Evaluate The Security Operations Company Zscaler On Phishing Simulation

The escalating sophistication of phishing attacks has thrust security vendors into the spotlight, demanding robust solutions that go beyond mere detection to proactive risk mitigation. Companies like Zscaler, a prominent player in cloud-based security, are increasingly evaluated not just on their ability to block threats, but also on their capacity to prepare employees for the inevitable human element in security breaches: falling prey to phishing attempts.
This article delves into an evaluation of Zscaler's capabilities in phishing simulation, examining its strengths, weaknesses, and overall effectiveness in enhancing organizational security posture. It will analyze the breadth and depth of their simulation offerings, scrutinizing the realism of their simulated attacks, the quality of their educational content, and the effectiveness of their reporting and analytics tools. Through analysis of publicly available information and expert perspectives, this evaluation aims to provide a balanced perspective on Zscaler's contribution to the fight against phishing.
Zscaler's Phishing Simulation Offering: An Overview
Zscaler offers phishing simulation as part of its broader security awareness training platform. This platform aims to educate employees about various cyber threats, including phishing, ransomware, and social engineering.
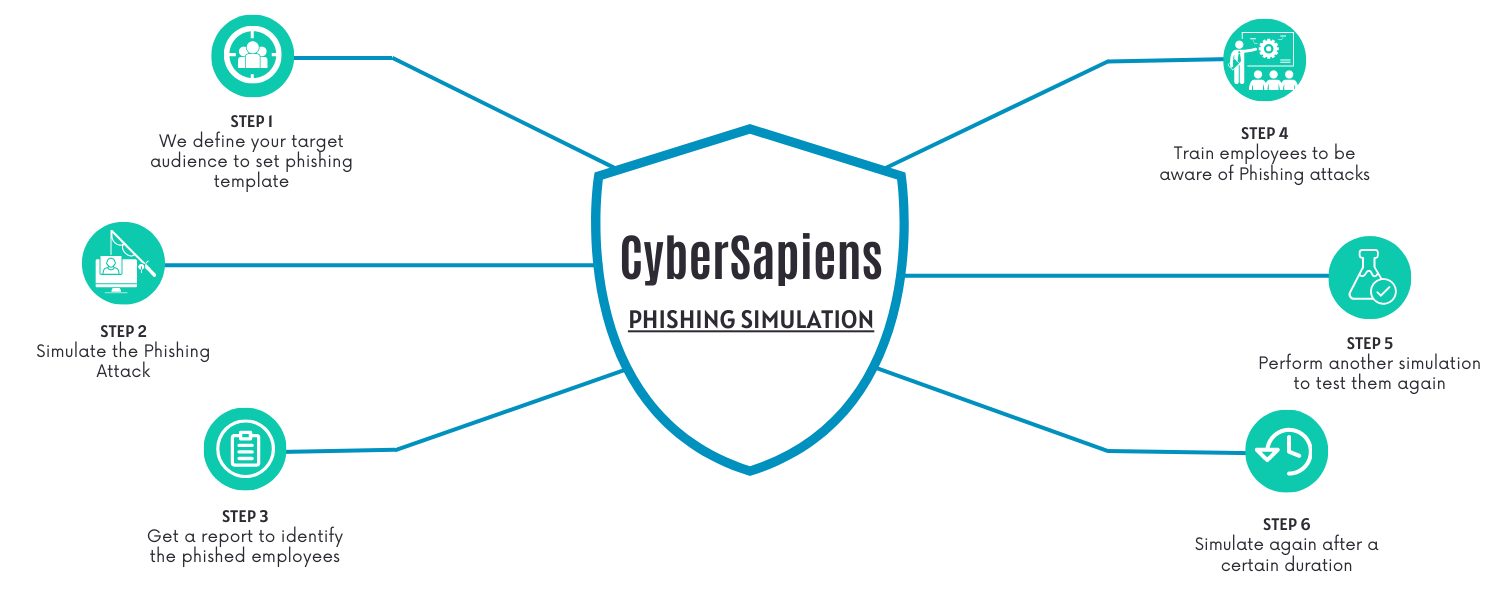
The phishing simulation component allows organizations to launch simulated phishing attacks against their employees, mimicking real-world scenarios to identify vulnerabilities and gauge employee awareness.
