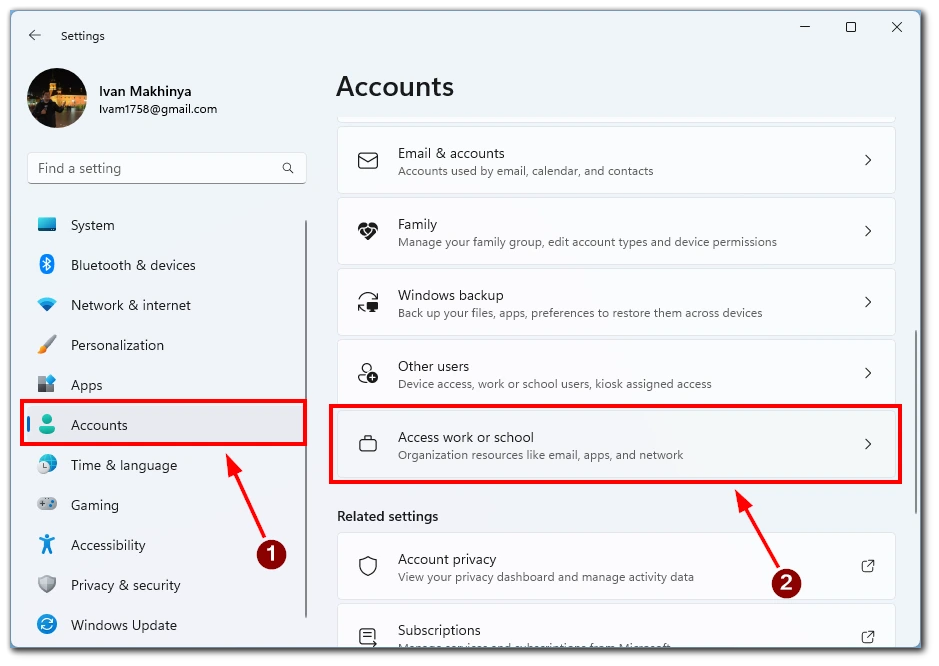
Device Must Comply With Your Organization Compliance Requirements
A seismic shift is underway in how organizations manage the devices accessing their networks and data. No longer is simple password protection and antivirus software enough. A new era of stringent compliance requirements is forcing companies to demand that every device, from corporate laptops to personal smartphones, meets rigorous security standards before gaining access to sensitive information.
This evolving landscape demands a fundamental change in approach. The implications are far-reaching, impacting everything from employee productivity and data security to IT infrastructure costs and regulatory compliance. Failure to adapt could result in crippling data breaches, hefty fines, and irreparable damage to reputation.
The Rise of Device Compliance
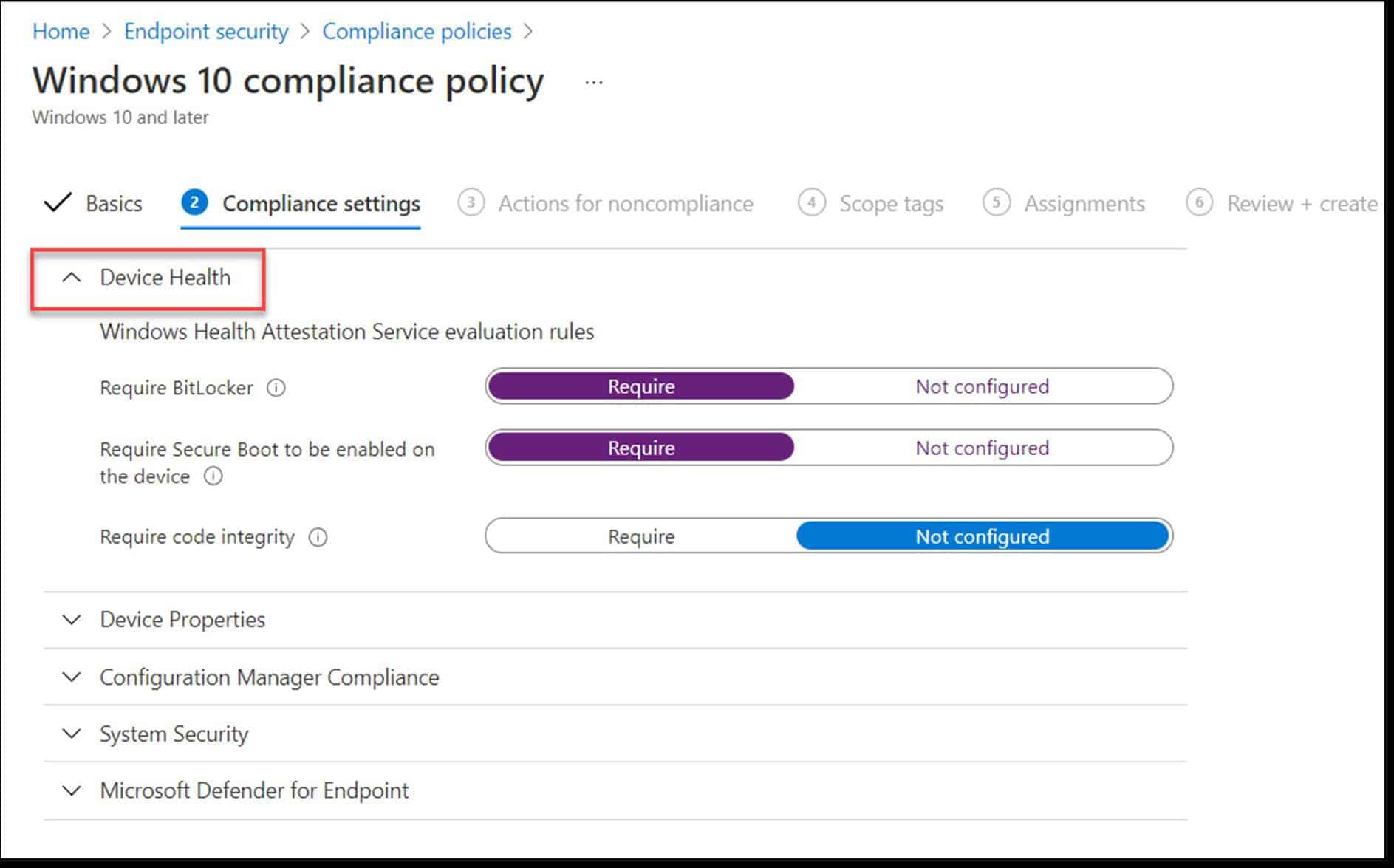
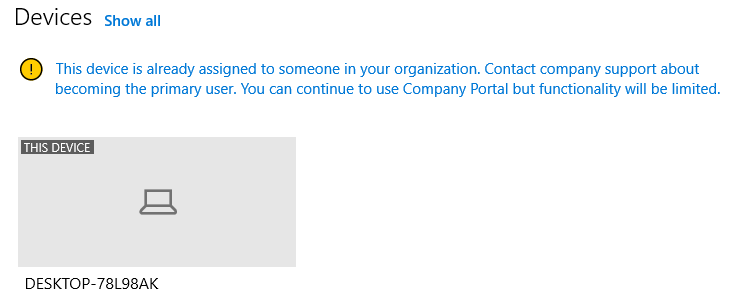
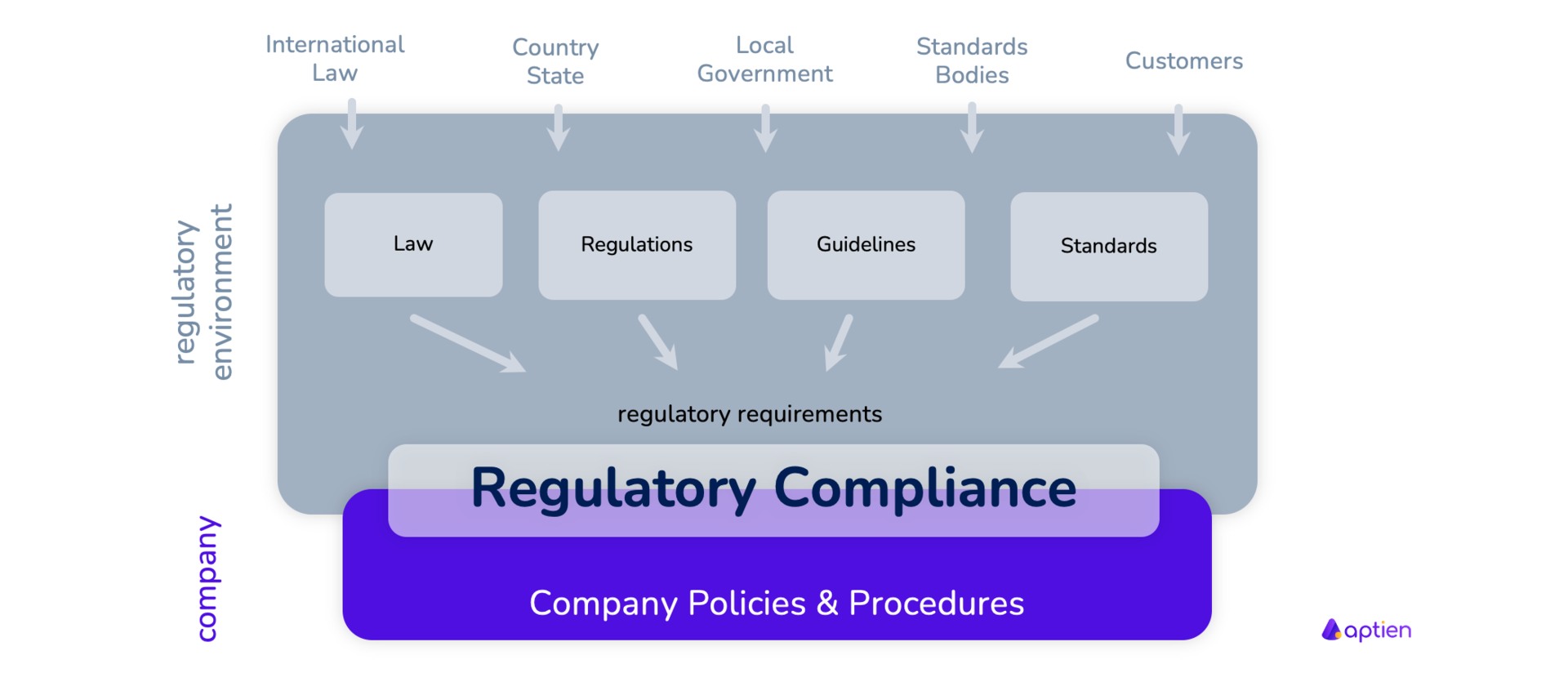
