How To Find Keylogger On Iphone

Imagine a quiet evening, phone in hand, casually scrolling through messages from loved ones. A subtle unease creeps in; a nagging feeling that something isn't quite right. The battery drains faster than usual, or a strange new app lingers on the home screen, unfamiliar and unwelcome. Could someone be watching? This fear, however unsettling, is a valid concern in our increasingly connected world.
This article is your comprehensive guide to identifying potential keyloggers or other surveillance software on your iPhone. We'll explore telltale signs, practical steps you can take to investigate, and actions to secure your device and regain peace of mind. While the chances of a keylogger being present are relatively low, knowledge is power, and knowing how to protect yourself is paramount.
Understanding the Threat: Keyloggers and iPhones
A keylogger, at its core, is a piece of software or hardware designed to record keystrokes. The intention is usually malicious, aiming to capture passwords, financial information, or personal correspondence. On iPhones, which are known for their robust security, keyloggers are less prevalent than on other devices.
Apple's iOS operating system implements several security measures that make it difficult, though not impossible, for keyloggers to be installed without the user's knowledge. Jailbreaking, a process that removes software restrictions imposed by Apple, significantly increases the risk of keylogger installation. It bypasses Apple's security protocols, leaving the device vulnerable.
Recognizing the Warning Signs
Several clues may indicate the presence of a keylogger or other spyware on your iPhone. It’s crucial to note that these signs can also be attributed to other factors, such as a buggy app or an aging battery. However, if several of these symptoms occur simultaneously, further investigation is warranted.
Unexplained Battery Drain
A sudden and noticeable decrease in battery life, even with normal usage, could be a red flag. Keyloggers and spyware often run in the background, constantly recording data and consuming power. This can lead to a significant drain on your battery, particularly if the phone is idle.
Increased Data Usage
Similarly, a spike in data usage that doesn't correlate with your typical online activities might suggest suspicious activity. Keyloggers transmit the recorded data to a remote server, which requires an internet connection. Check your data usage statistics in your iPhone's settings to monitor any unusual patterns.
Unfamiliar Apps
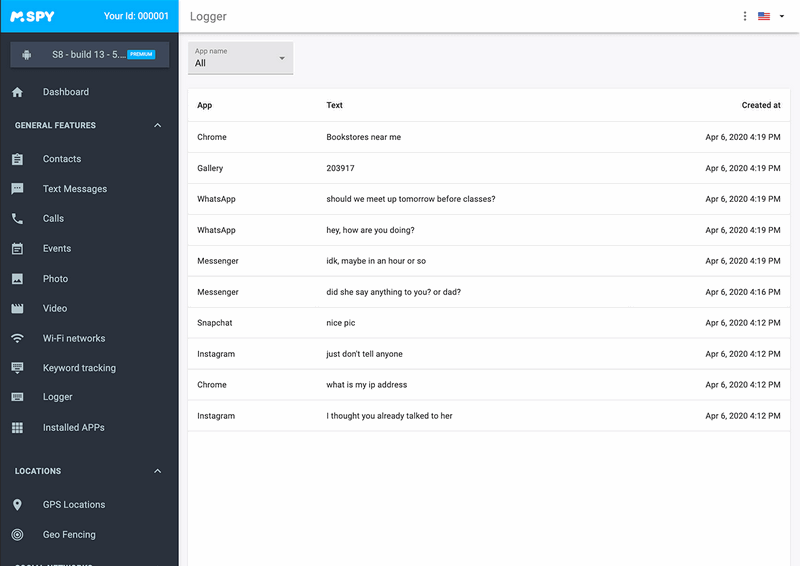
Browse through your iPhone's home screens and app library, paying close attention to any applications you don't recognize installing. Spyware is often disguised as legitimate apps, with generic or misleading names and icons. If you find something suspicious, research it online to verify its authenticity.
Strange Pop-Ups and Messages
Unexpected pop-up ads, error messages, or unusual SMS messages could indicate the presence of malware. Keyloggers sometimes interfere with the normal operation of the device, causing these anomalies. Be cautious and avoid clicking on any links within these messages.
Overheating
If your iPhone frequently overheats, even when not in use, it could be due to background processes consuming excessive resources. Keyloggers and spyware contribute to this problem, placing a strain on the device's processor.
