If You Discover A Data Breach
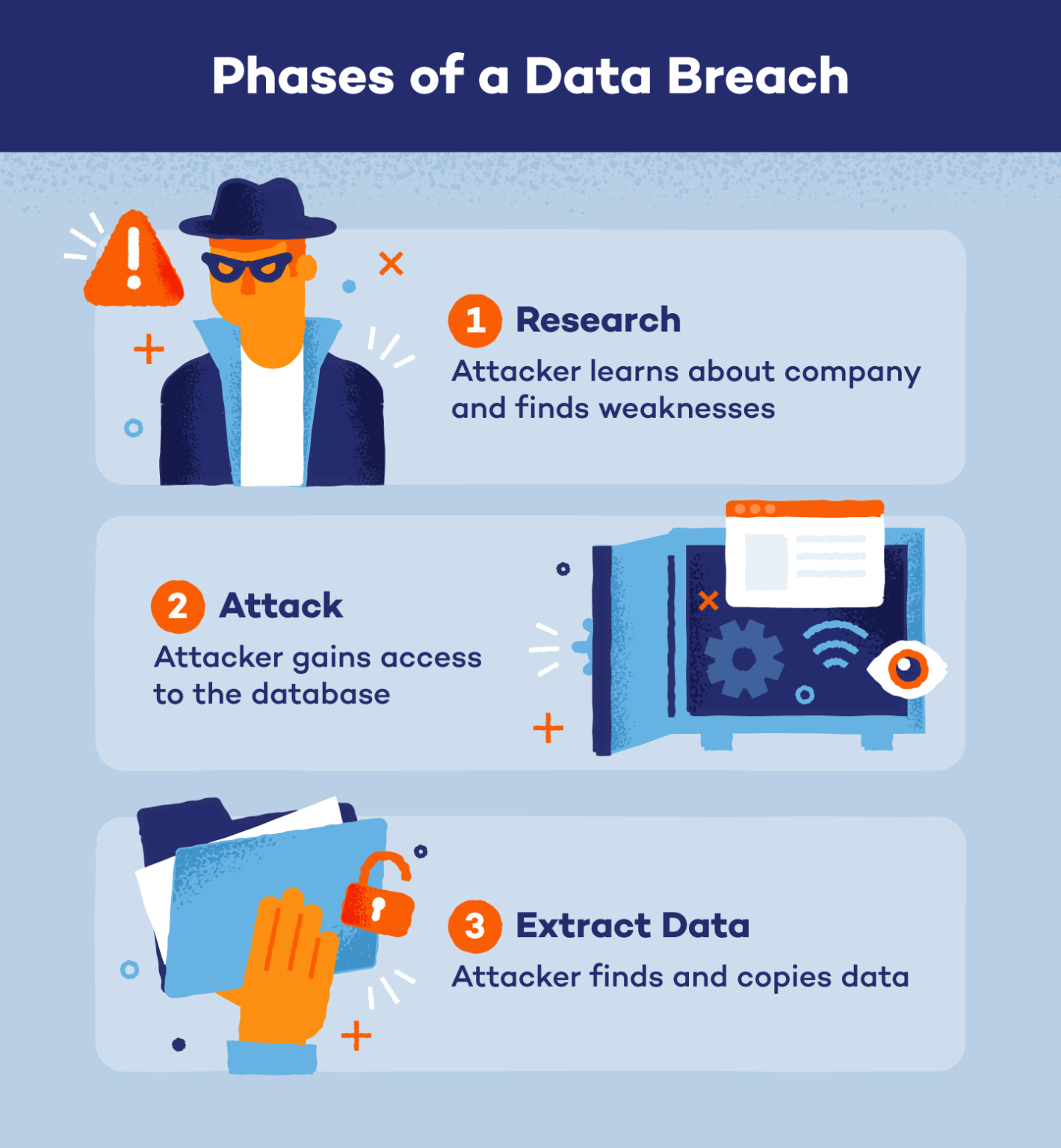
Imagine this: you're settling in for the evening, ready to unwind with your favorite online game, or perhaps check your bank balance before bed. Suddenly, a strange email lands in your inbox – a notification that your password has been changed, or worse, that unusual activity has been detected on your account. A wave of dread washes over you. It's the gut-wrenching realization that you might be facing a data breach.
