Which Of The Following Is True Of A Ddos Attack

In an era increasingly reliant on digital infrastructure, understanding the nuances of cyberattacks is paramount. Distributed Denial-of-Service (DDoS) attacks, a persistent threat to online availability, continue to evolve in sophistication and scale. This article delves into the fundamental characteristics of DDoS attacks, clarifying their nature and impact.
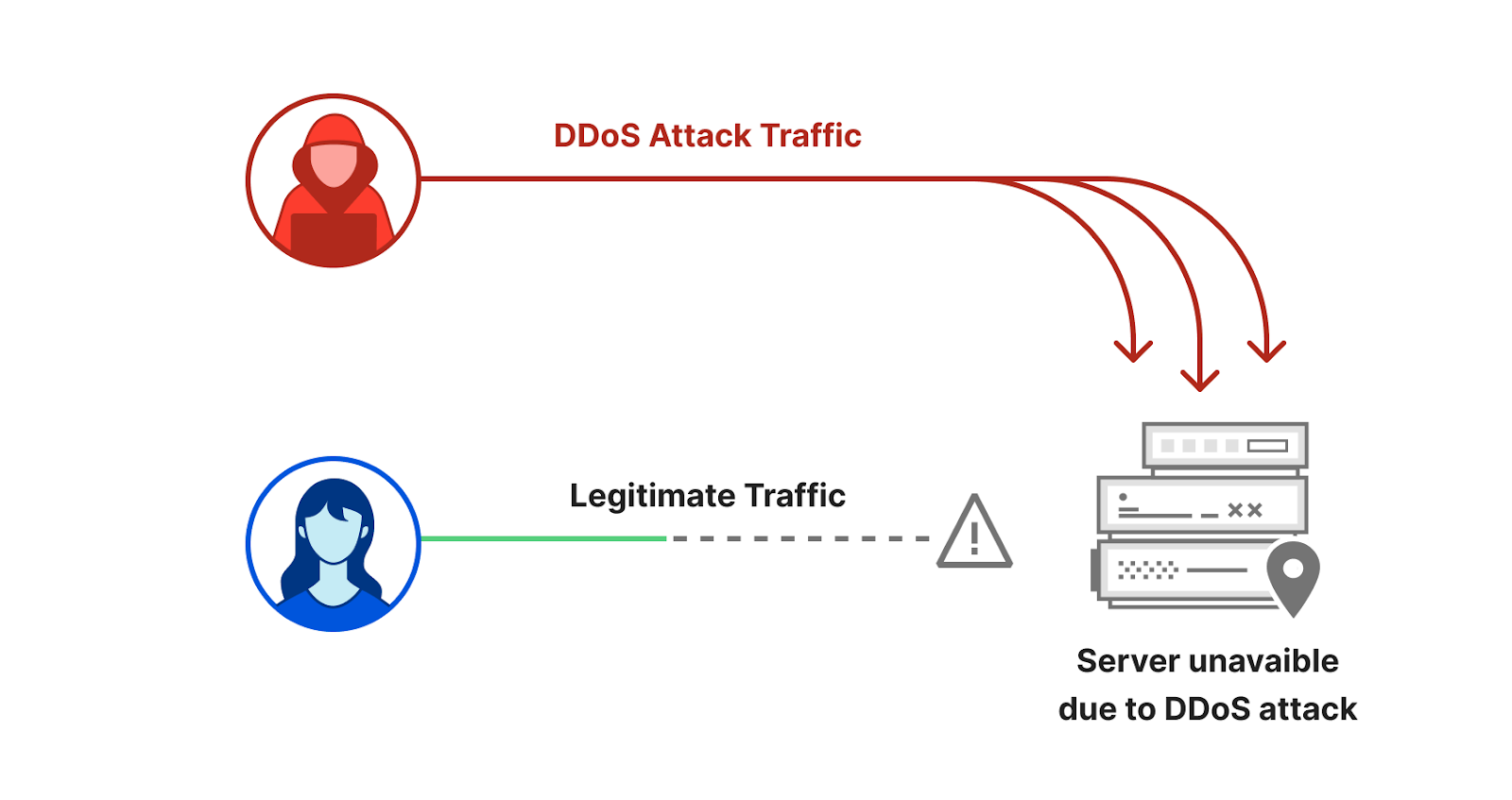
At its core, a DDoS attack aims to overwhelm a targeted server, service, or network with malicious traffic. This onslaught renders the target inaccessible to legitimate users, effectively denying service. Understanding which statements accurately describe these attacks is crucial for both individuals and organizations.
