Which Of The Following Statements About Protected Health Information

The digital age has ushered in unprecedented opportunities for healthcare innovation, but it has also amplified the challenges surrounding patient privacy. Protected Health Information (PHI), a cornerstone of healthcare ethics and law, faces ever-evolving threats in a landscape of data breaches, sophisticated cyberattacks, and expanding data sharing practices. Understanding the nuances of PHI—what it encompasses, how it's protected, and the consequences of its misuse—is crucial for patients, healthcare providers, and anyone working within the healthcare ecosystem.
This article aims to provide a comprehensive overview of PHI, clarifying key statements about its definition, protection, and permissible uses under the Health Insurance Portability and Accountability Act (HIPAA). We will delve into common misconceptions, explore recent regulatory updates, and examine the implications of non-compliance, shedding light on the critical importance of safeguarding sensitive health data in an increasingly interconnected world. Accuracy and understanding are paramount in ensuring patient trust and maintaining the integrity of the healthcare system.
Defining Protected Health Information (PHI)
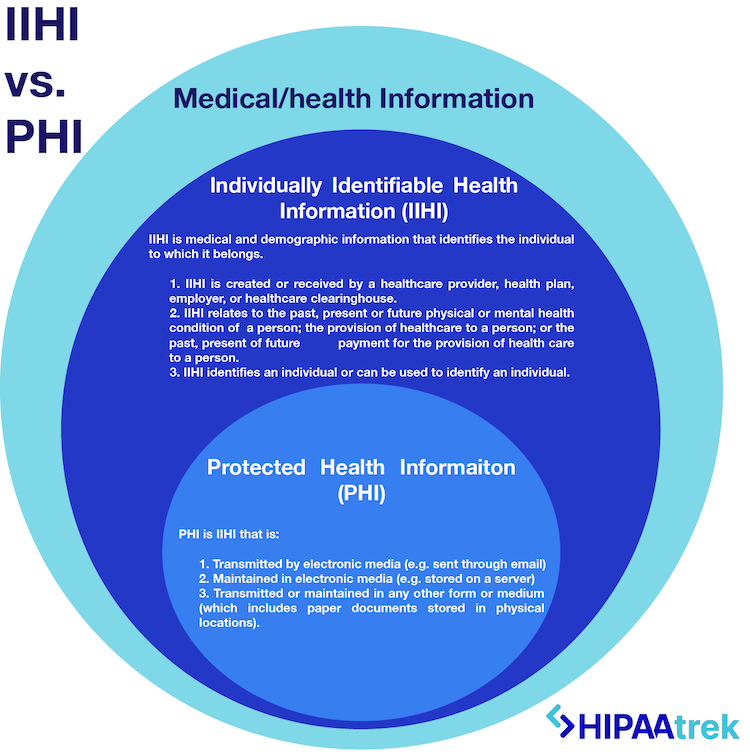
PHI, as defined by HIPAA, refers to any individually identifiable health information that is transmitted or maintained in any form or medium. This includes electronic, paper, and oral communication. Individually identifiable means the information relates to a person's past, present, or future physical or mental health condition.
