Behavior Based Analysis Involves Using Baseline Information To Detect What

Imagine walking through a bustling airport, a sea of faces rushing past, each person seemingly on their own mission. Most blend seamlessly into the background, their actions predictable and ordinary. But what if you could discern the subtle nuances, the almost imperceptible deviations from the norm that could signal something amiss?
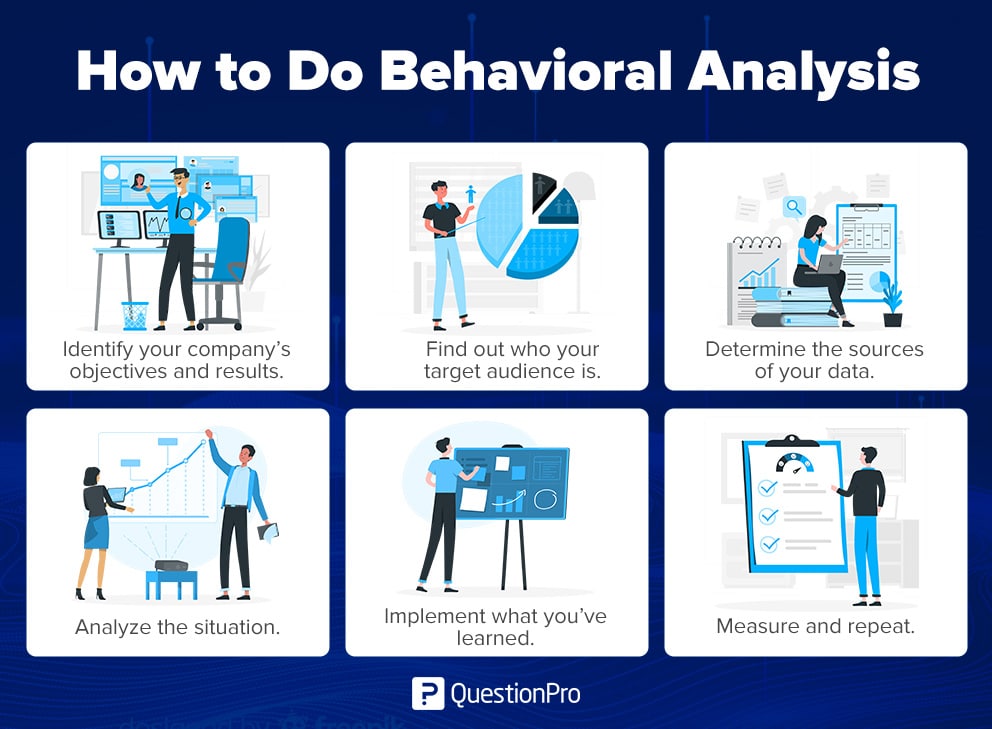
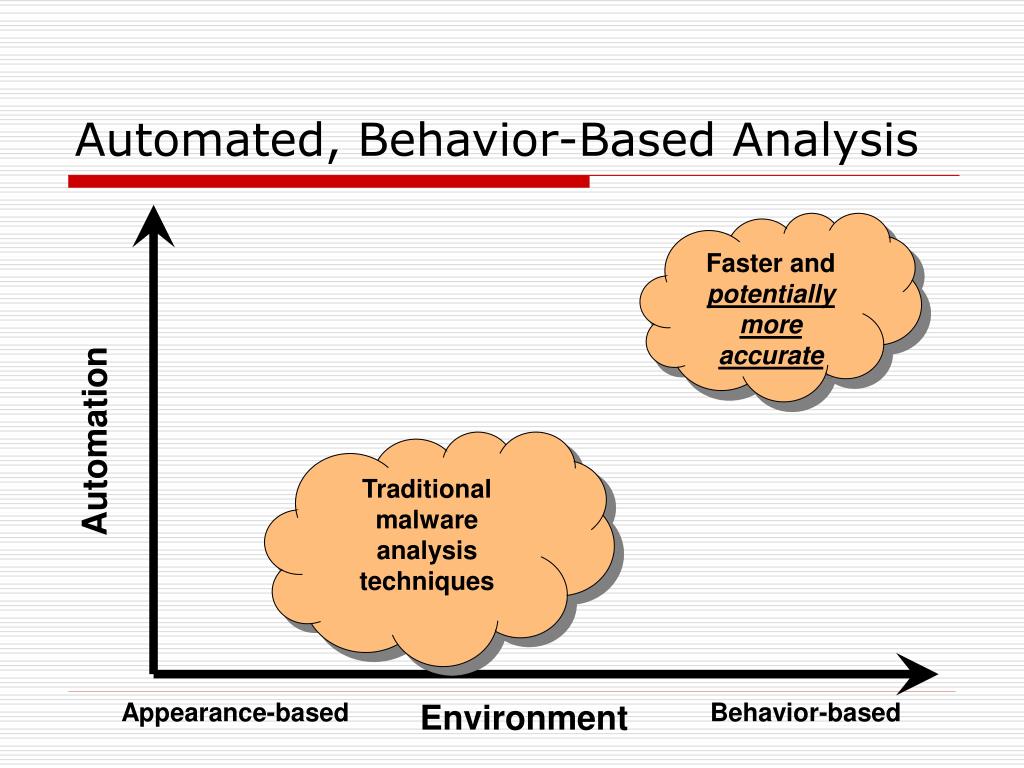
That's the promise of Behavior Based Analysis (BBA), a powerful technique that leverages baseline information to detect anomalies