How To Unlock Administrator Password
The vulnerability of computer systems to unauthorized access remains a critical concern for individuals, businesses, and governments alike. The unauthorized acquisition of administrator privileges, in particular, poses a significant security risk, potentially leading to data breaches, system compromise, and operational disruption.
This article addresses the crucial issue of understanding how individuals might attempt to bypass or unlock administrator passwords, focusing on the technical aspects and potential countermeasures, while emphasizing the importance of ethical and legal considerations. We will explore methods employed, potential vulnerabilities, and strategies for safeguarding systems against malicious actors, acknowledging that this information must be used responsibly and solely for preventative and educational purposes.
Understanding the Administrator Account
The administrator account is the key to controlling a computer system. It holds the highest level of privileges, enabling complete access and modification rights.
This includes installing software, changing system settings, and accessing all files. Compromising this account can have devastating consequences.
Common Attack Vectors
Password Cracking
Password cracking involves attempts to guess or decipher a user's password. This can be done through various techniques, including brute-force attacks, dictionary attacks, and the use of rainbow tables.
Brute-force attacks systematically try every possible combination of characters until the correct password is found. Dictionary attacks use lists of commonly used passwords to accelerate the process.
Rainbow tables are pre-computed hashes that allow for faster password recovery compared to brute-force.
Exploiting Software Vulnerabilities
Software vulnerabilities are flaws in a system's code that can be exploited by attackers. These vulnerabilities can allow an attacker to bypass authentication mechanisms and gain administrator privileges.
Attackers often use publicly available exploit code or develop their own to target known vulnerabilities. Keeping systems and software up to date with the latest security patches is crucial in mitigating this risk.
Social Engineering