Unusual Activity on Linked Accounts
Keep a close eye on your online accounts, such as email, social media, and banking, for any unauthorized access or suspicious activity. Keyloggers are often used to steal login credentials, which can then be used to compromise your accounts.
Investigating Your iPhone: A Step-by-Step Guide
If you suspect that your iPhone may be compromised, follow these steps to investigate further.
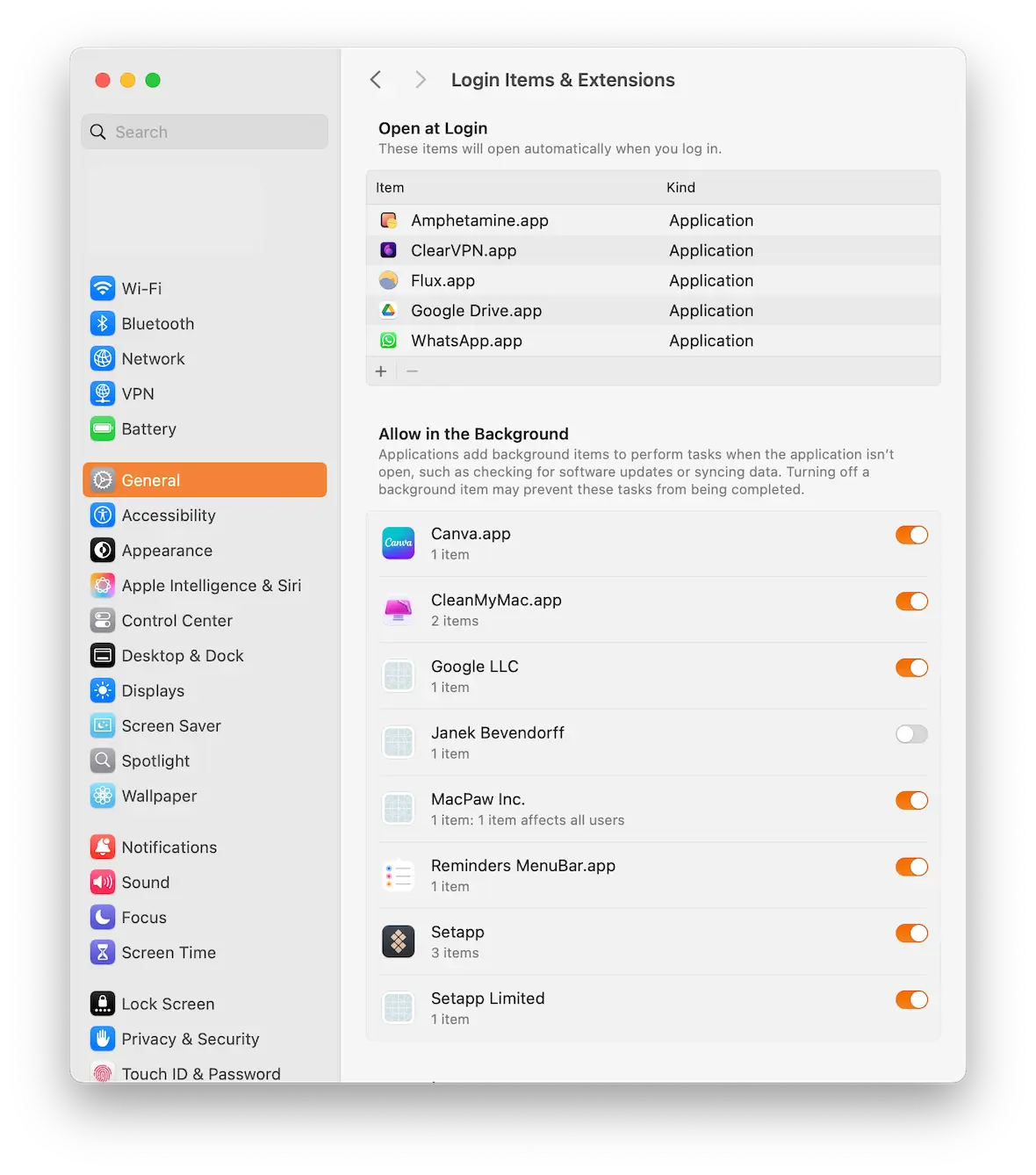
Check Installed Profiles
Configuration profiles are used to manage settings and restrictions on iPhones. Malicious profiles can be used to install spyware or modify device behavior. Go to Settings > General > VPN & Device Management. If you see any profiles you don't recognize or didn't intentionally install, remove them immediately.
