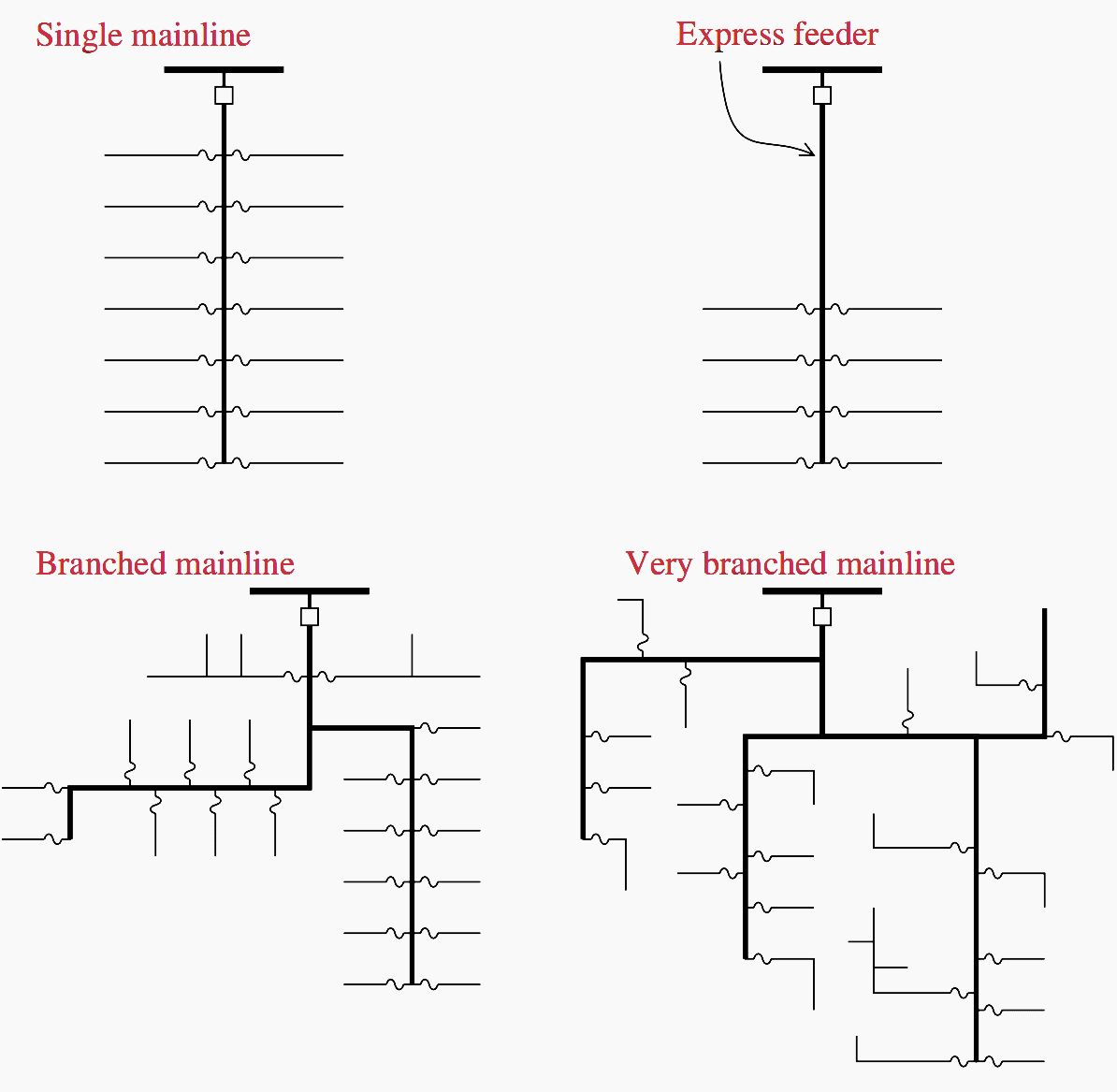
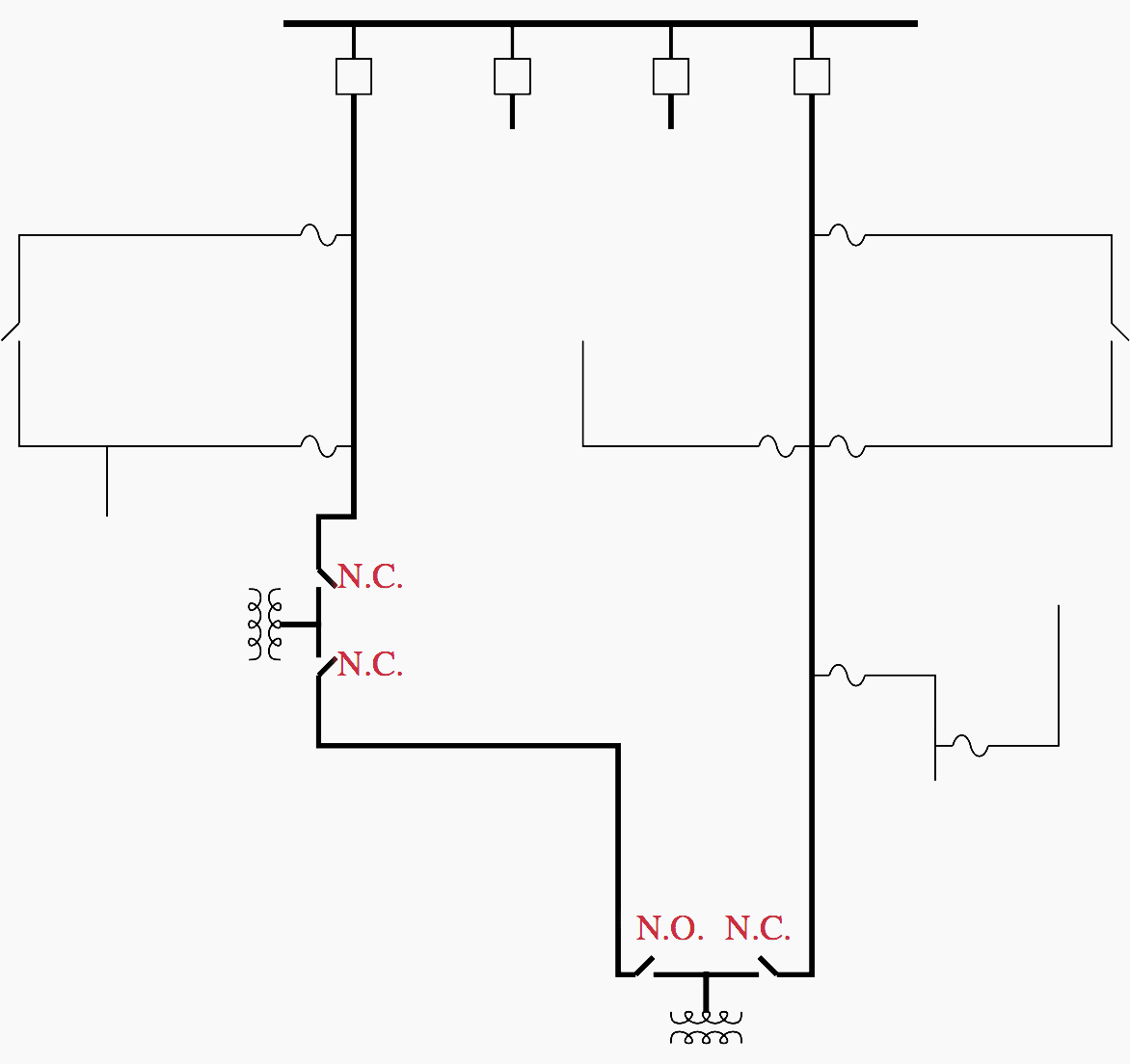
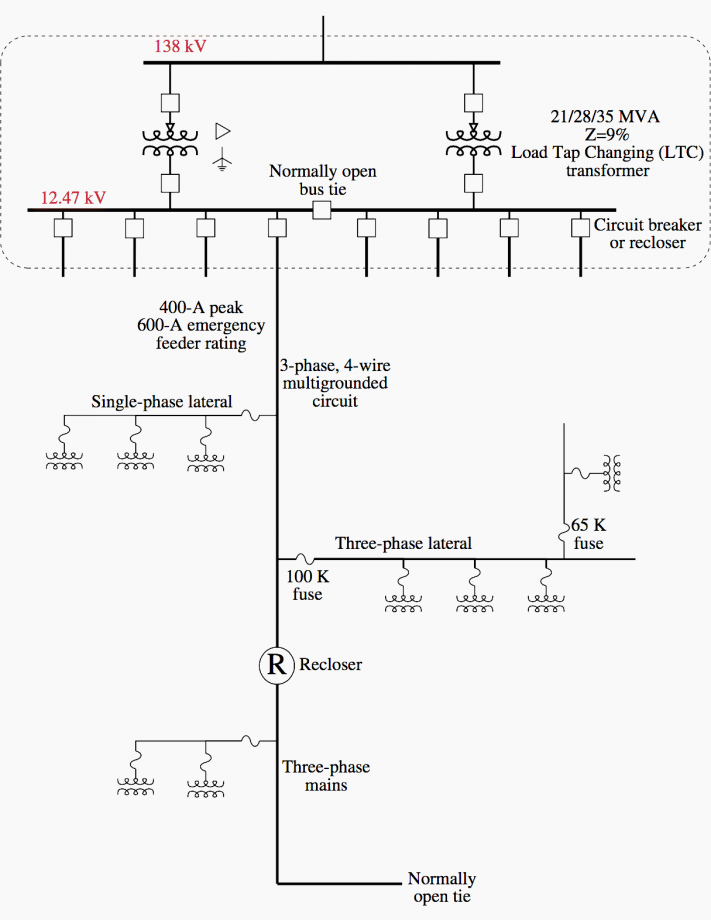
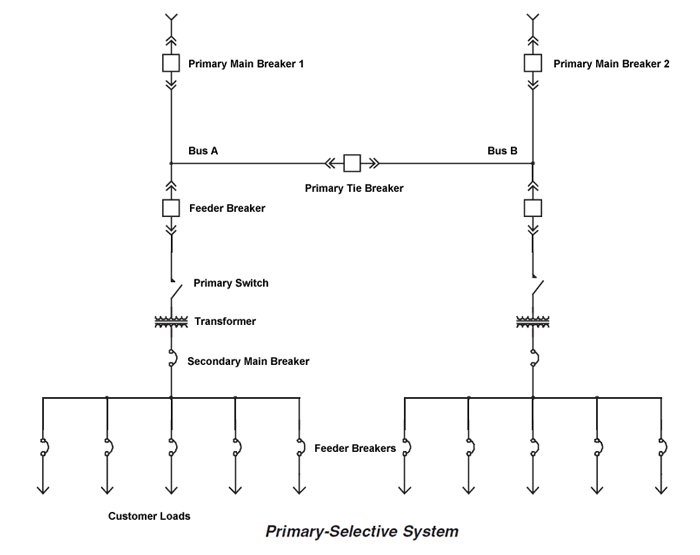
How To Open The Primary Distribution Gate

A coordinated emergency response team successfully breached the Primary Distribution Gate at 03:17 hours GMT today, averting a potential system-wide failure.
The successful override, employing a newly devised bypass sequence, comes after 72 hours of escalating pressure within the central network, threatening a catastrophic collapse of essential services.
Emergency Protocol Activation
At precisely 00:00 hours GMT on October 26, 2024, Emergency Protocol 73-Omega was activated following a critical pressure surge detected at the Primary Distribution Gate (PDG). The PDG, located within the Core Data Center in Geneva, Switzerland, serves as the primary nexus for global data flow.
Protocol 73-Omega dictates immediate implementation of bypass procedures in the event of irreversible pressure buildup. The surge was attributed to an unforeseen interaction between the new AI network (Project Nightingale) and legacy systems.
The Bypass Sequence: Operation Nightingale