This scenario, unfortunately, is becoming increasingly common. Knowing how to react swiftly and effectively when you suspect a data breach can make all the difference in mitigating potential damage. This article provides a practical guide on what steps to take if you believe your personal information has been compromised, empowering you to protect yourself in the digital age.
Understanding the Landscape of Data Breaches
Data breaches are no longer a rare occurrence; they are an ever-present threat in our interconnected world. According to the Identity Theft Resource Center (ITRC), data breaches reached record highs in recent years, impacting millions of individuals. These breaches can range from simple password compromises to sophisticated attacks targeting sensitive financial and medical information.
The impact of a data breach can be far-reaching and devastating. Victims may experience financial losses due to fraudulent transactions, damage to their credit scores, and even emotional distress. The consequences can linger for months, even years, as individuals struggle to recover from the fallout.
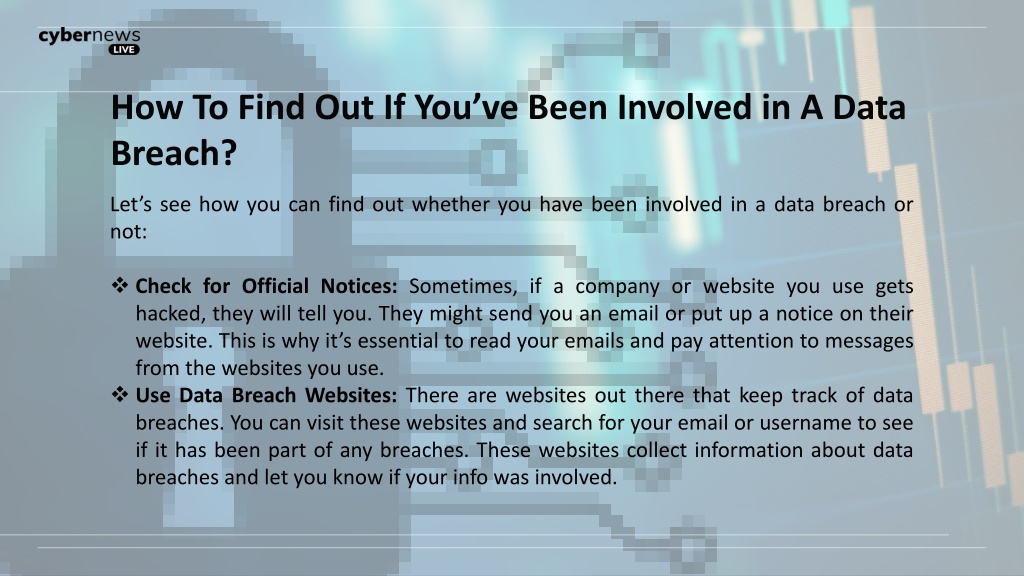
Recognizing the Signs of a Breach
The first step in addressing a potential data breach is recognizing the warning signs. This requires vigilance and a proactive approach to monitoring your accounts and online activity. Be alert for any unusual activity.
Look for unfamiliar emails or text messages, unauthorized transactions, or changes to your online profiles that you didn't initiate. Suspicious communications, like phishing attempts, often precede or accompany a larger data breach.
Pay close attention to your credit reports and bank statements. Sign up for account alerts to receive immediate notifications of any suspicious transactions or changes to your account information.
