Which One Would Be Considered Critical Information

In an increasingly interconnected world saturated with information, the crucial question arises: what exactly constitutes critical information? Defining this term is paramount as it dictates resource allocation, security protocols, and, ultimately, the ability of individuals, organizations, and governments to make informed decisions and safeguard essential assets.
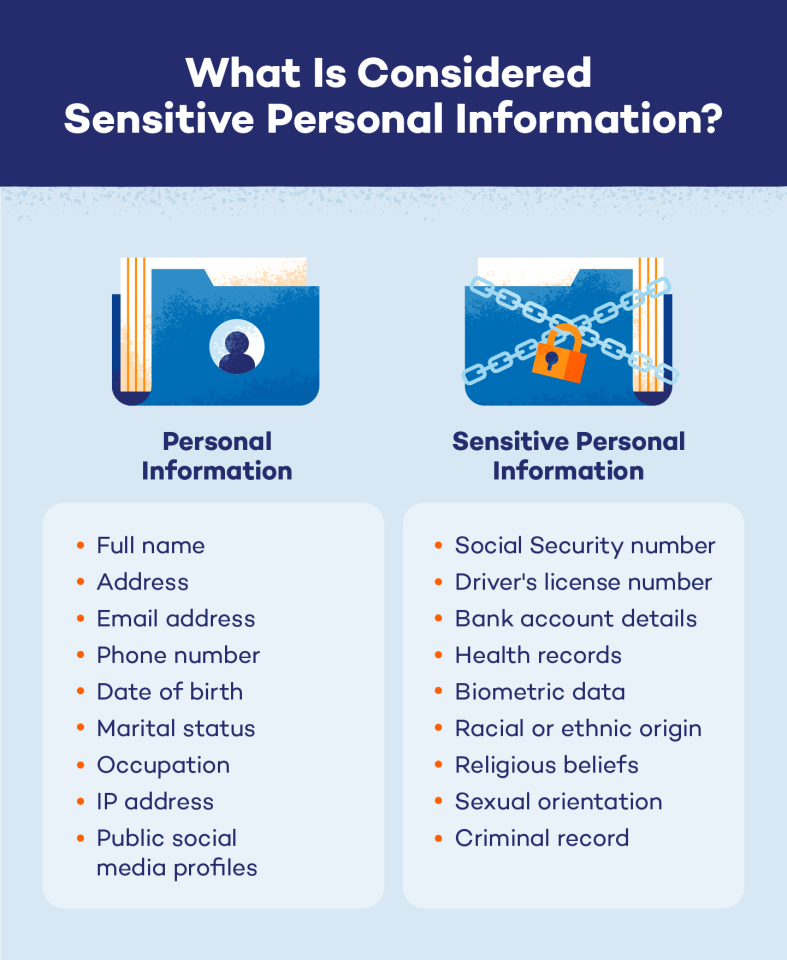
Critical information, in essence, is any data, knowledge, or intelligence that is vital to the successful operation, security, or well-being of an entity. It is information whose compromise, loss, or