Social engineering is a technique that manipulates individuals into divulging confidential information, such as passwords. Attackers might pose as technical support or other trusted figures to trick users into revealing their credentials.
Phishing emails, phone calls, and in-person interactions are common methods used in social engineering attacks. Education and awareness training are essential to protect users from these types of attacks.
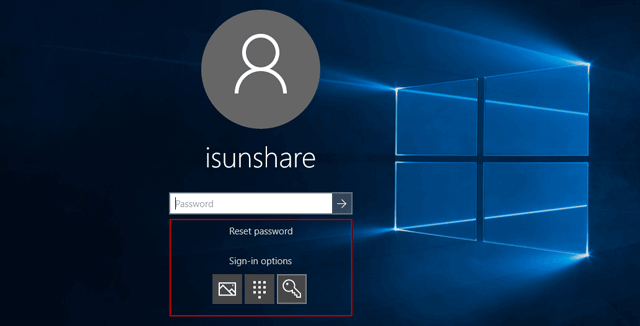
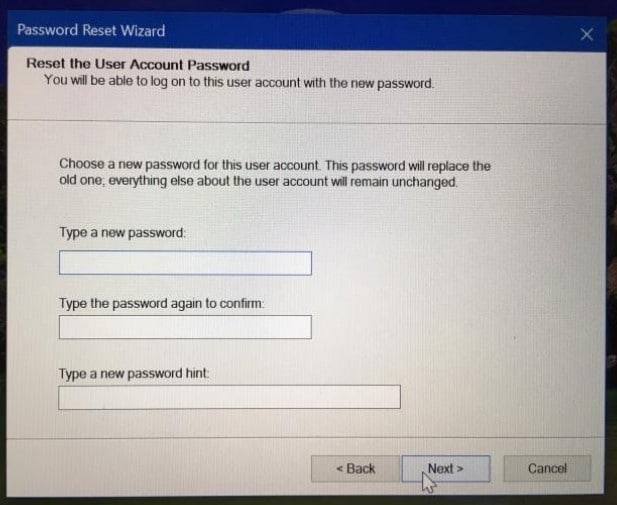
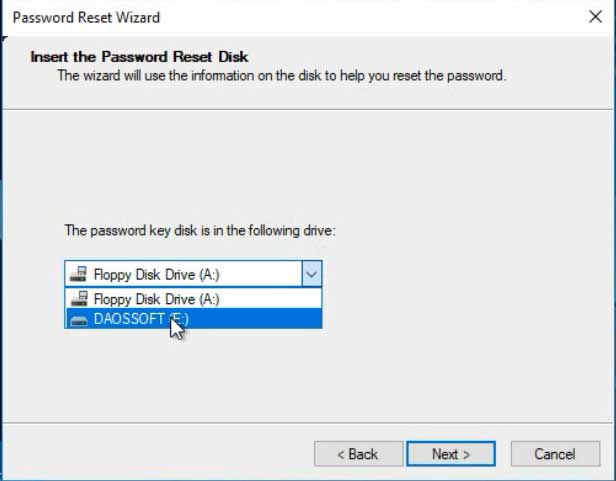
Bypassing Local Account Security
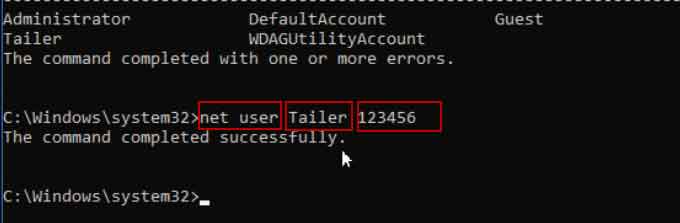
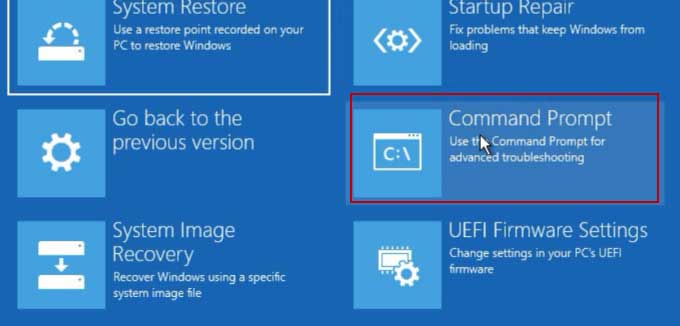
Some operating systems have built-in recovery options that could be misused if not properly secured. For example, default settings in older Windows versions sometimes allowed for bypassing the login screen.
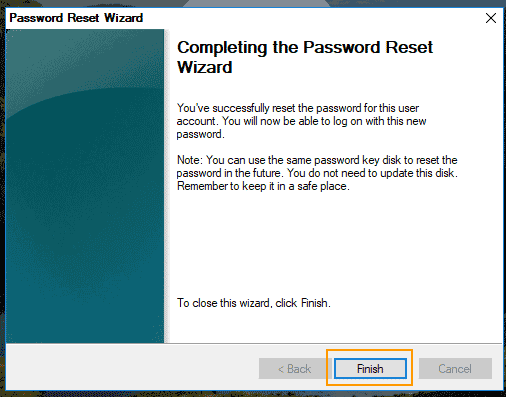
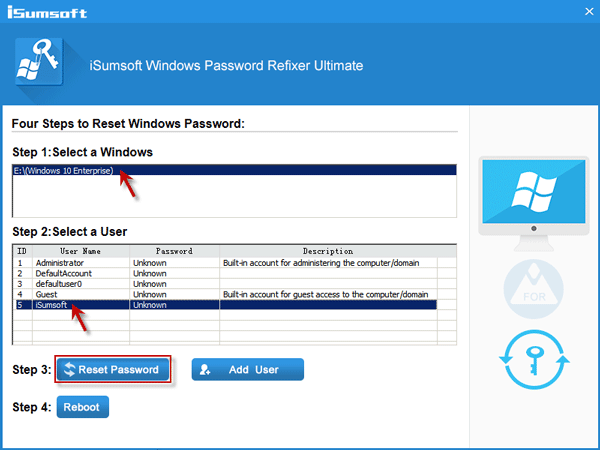
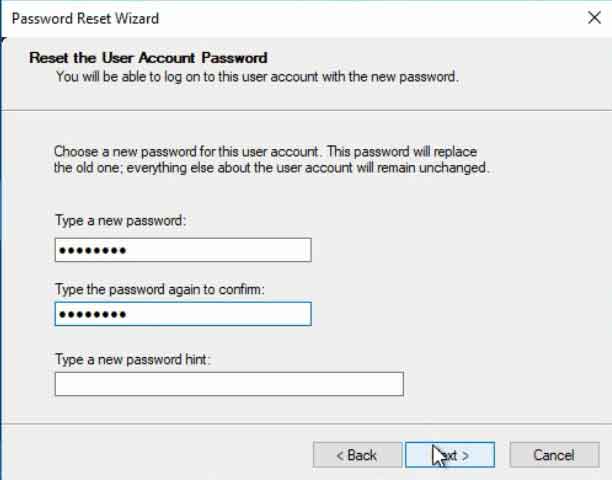
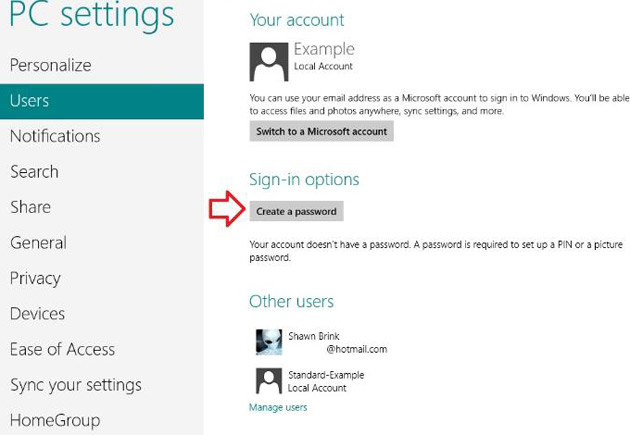
Tools like the System Recovery Options, if not password-protected, could be used to reset the administrator password. Disabling or securing these options is a critical security measure.
Mitigation Strategies
Preventing unauthorized access to the administrator account requires a multi-layered security approach.
Implementing strong password policies, keeping software updated, and educating users about social engineering tactics are all essential components of a robust security posture.
Strong Password Policies
Enforcing strong password policies is the first line of defense against password cracking attacks. Passwords should be long, complex, and unique, and users should be required to change them regularly.
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of identification. This makes it significantly harder for attackers to gain access, even if they have obtained the password.
Regular Software Updates
Keeping software updated with the latest security patches is critical for addressing known vulnerabilities. Software vendors regularly release updates to fix security flaws that could be exploited by attackers.
Automated update mechanisms can help ensure that systems are always running the latest version of software. However, it is important to test updates in a non-production environment before deploying them to the entire network.