Key Features and Functionality
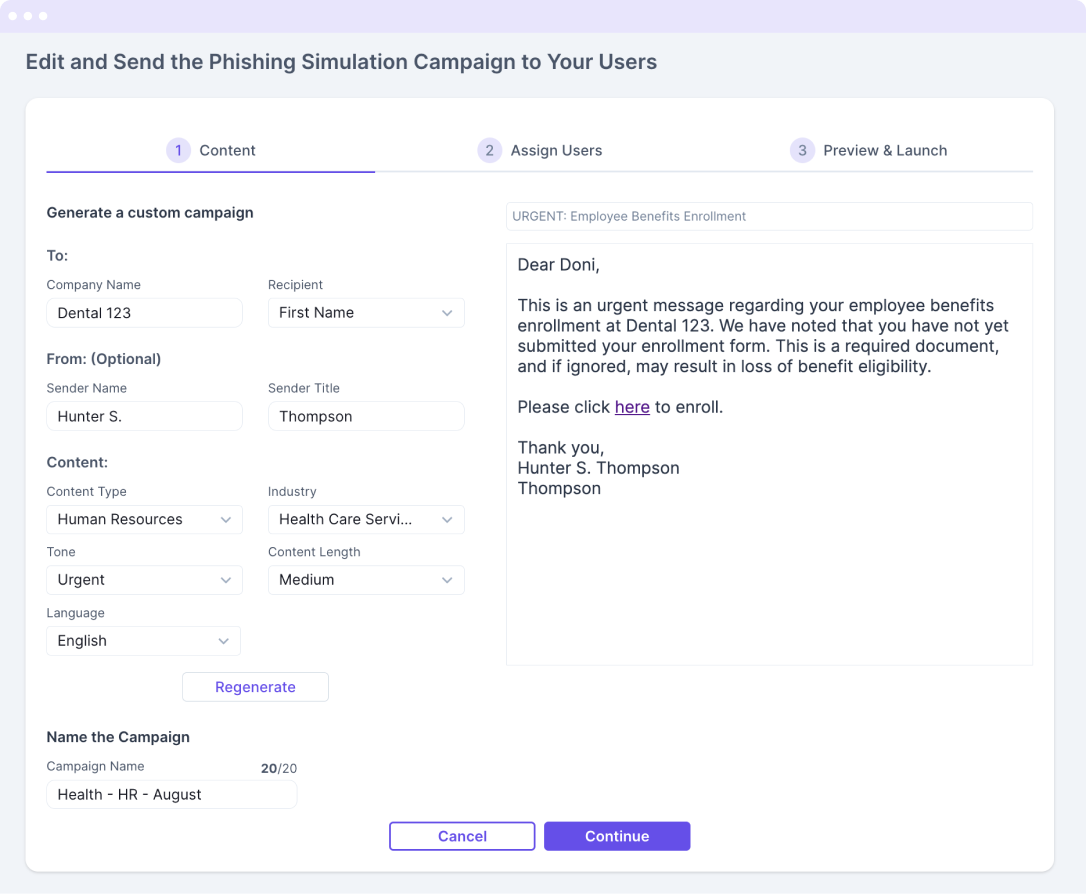
Zscaler's platform typically provides a range of features including customizable email templates, diverse attack scenarios, and integrated training modules. The platform also includes reporting and analytics dashboards.
These features are designed to help security teams understand employee susceptibility to phishing and measure the impact of training programs. The ability to tailor the simulation to specific organizational needs is a crucial aspect.
The system offers pre-built phishing templates designed to mimic real-world scams. These templates cover a variety of techniques, from credential harvesting to malware distribution. However, the real value comes from the ability to customize those templates.
Evaluating the Realism of Simulations
The effectiveness of any phishing simulation hinges on its realism. Simulations that are too generic or easily identifiable will fail to adequately prepare employees for genuine attacks. A critical aspect of realism is the ability to mimic current phishing trends. The quality of the Zscaler simulation’s realism is varied.
Reports indicate that Zscaler's simulation templates cover a range of phishing tactics, including spear-phishing, whaling, and business email compromise (BEC). These are tailored to specific roles and industries.
However, the extent to which Zscaler consistently updates its templates to reflect the very latest phishing scams is crucial and requires ongoing assessment. The rapidly evolving nature of phishing attacks demands constant vigilance and adaptation.
Integration with Threat Intelligence
The value of a phishing simulation platform significantly increases when integrated with real-time threat intelligence feeds. Integration with threat intelligence allows for the creation of simulations based on the latest phishing campaigns observed in the wild.
This ensures that employees are exposed to the actual threats they are most likely to encounter. While specifics on Zscaler’s threat intelligence integration are limited, the benefits of such integration are widely acknowledged within the industry.