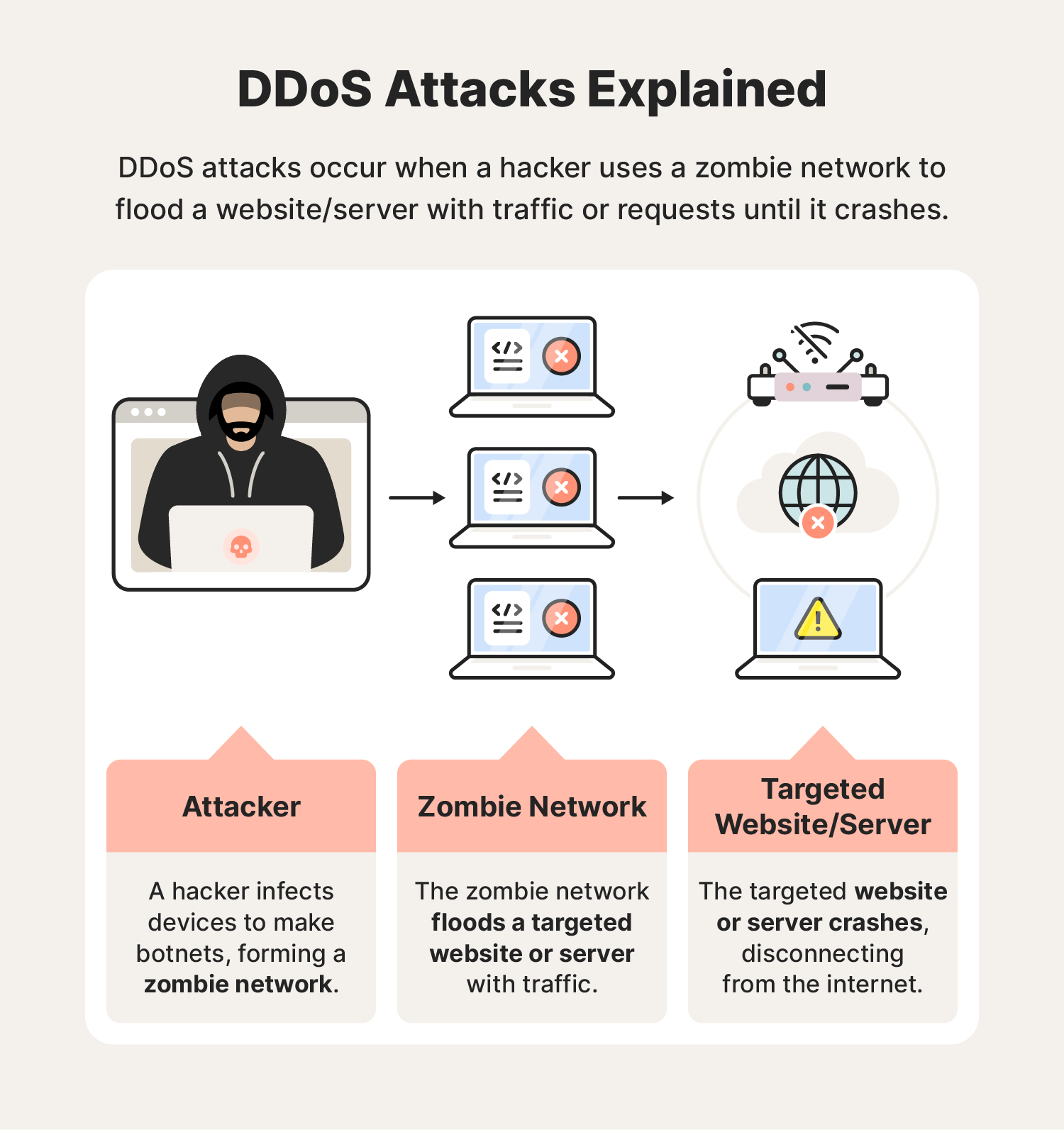
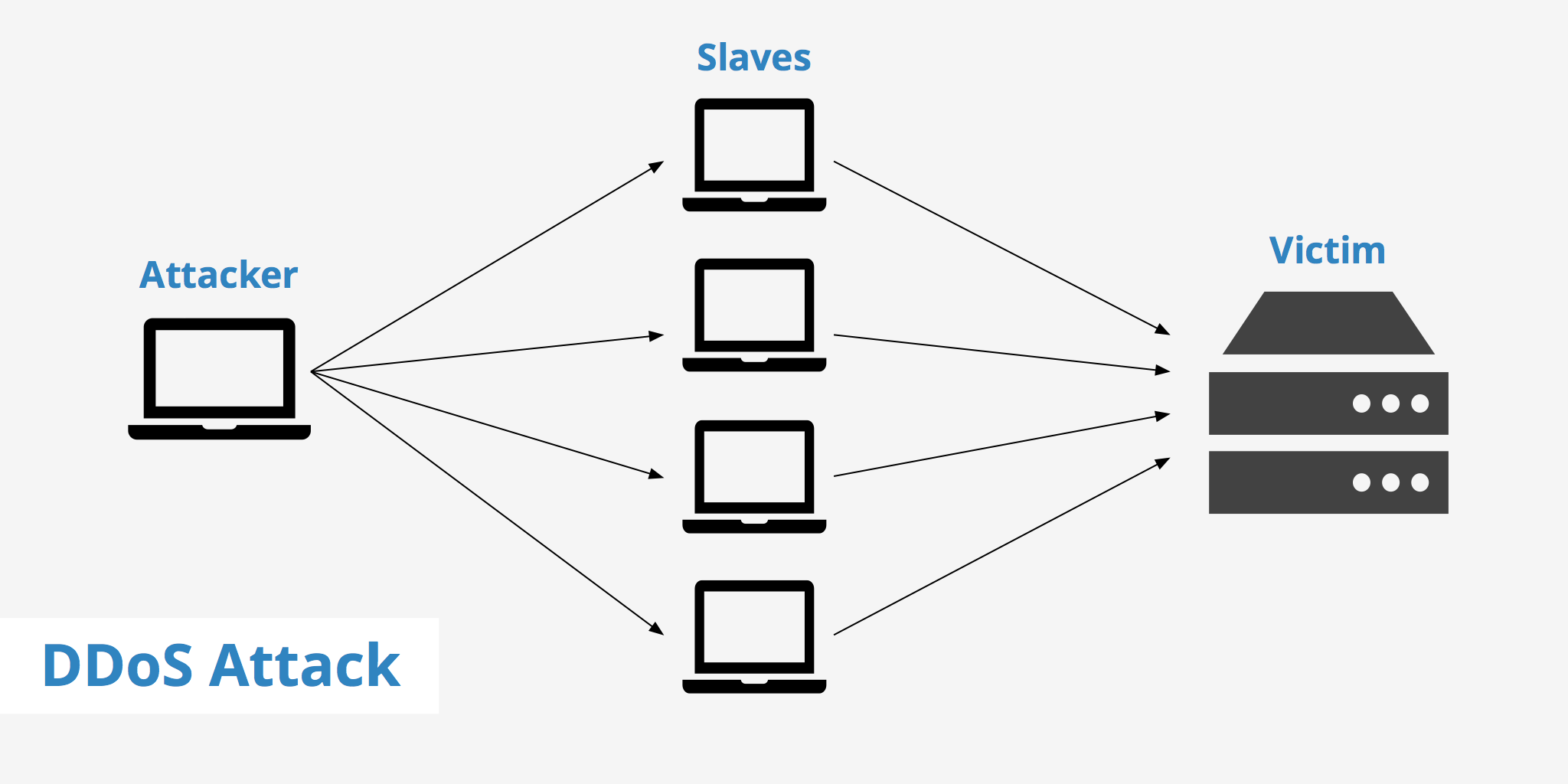
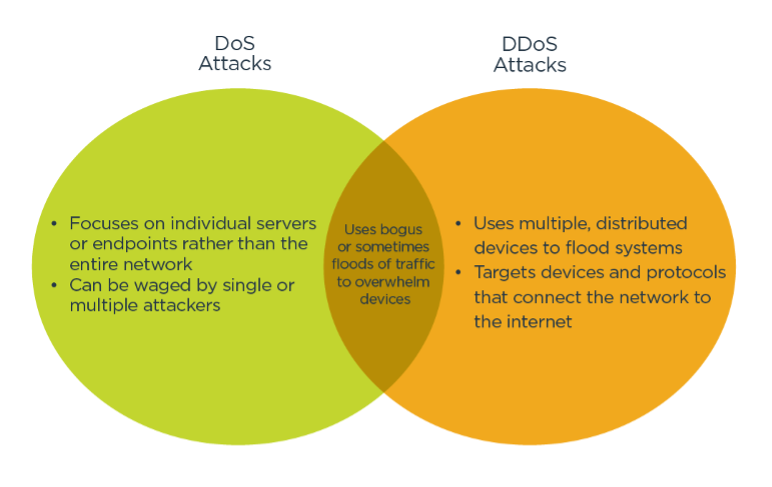
DDoS attacks are characterized by several key features. Unlike a standard Denial-of-Service (DoS) attack, which originates from a single source, a DDoS attack leverages multiple compromised systems. These systems, often forming a botnet, are controlled remotely by an attacker.
