How To Improve Information Security

Imagine walking into a cozy coffee shop, the aroma of freshly brewed beans filling the air. You connect to the Wi-Fi, eager to catch up on emails or browse the news. But lurking beneath the surface of that convenience is a complex world of digital threats, waiting to exploit vulnerabilities. Are you truly protected?
This article serves as your friendly guide to navigate the often-intimidating landscape of information security. It offers practical, actionable steps you can take to safeguard your personal and professional data from ever-evolving cyber threats.
Understanding the Landscape
Information security, often referred to as cybersecurity, is no longer just the concern of tech companies and government agencies. It's a crucial aspect of modern life, impacting everyone from individuals managing their personal finances online to small businesses storing customer data. Cybersecurity Ventures predicts that global damages from cybercrime will reach $10.5 trillion annually by 2025, highlighting the urgent need for proactive measures.
The Importance of a Strong Foundation
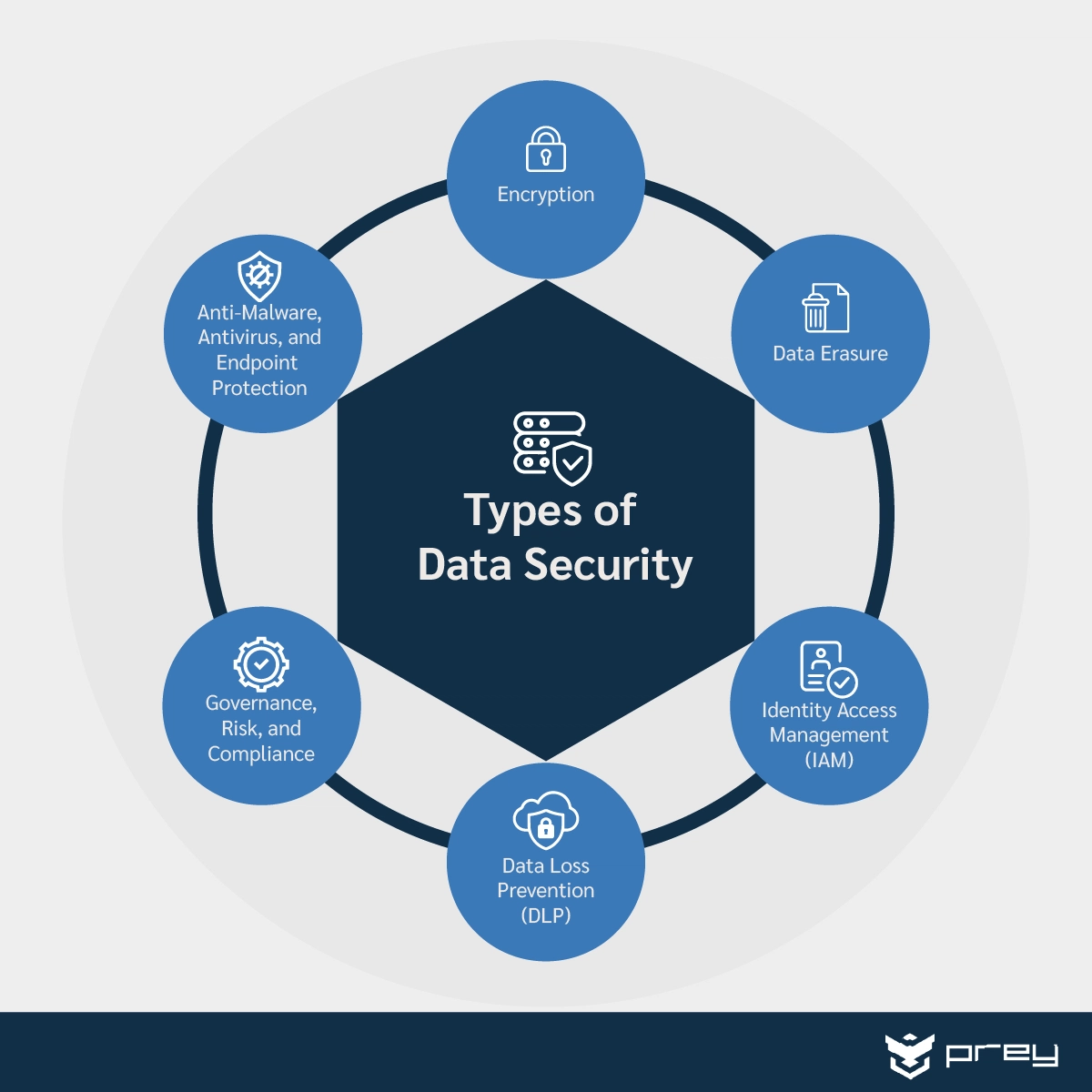
The bedrock of robust information security is built on a few key principles: confidentiality, integrity, and availability (CIA). These principles ensure that information is protected from unauthorized access, alteration, and destruction, respectively.
A strong password policy is the first line of defense. Encourage the use of complex passwords composed of a mix of upper and lowercase letters, numbers, and symbols.
