Scam Microsoft Account Unusual Sign In Activity
A surge in fraudulent "unusual sign-in activity" alerts targeting Microsoft account holders has sparked widespread concern and financial losses. Victims are lured by seemingly legitimate emails or SMS messages claiming unauthorized access to their accounts, prompting them to click on links or call phone numbers that ultimately lead to sophisticated phishing schemes and malware installations.
The alarming rise in these scams underscores the increasing sophistication of cybercriminals and the urgent need for heightened user awareness and robust security measures. Users report receiving emails that appear to be officially from Microsoft, warning of unusual activity and urging immediate action to secure their accounts, a ploy used to steal credentials and financial information.
The Anatomy of the Scam
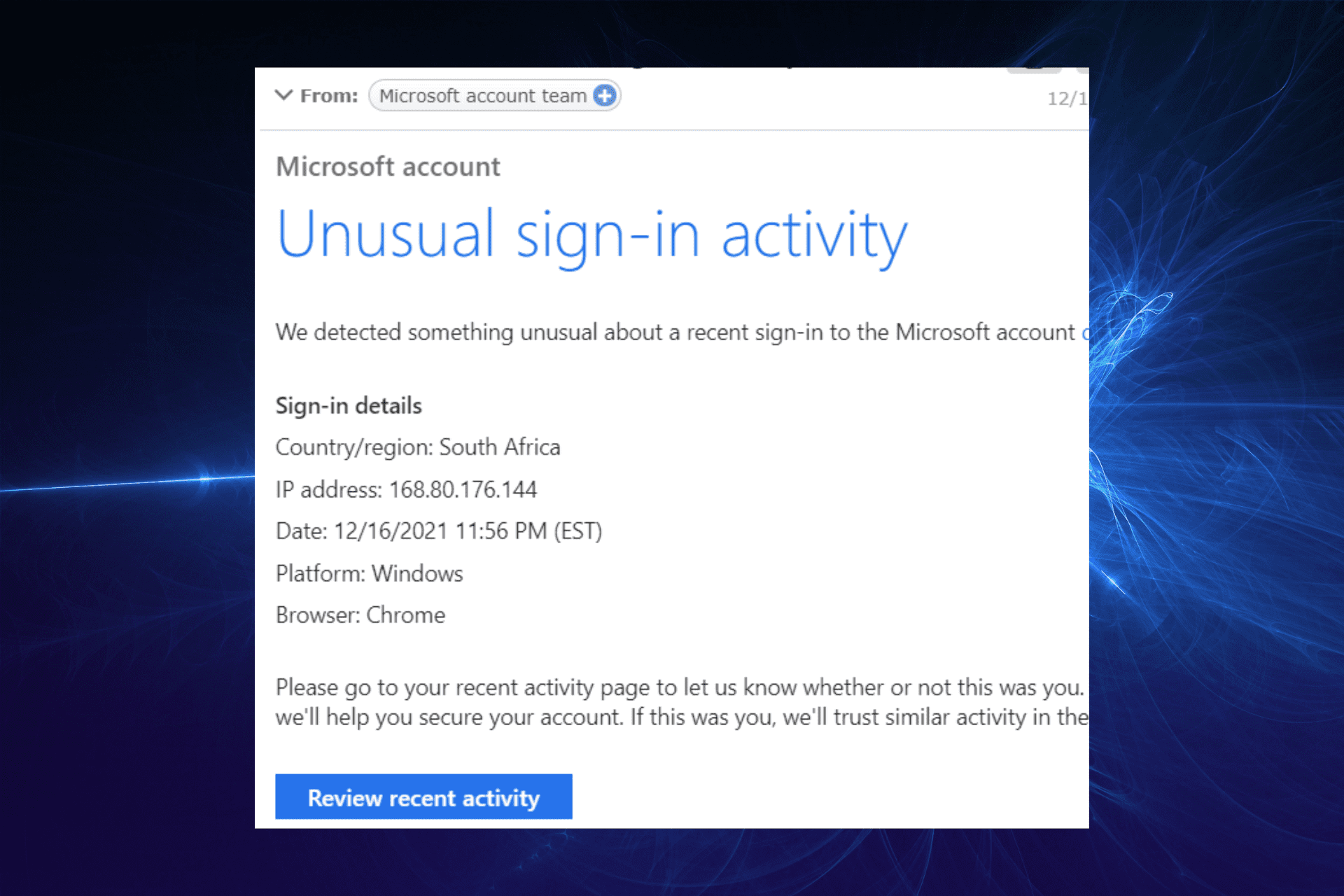
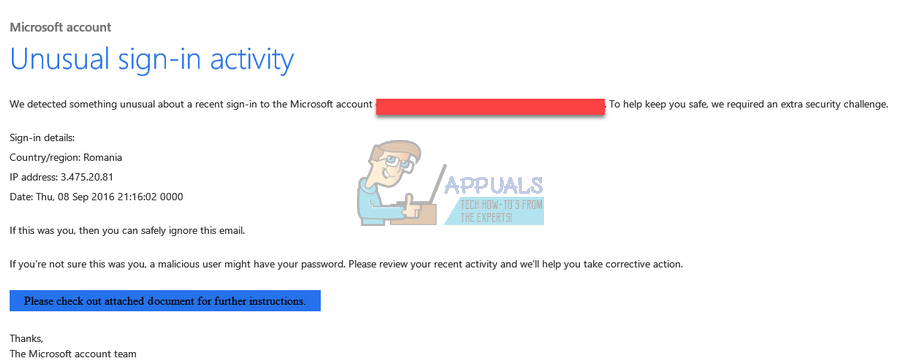
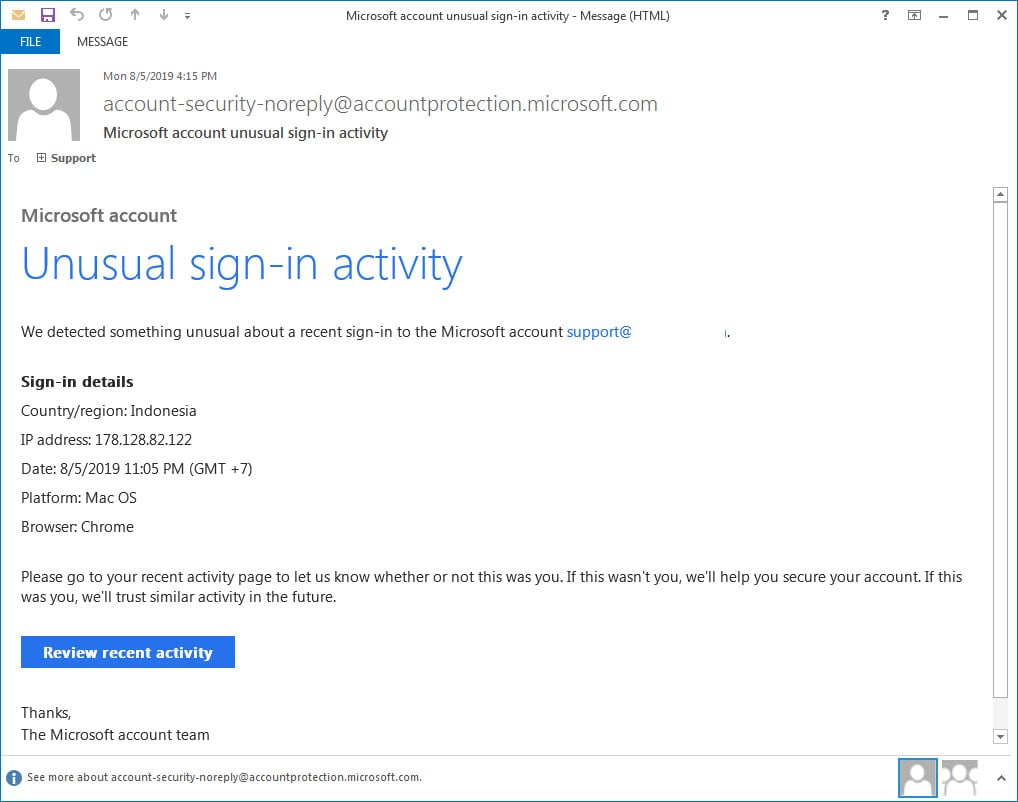
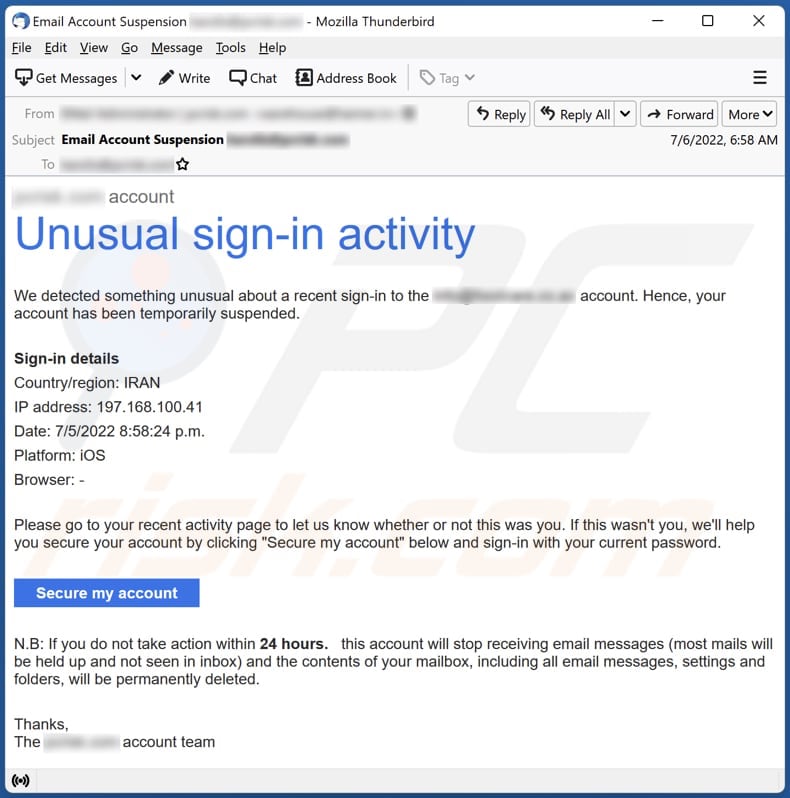
