When Securing A Database Ssl Encryption Ensures That Others
Imagine a bustling marketplace, traders shouting prices, goods changing hands. But instead of physical wares, think of data – sensitive customer information, intricate financial records, proprietary business strategies – all flowing through the digital arteries of the internet. Now picture shadowy figures lurking in the corners, eager to intercept and exploit this valuable information. This is the reality of data security in the modern age, and SSL encryption acts as a vigilant guard, ensuring that these digital transactions remain private and secure.
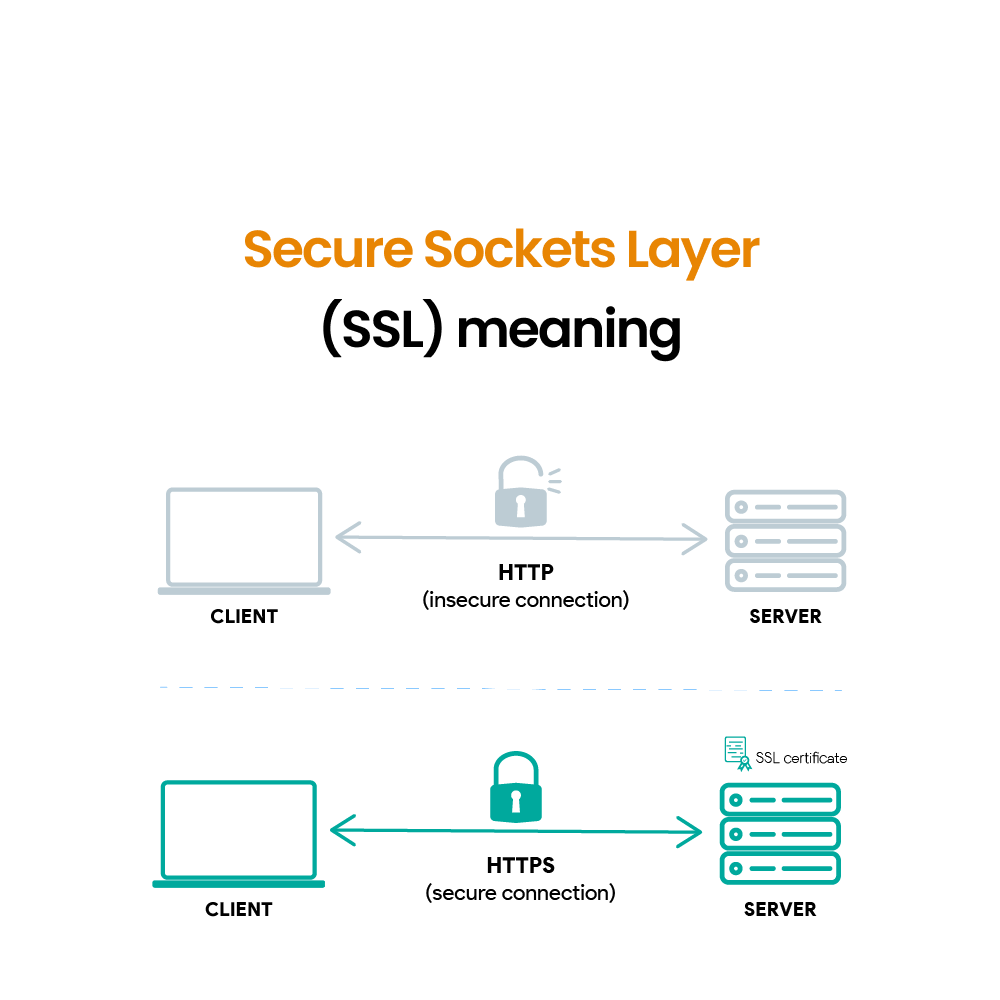
At its core, SSL (Secure Sockets Layer) encryption, now largely superseded by its successor TLS (Transport Layer Security), is a cornerstone of database security. It ensures that sensitive data transmitted between a client (like a user's computer) and a database server remains confidential and tamper-proof. This article will delve into why securing a database with SSL/TLS encryption is paramount, highlighting its importance in protecting sensitive information from unauthorized access and manipulation.