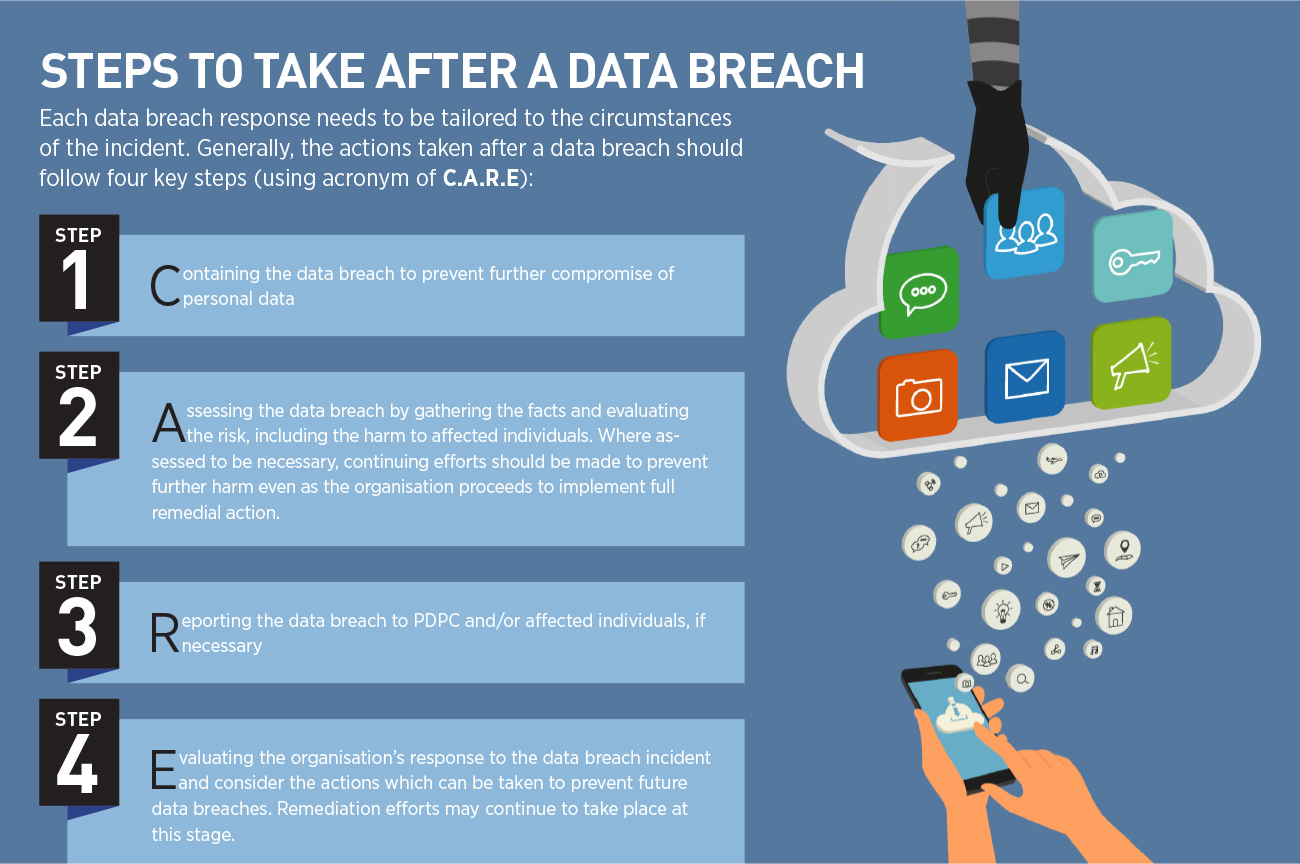
Immediate Actions: Containment and Assessment
Once you suspect a data breach, time is of the essence. Swift action can significantly reduce the potential damage and protect your sensitive information. The first crucial step is to contain the breach and assess the extent of the compromise.
Change your passwords immediately. Update the passwords for all affected accounts and any other accounts that share the same password. Choose strong, unique passwords that are difficult to guess. Consider using a password manager to generate and store complex passwords securely.
Next, notify the affected companies or institutions. Contact the customer service departments of any companies where you suspect your information has been compromised. Report the potential breach and ask them to investigate and take appropriate action.