and potential threats. It's about moving beyond simply reacting to events and proactively identifying potential risks before they escalate.
Understanding Behavior Based Analysis
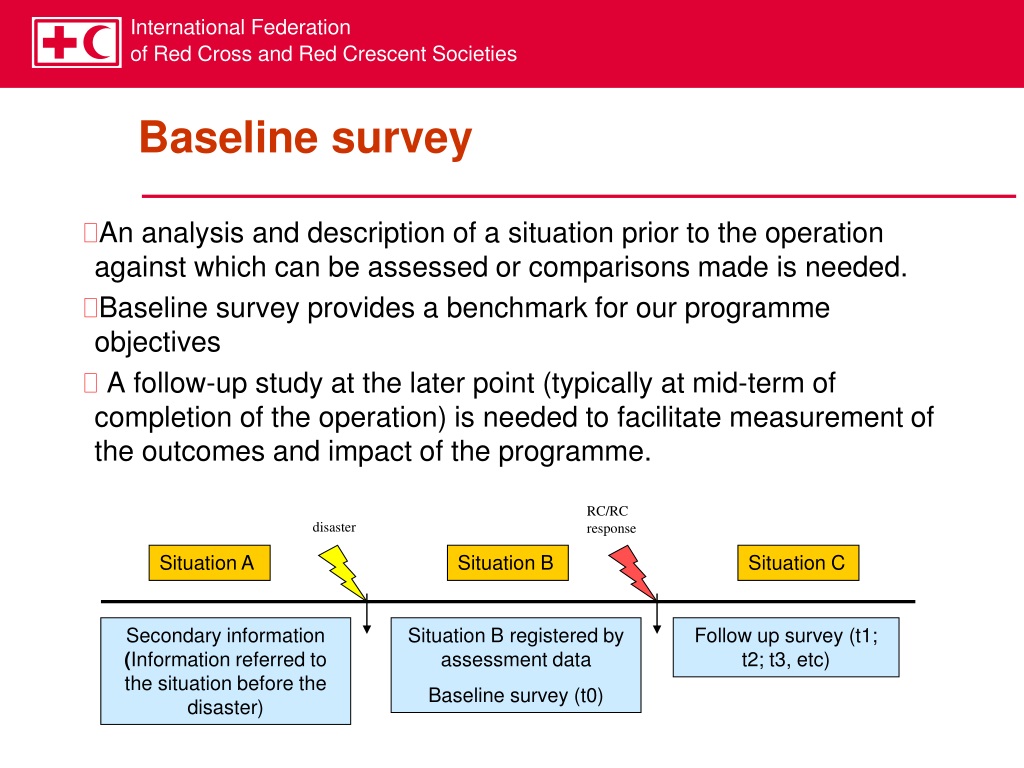
At its core, BBA relies on establishing a 'normal' or baseline understanding of behavior within a specific environment. This baseline is crucial for identifying deviations that could indicate suspicious activity. Think of it as understanding the usual rhythm of a city – the predictable flow of traffic, the regular patterns of pedestrian movement – before noticing a sudden, unexpected disruption.
