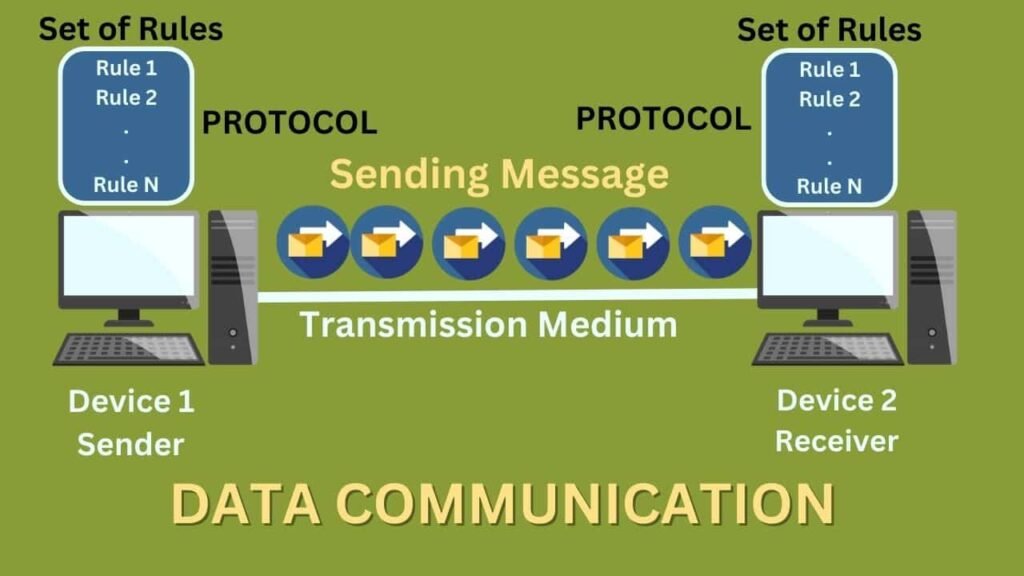
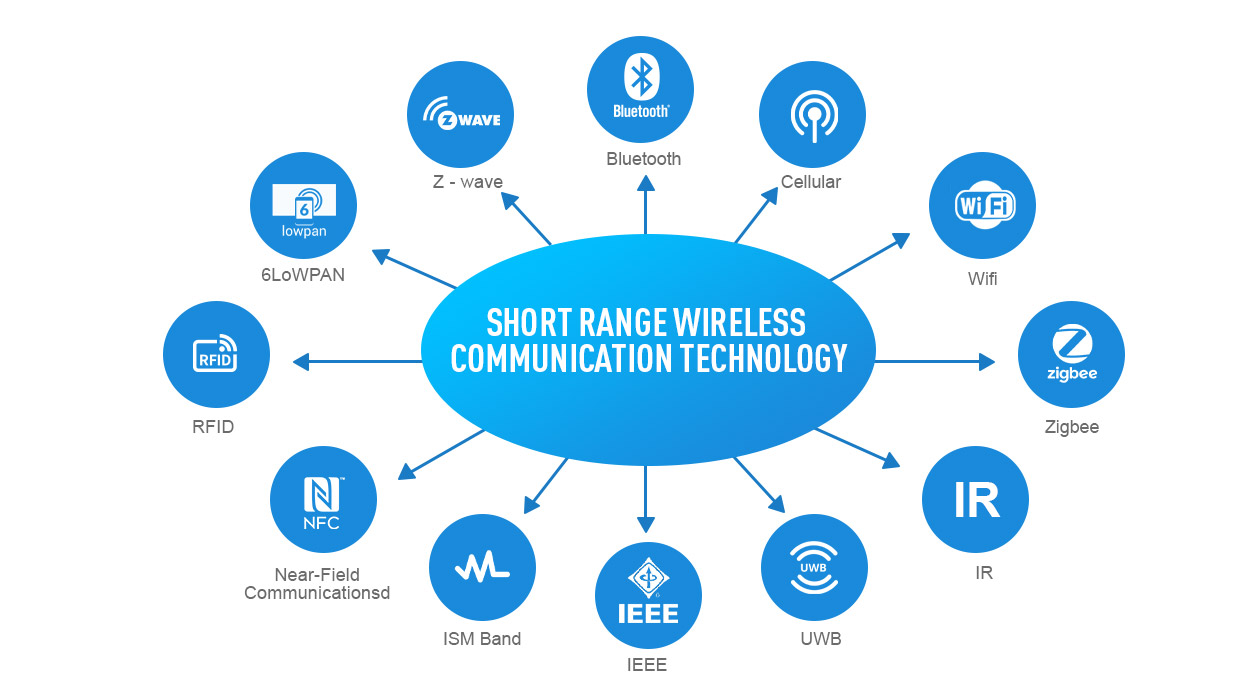
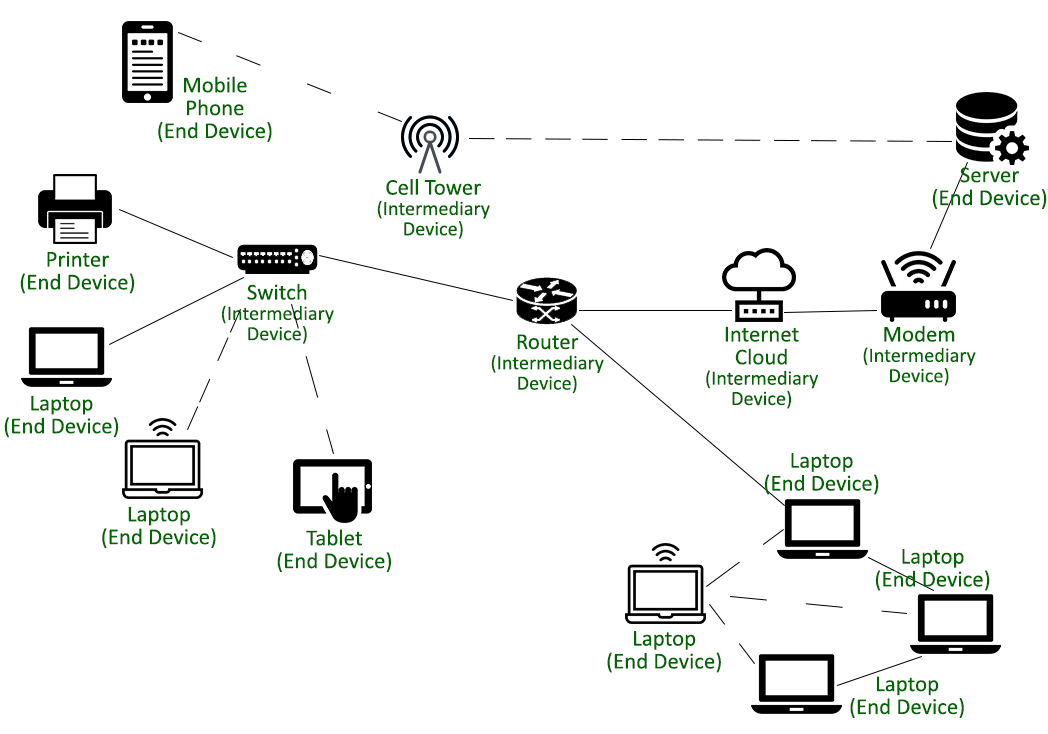
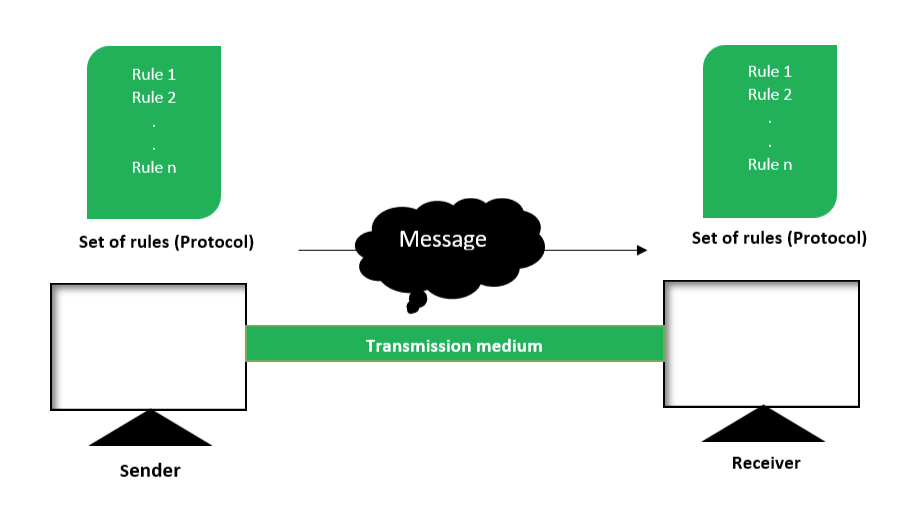
Ensure You Record Data About Your Communication Devices
In an increasingly interconnected world, experts are urging individuals and organizations to meticulously record data pertaining to their communication devices, citing enhanced security, streamlined management, and improved accountability as key benefits.