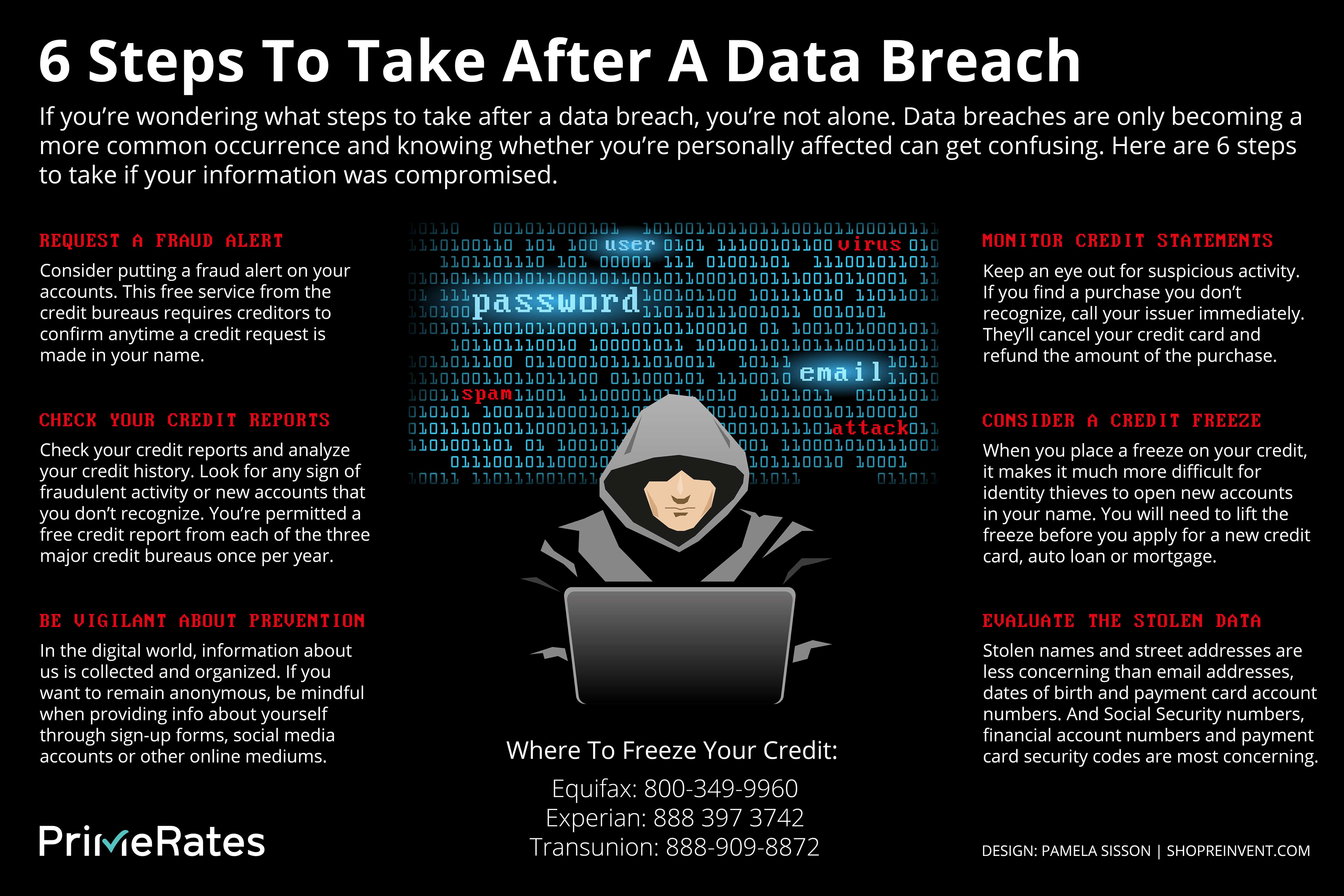
Freezing Your Credit and Monitoring Reports
Freezing your credit is a powerful tool for preventing identity theft and mitigating the impact of a data breach. A credit freeze restricts access to your credit report, making it difficult for criminals to open new accounts in your name.