Implementing Practical Strategies
Beyond strong passwords, Multi-Factor Authentication (MFA) adds an extra layer of security. MFA requires users to provide multiple verification factors, such as a password and a code sent to their phone, making it significantly harder for attackers to gain access.
Regularly updating software is paramount. Software updates often include security patches that address known vulnerabilities. Neglecting updates leaves systems exposed to potential exploitation.
Be wary of phishing attempts. Phishing emails, disguised as legitimate communications, trick users into revealing sensitive information. Always verify the sender's address and be cautious of suspicious links or attachments.
Consider using a password manager. These tools generate and store strong, unique passwords for all your accounts, alleviating the burden of remembering them all.
Protecting Your Devices
Securing your devices is equally important. Ensure your computer, smartphone, and tablet have up-to-date antivirus software. Regularly scan for malware and remove any suspicious files.
Enabling firewalls provides a barrier against unauthorized network access. Most operating systems have built-in firewalls that can be configured to block malicious traffic.
When using public Wi-Fi networks, be mindful of the risks. Avoid accessing sensitive information, such as bank accounts, without using a Virtual Private Network (VPN) to encrypt your traffic.
Education and Awareness
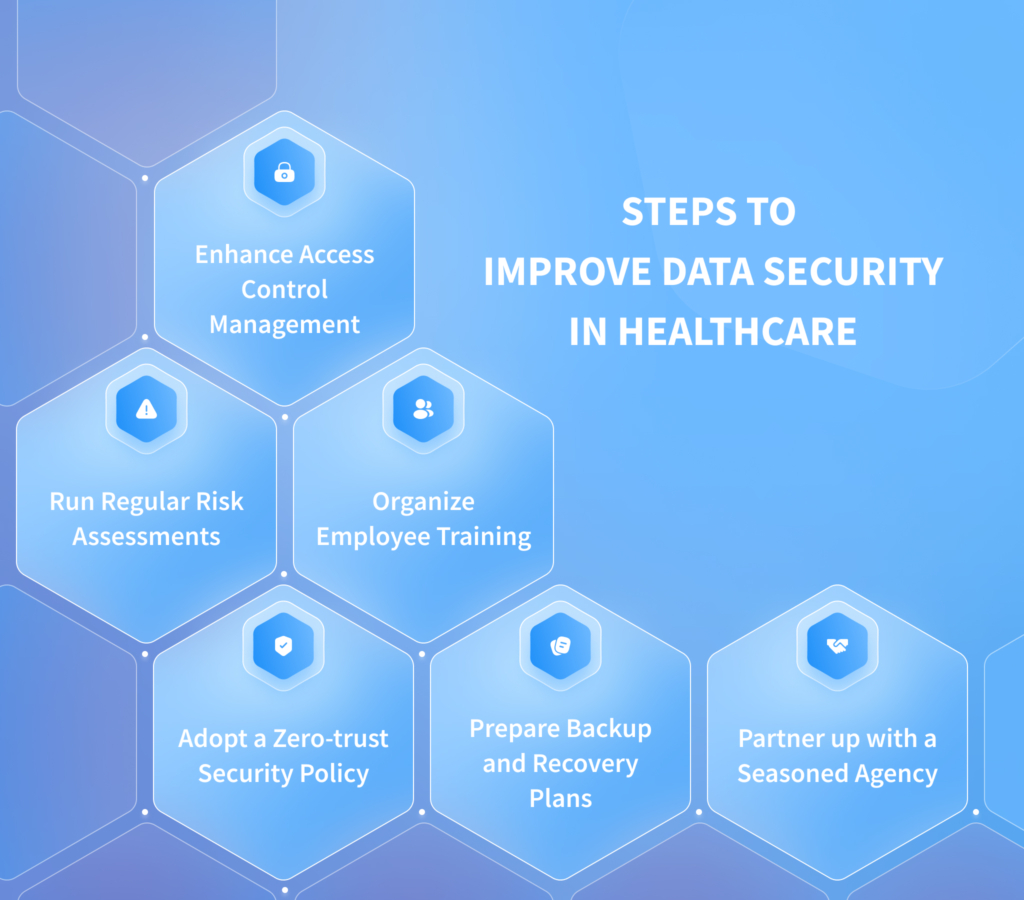
Information security isn't just about technology; it's also about people. Regular training and awareness programs can educate users about potential threats and best practices.
These programs should cover topics such as phishing awareness, password security, and safe browsing habits. According to a report by the National Institute of Standards and Technology (NIST), "human error" is a significant factor in many security breaches.
Staying Ahead of the Curve
The threat landscape is constantly evolving. It's crucial to stay informed about the latest threats and vulnerabilities by following cybersecurity news and blogs.
Implementing a layered security approach provides multiple defenses against various attacks. This approach combines technical controls with human awareness to create a more resilient security posture.
Looking Forward
Improving information security is an ongoing journey, not a destination. It requires vigilance, commitment, and a willingness to adapt to new challenges. By embracing these strategies, you can create a safer digital environment for yourself and those around you. You will be like a digital guardian, protecting your own information and empowering others to do the same.