How Do You Send An Email Password Protected

Your sensitive information is vulnerable if sent via regular email. Learn how to password protect your emails immediately to safeguard confidential data from unauthorized access.
This guide provides a concise, actionable strategy to encrypt your email content, ensuring only the intended recipient can unlock and read it. We will cover methods applicable to various email providers and operating systems, prioritizing ease of implementation and robust security.
Securing Emails: The Imperative
Unencrypted emails are akin to postcards, easily read by anyone intercepting them. Protecting sensitive data, be it financial records, legal documents, or personal information, is crucial in today's digital landscape.
Password protection adds a layer of encryption, rendering the email unreadable without the correct password. This measure significantly reduces the risk of data breaches and unauthorized access.
Methods for Password Protecting Emails
1. Using Encryption Software (PGP/GPG)
Pretty Good Privacy (PGP) and GNU Privacy Guard (GPG) are powerful encryption tools. They use public-key cryptography to encrypt and decrypt emails, ensuring only the recipient with the corresponding private key can read the message.
Kleopatra and Gpg4win are popular Windows-based GPG tools. GPG Suite is commonly used on macOS. Users must install the software, generate key pairs, and exchange public keys with their recipients.
To encrypt, you encrypt the email using recipient's public key. The recipient decrypts with their private key; thus, your email is safe.
2. Using Email Provider's Built-in Features
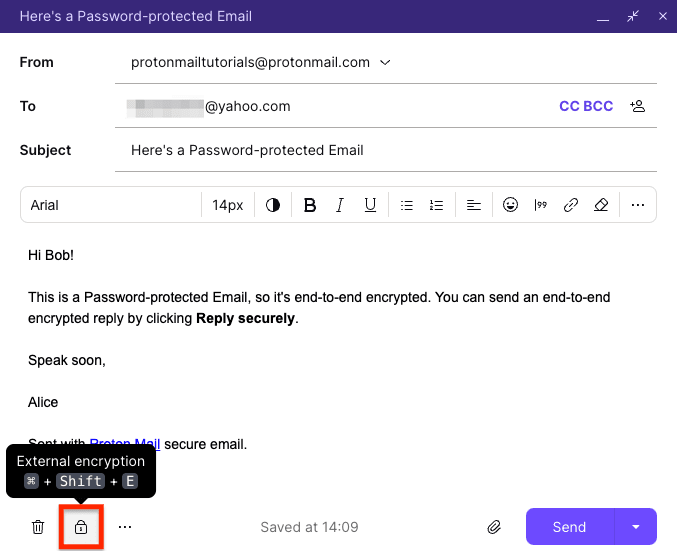
Some email providers offer built-in encryption features. ProtonMail, for instance, provides end-to-end encryption by default, requiring both sender and receiver to use ProtonMail for seamless secure communication.
Gmail’s Confidential Mode, while not full encryption, allows you to set an expiration date for emails and require recipients to authenticate with a passcode sent via SMS. To use it, compose a new email, click the lock icon at the bottom of the compose window, set your parameters, and send.
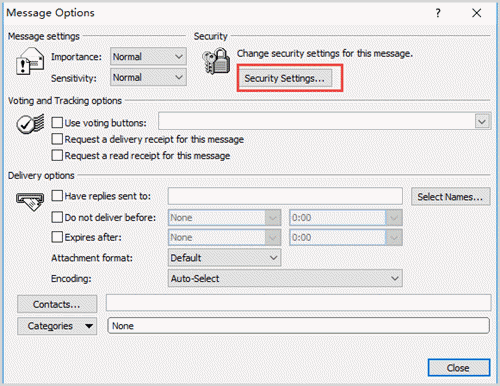
Microsoft Outlook offers message encryption through Azure Information Protection (AIP). To use AIP, select Options, then Permissions, and finally Encrypt.