The Silent Guardian: SSL/TLS Encryption Explained
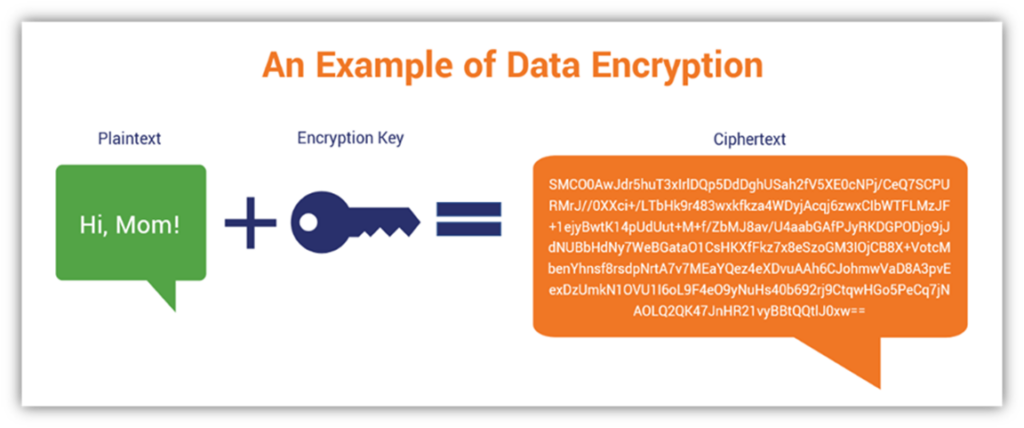
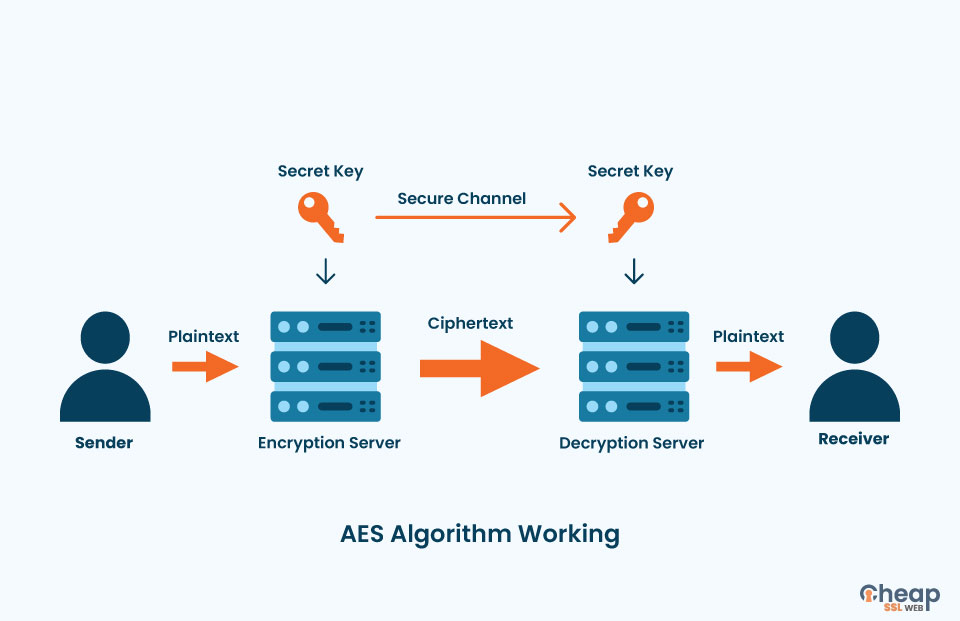
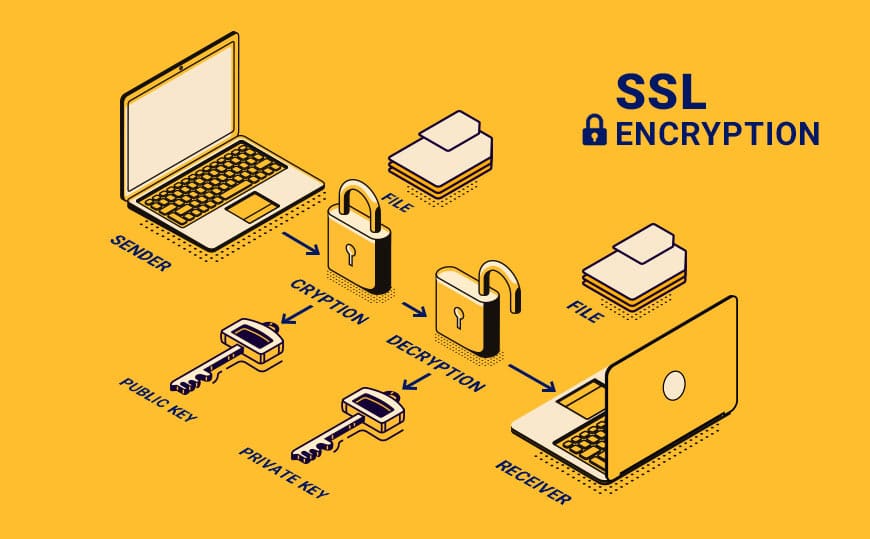
SSL/TLS encryption creates a secure tunnel for data transmission. It uses cryptographic algorithms to scramble data, rendering it unreadable to anyone who doesn't possess the correct decryption key.
