What Is A Hidden Network On Wifi
In an era defined by ubiquitous wireless connectivity, the very air around us hums with data, invisibly linking devices to the internet. While most Wi-Fi networks broadcast their presence, making connection straightforward, a more elusive type exists: the hidden network. These networks, intentionally cloaked from casual view, spark curiosity and sometimes, concern.
This article delves into the world of hidden Wi-Fi networks, examining their purpose, functionality, and the implications for both network administrators and everyday users. We will explore how these networks operate, the security benefits they may (or may not) offer, and the steps involved in connecting to one. By examining reliable data and technical insights, we aim to provide a comprehensive understanding of this often-misunderstood aspect of wireless technology.
What Defines a Hidden Wi-Fi Network?
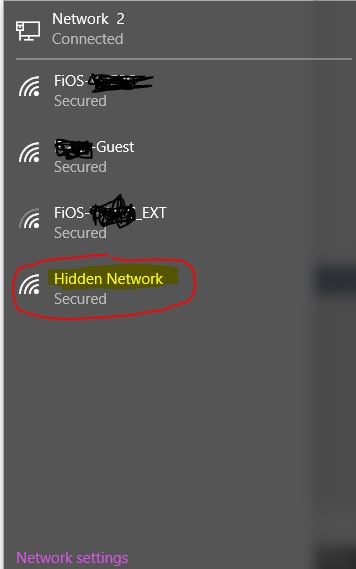
A standard Wi-Fi network broadcasts its Service Set Identifier (SSID), essentially its name, allowing devices to easily discover and connect. A hidden network, also known as an SSID-cloaked network, disables this broadcasting feature. This means the network's name is not publicly advertised, making it invisible to standard Wi-Fi scanning tools.
Technically, the network still operates on radio frequencies and transmits data as usual. Only the broadcast of the SSID is suppressed, making it more difficult to initially detect the network. It's crucial to understand that hiding the SSID doesn't inherently encrypt the data transmitted over the network; it only affects its discoverability.
Reasons for Hiding a Wi-Fi Network
The primary reason for hiding a Wi-Fi network is often perceived to be enhanced security. Administrators might believe that concealing the network name will deter unauthorized access. This is based on the logic that if a network isn't visible, it's less likely to be targeted.
However, experts generally agree that hiding the SSID offers minimal real security. More robust security measures, such as strong passwords and proper encryption (WPA3), are significantly more effective. In some niche environments, hidden networks might be used for very specific purposes, such as isolating network segments or for temporary networks.
In corporate settings, it can also be used for administrative purposes, for instance, isolating guest networks from internal systems. By preventing casual browsing and connections, it is believed that the risks of malware or unauthorized use can be mitigated.
The Illusion of Security: Why Hiding SSIDs Isn't Enough
While hiding the SSID might seem like a simple security measure, it's easily circumvented by determined individuals. Tools are readily available that can passively monitor Wi-Fi traffic and identify hidden networks. The mere presence of Wi-Fi signals betrays the network's existence, and specialized software can quickly reveal the hidden SSID.
Furthermore, once a device has connected to a hidden network, it stores the SSID. The device will actively probe for that network even when it's not actively connected, broadcasting the SSID in its search. This broadcasting can actually make the network more vulnerable to attacks.
Security professionals at organizations like SANS Institute consistently emphasize that strong encryption protocols and robust password policies are far more effective at securing a Wi-Fi network than simply hiding the SSID. Relying solely on SSID hiding creates a false sense of security and can even introduce new vulnerabilities.