3. Password-Protecting Attachments
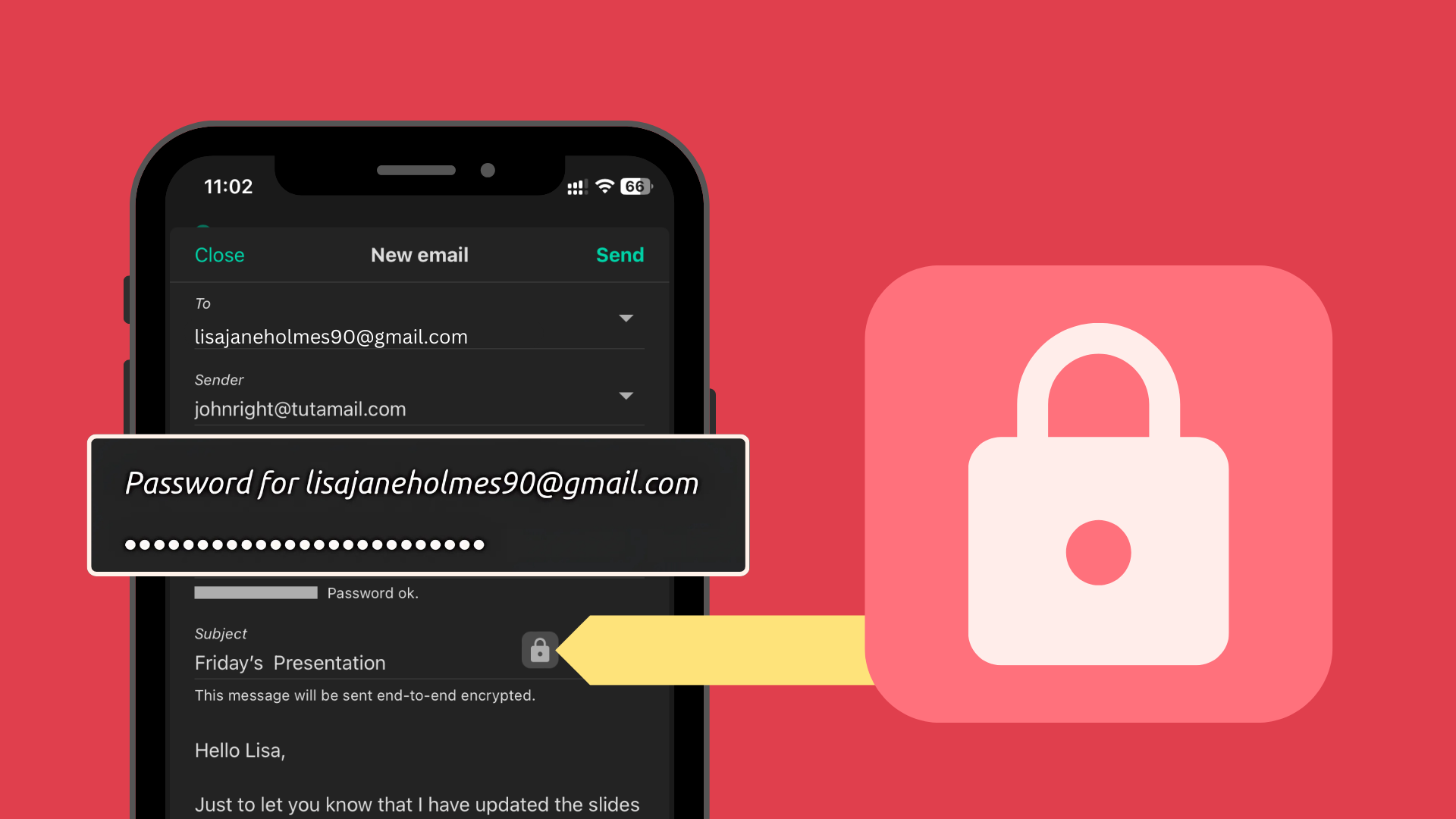
An alternative is to password-protect email attachments. You can create a password-protected archive (ZIP or 7z) or a password-protected document (Word, Excel, PDF).
To password-protect a ZIP file on Windows, right-click the file, select “Send to,” then “Compressed (zipped) folder.” Add the files to the zip archive and protect it by password.
In Microsoft Word, go to File > Info > Protect Document > Encrypt with Password. For PDFs, you can use Adobe Acrobat or other PDF editors to add password protection.
4. Third-Party Encryption Services
Various third-party services specialize in email encryption. These services often offer user-friendly interfaces and simplified encryption processes.
Examples include Virtru and Sendinc. These services provide plugins and extensions that integrate with popular email clients, enabling easy encryption with a few clicks.
Consider the service's reputation, security protocols, and pricing before choosing a third-party solution.
Critical Considerations
Password management is vital; store passwords securely using a password manager. Sharing passwords via unencrypted channels defeats the purpose of password protection.
Regularly update your encryption software and email clients to patch security vulnerabilities. Keep abreast of new threats and best practices for email security.
Ensure that the recipient knows the password through a secure channel (e.g., phone call, secure messaging app) - *never* in the same email as the protected content.
Next Steps
Immediately assess your email security needs and implement one of the described methods. Prioritize encryption for sensitive communications.
Research and choose the method that best suits your technical capabilities and organizational requirements. Start protecting your data now.
Stay informed about evolving encryption technologies and adapt your security measures accordingly. Data protection is an ongoing process.











/filters:quality(60)/2021-09-22-image9.png)