The bypass sequence, designated "Operation Nightingale," was developed by a team of 12 engineers led by Dr. Aris Thorne at the Advanced Systems Research Institute in Menlo Park, California. The sequence exploits a known vulnerability in the PDG's security architecture dating back to its initial deployment in 2018.
The vulnerability, documented in classified internal reports, allowed for the insertion of a digitally encrypted override command. This command, when executed, forces the PDG's internal regulators to temporarily disengage.
Dr. Thorne's team spent 48 hours refining the sequence, accounting for the escalating pressure and potential cascading failures. The final sequence consisted of 17 distinct sub-routines, each designed to manage specific system processes within the PDG.
Execution at the Core Data Center
The execution of Operation Nightingale required physical access to the PDG's control terminal. A four-person team, comprised of specialists from the International Emergency Response Agency (IERA), was dispatched to the Core Data Center.
The team, led by Agent Eva Rostova, arrived at the facility at 02:00 hours GMT. They encountered no external resistance, but faced significant internal system interference.
Agent Rostova's team navigated the complex network architecture, encountering several automated security protocols. The key was to maintain the data stream between the control terminal and the Advanced Systems Research Institute, ensuring the completion of each sub-routine.
Critical Moments and the Successful Breach
At 03:05 hours GMT, the pressure within the PDG reached critical levels, triggering an automatic system shutdown warning. Agent Rostova's team was racing against time.
Sub-routine 13 encountered an unexpected error, threatening to abort the entire sequence. Dr. Thorne's team remotely adjusted the parameters, allowing the sequence to continue with a modified pathway.
At 03:17 hours GMT, the final sub-routine executed successfully, disengaging the PDG's internal regulators. The pressure immediately began to stabilize, averting the potential system-wide collapse.
Immediate Aftermath and Stabilization
Following the successful breach, IERA personnel initiated a controlled system rollback, reverting to a pre-surge configuration. This process is expected to take 12-18 hours.
Essential services are currently operating at a reduced capacity. Full functionality is projected to be restored by 18:00 hours GMT on October 27, 2024.
Dr. Thorne's team remains on standby, monitoring the PDG's performance and addressing any residual anomalies. An investigation is underway to determine the root cause of the initial pressure surge and prevent future incidents.