The concept isn't new, but its application is evolving rapidly with advancements in technology. It's being deployed in diverse settings, from cybersecurity to retail, each tailored to the specific context and potential threats.
The Foundation: Baseline Information
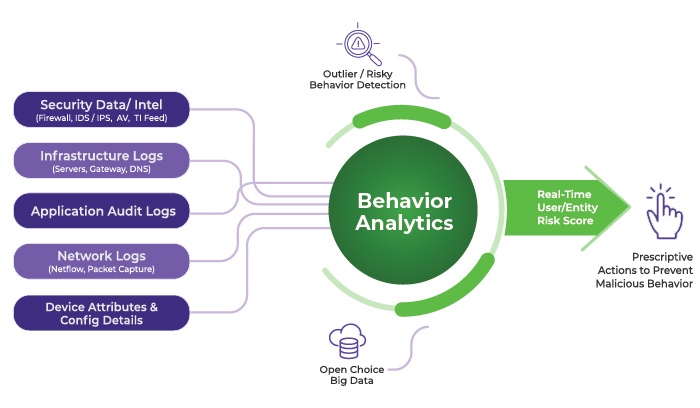
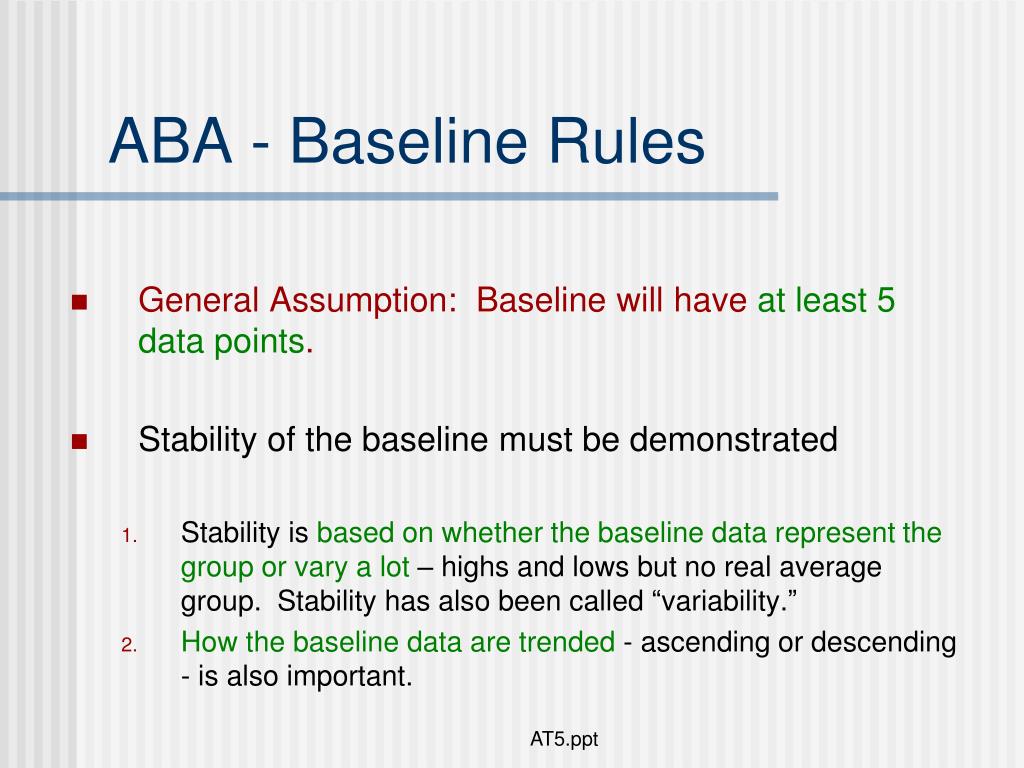
The success of BBA hinges on the quality and comprehensiveness of the baseline data. This data could include anything from historical transaction records in a financial institution to foot traffic patterns in a shopping mall.
In cybersecurity, for example, a baseline might encompass typical network traffic patterns, user access times, and the types of files commonly accessed. Anything outside of this established norm then becomes a red flag.