Think of it like sending a letter in a locked box. Only the person with the key can open the box and read the contents. Without encryption, data travels in plain text, like an open postcard, vulnerable to interception.
Protecting Data in Transit
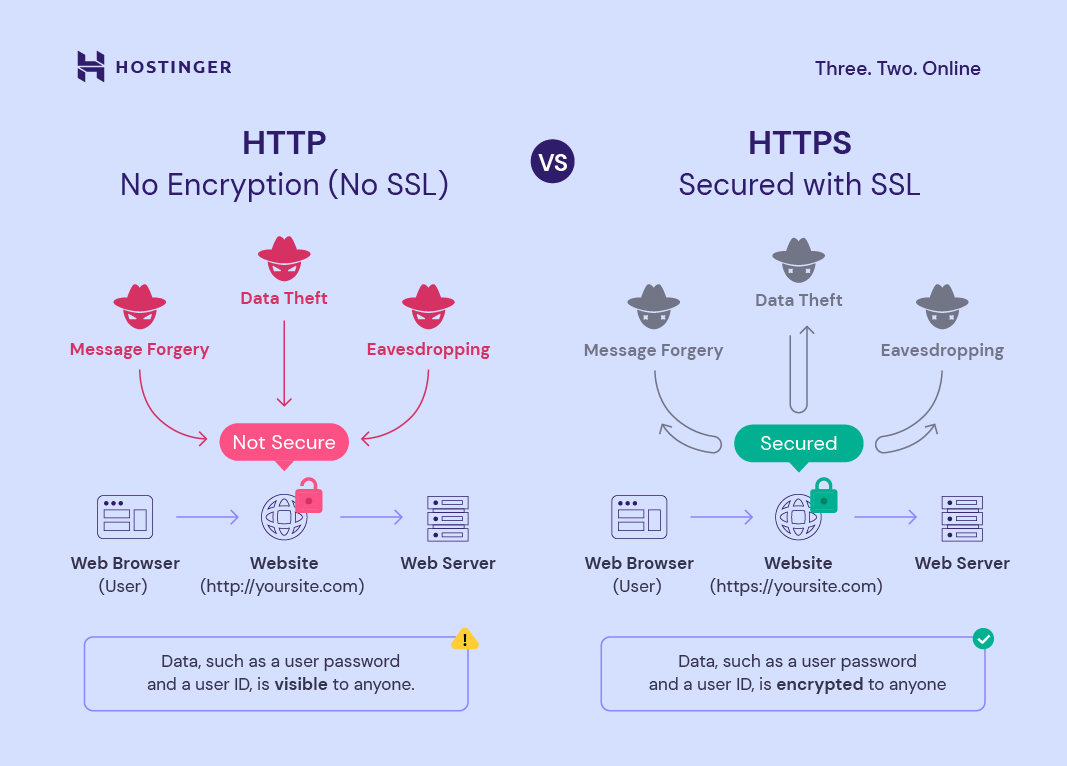
The primary function of SSL/TLS is to protect data while it's in transit. This is crucial because data travels across various networks and servers, increasing the risk of interception.
Without encryption, attackers can use network sniffing tools to capture sensitive information. Credit card numbers, usernames, passwords – all vulnerable if sent in plain text.
SSL/TLS ensures that even if data is intercepted, it's just a jumble of unreadable characters, useless to the attacker.