These botnets, networks of infected computers or devices, can consist of thousands, even millions, of machines. Each compromised device, without the owner's knowledge, participates in flooding the target with traffic. This distributed nature makes DDoS attacks significantly more difficult to mitigate than single-source attacks.
What is the main aim of a DDoS attack? The primary goal of a DDoS attack is to disrupt or disable the targeted service. This disruption can manifest in various ways, including slow loading times, complete unavailability, or even system crashes.
The impact of such attacks can range from minor inconvenience to significant financial losses and reputational damage. Businesses relying on online services, such as e-commerce platforms and online gaming providers, are particularly vulnerable.
Who is usually targeted in a DDoS attack? Targets vary widely depending on the attacker's motives. They may include websites, web applications, APIs, or even entire networks. Common targets include businesses, government agencies, and critical infrastructure providers.
Attacks can be motivated by various factors, including political activism (hacktivism), extortion, or simply a desire to cause disruption. Some attacks are launched by competitors seeking to sabotage a rival's operations. Understanding the attacker's motivation can aid in predicting potential targets and developing effective defense strategies.
How do DDoS attacks work? A DDoS attack typically involves several stages. First, the attacker builds a botnet by infecting numerous devices with malware. This malware allows the attacker to remotely control the infected devices.
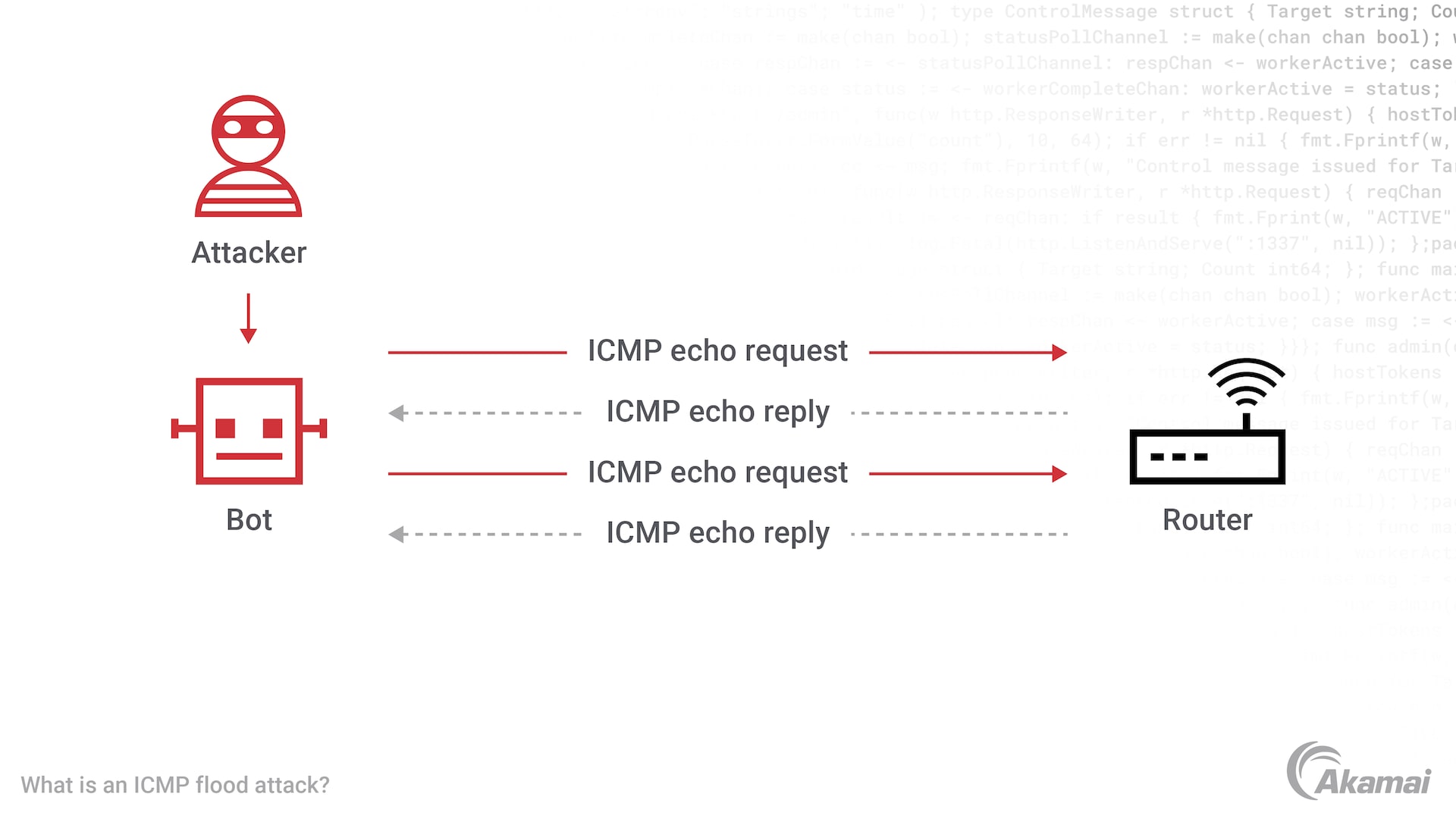
Once the botnet is established, the attacker sends commands to the infected devices, instructing them to flood the target with traffic. This traffic can take various forms, including HTTP requests, UDP packets, or SYN floods. The sheer volume of traffic overwhelms the target's resources, making it unable to respond to legitimate requests.
According to a report by Cloudflare, DDoS attacks have been increasing in frequency and sophistication. The report highlights the rise of application-layer attacks, which target specific vulnerabilities in web applications, making them more difficult to detect and mitigate.