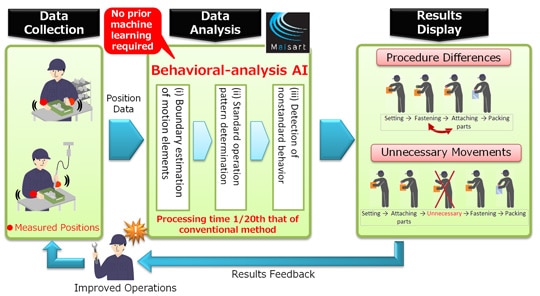
The process often involves analyzing large datasets and identifying statistical norms. The goal is to establish a robust and accurate representation of typical behavior.
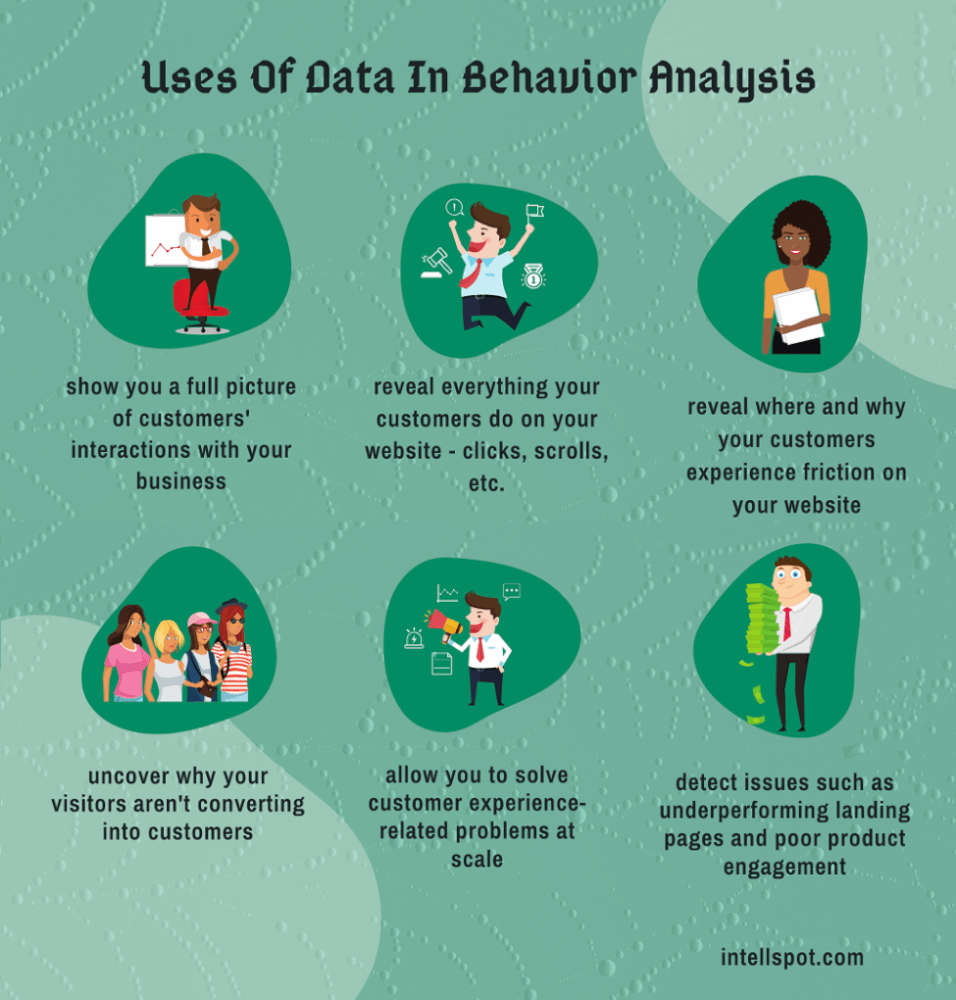
What BBA Detects: Anomalies and Deviations
Once the baseline is established, BBA systems continuously monitor for deviations from that norm. These deviations, or anomalies, are the key to detecting potential problems.
These anomalies can manifest in various forms. In a retail setting, it might be someone spending an unusually long time in a particular aisle, or repeatedly approaching a high-value item.