You can place a credit freeze with each of the three major credit bureaus: Equifax, Experian, and TransUnion. The process is typically free, and you can lift the freeze temporarily when you need to apply for credit.
In addition to freezing your credit, actively monitor your credit reports for any signs of fraudulent activity. Review your reports regularly for unfamiliar accounts, inquiries, or other discrepancies. You are entitled to a free copy of your credit report from each of the three major credit bureaus every 12 months at AnnualCreditReport.com.
Reporting the Breach and Seeking Assistance
Reporting a data breach is an important step in protecting yourself and helping to prevent future incidents. Contact the appropriate authorities to report the breach and seek assistance with recovery.
File a report with the Federal Trade Commission (FTC). The FTC is the primary federal agency responsible for protecting consumer privacy and enforcing data security laws. You can file a report online or by phone.
Consider reporting the breach to your state's attorney general. Many states have laws requiring companies to notify consumers of data breaches. Your state attorney general can investigate and take enforcement action against companies that violate these laws.
Leveraging Resources and Staying Informed
Navigating the aftermath of a data breach can be overwhelming, but you don't have to do it alone. Numerous resources are available to provide guidance, support, and assistance with recovery. The ITRC offers comprehensive resources and support services for victims of identity theft.
The Privacy Rights Clearinghouse is another valuable resource, providing information and advocacy on privacy issues. Stay informed about data breach news and security best practices by following reputable security blogs and news outlets. Regularly review and update your security settings on your online accounts.
Enable two-factor authentication (2FA) whenever possible to add an extra layer of security to your accounts. Be cautious of phishing emails and other scams that attempt to trick you into revealing personal information.
Long-Term Strategies for Data Protection
Protecting your personal information in the digital age is an ongoing effort. It requires a proactive and vigilant approach to data security. By adopting sound security practices and staying informed about emerging threats, you can significantly reduce your risk of becoming a victim of a data breach.
Regularly review and update your privacy settings on social media platforms and other online services. Limit the amount of personal information you share online and be mindful of the information you post. Be careful about the websites you visit and the apps you download.
Stick to trusted sources and avoid clicking on suspicious links or downloading files from unknown senders. Consider using a virtual private network (VPN) when connecting to public Wi-Fi networks to encrypt your internet traffic and protect your data from eavesdropping.
Data privacy is not just a technical issue; it's a fundamental right. Advocate for stronger data privacy laws and regulations to protect consumers from data breaches. Support organizations that are working to promote data security and privacy.
Conclusion: Embracing Digital Resilience
Discovering a data breach can be a jarring experience, but it doesn't have to be debilitating. By taking swift and decisive action, you can minimize the damage and protect your personal information. Remember, knowledge is power, and a proactive approach to data security is your best defense in the digital world.
Embrace digital resilience by staying informed, being vigilant, and adopting sound security practices. By working together, we can create a safer and more secure online environment for everyone.
The road to recovery after a data breach may seem daunting, but with the right resources and support, you can emerge stronger and more resilient. Consider this not just a moment of crisis, but an opportunity to learn and adapt, fortifying your defenses for the future. It’s a reminder that in our increasingly connected world, protecting our digital selves is an ongoing journey, one we must all actively participate in.




![If You Discover A Data Breach Top Known Data Breaches of 2022 [Timeline + Infographic] - Venngage](https://venngage-wordpress.s3.amazonaws.com/uploads/2022/09/40f5b5ae-d685-4379-b41e-e48bdea3e7ab-1-1024x791.png)







![If You Discover A Data Breach Must Know Data Breach Statistics and Facts [Updated 2023]](https://i0.wp.com/www.exabytes.sg/blog/wp-content/uploads/2022/11/data-breach-statistics-updated.jpg)