unavailability could have significant, negative consequences. Understanding the nuances of critical information requires examining its diverse forms, its dependence on context, and the methods used to protect it.
Defining Critical Information: A Multifaceted Approach
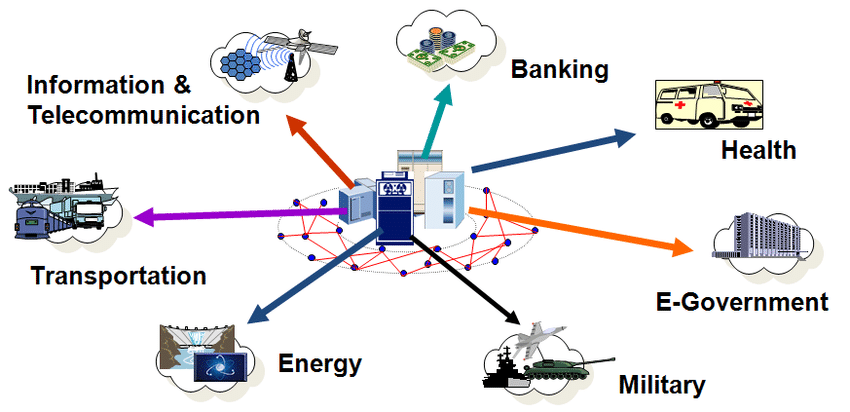
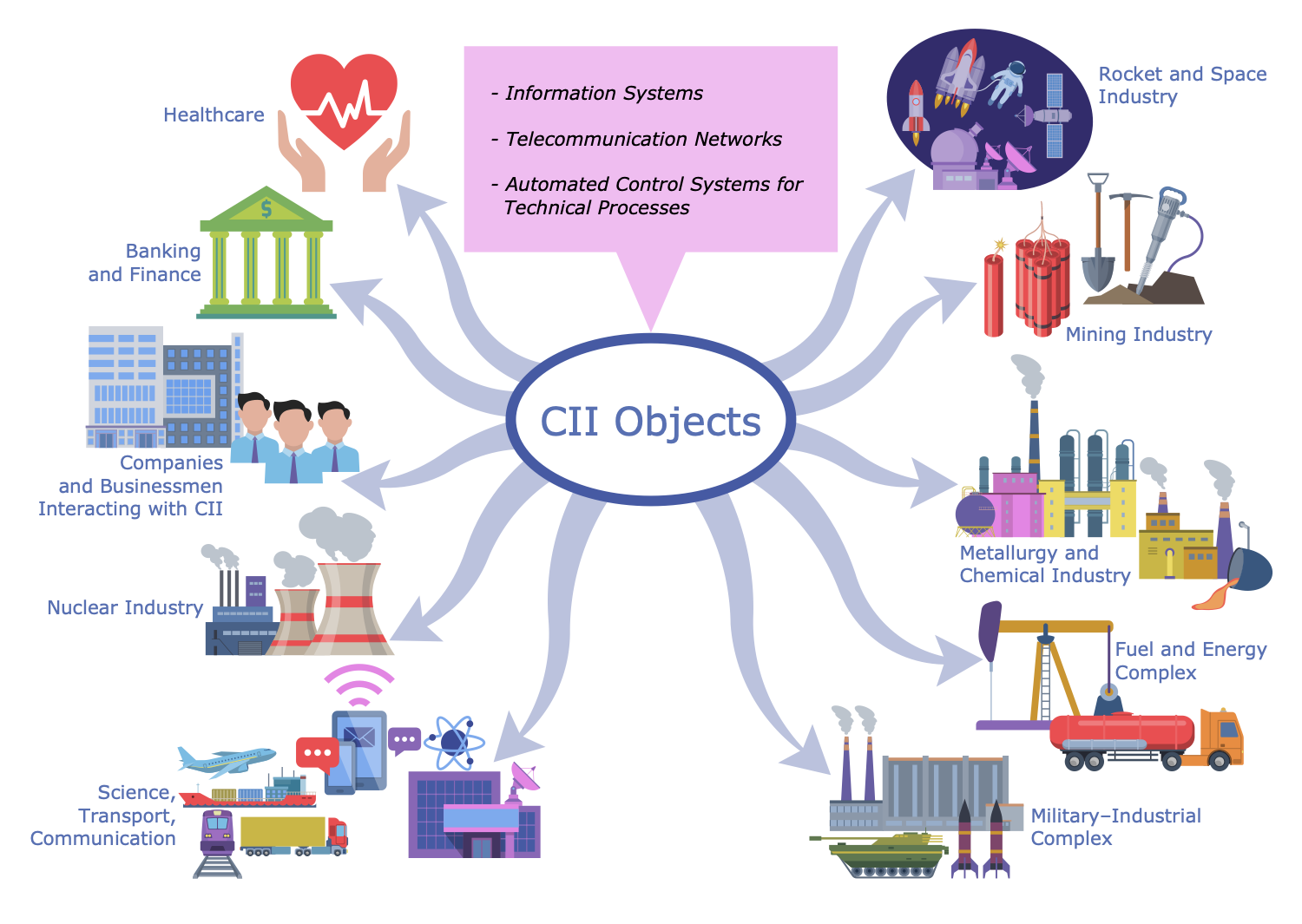
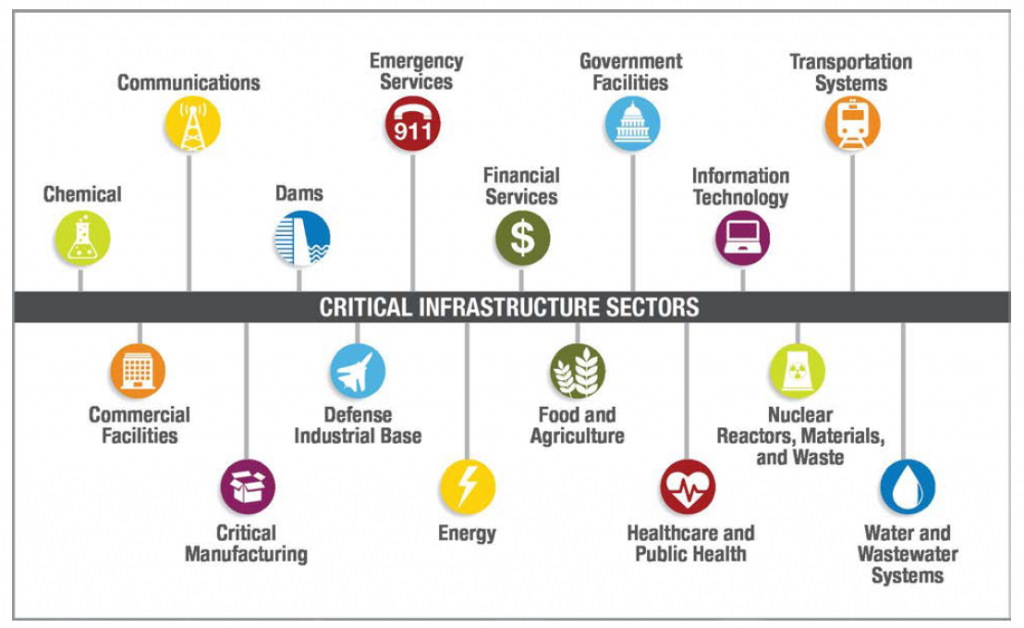
The definition of critical information varies depending on the context. For a hospital, it could be patient records, operating procedures, and emergency response plans. For a financial institution, it might include transaction data, security protocols, and customer information.
