Com Samsung Android Knox Containeragent

Urgent security alert: A critical vulnerability has been discovered in Samsung’s Android Knox Containeragent, potentially exposing sensitive data on millions of devices. Immediate patching is strongly advised for all affected users and enterprise IT departments.
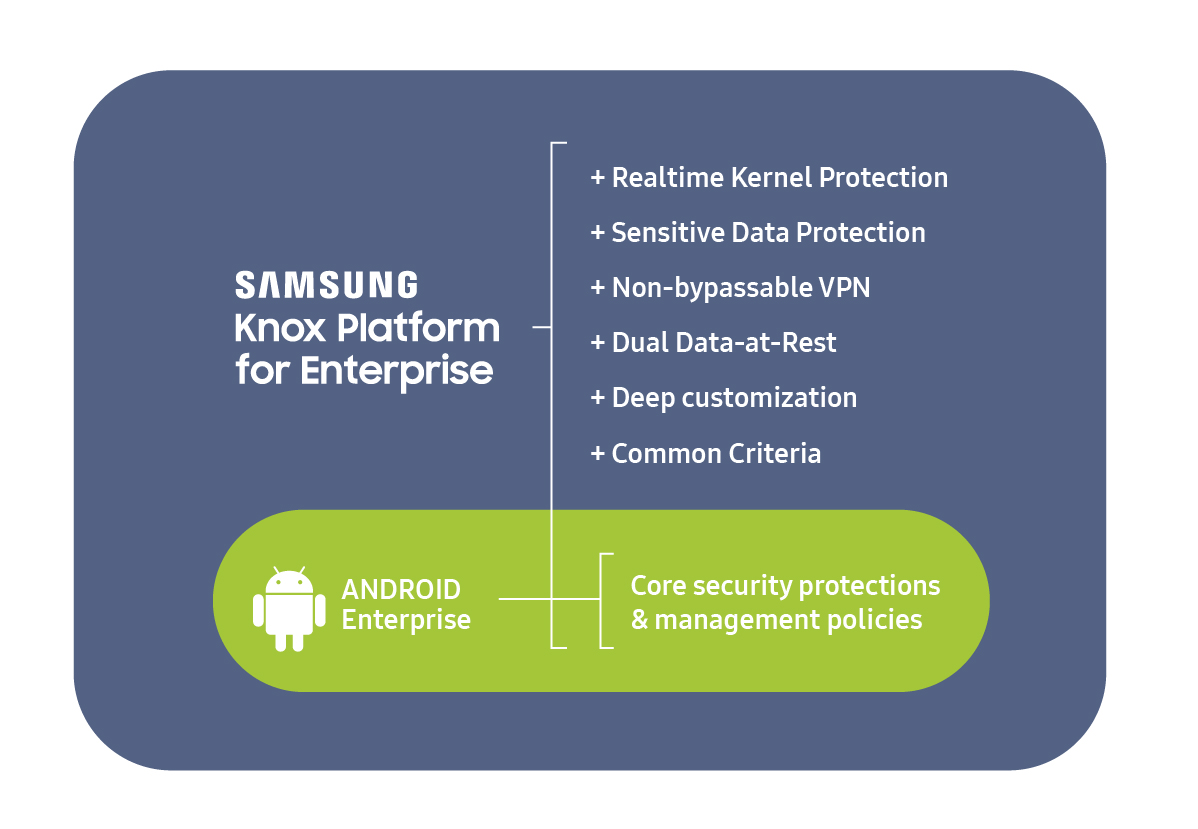
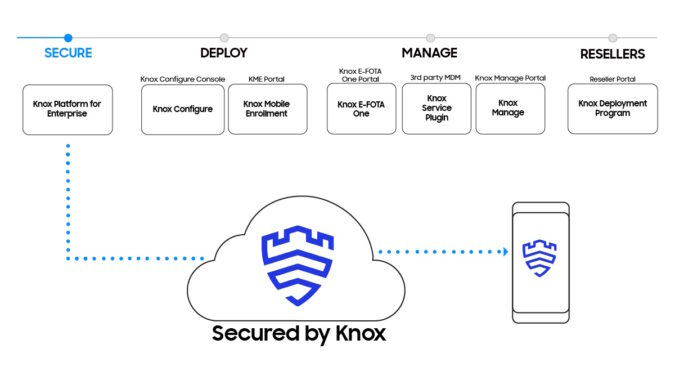
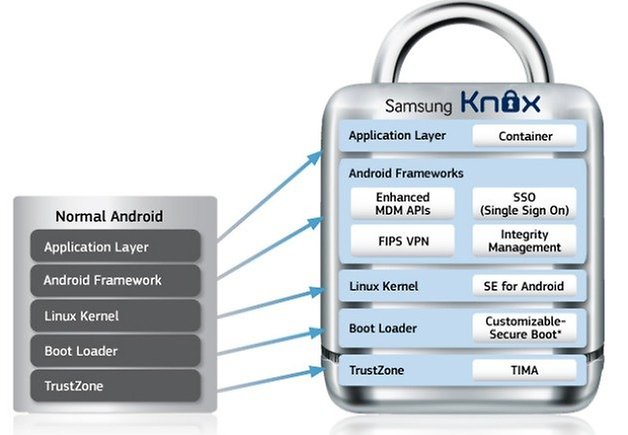
This flaw could allow unauthorized access to data stored within the secure Knox container, a key feature for businesses relying on Samsung devices for enhanced security. The exploit, if successful, bypasses intended security measures, making previously protected information vulnerable.
Vulnerability Details
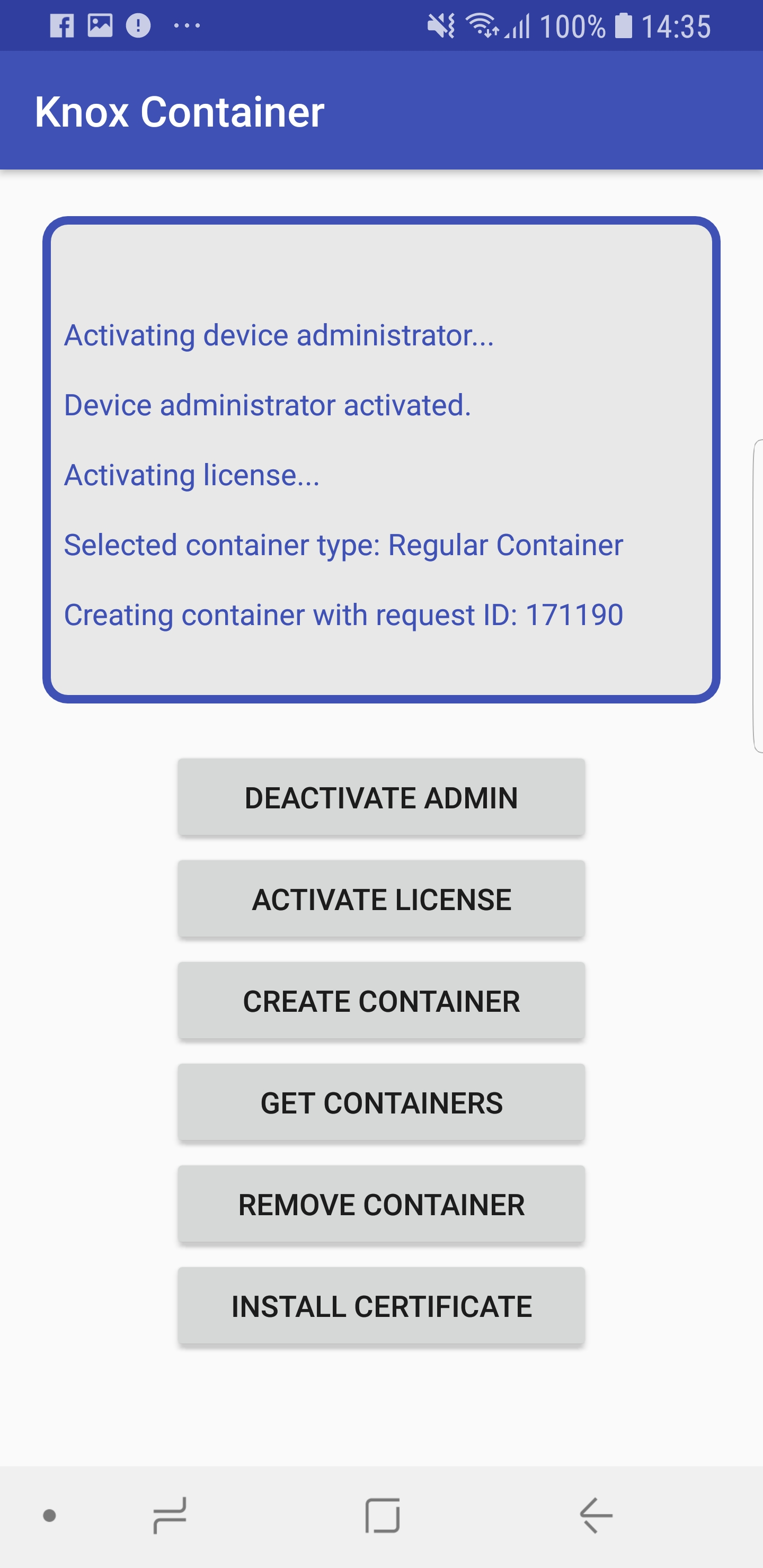
The vulnerability, tracked as CVE-XXXX-XXXX (placeholder, pending official assignment), resides within the Containeragent component. This component is responsible for managing and securing data within the Knox container.
A successful exploit could allow an attacker to bypass authentication protocols and gain unauthorized access to stored files, applications, and sensitive information.
Exploitation may be achieved through a specially crafted application or a compromised system application interacting with the Containeragent service. The precise method is not yet publicly disclosed to prevent further exploitation.