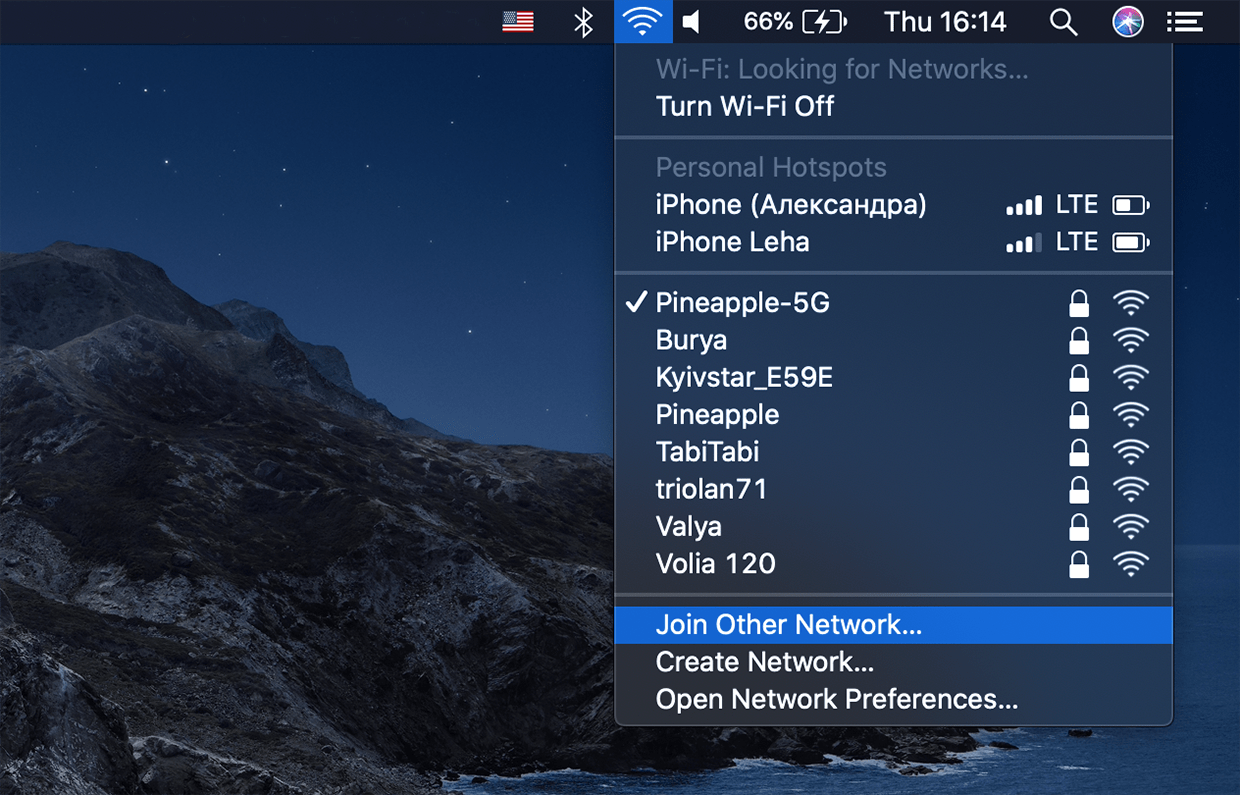
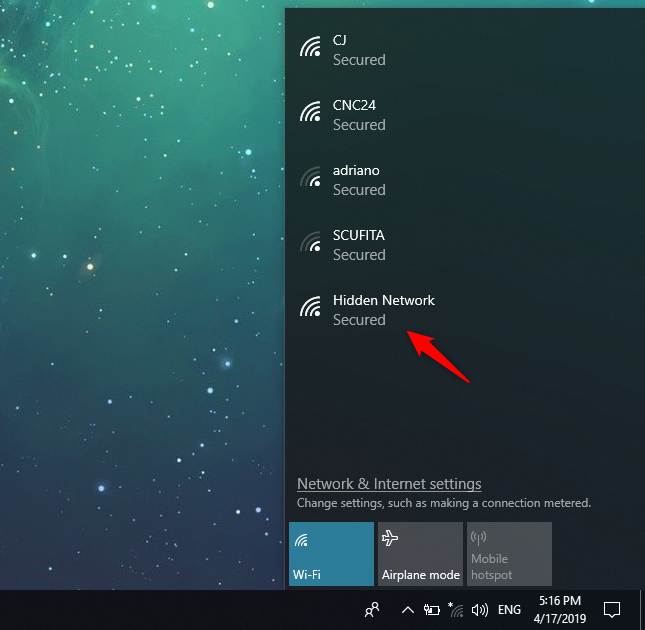
Connecting to a Hidden Wi-Fi Network
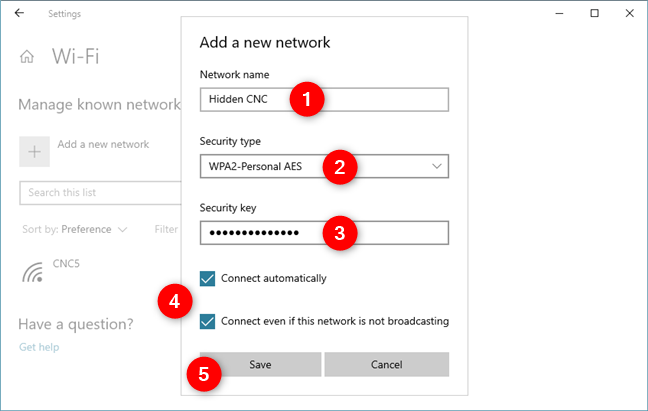
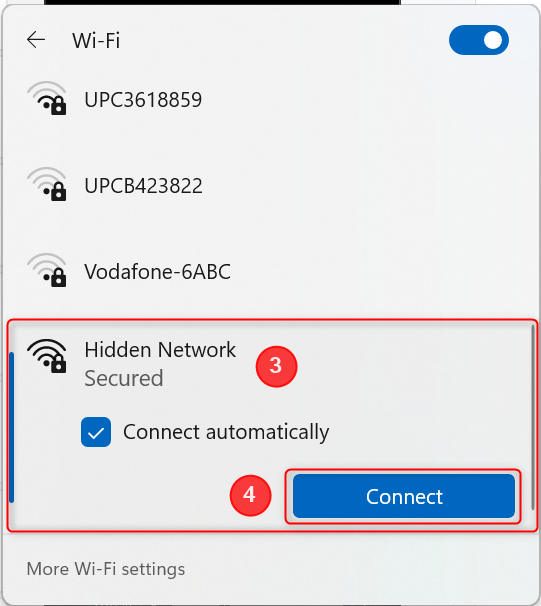
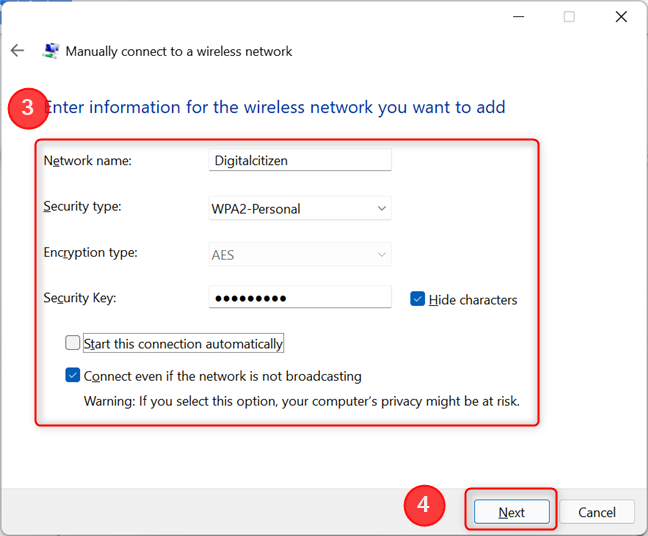
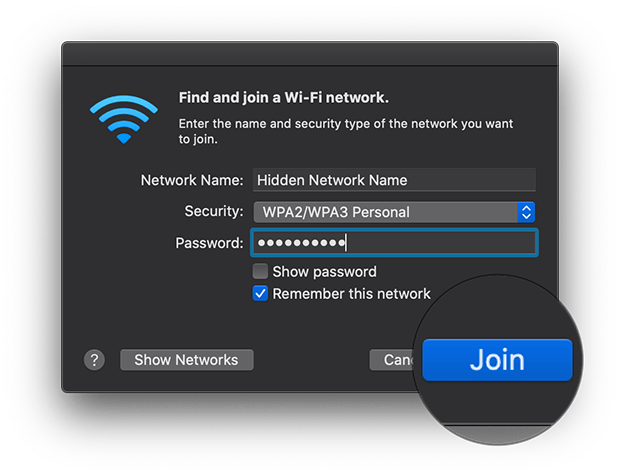
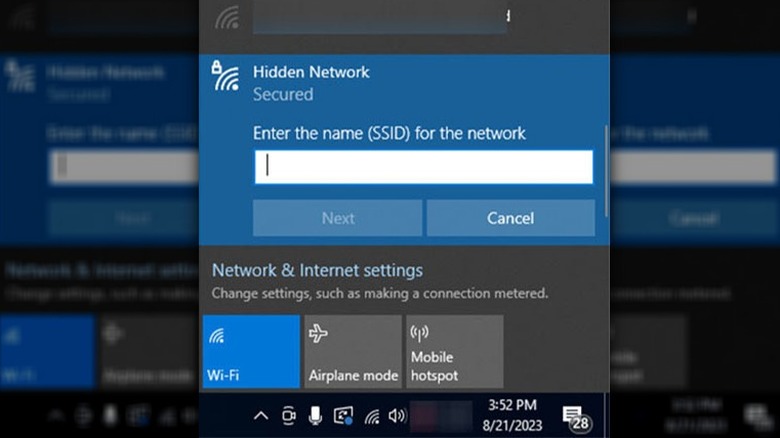
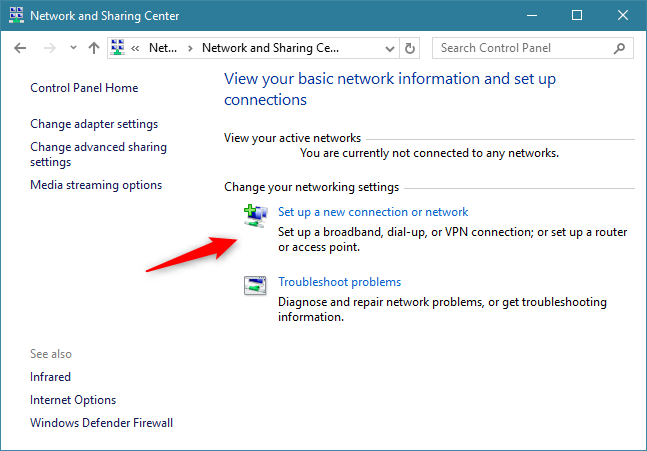
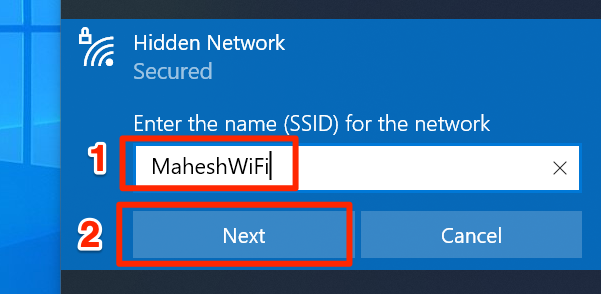
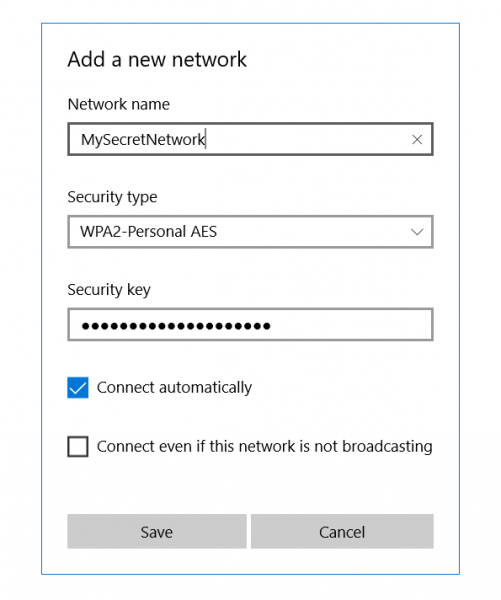
Connecting to a hidden Wi-Fi network requires manual configuration. You need to know the exact network name (SSID), security type (e.g., WPA2/WPA3), and password. Once you have this information, you can manually add the network in your device's Wi-Fi settings.
The process is similar across different operating systems, including Windows, macOS, Android, and iOS. Look for an option to "add a hidden network" or "manually configure network settings" in the Wi-Fi settings menu. This process can be tedious and is one of the drawbacks for everyday usability.
You will typically be required to input the exact SSID, select the correct security protocol (WPA2, WPA3 etc.), and enter the network password. Any slight error in these parameters can result in a failed connection. Therefore, it is important to ensure that all details are accurate.
Potential Drawbacks of Hidden Networks