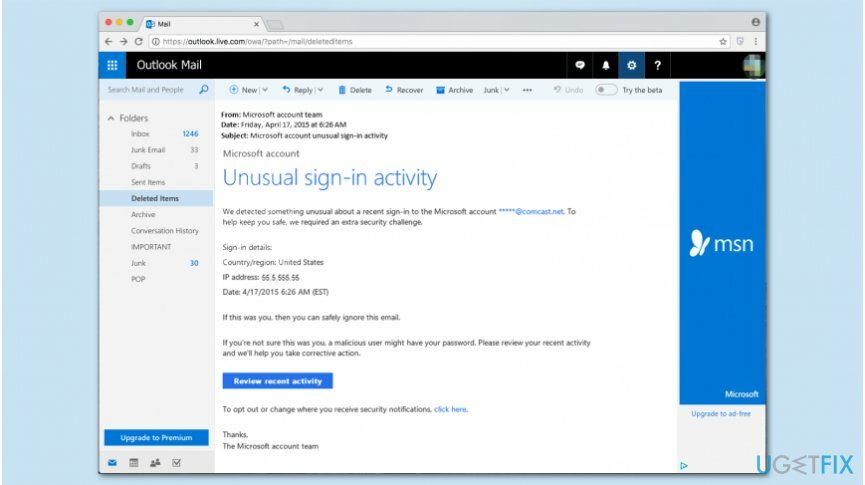
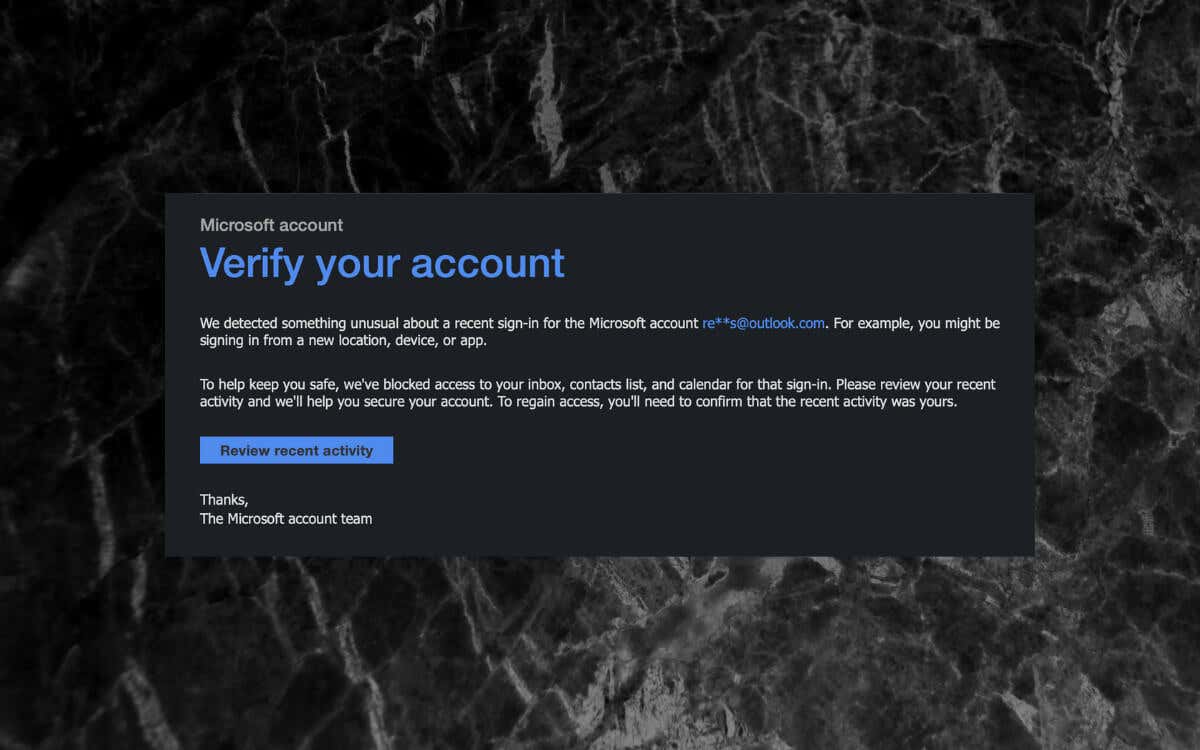
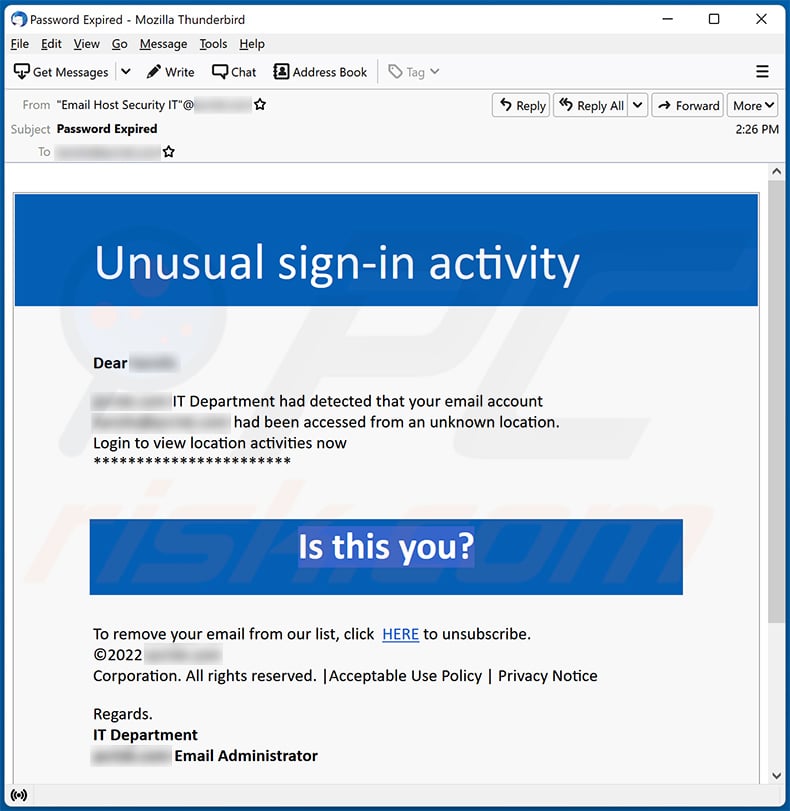
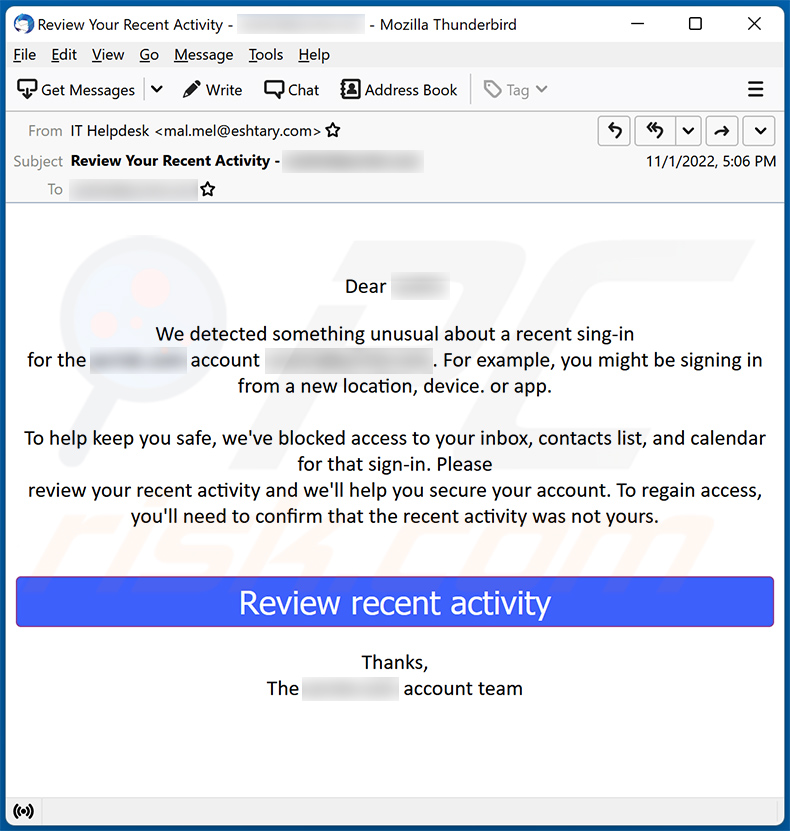
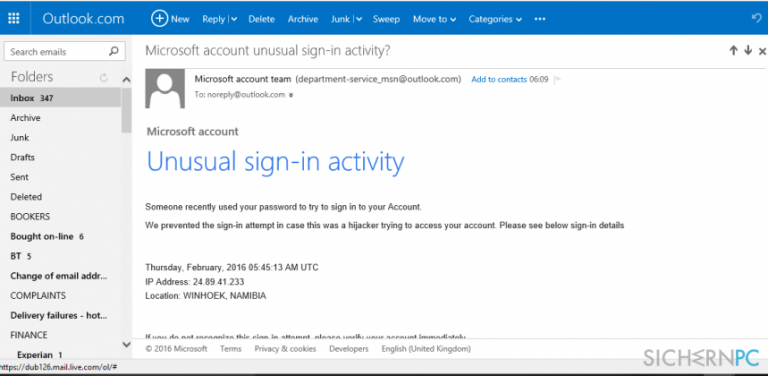
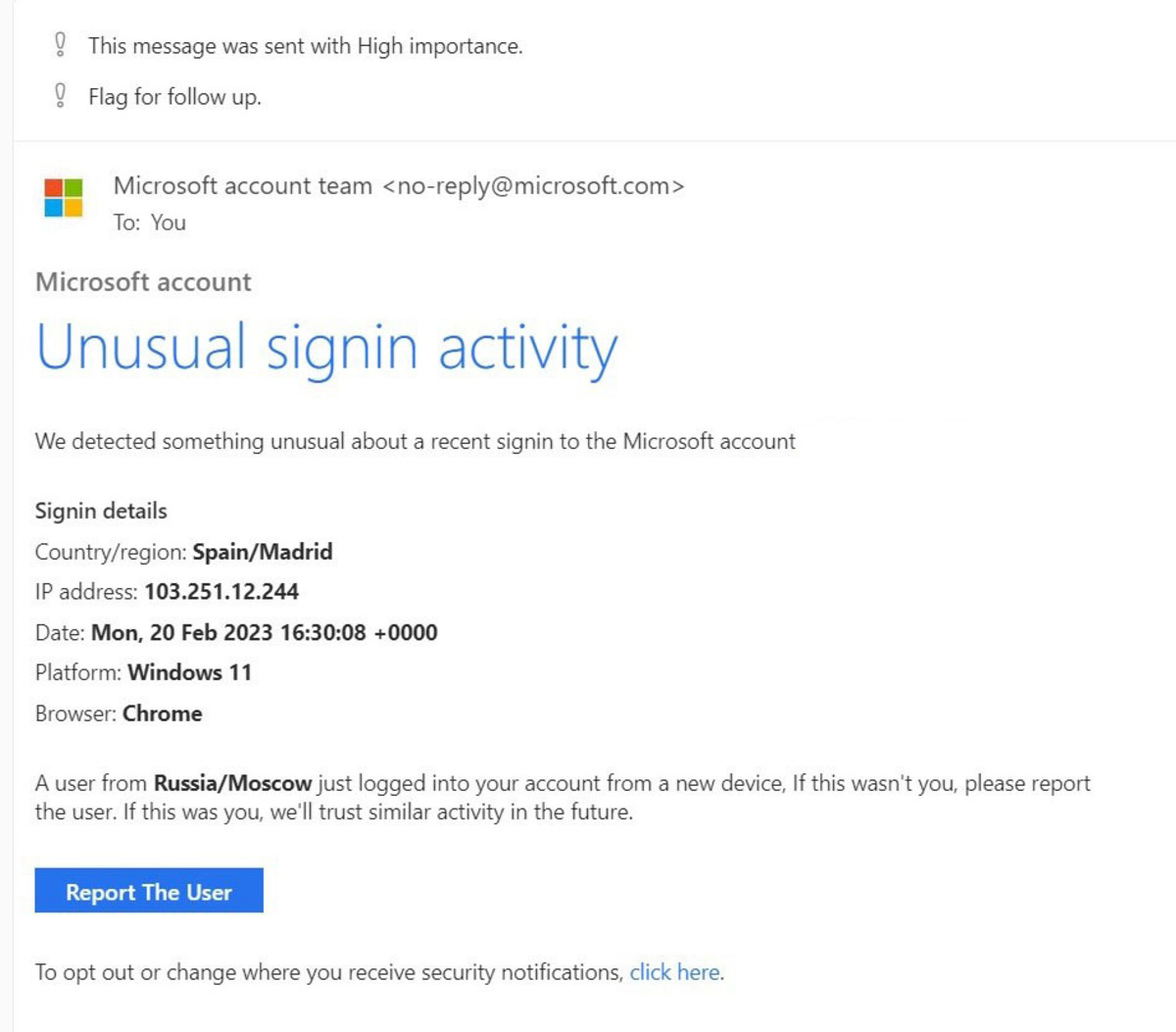
At the heart of this scam is a deceptive email or SMS message designed to mimic official Microsoft communications. The messages often include Microsoft logos and language that creates a sense of urgency, prompting recipients to act quickly without scrutinizing the details.