This recommendation, while seemingly simple, has far-reaching implications for both personal and professional spheres, impacting everything from data breach response to legal compliance.
The Importance of Detailed Device Records
The call to action focuses on maintaining comprehensive records of all communication devices, including smartphones, tablets, laptops, and desktop computers. These records should encompass details such as device type, serial number, operating system, installed software, user assignments, and dates of acquisition and disposal.
Dr. Anya Sharma, a cybersecurity consultant at TechSafe Solutions, emphasized the importance of this practice. "Having a detailed inventory of your communication devices is the first line of defense against potential security threats," she stated in a recent interview.
"Without this information, it's incredibly difficult to track devices, manage software updates, and respond effectively to security incidents."
Why Now? The Rising Tide of Cyber Threats
The urgency of this recommendation is underscored by the escalating frequency and sophistication of cyberattacks. Data breaches, ransomware attacks, and phishing scams are becoming increasingly common, targeting both individuals and organizations of all sizes.
According to a report released last month by the Cybersecurity and Infrastructure Security Agency (CISA), the number of reported cyber incidents increased by 20% in the past year alone.
Maintaining accurate device records can significantly enhance an organization's ability to detect and respond to such incidents.
For example, if a device is compromised, knowing its serial number and installed software allows security teams to quickly isolate the affected device and prevent the spread of malware.
Similarly, knowing the assigned user helps to determine the scope of the breach and identify potentially exposed data.
Beyond Security: Compliance and Management
The benefits of detailed device records extend beyond cybersecurity. In many industries, regulatory compliance requires organizations to maintain accurate inventories of their IT assets.
For instance, organizations subject to the Health Insurance Portability and Accountability Act (HIPAA) must implement security measures to protect patient data, including tracking the devices used to access that data. Failure to comply with these regulations can result in significant fines and penalties.
Furthermore, comprehensive device records can streamline IT management processes. Knowing the age and configuration of each device allows IT departments to proactively manage software updates, patch vulnerabilities, and plan for hardware upgrades.
This can lead to improved efficiency, reduced downtime, and lower overall IT costs.
"Think of it like keeping a meticulous logbook for your car," explains David Chen, an IT manager at a large manufacturing firm. "You need to know when it was last serviced, what parts were replaced, and who is driving it. Your communication devices are no different."
Practical Steps for Implementation
Implementing a system for recording device data doesn't have to be complex. Start by creating a simple spreadsheet or database to track key information for each device.
Consider using a mobile device management (MDM) solution. Many MDM solutions automate the process of collecting and managing device data, providing real-time visibility into the organization's device inventory.
Regularly review and update device records to ensure accuracy. This should be done at least quarterly, or more frequently if there are significant changes to the device inventory.
Train employees on the importance of device security and the proper procedures for reporting lost or stolen devices.
This includes informing them about phishing scams and malicious websites that could compromise their devices.
A Human Angle: Protecting Personal Data
While the focus is often on organizational benefits, the importance of recording device data extends to individual users as well.
Imagine losing your smartphone and having no record of its serial number or installed apps. Retrieving the device, remotely wiping its data, or reporting it to the authorities becomes significantly more difficult.
By maintaining a simple record of your personal devices, you can better protect your data and minimize the impact of theft or loss.
Consider using a password manager to securely store your login credentials and enable two-factor authentication wherever possible.
This will add an extra layer of security to your accounts and make it more difficult for unauthorized users to access your data.
The Bottom Line: A Proactive Approach
In an era of increasing cyber threats and complex regulatory requirements, recording data about your communication devices is no longer optional. It's a necessary step for protecting your data, streamlining IT management, and ensuring compliance.
By taking a proactive approach to device management, individuals and organizations can significantly reduce their risk of security breaches and improve their overall cybersecurity posture.
The time to start recording your device data is now.