These application-layer attacks, often referred to as Layer 7 attacks, require more sophisticated analysis and mitigation techniques than traditional network-layer attacks. They exploit vulnerabilities in the application logic, bypassing many common security measures.
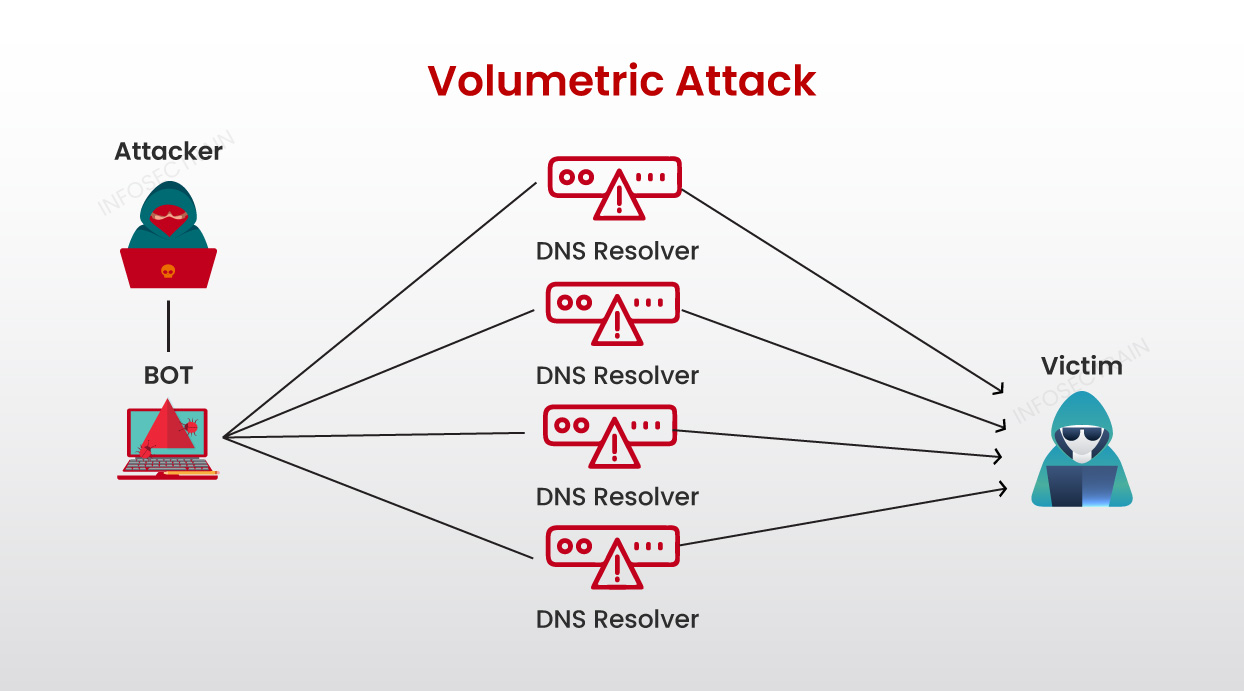
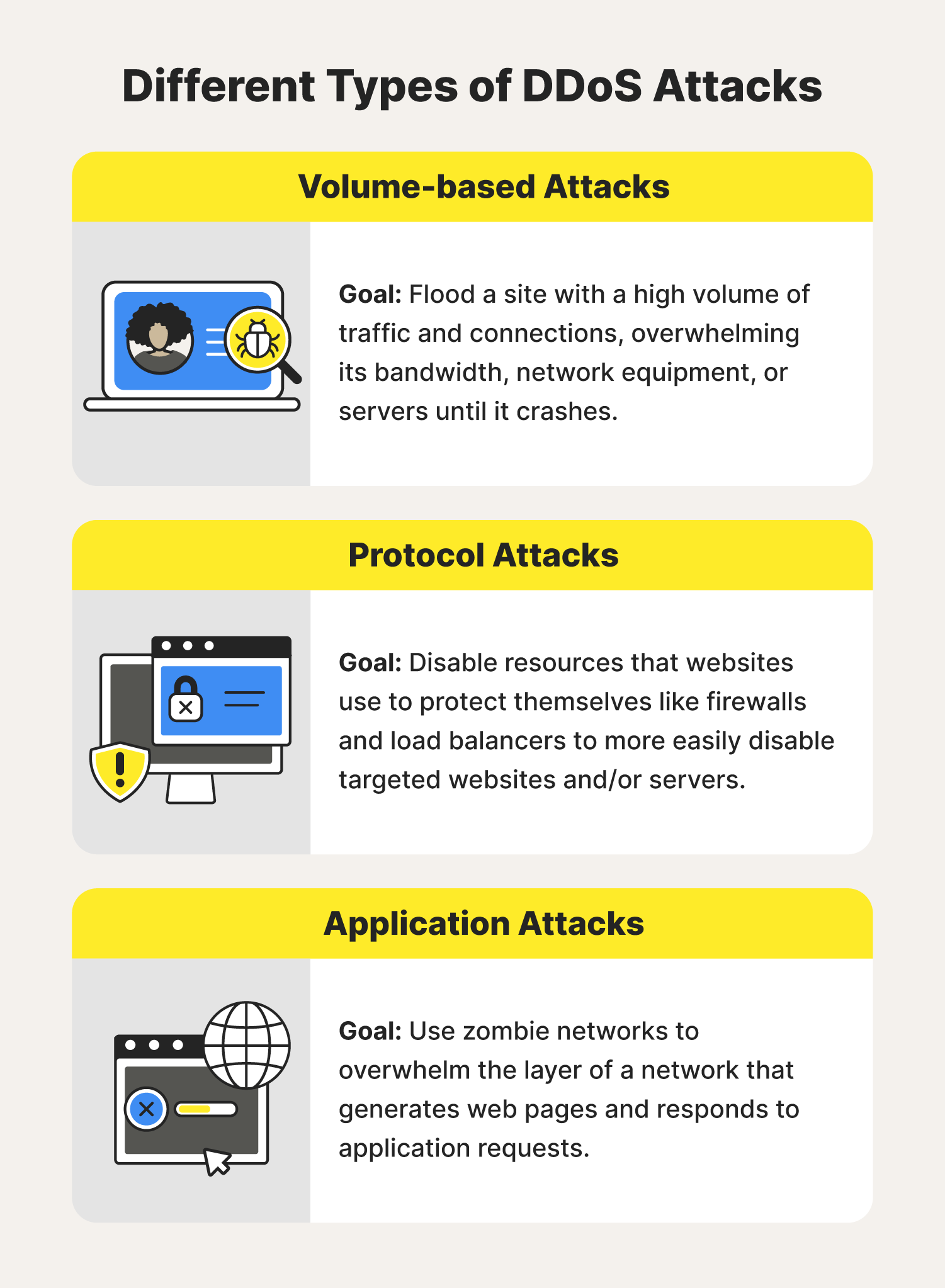
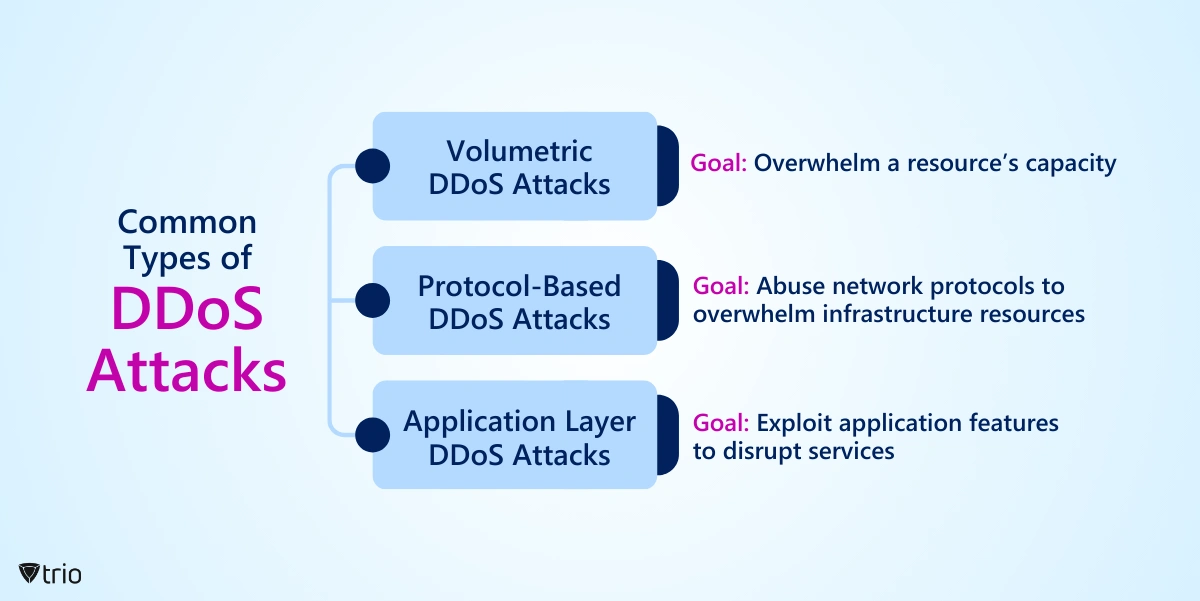
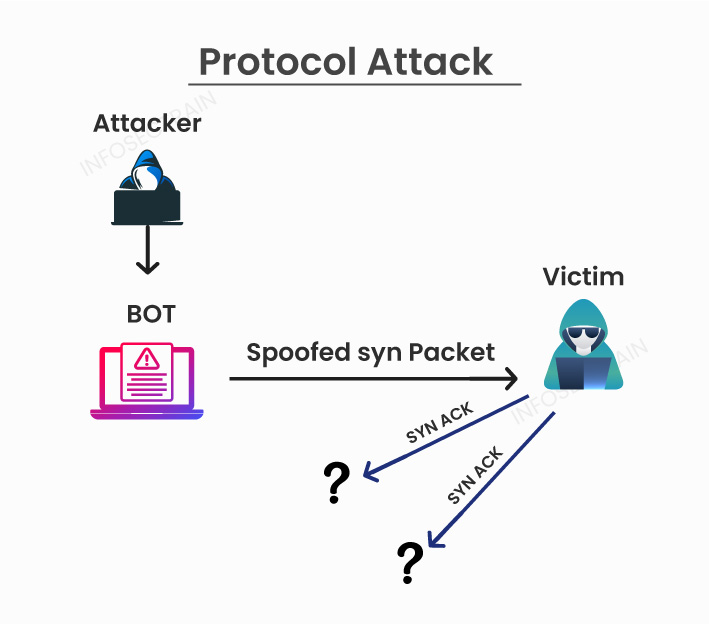
What are some common types of DDoS attacks? SYN floods, HTTP floods, and UDP floods are among the most common types of DDoS attacks. Each type exploits different vulnerabilities in network protocols or application behavior.
