Is Dark Web Monitoring Worth It

In the shadowy corners of the internet, where anonymity reigns and illicit activities thrive, lies the dark web. A growing concern for individuals and organizations alike is whether monitoring this murky realm for compromised data is a worthwhile investment, or just another overhyped security measure.
The debate around dark web monitoring boils down to a crucial question: Does proactively searching for stolen credentials and sensitive information in these hidden networks genuinely reduce the risk of data breaches and identity theft, or is it a costly exercise with limited returns? This article delves into the complexities of dark web monitoring, weighing its potential benefits against its practical limitations, and examining the perspectives of cybersecurity experts and affected organizations. It aims to provide a balanced assessment to help readers determine if dark web monitoring is a necessary component of their overall security strategy.
Understanding the Dark Web Threat Landscape
The dark web, a subset of the deep web, is accessible only through specialized browsers like Tor and is often associated with illegal marketplaces selling stolen data, drugs, weapons, and other illicit goods and services. Stolen credentials, including usernames, passwords, credit card numbers, and personal information, are frequently traded on these platforms. This information can be used for identity theft, financial fraud, and corporate espionage.
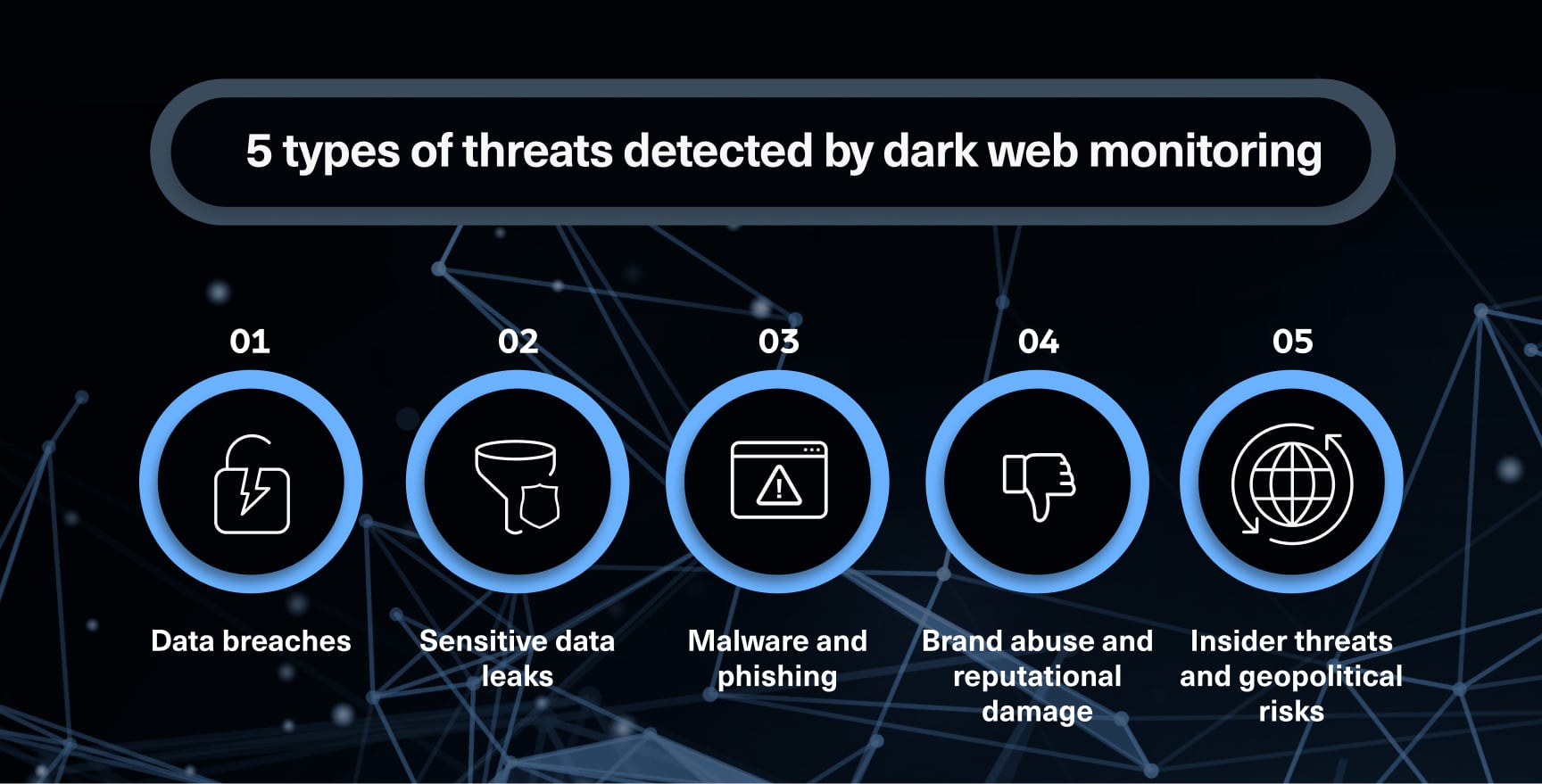
Data breaches are the primary source of this stolen data. Once a company suffers a breach, the compromised data often ends up being sold or distributed on the dark web, putting individuals and organizations at increased risk.
