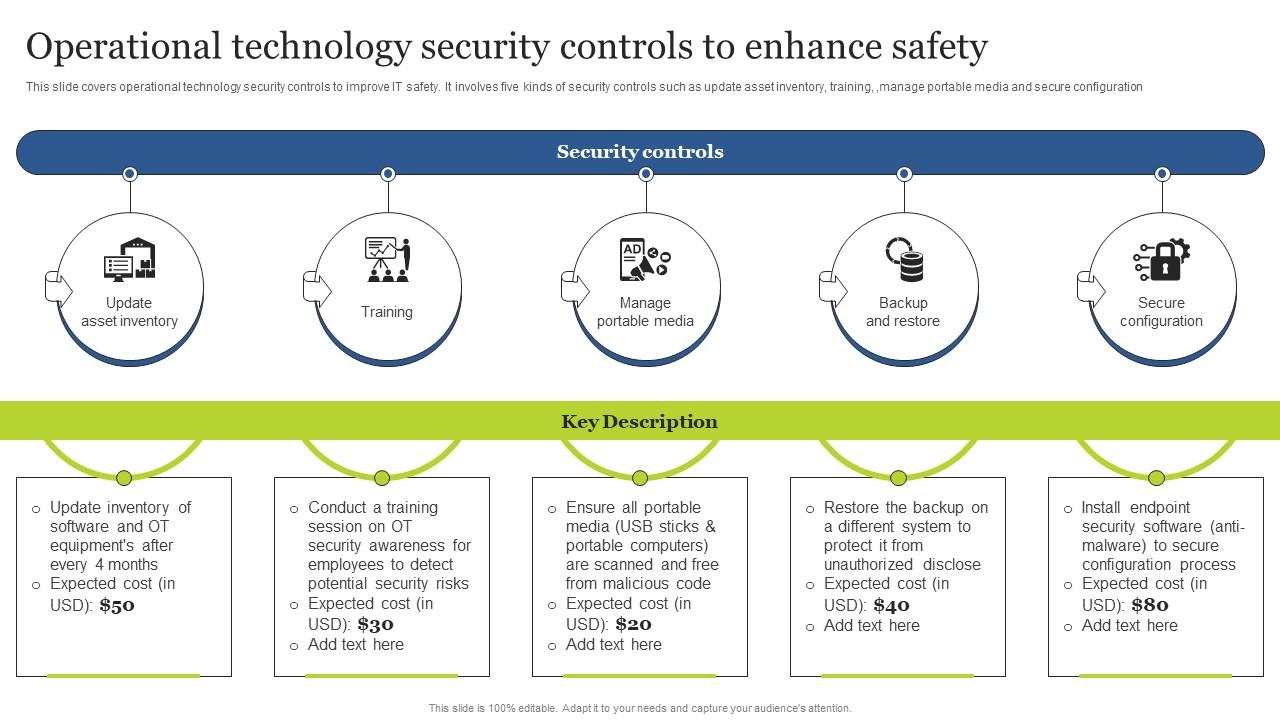
Recent data analysis from Cybersecurity Insights Group (CIG) indicates that approximately 68% of users who engage with computer safety control settings primarily use them for setting time limits and monitoring device usage. This figure represents a substantial lead over other functionalities, such as blocking malicious websites or restricting access to specific applications.
The findings, compiled from a survey of over 10,000 computer users across various demographics, highlight a concerning prioritization of digital well-being over active cybersecurity defense. This imbalance creates a significant risk profile, particularly for individuals and organizations handling sensitive data.
