Physical Security Program Is Designed To Prevent Unauthorized Access To

The threat is invisible but ever-present. A single breach, a momentary lapse in vigilance, can cripple operations, expose sensitive data, and inflict irreparable reputational damage. The modern enterprise understands that cybersecurity isn't just about firewalls and encryption; it's about fortifying the physical realm.
This is why robust physical security programs, designed to meticulously prevent unauthorized access, are becoming increasingly vital, representing the first line of defense against a spectrum of threats, from opportunistic intruders to sophisticated actors seeking to compromise assets and information.
These programs are not merely about locks and cameras; they encompass a holistic strategy, integrating technology, personnel, and procedures to create a layered security environment. They're built to deter, detect, and respond to any unauthorized attempt to enter a facility or access restricted areas.
Understanding the Core Components
At the heart of any effective physical security program lies a comprehensive risk assessment. This process identifies potential vulnerabilities, evaluates the likelihood and impact of various threats, and informs the selection of appropriate security measures.
A risk assessment might reveal weaknesses in perimeter security, such as inadequate fencing or lighting, or vulnerabilities within the building itself, like poorly secured doors or windows. Implementing layers of security is key, so a breach in one area doesn't compromise the entire system.
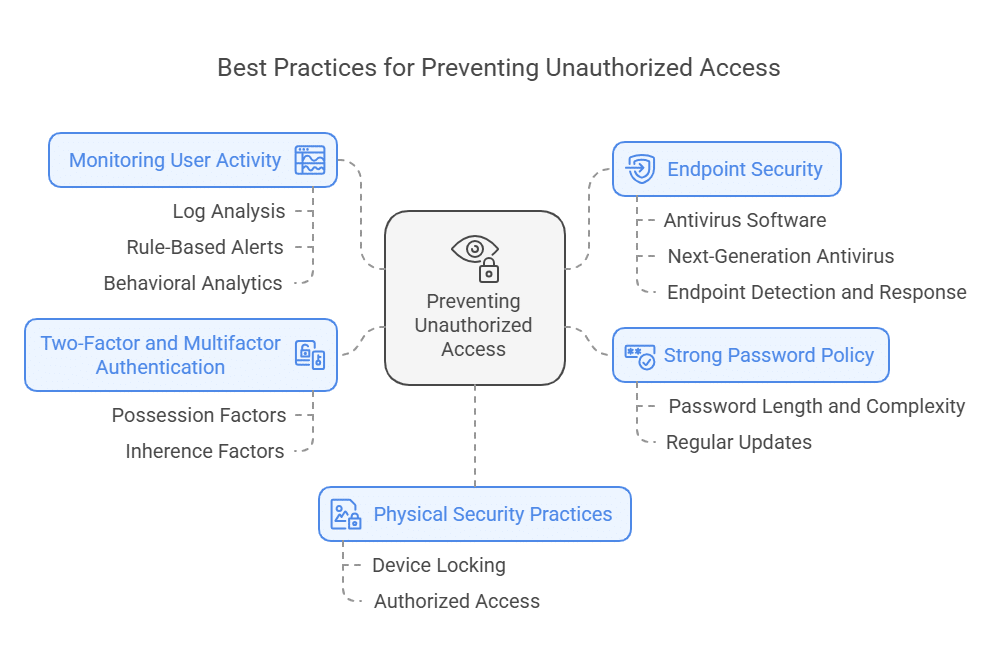
Based on the risk assessment, a program will incorporate a range of technologies. Access control systems, using keycards, biometric scanners, or mobile credentials, regulate entry to buildings and specific areas.
Surveillance systems, including closed-circuit television (CCTV) cameras and motion detectors, provide real-time monitoring and record evidence of suspicious activity. Intrusion detection systems trigger alarms when unauthorized entry is detected, alerting security personnel or law enforcement.
Trained security personnel play a crucial role in physical security. Guards stationed at entry points screen visitors, patrol the premises, and respond to incidents. They are the human element, providing a visible deterrent and acting as the first responders in a security event.
Procedures are just as crucial. Protocols for visitor management, package handling, and emergency response must be clearly defined and consistently enforced. Regular drills and training exercises ensure that personnel are prepared to respond effectively to various security threats.
The Importance of Perimeter Security
The perimeter of a facility is the first line of defense, and its security is paramount. Fencing, walls, and barriers deter casual intruders and delay more determined attackers. Lighting illuminates the area, making it easier to detect suspicious activity.
Vehicle barriers prevent unauthorized vehicles from approaching the building. These barriers can be physical, such as bollards or concrete barriers, or electronic, such as automated gates or tire spikes.
Perimeter intrusion detection systems (PIDS) use sensors to detect attempts to breach the perimeter. These sensors can detect movement, vibration, or pressure, and they trigger alarms to alert security personnel.
Internal Security Measures
Once inside the perimeter, access control systems regulate entry to specific areas. These systems use a variety of technologies, including keycards, biometric scanners, and mobile credentials.
Different levels of access can be granted to different individuals, depending on their roles and responsibilities. This ensures that only authorized personnel can access sensitive areas.
Surveillance systems monitor activity within the building, recording video footage of entrances, hallways, and other critical areas. This footage can be used to investigate incidents, identify perpetrators, and provide evidence for law enforcement.
The Human Element
Even the most advanced technology is only as effective as the people who operate and maintain it. Training programs are essential to ensure that security personnel are proficient in their roles.
Security awareness training for all employees is also crucial. Employees should be educated about potential security threats and how to report suspicious activity. They should be encouraged to be vigilant and to challenge anyone who appears to be out of place.
Regular background checks and security clearances are necessary for employees who have access to sensitive areas or information. This helps to mitigate the risk of insider threats.
The Evolving Threat Landscape
Physical security threats are constantly evolving, requiring programs to be dynamic and adaptable. Traditional threats, such as theft and vandalism, remain a concern, but new threats are emerging.
Cyber-physical attacks, in which hackers attempt to manipulate physical systems through digital means, are becoming increasingly common. Drones can be used to survey facilities or to deliver malicious payloads.
Active shooter incidents are a growing concern, requiring organizations to develop plans for responding to such events. These plans should include procedures for evacuation, lockdown, and communication.
Looking Ahead
The future of physical security will be shaped by advancements in technology. Artificial intelligence (AI) and machine learning (ML) are being used to analyze video footage, detect anomalies, and predict potential security breaches.
The Internet of Things (IoT) is connecting more and more devices, creating new opportunities for security solutions. Smart locks, sensors, and cameras can be integrated into a comprehensive security system.
However, the human element will remain critical. Technology can enhance security, but it cannot replace the need for trained personnel, clear procedures, and a culture of security awareness. A balanced approach is essential.
In conclusion, a robust physical security program is not a luxury but a necessity. It is an investment that protects assets, safeguards data, and preserves reputation. By understanding the core components of such programs and adapting to the evolving threat landscape, organizations can create a secure environment for their employees, customers, and stakeholders.