Understanding That Protection Of Sensitive Unclassified Information Is

Imagine a bustling office, papers stacked high, computers humming with activity. Information flows freely, ideas sparking in every corner. But within this vibrant ecosystem lies data that, while not classified as top secret, requires careful safeguarding. It's the kind of information that, if mishandled, could lead to significant disruptions, reputational damage, or even competitive disadvantages.
Understanding the nuances of protecting Sensitive Unclassified Information (SUI) is paramount in today's interconnected world. This article delves into the importance of SUI protection, explores the potential risks associated with its compromise, and provides practical strategies for organizations and individuals to enhance their security posture.
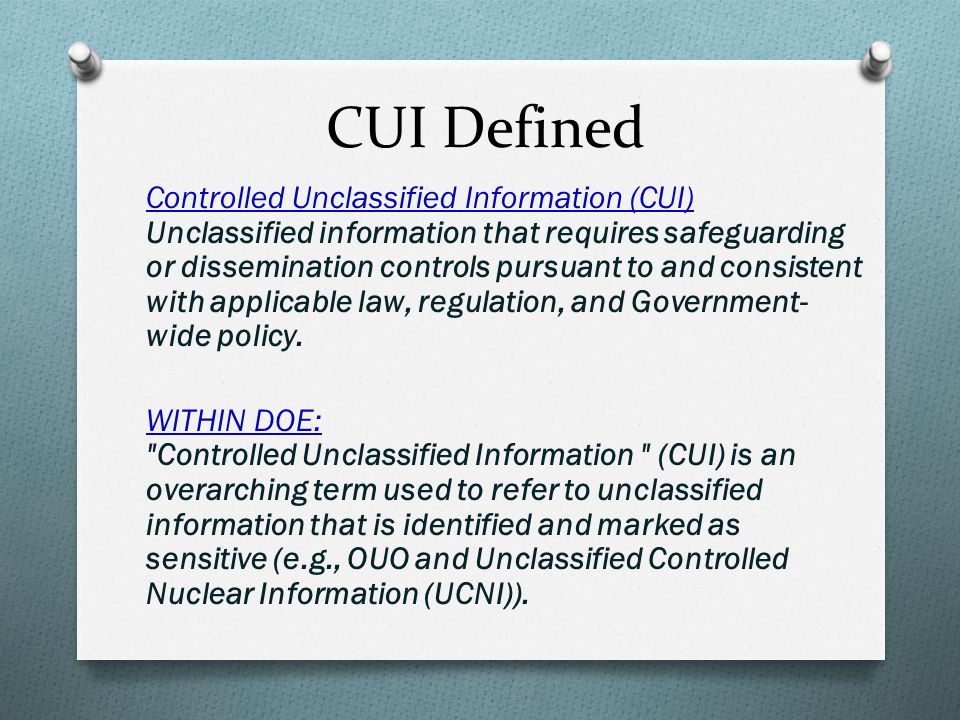
SUI refers to information that, while not formally classified under national security guidelines, is sensitive and requires protection from unauthorized disclosure, modification, destruction, or loss. This can encompass a wide array of data, ranging from personally identifiable information (PII) to proprietary business strategies and critical infrastructure details. The crucial aspect is that its compromise could adversely affect an organization or individual's interests.
The Rise of SUI and Why It Matters
The digital revolution has dramatically increased the volume and accessibility of information. With this expansion, the lines between classified and unclassified data have blurred, creating new challenges for information security. Organizations now grapple with vast amounts of SUI residing in various digital and physical formats.
The consequences of SUI breaches can be significant. For example, a healthcare provider's failure to protect patient data could lead to violations of the Health Insurance Portability and Accountability Act (HIPAA), resulting in hefty fines and reputational harm. Similarly, a manufacturer's proprietary design specifications falling into the hands of competitors could erode its competitive advantage.
According to a report by the Ponemon Institute, the average cost of a data breach in 2023 reached $4.45 million. While this figure includes breaches involving classified data, it highlights the substantial financial burden associated with compromising sensitive information of all kinds. Beyond the financial impact, SUI breaches can erode trust, damage relationships with stakeholders, and disrupt operations.
Sources of SUI Vulnerabilities
Numerous factors can contribute to SUI vulnerabilities. One of the most common is human error. Employees may inadvertently disclose sensitive information through phishing scams, weak passwords, or careless handling of data.
Insider threats also pose a significant risk. Disgruntled employees or malicious actors with access to sensitive data can deliberately leak or steal information. These threats are often difficult to detect because insiders have legitimate access to the systems and data they target.
Technical vulnerabilities in software and hardware can also create opportunities for attackers to exploit SUI. Outdated systems, unpatched software, and misconfigured security settings can leave organizations vulnerable to cyberattacks.
Physical security weaknesses can further compromise SUI. Unsecured buildings, inadequate access controls, and improper disposal of documents can all lead to data breaches.
Strategies for Protecting SUI
Protecting SUI requires a multi-faceted approach that addresses both technical and human factors. Organizations should implement robust security controls to prevent unauthorized access to sensitive data. These controls may include strong authentication mechanisms, data encryption, access control lists, and intrusion detection systems.