At its core, device compliance refers to the process of ensuring that any device attempting to connect to a network or access organizational resources meets a predefined set of security policies and standards. This encompasses a wide range of factors, including operating system version, installed software, security patches, encryption status, and adherence to password policies.
The rise of device compliance is driven by several key factors. The increasing sophistication of cyberattacks, the proliferation of mobile devices and BYOD (Bring Your Own Device) policies, and the growing number of data privacy regulations, such as GDPR and CCPA, have all contributed to the urgent need for more robust device security measures.
According to a recent report by Gartner, "By 2025, 70% of organizations will implement device compliance programs, up from less than 30% in 2022." This underscores the growing recognition of device compliance as a critical component of a comprehensive cybersecurity strategy.
Key Components of a Device Compliance Program
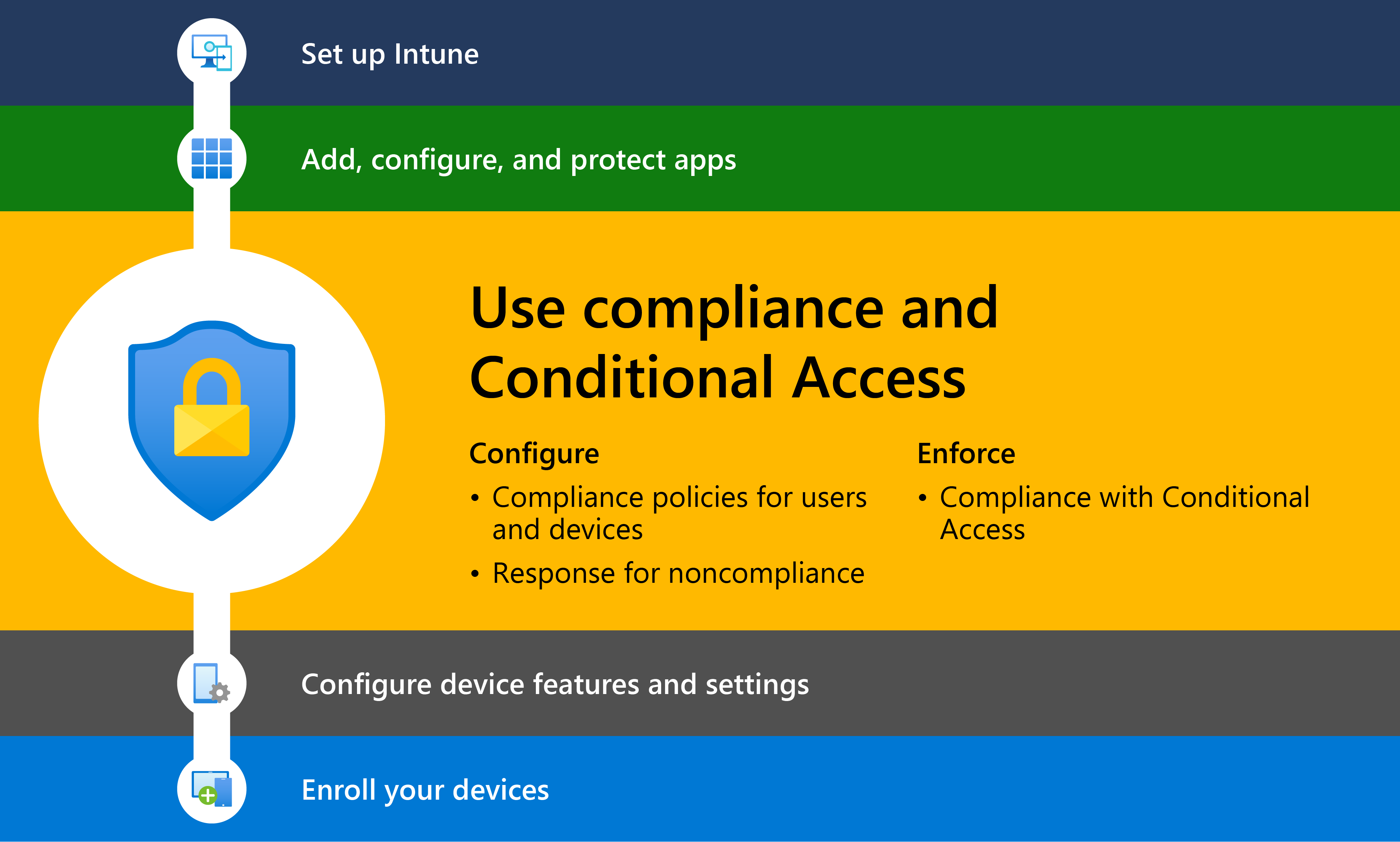