Authentication: Verifying Identity
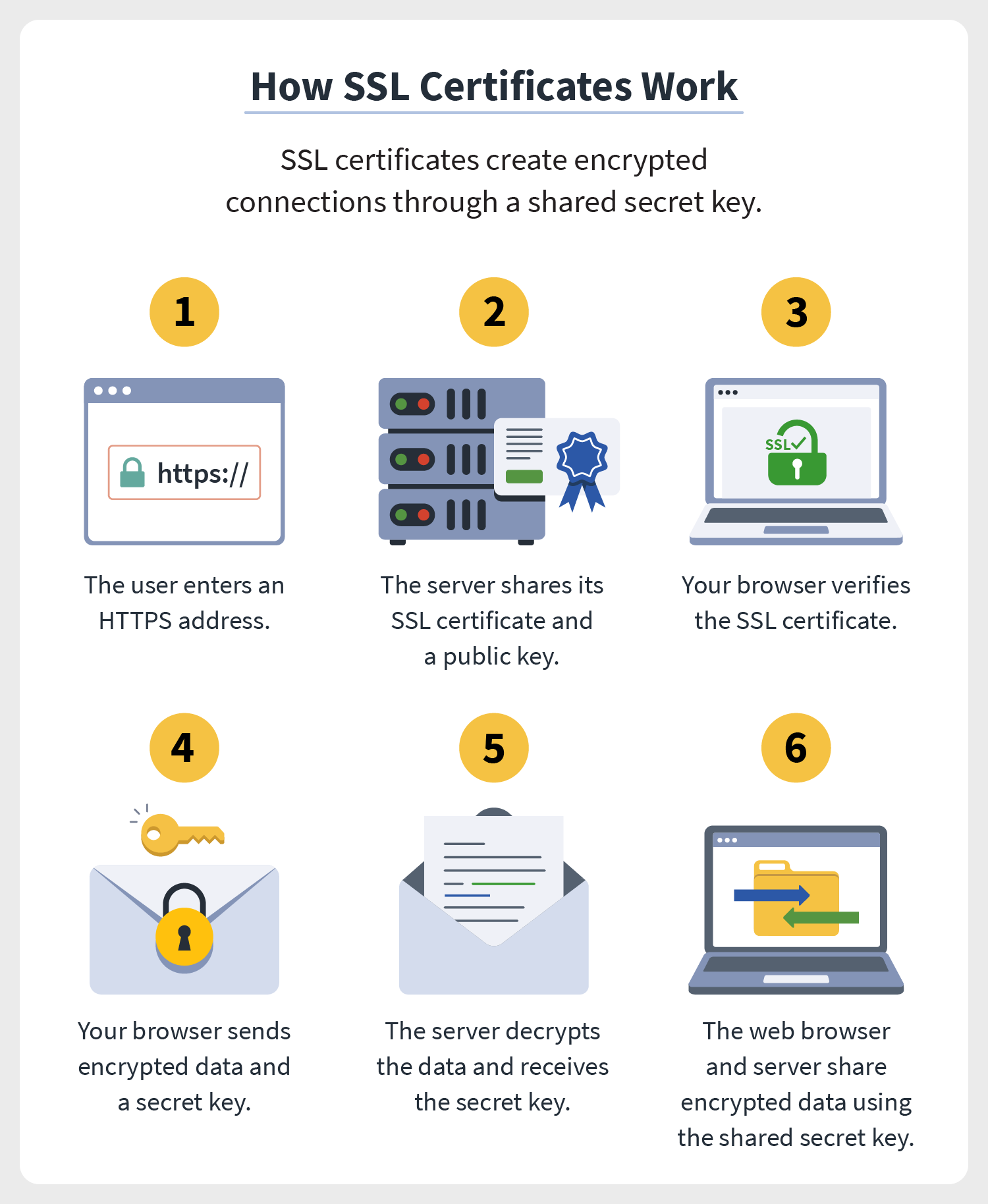
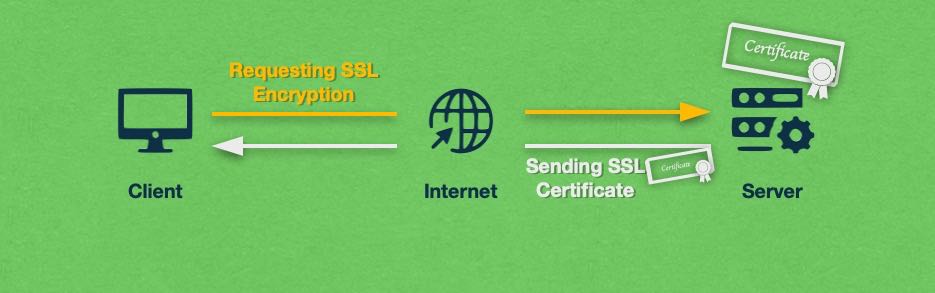
SSL/TLS also plays a vital role in authentication. It helps verify the identity of the server the client is connecting to.