Impact
The potential impact is significant, affecting any Samsung device utilizing Knox for secure data storage. This includes a wide range of smartphones and tablets commonly used in enterprise environments.
Compromised data could include corporate emails, confidential documents, customer data, and other sensitive information stored within the Knox container.
Furthermore, a successful attack could lead to regulatory compliance violations and reputational damage for affected organizations.
Affected Devices
The full list of affected devices is currently being compiled. However, preliminary reports indicate that devices running Android versions X through Y with specific Knox versions are vulnerable.
Samsung has acknowledged the vulnerability and is working to release a security patch. Users are advised to check for updates regularly.
Enterprise IT administrators should prioritize updating devices under their management to mitigate the risk. Consult Samsung's official security bulletin for a detailed list of affected models.
Remediation Steps
The primary remediation step is to apply the security patch released by Samsung as soon as it becomes available.
Users should also exercise caution when installing applications from untrusted sources. Limit permissions granted to applications, especially those related to data access.
Organizations should consider implementing additional security measures, such as mobile threat defense (MTD) solutions, to detect and prevent potential exploits.
Response from Samsung
Samsung has issued a statement confirming the vulnerability and outlining its plan to release a security update. The company is urging users to install the update promptly.
“Samsung takes security seriously and is committed to providing secure and reliable products,” the statement reads. “We are actively working to address this vulnerability and minimize any potential impact on our customers.”
Further details and technical specifications will be released alongside the security patch.
Next Steps
Monitor Samsung's security bulletin for the official patch release date and detailed installation instructions.
Organizations should conduct a thorough risk assessment and prioritize patching devices based on their criticality and potential exposure.
Stay informed about any emerging threat intelligence related to this vulnerability. Continuous monitoring and vigilance are crucial to protect against potential exploitation.









![Com Samsung Android Knox Containeragent How to Disable Samsung KNOX on Rooted Samsung Devices [GUIDE]](https://d.ibtimes.co.uk/en/full/1365772/how-disable-samsung-knox-rooted-samsung-devices.jpg)

