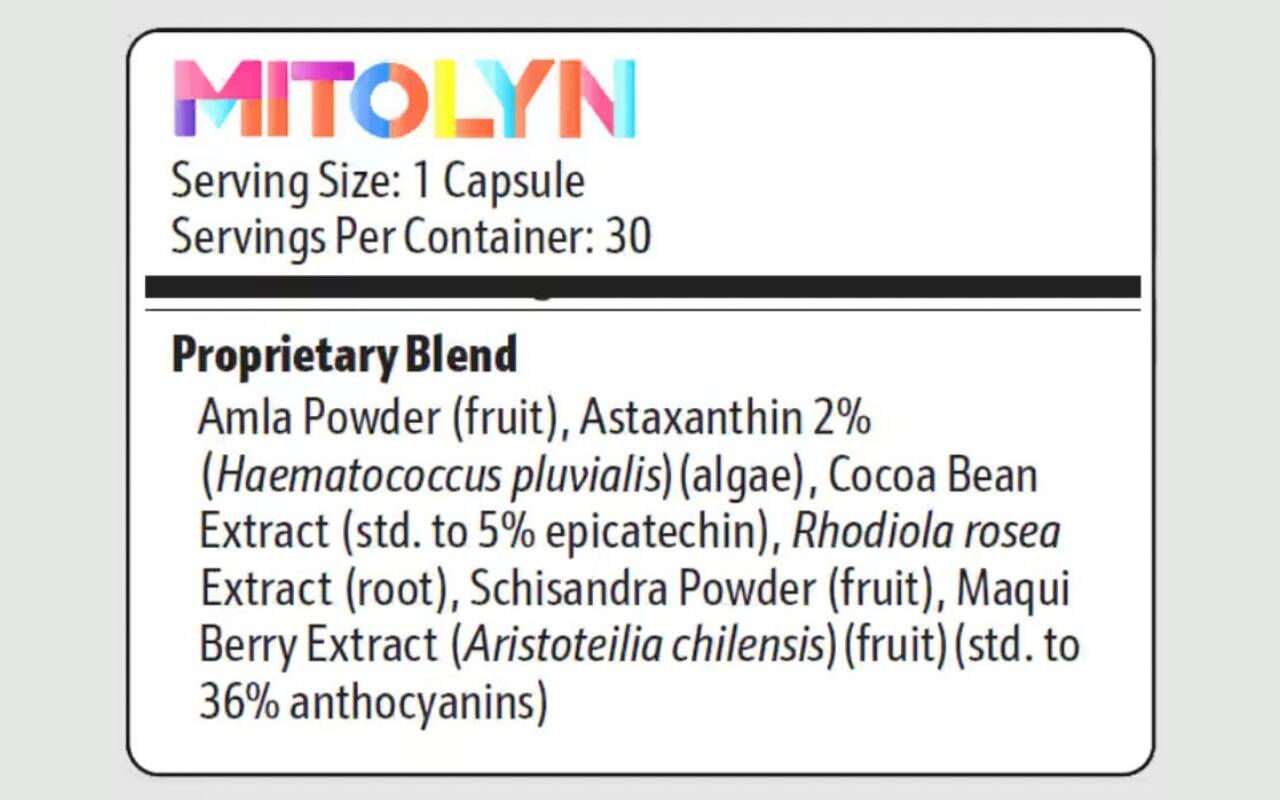
What Is The Purple Peel Exploit

Urgent security alert: A critical vulnerability, dubbed "Purple Peel," is actively being exploited, allowing unauthorized access to Apple devices through a complex sequence of interactions with the checkm8 exploit and potentially a zero-day vulnerability.
Purple Peel, not to be confused with any dermatological procedure, is a significant security flaw that allows attackers to bypass standard security measures, potentially gaining complete control over an iPhone or iPad.
The Purple Peel Exploit: What We Know
At its core, Purple Peel leverages the well-known checkm8 bootrom exploit.
checkm8, discovered in 2019, is a permanent unpatchable vulnerability affecting hundreds of millions of Apple devices running on A5 to A11 chips.
While checkm8 requires physical access to the device, Purple Peel allegedly allows for remote exploitation after initial access is achieved via checkm8, possibly in combination with a zero-day exploit, turning a temporary foothold into persistent control.
How the Exploit Works (Allegedly)
The exact technical details of Purple Peel are still being actively investigated by security researchers. However, the current understanding is as follows.
First, the attacker needs initial access to the device to run the checkm8 exploit.
This could be through physical connection or, more alarmingly, a sophisticated social engineering attack coupled with malicious software installation.
The second step allegedly involves the zero-day vulnerability: a previously unknown flaw in iOS that, when triggered by checkm8, grants further access to the device's core functions, allowing the attacker to bypass security restrictions and install persistent malware.
Who is Affected?
Devices with the A5 to A11 chips are inherently vulnerable to the checkm8 exploit that Purple Peel is leveraging.
This includes iPhones from the 4S to the 8 and 8 Plus, as well as iPads from the 4th to the 7th generation and the iPad Pro 1st and 2nd generation.
The alleged zero-day component might also extend the scope of affected devices and iOS versions, but this remains unconfirmed.
When Was the Exploit Discovered?
Details are emerging now in late 2024.
Independent security researchers are actively reverse-engineering and analyzing proof-of-concept code to understand the full scope of the vulnerability.
Where is the Exploit Being Used?
Reports suggest that Purple Peel is currently being used in targeted attacks, focusing on specific individuals or organizations.
However, the risk of wider exploitation is a major concern if the technical details become more widely available.
The Importance of Purple Peel
The significance of Purple Peel stems from its ability to bypass crucial security layers.
checkm8, on its own, requires a physical connection and is considered a tethered exploit, meaning it needs to be re-applied after each reboot.
Purple Peel's use of a zero-day component potentially enables a persistent and remote attack, making it far more dangerous.
If confirmed, it signifies a breakthrough in iOS exploitation techniques, highlighting the ongoing arms race between security researchers and malicious actors.
Impact on Users
The potential consequences for users are severe, ranging from data theft and privacy breaches to complete device compromise.
An attacker could potentially install spyware, steal sensitive information such as banking credentials and personal photos, or even remotely control the device.
For organizations, Purple Peel poses a significant threat to corporate security, potentially allowing attackers to gain access to sensitive data and internal networks.
What Should Users Do?
While a patch specifically addressing Purple Peel isn't available yet, there are steps users can take to mitigate the risk.
First and foremost, be extremely cautious about connecting your device to untrusted computers or networks.
Avoid installing apps from unofficial sources and be wary of phishing attempts that could lead to malicious software installation.
Ensure your device is running the latest available iOS version, as Apple frequently releases security updates that may address underlying vulnerabilities.
However, remember that devices vulnerable to checkm8 cannot be fully protected through software updates alone. The best defense is caution and awareness.
Ongoing Developments and Next Steps
The security community is actively working to understand the full scope and impact of Purple Peel.
Researchers are analyzing the alleged zero-day component and developing detection methods to identify compromised devices.
Apple is likely aware of the situation and is working on developing a patch or mitigation strategy, although the inherent limitations imposed by checkm8 on vulnerable devices will make a complete fix challenging.
Monitor trusted security news sources for updates and guidance. Vigilance is key in this rapidly evolving situation.
We will continue to update this article as more information becomes available.