The FBI and other law enforcement agencies have repeatedly warned about the dangers of the dark web and the potential for stolen data to be used for malicious purposes.
What is Dark Web Monitoring?
Dark web monitoring services scan various dark web marketplaces, forums, and chat rooms for specific keywords and phrases, such as email addresses, usernames, company names, or sensitive data patterns. When a match is found, the service alerts the user or organization, allowing them to take proactive steps to mitigate potential damage. These steps can include changing passwords, canceling credit cards, and implementing additional security measures.
Different dark web monitoring services offer varying levels of sophistication. Some services simply scan for exact matches of specified keywords, while others employ more advanced techniques, such as natural language processing and machine learning, to identify related or contextual information.
The goal of dark web monitoring is to provide early warning of compromised data so that preventative action can be taken before the information is used for malicious purposes. This proactive approach is often touted as a key advantage over reactive measures taken after a data breach has already occurred.
Arguments in Favor of Dark Web Monitoring
Proponents of dark web monitoring argue that it provides a valuable layer of defense against data breaches and identity theft. By proactively searching for compromised data, organizations can identify potential threats early on and take steps to mitigate the damage.
Finding your compromised credentials on the dark web allows you to change your passwords and update your security settings before an attacker can use that information. This early detection can save significant time, money, and reputational damage.
For organizations, dark web monitoring can help to identify potential vulnerabilities in their security systems. If a large amount of company data is found on the dark web, it may indicate a larger breach or vulnerability that needs to be addressed.
Arguments Against Dark Web Monitoring
Critics of dark web monitoring argue that it is often ineffective, costly, and prone to false positives. They contend that much of the information found on the dark web is outdated, inaccurate, or already publicly available.
The sheer volume of data on the dark web makes it difficult to sift through and identify truly relevant information. Many dark web monitoring services generate a high number of false positives, wasting time and resources investigating non-threats.
Some experts argue that focusing solely on dark web monitoring can create a false sense of security and divert resources from more critical security measures, such as vulnerability management, employee training, and incident response planning. Instead, they suggest investing in preventing data breaches in the first place.
The Importance of Context and Actionable Intelligence
The value of dark web monitoring hinges on the context of the information found and the ability to translate that information into actionable intelligence. Simply finding a list of email addresses and passwords on the dark web is not enough.
Effective dark web monitoring requires the ability to verify the authenticity of the data, assess the potential impact, and take appropriate action. This may involve investigating the source of the data, identifying affected individuals or systems, and implementing remedial measures.
"Actionable intelligence is key," states cybersecurity consultant, Sarah Chen. "Simply knowing your data is out there isn't enough. You need to understand the context and take steps to mitigate the risk."
Is Dark Web Monitoring Right for You?
The decision of whether or not to invest in dark web monitoring depends on several factors, including the size and complexity of the organization, the sensitivity of the data being protected, and the overall security budget.
Smaller organizations with limited resources may find that dark web monitoring is not cost-effective. Larger organizations with more sensitive data may benefit from the added layer of security that dark web monitoring provides.
Ultimately, the decision to invest in dark web monitoring should be based on a careful assessment of the potential risks and benefits, taking into account the specific needs and circumstances of the organization. It should be part of a comprehensive security strategy that includes proactive measures to prevent data breaches and effective incident response planning.
Looking Ahead: The Future of Dark Web Monitoring
As the dark web continues to evolve, dark web monitoring services will need to adapt and improve their capabilities. This includes using more sophisticated techniques to identify and verify compromised data, reducing the number of false positives, and providing more actionable intelligence.
The integration of artificial intelligence and machine learning will likely play a significant role in the future of dark web monitoring. These technologies can help to automate the process of identifying and analyzing dark web data, making it more efficient and effective.
While dark web monitoring is not a silver bullet, it can be a valuable tool for organizations looking to proactively protect themselves from data breaches and identity theft. However, it is crucial to understand the limitations of dark web monitoring and to use it as part of a comprehensive security strategy that addresses all aspects of cybersecurity.