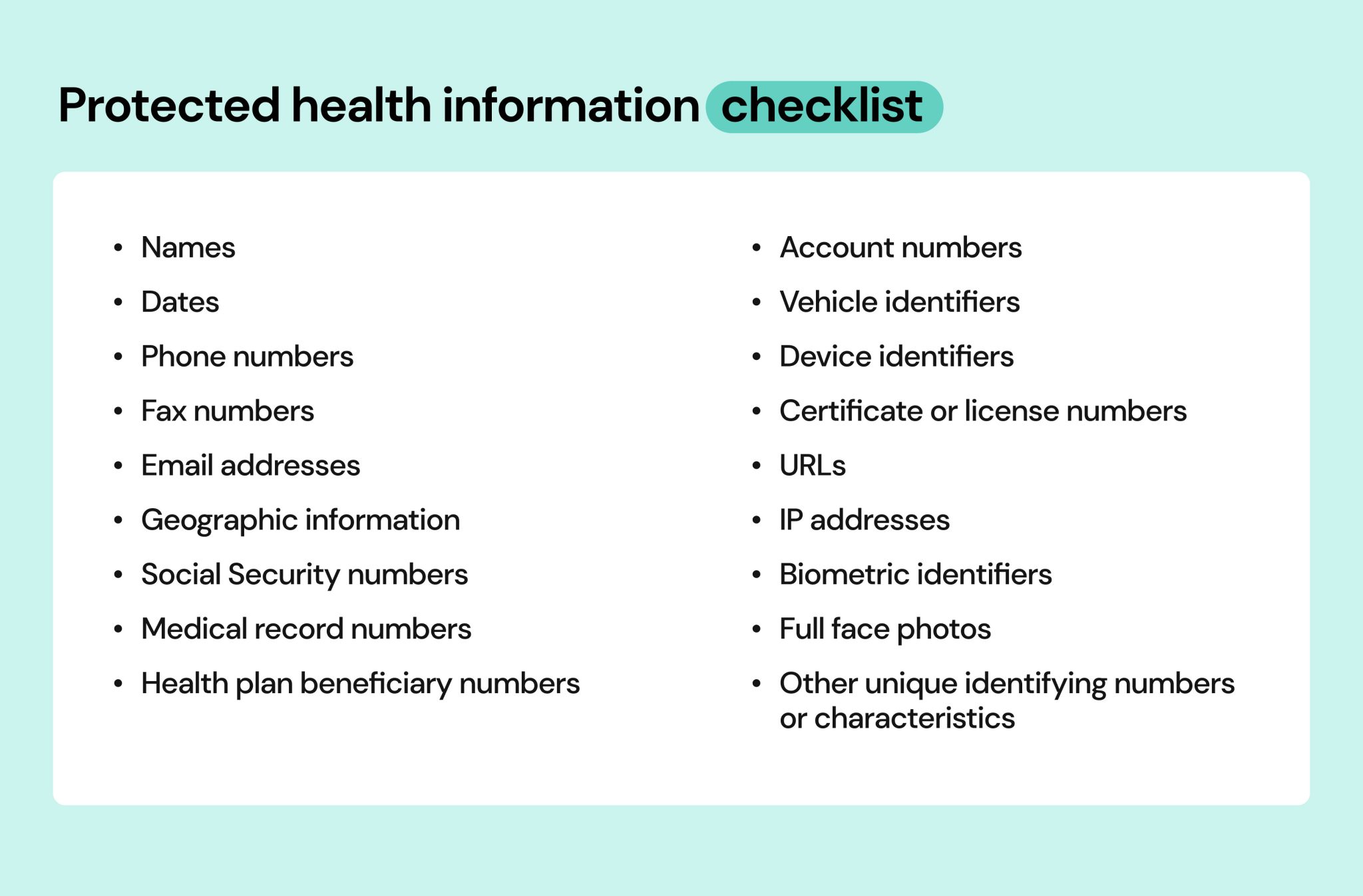
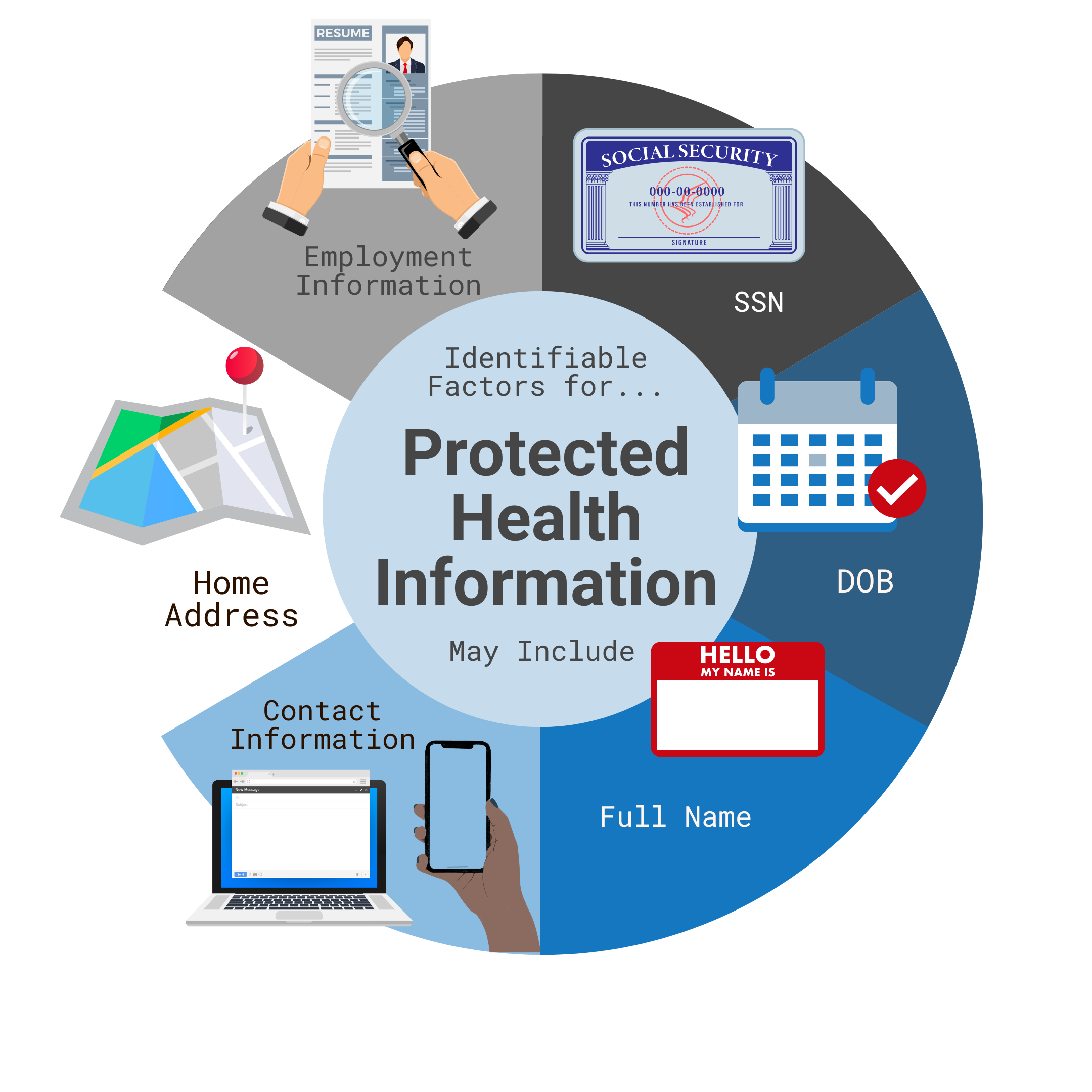
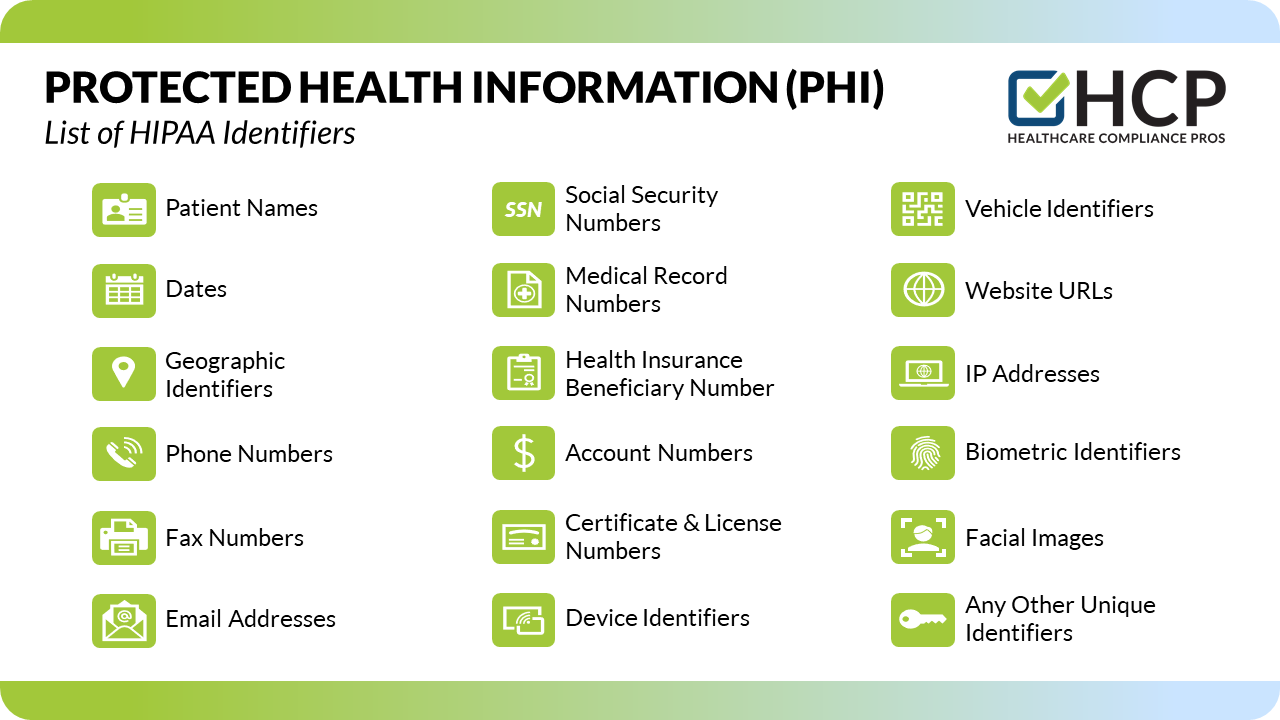
The U.S. Department of Health and Human Services (HHS) outlines 18 identifiers that, if associated with health information, render it PHI. These include names, addresses, dates (except year), phone numbers, email addresses, Social Security numbers, medical record numbers, health plan beneficiary numbers, account numbers, certificate/license numbers, vehicle identifiers and serial numbers (including license plate numbers), device identifiers and serial numbers, URLs, IP addresses, biometric identifiers (fingerprints, retinal scans), full-face photographic images, and any other unique identifying number, characteristic, or code.