For a government, it extends to national security intelligence, infrastructure schematics, and economic forecasts. The common thread is the potential for serious damage should this information fall into the wrong hands or become inaccessible.
Key Characteristics of Critical Information
Several characteristics distinguish critical information from general data. Confidentiality is often a primary concern, as unauthorized access can lead to espionage, fraud, or reputational damage.
Integrity is equally important; the accuracy and completeness of the information must be maintained to ensure reliable decision-making. Availability ensures that authorized users can access the information when needed, especially during crises.
Timeliness becomes important. Information quickly loses its value when it is no longer current or relevant.
Examples Across Sectors
Consider the energy sector. Schematics of power grids, control systems, and emergency shutdown procedures are undoubtedly critical information. A cyberattack targeting these systems could disrupt power supply to entire cities, potentially causing widespread chaos and economic damage.
In the healthcare industry, patient medical records are highly sensitive. Data breaches not only violate privacy regulations but can also expose individuals to identity theft and medical fraud.
The financial sector is particularly vulnerable. Proprietary trading algorithms, client account details, and security keys are prime targets for cybercriminals. Breaches can lead to massive financial losses and erode public trust.
The Role of Threat Assessment
Identifying critical information involves conducting a thorough threat assessment. This process entails identifying potential adversaries, assessing their capabilities and motivations, and understanding the vulnerabilities in existing systems.
This process enables organizations to prioritize the protection of their most valuable assets. Risk management frameworks, such as those provided by the National Institute of Standards and Technology (NIST), offer guidance on identifying, assessing, and mitigating risks associated with critical information.
Protection Strategies
Protecting critical information requires a multi-layered approach. This includes implementing robust cybersecurity measures, such as firewalls, intrusion detection systems, and data encryption.
Physical security measures are also essential, particularly for protecting servers and data centers. Employee training on data security protocols is crucial to prevent human error, which is often a major cause of data breaches.
Regular security audits and vulnerability assessments can help identify weaknesses in systems. Developing incident response plans enables organizations to quickly and effectively respond to security breaches.
The Human Element
Beyond technological safeguards, the human element is crucial. Employees must understand the importance of safeguarding critical information and be vigilant against social engineering tactics.
A culture of security awareness is essential. This can be fostered through training programs, regular reminders, and clear policies.
For example, Whistleblower policies empower employees to report potential security threats without fear of retaliation. This strengthens the organization's overall security posture.
Legal and Regulatory Landscape
Numerous laws and regulations govern the protection of critical information. The Health Insurance Portability and Accountability Act (HIPAA) protects patient medical information. The Gramm-Leach-Bliley Act (GLBA) regulates the handling of financial information.
The European Union's General Data Protection Regulation (GDPR) sets stringent requirements for data protection and privacy. Organizations must comply with these regulations to avoid costly penalties and legal repercussions.
Looking Ahead
As technology evolves, so do the threats to critical information. The rise of artificial intelligence (AI) and machine learning (ML) presents both opportunities and challenges.
AI can be used to enhance security measures by detecting anomalies and predicting potential threats. It can also be used by malicious actors to develop sophisticated cyberattacks.
The ongoing challenge is to stay ahead of these evolving threats and continuously adapt security strategies to protect critical information. This proactive approach is essential for maintaining security, competitiveness, and public trust in an increasingly digital world.