Employee training is crucial. Educating employees about SUI risks and best practices can help reduce the likelihood of human error. Training programs should cover topics such as phishing awareness, password security, data handling procedures, and reporting security incidents.
Developing and enforcing clear policies and procedures for handling SUI is also essential. These policies should outline acceptable use of company resources, data retention guidelines, and procedures for reporting security breaches. Regular audits and assessments can help identify vulnerabilities and ensure that security controls are effective.
Key Areas of Focus:
Data Loss Prevention (DLP): Implementing DLP tools can help prevent sensitive data from leaving the organization's control. These tools can monitor network traffic, email communications, and removable media to detect and block unauthorized data transfers.
Access Control: Enforcing strict access controls ensures that only authorized personnel can access sensitive data. This involves implementing role-based access control (RBAC) and regularly reviewing access privileges.
Encryption: Encrypting sensitive data, both at rest and in transit, protects it from unauthorized access even if it is intercepted.
Incident Response: Having a well-defined incident response plan is crucial for minimizing the impact of a data breach. This plan should outline procedures for detecting, containing, eradicating, and recovering from security incidents.
Physical Security: Maintaining strong physical security measures, such as secure access controls and surveillance systems, is essential for protecting SUI stored in physical form.
Individual Responsibility in Protecting SUI
Protecting SUI is not solely the responsibility of organizations. Individuals also play a crucial role in safeguarding sensitive information. Practicing good cyber hygiene can significantly reduce the risk of data breaches.
Using strong passwords, being wary of phishing scams, and keeping software up to date are all essential steps. Individuals should also be mindful of the information they share online and avoid posting sensitive data on social media or other public platforms.
Furthermore, individuals should be aware of their organization's SUI policies and procedures and follow them diligently. Reporting suspected security breaches promptly is crucial for mitigating potential damage.
Looking Ahead: The Future of SUI Protection
As technology continues to evolve, the challenges of protecting SUI will only become more complex. Organizations must stay ahead of the curve by adopting innovative security solutions and adapting their security strategies to address emerging threats.
Artificial intelligence (AI) and machine learning (ML) are playing an increasingly important role in SUI protection. These technologies can be used to detect anomalies, identify suspicious activity, and automate security tasks.
Collaboration and information sharing are also essential for effective SUI protection. Organizations should work together to share threat intelligence and best practices. By sharing information, organizations can improve their ability to detect and respond to cyberattacks.
In conclusion, understanding and actively protecting Sensitive Unclassified Information is no longer a suggestion but a necessity. It requires a collaborative, multi-faceted approach, blending technological safeguards with informed human behavior. As we navigate an increasingly interconnected world, prioritizing SUI protection will ensure continued innovation, trust, and security for organizations and individuals alike. It is not merely about compliance, but about safeguarding valuable assets and maintaining a competitive edge in an ever-evolving digital landscape.



 A Guide for Government Contractors (2).png)




.jpg)


+information+definition.jpg)



+Information.jpg)