This is important because attackers can set up fake websites that mimic legitimate ones to steal information. These are called phishing attacks.
SSL/TLS certificates act as digital IDs, confirming that the server is who it claims to be. Browsers display a padlock icon to indicate that the connection is secure and authenticated.
Why SSL/TLS Encryption is Non-Negotiable
Securing a database with SSL/TLS encryption is no longer optional; it's a necessity. The consequences of failing to do so can be devastating.
Data breaches can result in significant financial losses, reputational damage, and legal liabilities. Customers lose trust, and businesses can face hefty fines for non-compliance with data protection regulations.
Compliance with Regulations
Many data protection regulations, such as GDPR (General Data Protection Regulation) and HIPAA (Health Insurance Portability and Accountability Act), mandate the use of encryption to protect sensitive data.
Failing to comply with these regulations can result in severe penalties. Encryption is a fundamental requirement for demonstrating due diligence in protecting personal information.
According to a report by IBM, the average cost of a data breach in 2023 was $4.45 million. Implementing SSL/TLS encryption is a proactive step in mitigating this risk.
Protecting Customer Data
Customers entrust businesses with their personal information, including credit card numbers, addresses, and medical records.
It's a moral and ethical obligation to protect this information. SSL/TLS encryption is a critical tool for fulfilling this obligation.
By securing data in transit, businesses can prevent sensitive customer information from falling into the wrong hands. This helps maintain customer trust and loyalty.
Preventing Data Tampering
SSL/TLS encryption not only protects data from being intercepted but also prevents it from being tampered with.
The encryption process includes a mechanism for verifying the integrity of the data. If the data is altered in any way during transmission, the decryption process will fail.
This ensures that the data received is exactly the same as the data sent. This is particularly important for financial transactions and other sensitive data where accuracy is critical.
Implementing SSL/TLS Encryption: A Practical Guide
Implementing SSL/TLS encryption is a straightforward process. Most database management systems (DBMS) offer built-in support for SSL/TLS.
The first step is to obtain an SSL/TLS certificate from a trusted Certificate Authority (CA). These certificates verify the identity of the server.
Once the certificate is installed, the DBMS can be configured to use SSL/TLS encryption. This typically involves enabling the feature in the DBMS configuration file and specifying the path to the certificate file.
Choosing the Right Certificate
There are different types of SSL/TLS certificates available, each offering different levels of validation and features.
For example, Domain Validated (DV) certificates offer basic validation, while Organization Validated (OV) and Extended Validation (EV) certificates provide more comprehensive validation.
The choice of certificate depends on the specific needs and requirements of the business. For businesses that handle sensitive customer data, EV certificates are often recommended.
Regular Updates and Maintenance
SSL/TLS certificates have an expiration date. It's important to renew them before they expire to avoid disruptions in service.
Additionally, it's important to keep the DBMS and the underlying operating system up to date with the latest security patches. These patches often include fixes for vulnerabilities that could be exploited by attackers.
Regular security audits can also help identify and address potential vulnerabilities in the database security configuration.
The Future of Database Security
As technology evolves, so do the threats to database security. Attackers are constantly developing new and sophisticated techniques to bypass security measures.
SSL/TLS encryption remains a critical component of database security, but it's important to stay informed about the latest threats and best practices. New encryption algorithms and protocols are constantly being developed to enhance security.
Furthermore, adopting a layered security approach, which includes firewalls, intrusion detection systems, and access control mechanisms, is essential for providing comprehensive protection for sensitive data.
Conclusion
In the relentless digital landscape, securing databases with SSL/TLS encryption is no longer a luxury, but a fundamental necessity. It’s the bedrock of trust, the silent guardian that protects sensitive information from prying eyes and malicious intent. By implementing and maintaining robust encryption protocols, organizations not only safeguard their data but also foster a culture of security and responsibility.
As we navigate the ever-evolving world of cybersecurity, remembering the core principles of data protection, with SSL/TLS at the forefront, will be crucial in building a safer and more secure digital future for everyone.