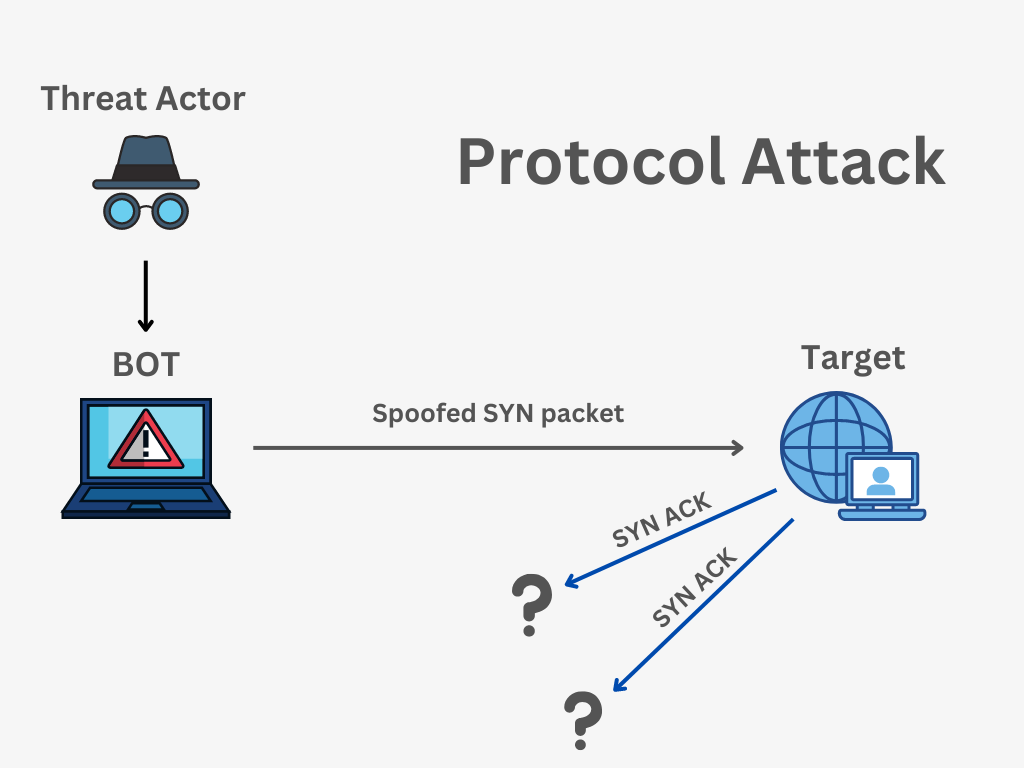
A SYN flood, for example, exploits the TCP handshake process, overwhelming the target with half-open connections. An HTTP flood floods the target with HTTP requests, consuming server resources and preventing legitimate users from accessing the website. UDP floods inundate the target with UDP packets, saturating network bandwidth.
How can organizations protect themselves from DDoS attacks? Mitigation strategies typically involve a multi-layered approach. This approach includes using firewalls, intrusion detection systems, and content delivery networks (CDNs). It also includes employing specialized DDoS mitigation services.
CDNs can absorb large volumes of traffic, distributing it across multiple servers and preventing the target from being overwhelmed. DDoS mitigation services use advanced techniques, such as traffic filtering and rate limiting, to identify and block malicious traffic.
What is the impact of a successful DDoS attack? The consequences of a successful DDoS attack can be severe. Beyond the immediate disruption of service, attacks can lead to financial losses, reputational damage, and loss of customer trust. In some cases, they can even disrupt critical infrastructure, such as power grids and communication networks.
The Cybersecurity and Infrastructure Security Agency (CISA) recommends that organizations regularly assess their vulnerability to DDoS attacks and implement appropriate security measures. CISA also provides resources and guidance on how to respond to and recover from DDoS attacks.
The rise of the Internet of Things (IoT) has further exacerbated the DDoS threat. Many IoT devices, such as security cameras and smart appliances, are poorly secured and easily compromised, making them ideal candidates for inclusion in botnets.
Securing IoT devices is therefore crucial in mitigating the risk of DDoS attacks. This includes changing default passwords, keeping firmware up to date, and implementing network segmentation to isolate vulnerable devices.
In conclusion, a DDoS attack is characterized by the use of multiple compromised systems to overwhelm a target with malicious traffic, rendering it inaccessible to legitimate users. Understanding this definition and the associated characteristics is essential for effective prevention and mitigation.