Implementing a successful device compliance program requires a multi-faceted approach. It involves establishing clear security policies, deploying appropriate technology solutions, and providing ongoing training and support to employees.
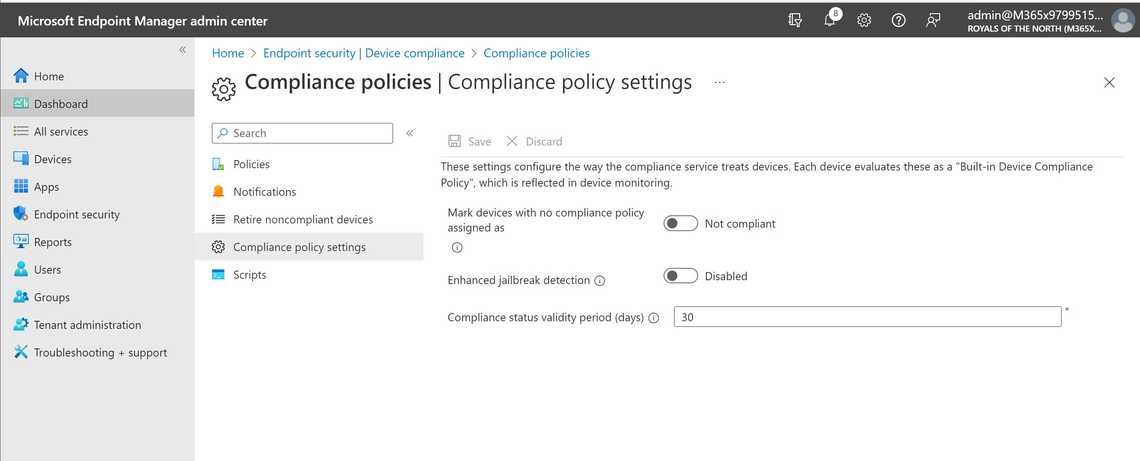
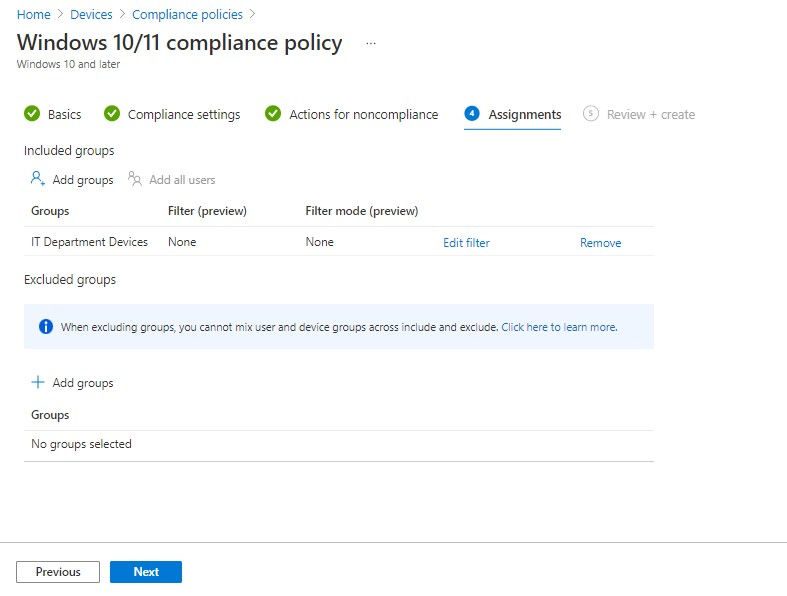
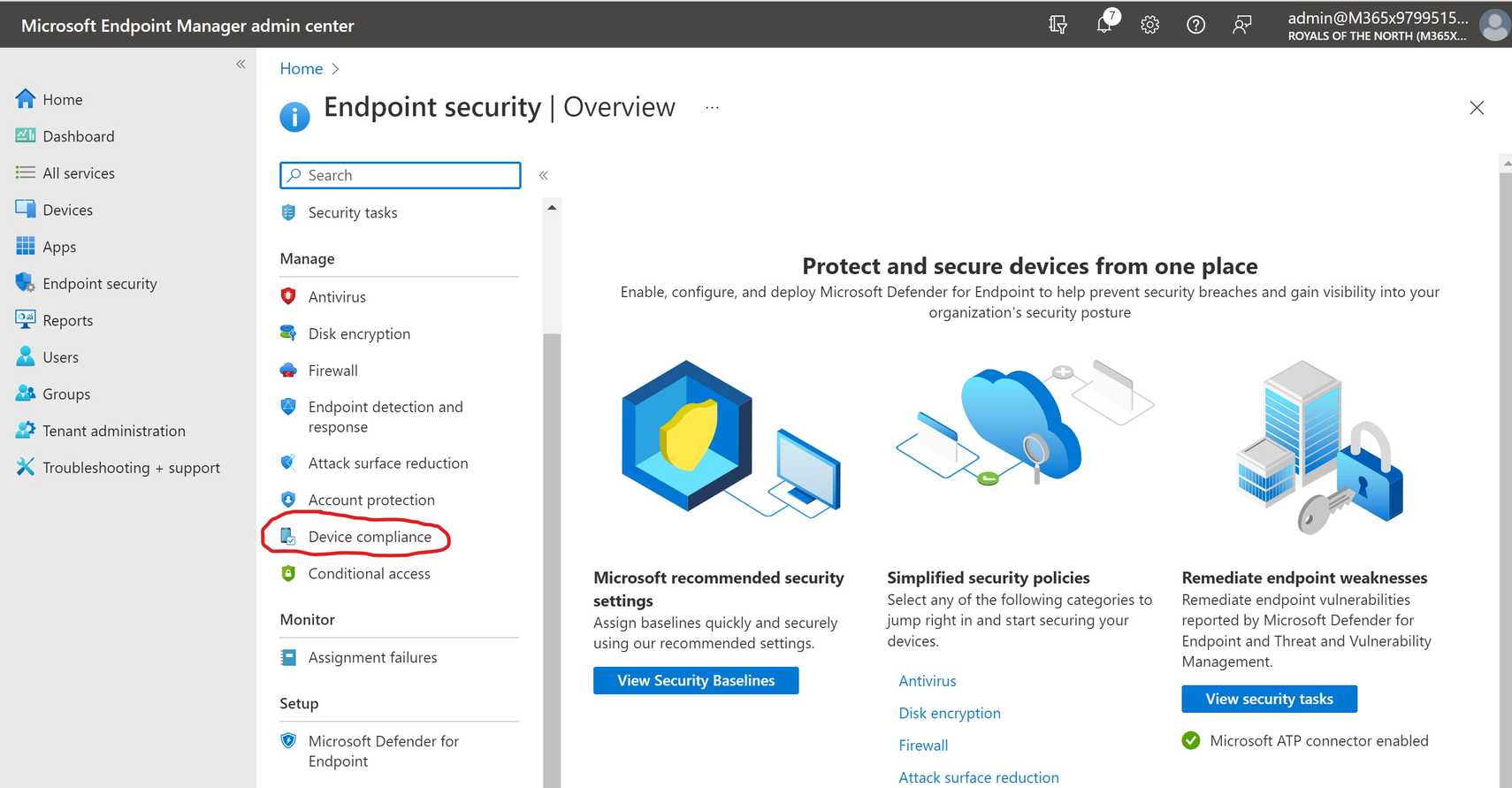
One crucial element is Mobile Device Management (MDM) software. MDM solutions enable organizations to remotely manage and secure mobile devices, enforce security policies, and monitor device compliance in real-time. Leading vendors in the MDM space include Microsoft with Intune, VMware with Workspace ONE, and Citrix with Endpoint Management.
Another important aspect is Endpoint Detection and Response (EDR). EDR solutions provide advanced threat detection and response capabilities, enabling organizations to identify and mitigate security incidents on devices before they can cause significant damage. EDR complements MDM by providing an additional layer of security focused on detecting and responding to sophisticated threats.
