Sorry To Disturb You In Your Busy Schedule Email

A surge in sophisticated phishing attacks leveraging the ubiquitous "Sorry To Disturb You In Your Busy Schedule" email subject line has prompted an urgent cybersecurity alert from the Cybersecurity and Infrastructure Security Agency (CISA).
These attacks, detected across various sectors, bypass traditional security filters by exploiting human psychology and trust, leading to significant data breaches and financial losses.
Widespread Impact of "Sorry To Disturb You" Phishing
CISA reports a 500% increase in incidents using this specific subject line in the past quarter. This alarming statistic highlights the campaign's effectiveness in tricking users into interacting with malicious content.
Targeted organizations include those in the financial, healthcare, and critical infrastructure sectors. The attackers are primarily after credentials, financial information, and access to sensitive systems.
One major healthcare provider reported a breach affecting over 100,000 patient records due to a successful phishing attack originating from a "Sorry To Disturb You" email.
How the Attacks Work
The phishing emails typically impersonate colleagues, business partners, or even superiors. The messages often request urgent action, such as reviewing a document, making a payment, or updating account information.
Links embedded in the emails lead to fake login pages that steal credentials. Malicious attachments may also contain malware that infects the user's device and network.
According to a recent Verizon Data Breach Investigations Report, 94% of malware is delivered via email. This underscores the importance of vigilance when handling unsolicited messages.
Expert Analysis and Recommendations
"The simplicity and perceived politeness of the subject line is its strength," says Dr. Anya Sharma, a leading cybersecurity expert at CyberDefend Solutions. "It disarms recipients and bypasses their initial skepticism."
CISA recommends implementing multi-factor authentication (MFA) across all systems. They also advise conducting regular security awareness training for employees to recognize and report phishing attempts.
Companies should also review and update their email security policies and implement advanced threat protection solutions. This includes spam filters, anti-malware software, and intrusion detection systems.
Immediate Actions to Take
Verify the sender's identity: Always double-check the sender's email address and contact them directly through a known, trusted channel to confirm the legitimacy of the message.
Be wary of urgent requests: Phishing emails often create a sense of urgency to pressure recipients into acting quickly without thinking critically.
Never click on suspicious links or open attachments: If you are unsure about the legitimacy of an email, do not interact with any links or attachments. Report the email to your IT department.
Ongoing Investigations and Future Threats
The FBI's Cyber Division is actively investigating the source of these attacks. Preliminary findings suggest that the campaign is being orchestrated by a sophisticated cybercrime group operating from Eastern Europe.
Authorities are working with international partners to identify and apprehend the perpetrators. The investigation is ongoing and further details are expected to be released in the coming weeks.
CISA continues to monitor the situation and will provide updates and guidance as needed. Stay vigilant and report any suspected phishing attempts to authorities immediately.





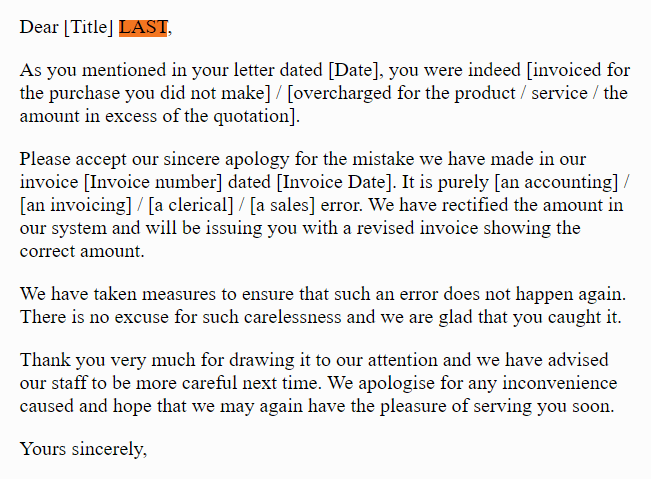
![Sorry To Disturb You In Your Busy Schedule Email How To Write An Apology Email: 7 Tips And Examples [2025] | Mailmunch](https://cdn.prod.website-files.com/5f3a33a074c2eb9e90f16437/66d917b33faf9aae9095c808_63280e96c2acfc2447f1d3b6_3.png)
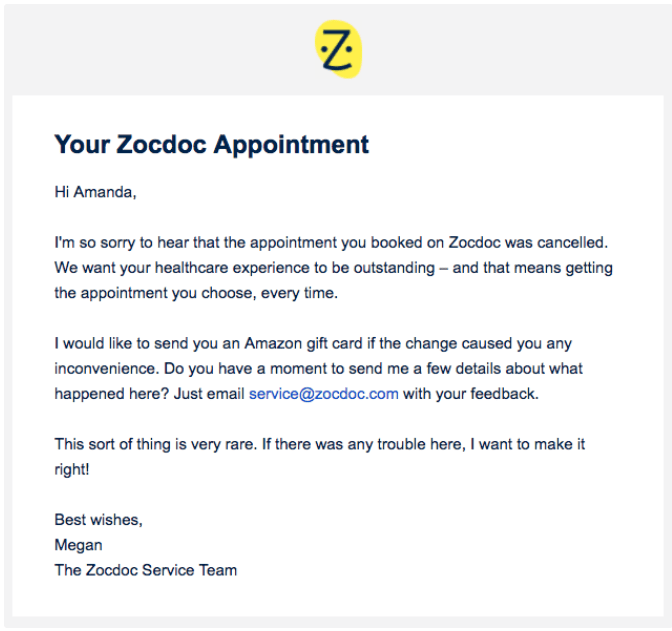
![Sorry To Disturb You In Your Busy Schedule Email How to Write & Send Apology Emails to Customers [+Examples]](https://automizy.com/wp-content/uploads/our-mistake.png)