Educational Content and Training Effectiveness
A successful phishing simulation program isn't solely about launching fake attacks; it's also about providing effective training to address identified vulnerabilities. The quality of the educational content and its delivery method are critical components. This education should be timely and relevant.
Zscaler's platform typically offers training modules that can be assigned to employees who fall for simulated phishing attacks. These modules often cover topics such as identifying phishing indicators, safe browsing practices, and password security.
The effectiveness of these training modules hinges on their engagement level, clarity, and relevance to the employee's role and responsibilities. A standardized, one-size-fits-all approach is unlikely to be as effective as personalized, role-based training.
Reporting and Analytics Capabilities
Robust reporting and analytics are essential for measuring the effectiveness of a phishing simulation program. Detailed reports allow security teams to track employee performance, identify high-risk individuals or departments, and assess the impact of training initiatives.
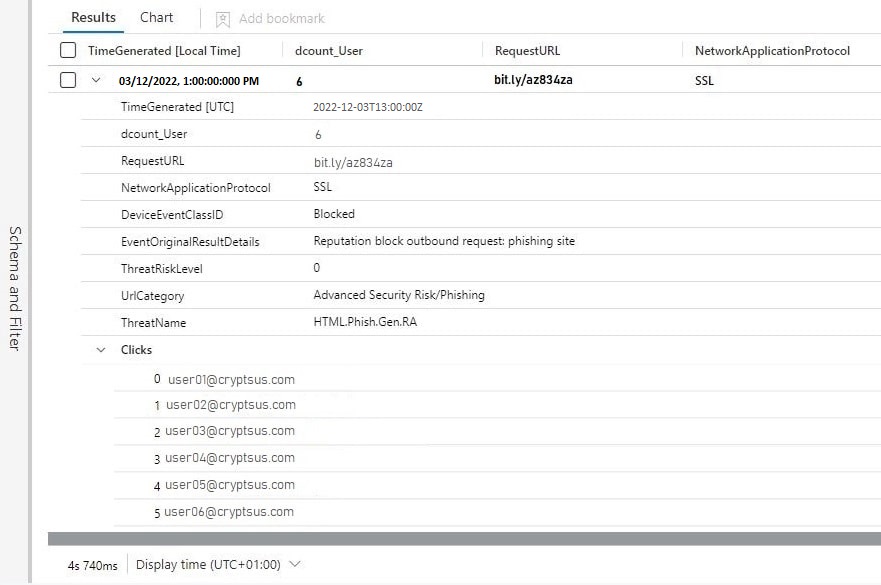
Zscaler's platform offers reporting dashboards that provide insights into key metrics such as click-through rates, compromise rates, and training completion rates. These dashboards allow for the visualization of data and identification of trends.
However, the depth and granularity of the reporting are important considerations. Security teams need the ability to drill down into the data to identify specific vulnerabilities and tailor their training programs accordingly. The reports should ideally allow for segmentation based on department, location, and job role, and the data is crucial.
Potential Limitations and Challenges
Despite the benefits of phishing simulation programs, there are potential limitations and challenges to consider. One key challenge is the risk of employee resentment or demotivation if the simulations are perceived as punitive or overly frequent. This can be countered with clear communication.
Another challenge is ensuring that the simulations are relevant and engaging for all employees, regardless of their technical expertise. A poorly designed or implemented program can be counterproductive, leading to decreased employee engagement and a negative impact on morale. Furthermore, relying solely on Zscaler for security awareness could create blind spots.
Organizations should also be mindful of the potential for confirmation bias, where security teams focus on metrics that support their existing beliefs or strategies, rather than objectively evaluating the program's effectiveness.
The Future of Phishing Simulation
The future of phishing simulation is likely to involve greater automation, personalization, and integration with other security tools. As phishing attacks become more sophisticated, simulation programs will need to evolve to keep pace. The simulations need to be more dynamic and realistic.
Artificial intelligence (AI) and machine learning (ML) are expected to play an increasingly important role in creating more realistic and targeted simulations. AI can be used to analyze employee behavior and tailor simulations to their individual vulnerabilities, leading to more effective training outcomes. This future will need to be carefully evaluated.
Ultimately, the success of any phishing simulation program depends on a holistic approach that combines realistic simulations, effective training, and ongoing monitoring and evaluation. Zscaler's platform, like all security solutions, must be continuously adapted and improved to meet the ever-evolving threat landscape. Therefore the company’s work will never be completed, but that is a good thing. The continual evaluation of such systems is extremely important.