Beyond technology, clear and comprehensive security policies are essential. These policies should outline acceptable device usage, password requirements, data encryption standards, and procedures for reporting security incidents. Regular security awareness training can help employees understand these policies and adopt secure practices.
The Challenges of Implementation
While the benefits of device compliance are undeniable, implementing a successful program can present significant challenges. One of the biggest hurdles is balancing security with user convenience.
Imposing overly strict security policies can frustrate employees and hinder productivity. Finding the right balance requires careful consideration of the organization's risk tolerance, the sensitivity of the data being accessed, and the needs of the workforce.
Another challenge is managing the diversity of devices and operating systems in a BYOD environment. Supporting a wide range of devices can be complex and time-consuming. Organizations may need to implement different security policies for different types of devices or restrict access to certain resources based on device type.
Employee Privacy Concerns
Device compliance programs can raise legitimate employee privacy concerns. Employees may be wary of allowing their employers to monitor their personal devices. Transparency is key.
Organizations need to clearly communicate their security policies to employees. Explain how data collected from devices will be used and emphasize the measures taken to protect employee privacy.
It’s crucial to establish clear boundaries between corporate and personal data. Organizations must respect employees' privacy rights and avoid accessing or monitoring personal information unrelated to work activities. Experts recommend using containerization techniques to separate work and personal data on devices, mitigating privacy concerns and enhancing security.
The Future of Device Compliance
Device compliance is not a static concept. It is constantly evolving to keep pace with the ever-changing threat landscape. Artificial intelligence (AI) and machine learning (ML) are playing an increasingly important role in device compliance programs.
AI-powered solutions can automate many aspects of device compliance. This includes threat detection, vulnerability management, and policy enforcement. These technologies can also help organizations identify and prioritize security risks more effectively.
Looking ahead, device compliance will likely become even more integrated with identity and access management (IAM) systems. This will enable organizations to enforce more granular access controls based on device posture, user identity, and contextual factors such as location and time of day.
In conclusion, device compliance is no longer optional. It is a critical requirement for organizations of all sizes. Organizations that embrace a proactive approach to device compliance will be better positioned to protect their data, mitigate security risks, and maintain a competitive advantage in an increasingly digital world. Ignoring these requirements could result in significant financial and reputational consequences.