User Education and Awareness
Educating users about social engineering tactics and other security threats is essential for creating a security-conscious culture. Users should be trained to recognize phishing emails, suspicious phone calls, and other types of attacks.
Regular security awareness training can help users to make informed decisions and avoid falling victim to social engineering attacks.
Principle of Least Privilege
The principle of least privilege states that users should only be granted the minimum level of access required to perform their job duties. This reduces the potential damage that an attacker can cause if they compromise a user's account.
By limiting access rights, organizations can minimize the impact of a security breach and prevent attackers from gaining access to sensitive data or systems.
Ethical and Legal Considerations
Attempting to bypass or unlock administrator passwords without proper authorization is illegal and unethical. Unauthorized access to computer systems can result in severe legal consequences, including criminal charges and civil lawsuits.
It is crucial to respect the privacy and security of others and to only access computer systems with the express permission of the owner. This knowledge should be used for authorized security testing and defensive purposes only.
Conclusion
Securing the administrator account is paramount for protecting computer systems from unauthorized access and potential compromise. Employing a combination of strong password policies, regular software updates, user education, and the principle of least privilege is essential for creating a robust security posture.
By understanding the methods that attackers use to bypass security measures, organizations and individuals can take proactive steps to mitigate these risks and safeguard their valuable data and systems. Staying informed about emerging threats and best practices is crucial for maintaining a strong security posture in an ever-evolving threat landscape. As technology continues to advance, the challenges of protecting administrator accounts will likely become more complex, necessitating ongoing vigilance and adaptation.







:max_bytes(150000):strip_icc()/002-reset-windows-10-admin-password-4589065-9c9156b5bee74c28a57bfbdcac5bad1e.jpg)