In a manufacturing plant, it could be a sudden spike in machine downtime or an unexplained increase in raw material usage.
Applications Across Industries
The versatility of BBA makes it applicable to a wide range of industries and scenarios. Here are a few notable examples:
- Cybersecurity: Identifying unusual network activity, detecting malware infections, and preventing data breaches. Companies like CrowdStrike utilize BBA extensively in their threat detection platforms.
- Fraud Detection: Identifying fraudulent transactions, detecting money laundering activities, and preventing financial crimes. Many banks and credit card companies use BBA to monitor transactions in real-time.
- Retail Security: Preventing shoplifting, identifying suspicious behavior, and improving overall security. Loss prevention officers can leverage BBA insights to proactively address potential threats.
- Healthcare: Monitoring patient behavior, detecting anomalies in vital signs, and improving patient safety. BBA can help healthcare providers identify patients at risk of falls or other adverse events.
- Aviation Security: Identifying potential security threats at airports, monitoring passenger behavior, and improving overall security. The Transportation Security Administration (TSA) uses BBA principles, alongside other security measures, to screen passengers and luggage.
Benefits and Challenges
The benefits of BBA are significant. It allows for proactive detection of threats, reduces false positives compared to rule-based systems, and can adapt to changing environments.
However, there are also challenges. Building an accurate baseline requires extensive data and careful analysis. It also requires continuous monitoring and updating as behavior patterns evolve.
Furthermore, ethical considerations are paramount. Ensuring that BBA systems are used responsibly and do not lead to biased or discriminatory outcomes is crucial.
The Future of Behavior Based Analysis
The future of BBA is closely tied to advancements in artificial intelligence (AI) and machine learning (ML). These technologies are enabling more sophisticated and nuanced analysis of behavioral data.
AI-powered BBA systems can automatically learn and adapt to changing patterns, making them more effective at detecting anomalies. They can also handle larger and more complex datasets, providing a more comprehensive view of behavior.
Furthermore, the integration of BBA with other security technologies, such as video surveillance and access control systems, is creating even more powerful security solutions.
Case Study: Cybersecurity Application
Consider a hypothetical cybersecurity scenario. A company establishes a baseline of normal network traffic patterns, user access times, and file access behavior. Then, an employee's account begins accessing files they've never accessed before, at odd hours, and from a location outside the company's network.
A BBA system would flag this as an anomaly, triggering an alert for security personnel. Further investigation might reveal that the employee's account has been compromised, allowing the company to take swift action to prevent a data breach.
This proactive approach is far more effective than simply reacting to a breach after it has already occurred.
Ethical Considerations and Responsible Implementation
While BBA offers significant security benefits, it's essential to address the ethical implications. Over-reliance on BBA can lead to profiling and discriminatory practices if not implemented carefully.
Transparency and fairness are paramount. Individuals should be aware of how their behavior is being monitored and have the opportunity to challenge any incorrect or biased assessments.
Data privacy is also a critical concern. Organizations must ensure that personal data is protected and used only for legitimate purposes.
Moving Forward: A Balanced Approach
The key to successful BBA lies in a balanced approach. This means combining BBA with other security measures, such as traditional rule-based systems and human oversight.
It also requires ongoing training and education for security personnel to ensure that they understand how to interpret BBA alerts and take appropriate action. Collaboration between data scientists, security professionals, and ethicists is essential.
Ultimately, the goal is to create a security ecosystem that is both effective and ethical, protecting individuals and organizations without compromising fundamental rights.
Conclusion
Behavior Based Analysis represents a significant step forward in our ability to detect and prevent threats. By understanding the 'normal' and identifying deviations, we can proactively address potential problems before they escalate. It's not about predicting the future with certainty, but about increasing our awareness and responsiveness to the subtle signs that something might be amiss.
As technology continues to evolve, BBA will become even more powerful and sophisticated. However, it's crucial to remember that technology is only a tool. The real power lies in our ability to use it responsibly and ethically, ensuring that it serves to protect and empower us all.
The journey toward a more secure and predictable world relies not just on algorithms and data, but on our collective commitment to using these tools wisely and with unwavering respect for human dignity and privacy.