The Neglected Security Settings
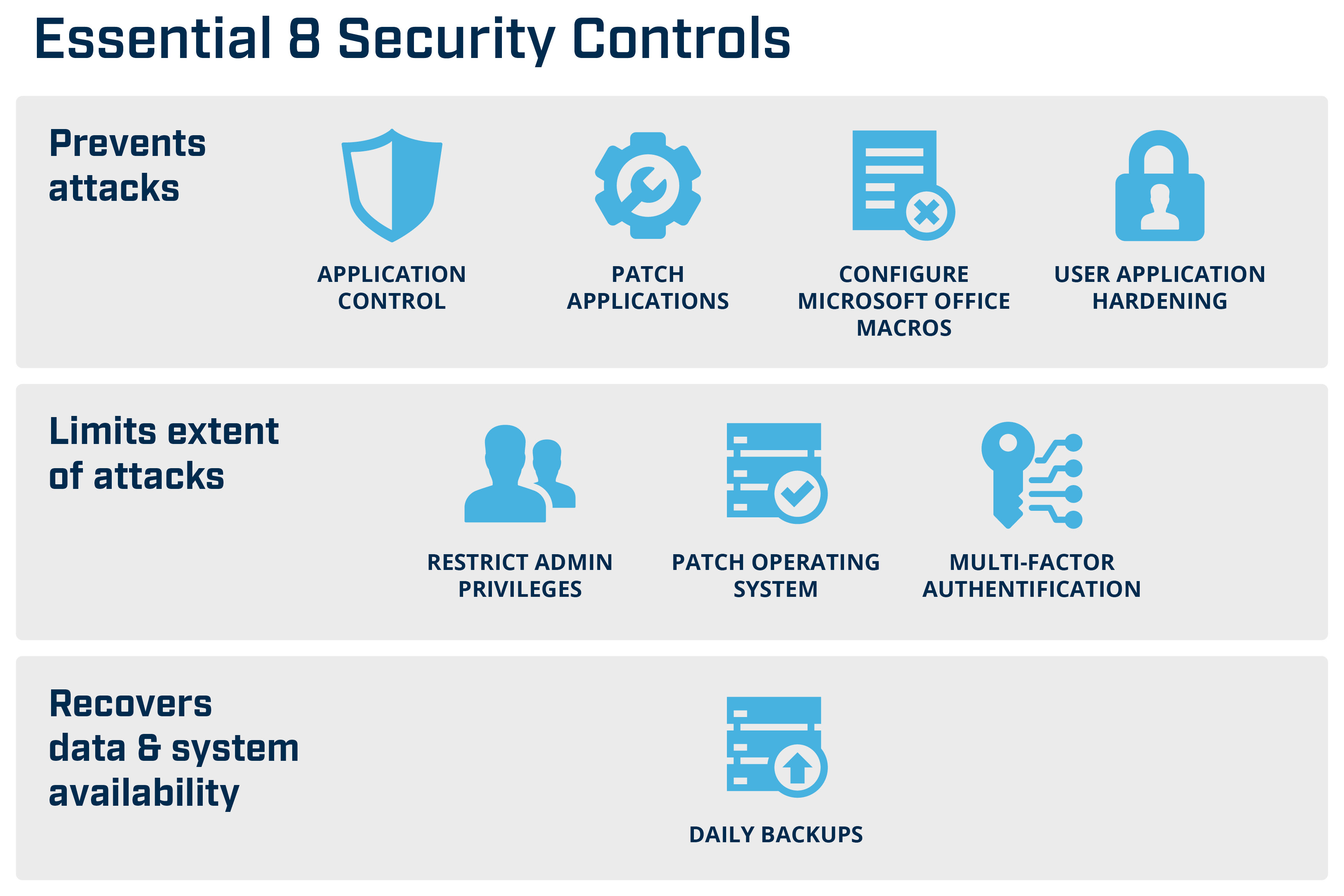
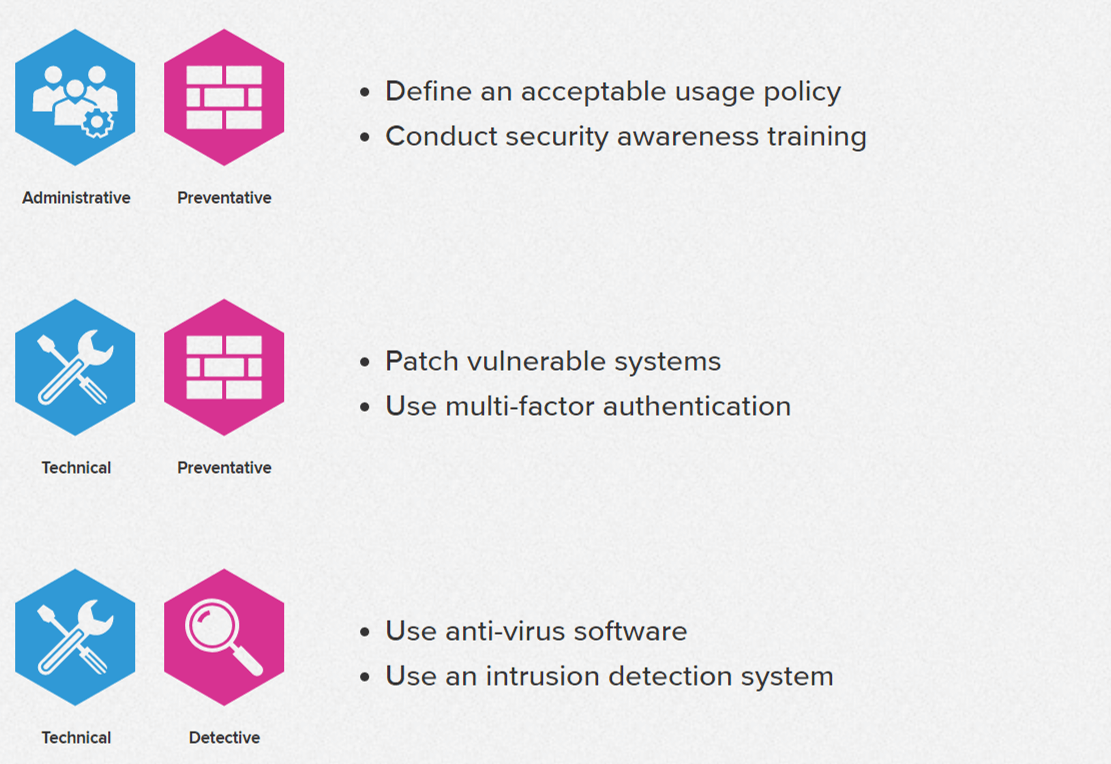
While screen time management dominates user interaction with safety controls, crucial security settings are frequently overlooked. Only 22% of respondents reported using safety settings to manage application permissions, a critical feature for preventing malware installation and unauthorized data access.