Review App Permissions
Carefully examine the permissions granted to each app on your iPhone. Some apps may request access to sensitive data, such as your location, contacts, or microphone, which is unnecessary for their functionality. Go to Settings > Privacy & Security to review and adjust app permissions as needed.
Scan for Jailbreaking
If you didn't intentionally jailbreak your iPhone, but suspect it may have been done without your knowledge, look for the Cydia app icon. Cydia is a package manager used to install software on jailbroken devices. If you find Cydia, it's a strong indication that your iPhone has been jailbroken, which increases the risk of keyloggers and other malware.
Use a Mobile Security App
Several reputable mobile security apps can scan your iPhone for malware and other security threats. While iPhones are generally secure, these apps provide an additional layer of protection. Some popular options include Norton Mobile Security and McAfee Mobile Security. Be sure to download apps only from the official App Store to avoid installing malicious software.
Monitor Network Activity
While more technical, monitoring network activity can reveal suspicious connections or data transfers. Specialized apps and tools can capture and analyze network traffic, but this requires some technical expertise. Consult with a cybersecurity professional if you need assistance with this process.
Taking Action: Removing and Preventing Keyloggers
If you find evidence of a keylogger or other malware on your iPhone, take immediate action to remove it and prevent future infections.
Update to the Latest iOS Version
Apple regularly releases software updates that include security patches to address vulnerabilities and protect against new threats. Ensure your iPhone is running the latest version of iOS to benefit from these security enhancements. Go to Settings > General > Software Update to check for updates.
Remove Suspicious Apps and Profiles
As mentioned earlier, immediately remove any unfamiliar apps or configuration profiles you find on your iPhone. This can often remove the keylogger itself or prevent it from functioning properly.
Change Passwords
If you suspect your iPhone has been compromised, change all of your important passwords, including your Apple ID, email, social media, and banking passwords. Choose strong, unique passwords for each account and consider using a password manager to store them securely.
Restore from Backup (with Caution)
Restoring your iPhone from a backup can remove malware, but it's crucial to use a backup that was created before the infection occurred. If you restore from a backup that contains the keylogger, you'll simply reinstall the problem. If unsure, it’s better to restore to factory settings and set up the phone as new.
Erase All Content and Settings
The most drastic, but often most effective, solution is to erase all content and settings on your iPhone. This will restore the device to its factory default state, removing any malware or suspicious software. Go to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings. Be sure to back up your important data before performing this step, but again, exercise caution regarding when the backup was made.
Contact Apple Support
If you're unable to remove the keylogger or have further concerns, contact Apple Support for assistance. They can provide expert guidance and help you troubleshoot the problem.
Preventive Measures: Staying Safe in the Future
Prevention is always better than cure. Here are some proactive steps you can take to protect your iPhone from keyloggers and other security threats.
Avoid Jailbreaking
Unless you have a compelling reason to jailbreak your iPhone, avoid doing so. Jailbreaking removes Apple's security restrictions and makes your device more vulnerable to malware.
Be Careful What You Click
Exercise caution when clicking on links in emails, SMS messages, or online advertisements. Phishing attacks are a common way to trick users into installing malware.
Download Apps from the App Store Only
Only download apps from the official App Store. Apple rigorously reviews apps before they are made available for download, reducing the risk of installing malicious software.
Use a Strong Passcode and Enable Face ID/Touch ID
A strong passcode and biometric authentication (Face ID or Touch ID) can prevent unauthorized access to your iPhone and protect your data.
Enable Two-Factor Authentication
Enable two-factor authentication for all of your important online accounts. This adds an extra layer of security by requiring a verification code in addition to your password.
Regularly Review Your iPhone's Security Settings
Take the time to regularly review your iPhone's security settings and ensure that all of the recommended security features are enabled. This will help you stay one step ahead of potential threats.
Conclusion
The fear of a keylogger lurking on your iPhone is understandable, but with knowledge and vigilance, you can protect yourself. By understanding the warning signs, taking proactive steps to investigate, and implementing preventive measures, you can significantly reduce your risk. Remember that security is an ongoing process, not a one-time fix. Stay informed, stay cautious, and enjoy the peace of mind that comes with knowing you've taken steps to secure your digital life.