Besides offering questionable security benefits, hiding the SSID can introduce practical problems. It can make it more difficult for legitimate users to connect to the network, requiring manual configuration and technical knowledge.
As mentioned earlier, devices constantly probing for hidden networks can degrade network performance and battery life. Since a device is constantly sending out probe requests. This also presents privacy concerns as these probes are effectively advertising what networks a device has previously connected to.
Furthermore, some older devices or operating systems may have difficulty connecting to hidden networks. These devices are not optimized for constantly probing for these networks and can create unstable connections. This incompatibility can cause frustration for users with legacy devices.
Alternative Security Measures for Wi-Fi Networks
Rather than relying on SSID hiding, focus on proven security measures. Strong passwords, employing a mix of upper and lowercase letters, numbers, and symbols, are essential.
Utilize the latest encryption protocol, WPA3, for robust data protection. Enable network firewalls, and regularly update router firmware to patch security vulnerabilities. Consider using a Virtual Private Network (VPN) for an added layer of security when accessing sensitive information, especially on public Wi-Fi.
Implement MAC address filtering to restrict network access to authorized devices only. Furthermore, consider using a guest network for visitors, so you are not sharing your primary network password with potentially insecure devices.
The Future of Wi-Fi Security
The trend in Wi-Fi security is moving towards more sophisticated and adaptive solutions. Features like Wi-Fi Protected Setup (WPS), once considered a convenience, have been found to have vulnerabilities, emphasizing the need for constant vigilance and improved security protocols. Advancements in AI-powered threat detection promise to proactively identify and mitigate network threats.
Organizations like the Wi-Fi Alliance are continuously working on enhancing security standards and promoting best practices. The goal is to make Wi-Fi networks more secure and user-friendly. This involves a combination of technological advancements and user education.
Ultimately, a layered approach to security is the most effective strategy, combining strong passwords, encryption, and regular security audits to protect against evolving threats. The era of relying on simple obscurity measures like hiding the SSID is rapidly coming to an end, replaced by a focus on robust, verifiable security.