The "unusual sign-in activity" is typically cited as the pretext for demanding immediate action. This pretense of a security breach preys on user's fear of losing access to their accounts and personal data. The goal is to panic the victim into providing sensitive information.
Phishing Emails and Fake Websites
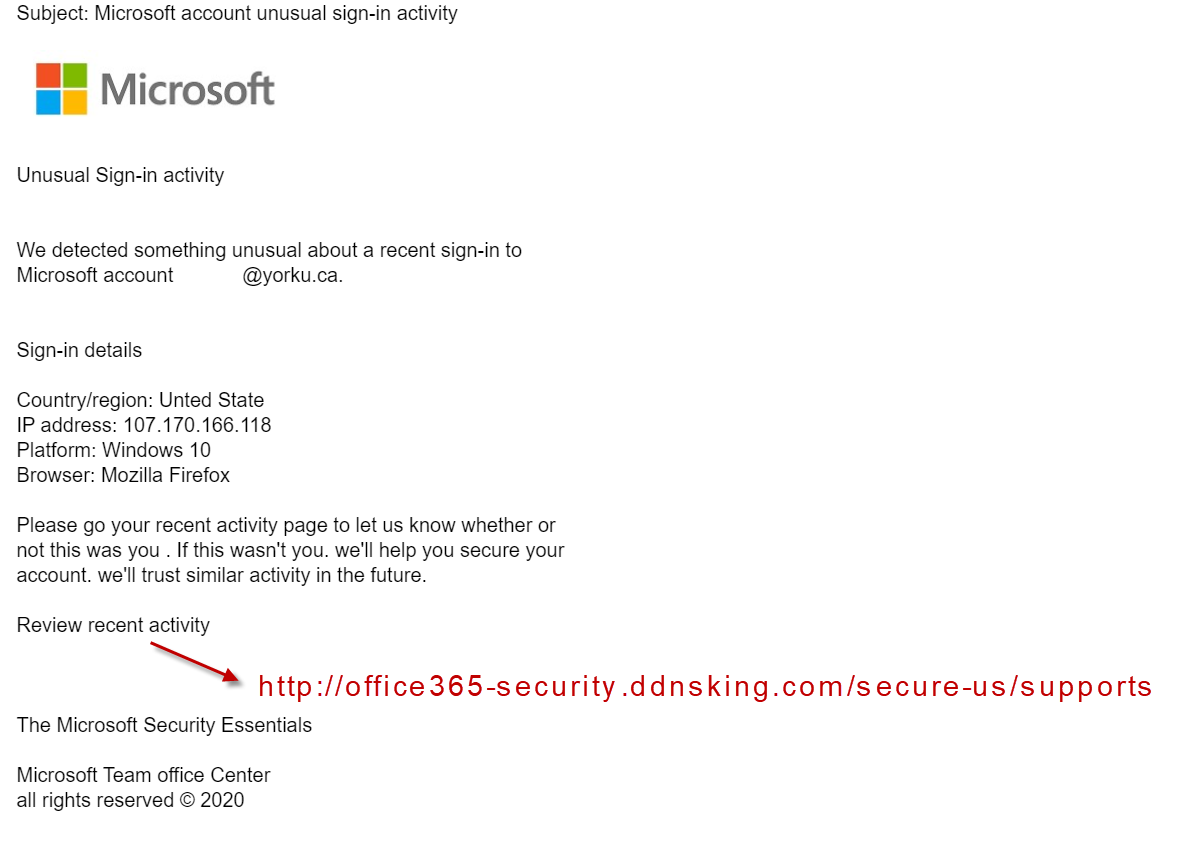
The phishing emails usually contain a link that redirects users to a fake Microsoft login page. This page is designed to capture the user's username and password. Once the victim enters their credentials, the scammers have access to their actual Microsoft account.