Therefore, a statement like "Only medical records and billing information constitute PHI" is demonstrably false. The definition is much broader, encompassing a wide array of data points. A photograph of a patient, for instance, can be considered PHI if it's linked to their medical record or used in a way that reveals their health status.
HIPAA and the Protection of PHI
HIPAA establishes a national standard to protect individuals' medical records and other personal health information and applies to health plans, healthcare clearinghouses, and healthcare providers that conduct certain health care transactions electronically.covered entities.
HIPAA's Privacy Rule provides individuals with rights over their health information, including the right to access, request amendments to, and receive an accounting of disclosures of their PHI. It also outlines the conditions under which covered entities may use and disclose PHI.
A common misunderstanding is that HIPAA prohibits all sharing of health information. In reality, HIPAA permits the use and disclosure of PHI for treatment, payment, and healthcare operations without the patient's authorization, subject to specific safeguards. It also allows for disclosures required by law, such as reporting certain communicable diseases.
Permissible Uses and Disclosures
HIPAA allows the use and disclosure of PHI for treatment purposes, meaning healthcare providers can share information to coordinate patient care. This can involve sharing information with other doctors, specialists, and pharmacists involved in the patient's treatment.
PHI can also be used for payment purposes, such as billing insurance companies or collecting payments from patients. However, even in these instances, covered entities must make reasonable efforts to limit the amount of PHI disclosed to the minimum necessary to accomplish the intended purpose.
Healthcare operations include activities such as quality assessment, utilization review, and business management. Again, the minimum necessary standard applies.
The Minimum Necessary Standard
The minimum necessary standard is a core principle of HIPAA, requiring covered entities to limit the use and disclosure of PHI to the minimum amount necessary to accomplish the intended purpose. This means that individuals within the organization who need access to PHI to perform their job duties should only be granted access to the information they require.
This standard doesn't apply to disclosures to the individual who is the subject of the information, disclosures made pursuant to an individual's authorization, disclosures for treatment purposes, or disclosures required by law.
One incorrect statement is that "The minimum necessary standard applies to all uses and disclosures of PHI." There are specific exceptions, as outlined above. A blanket statement like this oversimplifies a complex legal requirement.
Consequences of Non-Compliance
Violations of HIPAA can result in significant financial penalties and reputational damage. The Office for Civil Rights (OCR) within HHS is responsible for enforcing HIPAA.
Penalties for HIPAA violations range from $100 to $50,000 per violation, with a maximum penalty of $1.5 million per calendar year for each violation. These penalties can be assessed based on the level of culpability, ranging from unknowing violations to willful neglect.
In addition to financial penalties, HIPAA violations can also lead to criminal charges in certain cases. For example, knowingly obtaining or disclosing PHI in violation of HIPAA can result in imprisonment.
Real-World Examples
Data breaches involving PHI are becoming increasingly common. These breaches can occur due to hacking, ransomware attacks, insider threats, or simple human error. In recent years, large-scale breaches have compromised the PHI of millions of individuals, highlighting the vulnerability of healthcare data.
A hospital employee improperly accessing patient records and sharing them with unauthorized individuals is a HIPAA violation. A business associate failing to adequately protect PHI can also be held liable.
It's incorrect to assume that "Only large hospitals and insurance companies are targets for data breaches." Small practices and clinics are also vulnerable and often lack the resources to implement robust security measures.
Looking Ahead: The Future of PHI Protection
As technology advances, the challenges of protecting PHI will continue to evolve. The increasing use of telehealth, wearable devices, and cloud-based healthcare systems creates new opportunities for data breaches and privacy violations.
Future efforts will need to focus on strengthening cybersecurity measures, enhancing employee training, and developing more robust data governance policies. The development of new technologies, such as blockchain, may offer innovative solutions for securing PHI.
Ultimately, protecting PHI requires a multi-faceted approach that involves collaboration between healthcare providers, technology vendors, regulators, and patients themselves. A proactive and vigilant approach is essential to safeguard patient privacy and maintain trust in the healthcare system.