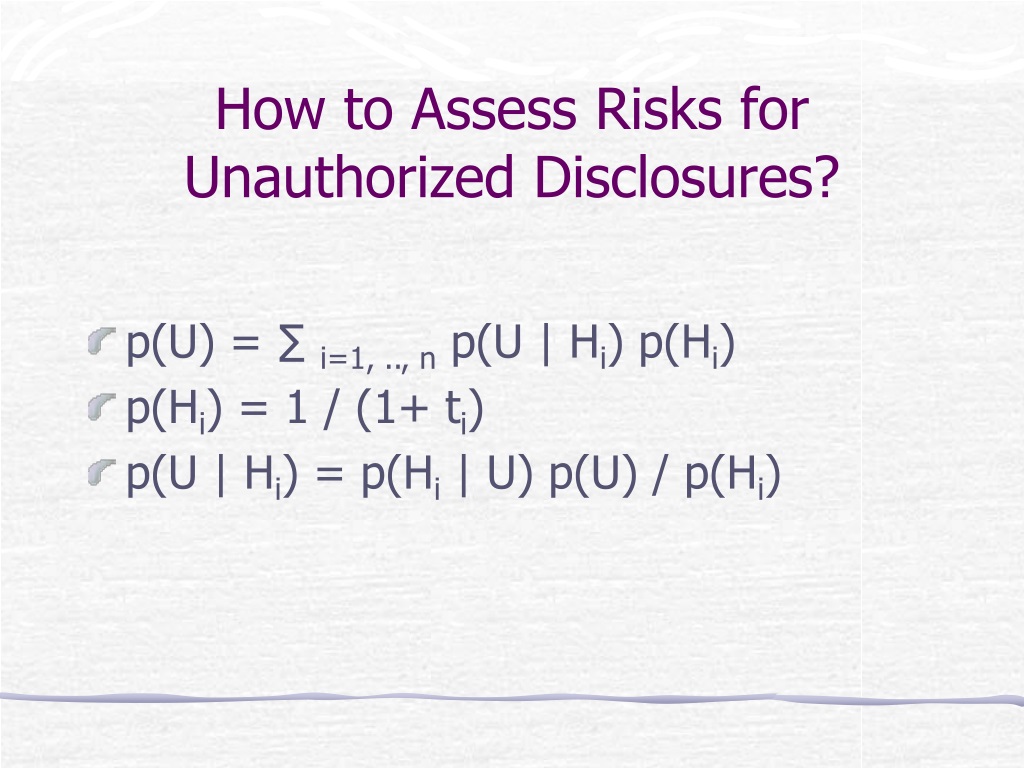
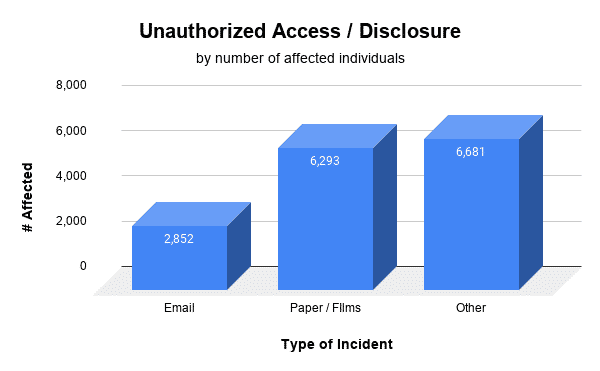
Which Of The Following Are Potential Indicators Of Unauthorized Disclosure

Urgent security alert: A surge in detected anomalies suggests a heightened risk of unauthorized data disclosure across multiple sectors. Organizations must immediately review internal protocols and security measures to mitigate potential breaches.
This report outlines key indicators signaling potential unauthorized disclosure, empowering security teams to identify and address vulnerabilities proactively. Recognizing these warning signs is crucial for safeguarding sensitive information and preventing damaging data leaks.
Unusual Network Activity
Data exfiltration often leaves digital fingerprints. Watch for spikes in outbound network traffic, particularly to unfamiliar IP addresses or geographical locations. Monitor for unusual data transfer patterns, such as large file transfers occurring outside of normal business hours.
Anomalous login activity is a critical red flag. Look for failed login attempts from multiple locations, especially if they target privileged accounts. Investigate logins occurring at odd hours or originating from unusual devices.
Endpoint Anomalies
Compromised endpoints are frequently gateways for unauthorized access. Pay attention to new or unfamiliar processes running on employee computers, especially those with administrative privileges. Monitor for the installation of unauthorized software, indicating potential malware infections.
Changes to system files, especially those related to security configurations, warrant immediate investigation. Deleted or modified log files are a strong indicator of malicious activity attempting to cover its tracks. Regularly verify the integrity of critical system files using file integrity monitoring tools.
Data Access Patterns
Irregular data access is a major warning sign. Employees accessing data outside their typical job responsibilities should raise immediate concern. Investigate access to sensitive information by accounts with limited or no authorization.
Monitor for multiple file downloads or printing activity from a single user, especially involving sensitive documents. Unusual access patterns often precede or accompany data exfiltration attempts, requiring immediate intervention.
Human Indicators
Employee behavior can provide clues about potential insider threats or compromised accounts. Look for signs of disgruntled employees, such as increased absenteeism or negative comments about the company. Monitor for employees circumventing security policies, such as disabling security software or sharing passwords.
Increased use of removable media, like USB drives, particularly for transferring sensitive data, should be closely scrutinized. Education and awareness are crucial; ensure employees are trained to recognize and report suspicious activity.
Communication Anomalies
Unusual email activity can signify data leaks or phishing attempts. Monitor for employees sending large attachments or forwarding sensitive information to external email addresses. Scrutinize emails with suspicious subject lines or requests, especially those asking for sensitive credentials.
Unexplained communication with known malicious domains or IP addresses is a serious warning. Investigate any instances of employees communicating with individuals or organizations not affiliated with their work duties. Implement strict email filtering and monitoring policies to prevent data leakage.
Physical Security Breaches
Physical security vulnerabilities can also contribute to unauthorized disclosure. Monitor for unauthorized access to restricted areas, especially server rooms or data centers. Review surveillance footage for suspicious behavior, such as individuals loitering near sensitive areas or attempting to bypass security measures.
Missing or misplaced devices, such as laptops or mobile phones, pose a significant security risk. Implement remote wipe capabilities and enforce strong password policies on all company-issued devices. Regularly audit physical security controls to identify and address weaknesses.
Cloud Security Issues
Cloud environments require specific security considerations. Misconfigured cloud storage buckets with public access can expose sensitive data. Monitor for unauthorized access to cloud resources, such as virtual machines or databases, and implement strong access controls.
Ensure data encryption both in transit and at rest in the cloud environment. Regularly audit cloud security configurations and implement multi-factor authentication for all cloud accounts. Utilize cloud security monitoring tools to detect and respond to threats in real-time. Microsoft Azure and Amazon Web Services offer advanced security services.
Immediate Actions Required
Upon detecting any of these indicators, immediately initiate incident response protocols. Isolate affected systems and prevent further data leakage. Contact your security team or incident response provider for assistance. Consider notifying relevant authorities if a breach is confirmed.
Regular security assessments and penetration testing are essential for identifying vulnerabilities. Implement robust data loss prevention (DLP) solutions to prevent sensitive data from leaving the organization's control. Ongoing monitoring and analysis are critical for maintaining a strong security posture.
Ongoing Investigation: Security teams are actively investigating recent anomalies. Updates will be provided as the situation evolves. Prioritize employee training on identifying and reporting suspicious activities. Data security is everyone's responsibility.