Even fewer, a mere 15%, utilize safety controls to restrict access to potentially harmful websites, leaving users exposed to phishing scams and other online threats. The data underscores a knowledge gap and a potential underestimation of the risks associated with unchecked online activity.
Why the Disconnect?
Several factors contribute to this skewed usage pattern. A primary driver is the perceived immediacy of screen time management, particularly for parents concerned about their children's digital habits.
The visible and tangible effects of excessive screen time – sleep deprivation, decreased attention spans – are more readily apparent than the abstract threat of a data breach or cyberattack. Furthermore, cybersecurity settings are often perceived as complex and technically challenging, leading users to avoid them in favor of more easily understood time management tools.
The Role of Software Design
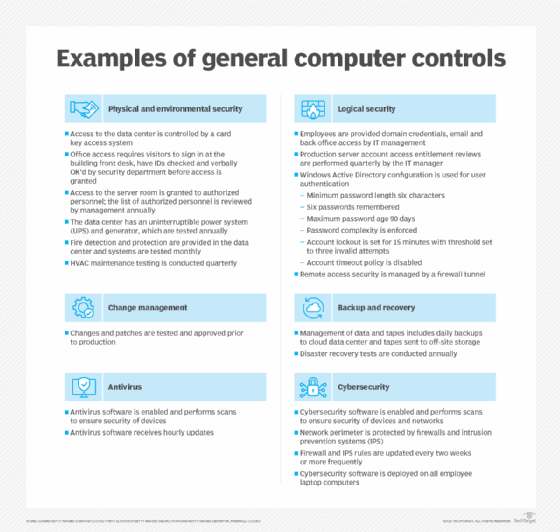
Software design also plays a role. Many operating systems and security software prioritize user-friendly interfaces for screen time management, often placing them prominently in settings menus. Conversely, security controls are frequently buried within advanced settings, requiring more technical expertise to configure correctly.
This design bias reinforces the focus on time management, inadvertently relegating cybersecurity concerns to the background. This emphasizes the need for more intuitive design principles that make security settings more accessible and understandable for the average user.
The Implications
The prevailing trend of prioritizing screen time management over security settings has far-reaching implications. Individuals are increasingly vulnerable to data breaches, identity theft, and financial fraud.
Businesses face heightened risks of cyberattacks, data loss, and reputational damage. The neglect of fundamental security measures creates a breeding ground for cybercriminals, who exploit these vulnerabilities to their advantage.
Expert Opinions
"This data paints a concerning picture of the current state of digital safety," says Dr. Anya Sharma, lead researcher at CIG. "While managing screen time is undoubtedly important, it should not come at the expense of basic cybersecurity hygiene. We need to educate users about the importance of proactive security measures and make those measures more accessible."
"The ease of access to screen time settings versus the complexity of security settings is a significant problem," adds Marcus Bellwether, a cybersecurity consultant. "Vendors need to prioritize user-friendly security interfaces and provide clear guidance on how to configure them effectively."
Moving Forward: Increased Awareness and Action
The findings from CIG underscore the urgent need for increased awareness and proactive measures to address the imbalance in computer safety control usage. Public awareness campaigns should emphasize the importance of comprehensive digital security, highlighting the risks associated with neglecting crucial security settings.
Software vendors must prioritize user-friendly design principles that make security controls more accessible and understandable for all users. Educational institutions and businesses should incorporate cybersecurity training into their curricula, equipping individuals with the knowledge and skills necessary to navigate the digital landscape safely.
CIG plans to release a detailed report outlining actionable steps for individuals and organizations to improve their cybersecurity posture. The report will be available on their website next month, aiming to empower users to take control of their digital safety and protect themselves from evolving cyber threats.