These fake websites often look remarkably similar to the real Microsoft login page, making it difficult for users to distinguish between the legitimate site and the fraudulent one. The scammers use various techniques, such as using Microsoft's branding and logos, to create a convincing replica.
Tech Support Scams and Malware
Another variation of the scam involves directing victims to call a fraudulent tech support number. The individuals answering these calls often claim to be Microsoft representatives and pressure users into granting remote access to their computers.
Once they have remote access, the scammers can install malware, steal personal data, or demand payment for unnecessary or nonexistent technical services. These services are portrayed as essential to fix the compromised security of the Microsoft account.
Microsoft's Response and Recommendations
Microsoft has acknowledged the increasing prevalence of these scams and is actively working to combat them. They have issued warnings to users about the dangers of phishing emails and tech support scams. Microsoft encourages users to be cautious of unsolicited communications.
Microsoft's official website provides detailed information on how to identify and avoid phishing scams, including tips on verifying the authenticity of emails and websites. Users should also check the sender's email address carefully and avoid clicking on links in suspicious emails. It is crucial to hover over links to reveal the actual URL before clicking.
Protecting Your Microsoft Account
Microsoft recommends several security measures to protect user accounts from unauthorized access. These include enabling two-factor authentication (2FA), using strong and unique passwords, and regularly updating your software.
Enabling 2FA adds an extra layer of security by requiring a verification code from your phone or email in addition to your password. This makes it much harder for scammers to access your account even if they have your password. Choosing strong, unique passwords for each online account also is critical to prevent credential stuffing attacks.
Staying current with software updates is essential because these updates often include security patches that address known vulnerabilities. Keeping your operating system, browser, and other software up to date helps to protect your computer from malware and other threats.
Expert Perspectives and Industry Trends
Cybersecurity experts note that the "unusual sign-in activity" scam is part of a broader trend of increasingly sophisticated phishing attacks. Scammers are constantly evolving their tactics to exploit human psychology and bypass security measures.
According to the Anti-Phishing Working Group (APWG), phishing attacks are on the rise across various industries, with email remaining the most common attack vector. The APWG emphasizes the importance of user education and awareness to combat phishing scams effectively.
"The key to preventing these scams is to be vigilant and skeptical," says cybersecurity consultant John Smith. "Always verify the authenticity of any email or phone call before taking action, and never give out personal information unless you are absolutely certain that you are dealing with a legitimate organization."
Victim Impact and Reporting Mechanisms
The impact of these scams can be devastating, resulting in financial losses, identity theft, and emotional distress. Victims may lose access to their email accounts, personal files, and online services.
It is important for victims to report these scams to the authorities and to take steps to mitigate the damage. Reporting the scam to the Federal Trade Commission (FTC) and the Internet Crime Complaint Center (IC3) can help law enforcement track and prosecute scammers.
Users should also change their passwords, monitor their credit reports, and consider placing a fraud alert on their accounts. Contacting financial institutions is key to notify them of the possible fraud and get them involved in prevention.
Looking Ahead: The Evolving Threat Landscape
The "unusual sign-in activity" scam is likely to persist and evolve as cybercriminals continue to refine their tactics. Staying informed about the latest scams and security threats is crucial for protecting yourself online.
As technology advances, so too will the methods used by scammers. Future attacks may leverage artificial intelligence (AI) to create even more convincing phishing emails and social engineering campaigns. Continuous user education and investment in robust security measures are essential to stay ahead of the curve.
Ultimately, a multi-layered approach to security is needed, combining user awareness, robust security technologies, and proactive monitoring to protect against the ever-evolving threat landscape. Vigilance is key.