Which Of The Following Factors Would Be Considered De-identified Information

Imagine you're a researcher, diligently sifting through mountains of data, trying to unlock secrets hidden within. You want to understand trends in patient health, optimize public services, or even personalize user experiences. But there's a catch: you need to protect the privacy of the individuals represented in that data.
The challenge lies in striking a balance between extracting valuable insights and ensuring that no one can identify the people behind the numbers. This is where the concept of de-identification comes into play. But what specific pieces of information need to be removed or altered to truly achieve this crucial goal?
This article dives into the factors that would be considered de-identified information, shedding light on the safeguards that protect individual privacy while allowing researchers and analysts to unlock the power of data. Understanding these factors is essential for anyone working with sensitive information, from healthcare professionals to data scientists and policymakers.
Understanding De-identification
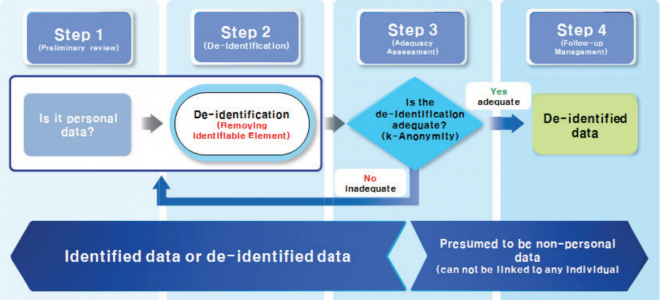
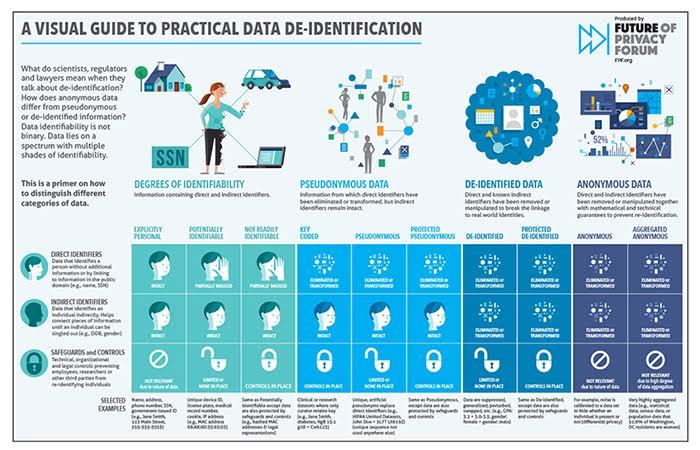
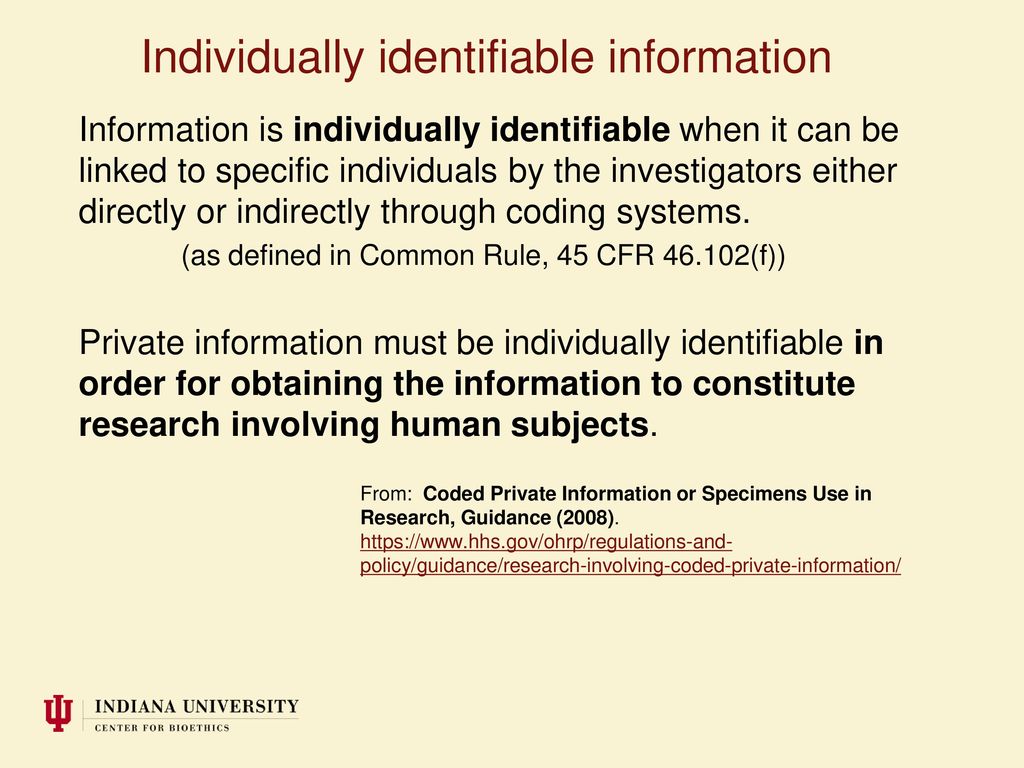
De-identification is the process of removing or obscuring any information that could potentially identify an individual. This allows data to be used for research, analysis, and other purposes without compromising privacy. Federal regulations, like the Health Insurance Portability and Accountability Act (HIPAA), provide guidelines on what constitutes de-identified information.
The goal is to create a dataset where the risk of re-identification is very low. Different approaches to de-identification exist, each with its own strengths and weaknesses. The key is choosing the method that best suits the specific data and intended use.
The HIPAA Safe Harbor Method
One of the most widely recognized de-identification methods is the HIPAA Safe Harbor method. This approach requires the removal of 18 specific identifiers, which, if present, would make it relatively easy to identify an individual. Let’s take a closer look at these.
1. Names: This seems obvious, but all direct identifiers, including full names, initials, and even nicknames, must be removed. Simply redacting a full name is often the first step in the de-identification process.
2. Geographic Subdivision Smaller Than a State: Information like street addresses, city, county, precinct, zip codes and their equivalent geocodes must be removed. Even seemingly innocuous location data can be used to narrow down potential individuals, especially in smaller communities.
3. All Elements of Dates (Except Year) for Dates Directly Related to an Individual: This includes birth dates, admission dates, discharge dates, and death dates. Reducing the granularity of dates to just the year significantly reduces the risk of re-identification.
4. Telephone Numbers: Phone numbers are direct identifiers and must be removed entirely. They can be easily used to trace back to a specific individual.
5. Fax Numbers: Similar to telephone numbers, fax numbers provide a direct link to an individual or organization. They must be removed to achieve de-identification.
6. Email Addresses: Email addresses are unique identifiers that can be easily used to identify individuals. Removing them is crucial for protecting privacy.
7. Social Security Numbers: Social Security Numbers are highly sensitive and unique identifiers. Their removal is paramount for de-identification.
8. Medical Record Numbers: Medical Record Numbers are unique to each patient within a healthcare system. Removing them prevents linking data back to specific medical records.
9. Health Plan Beneficiary Numbers: These numbers identify individuals within a health plan. Removing them protects privacy related to health insurance coverage.
10. Account Numbers: Account numbers associated with financial institutions or other services can be used to identify individuals. Their removal is necessary for de-identification.
11. Certificate/License Numbers: Certificate or license numbers, such as driver's license numbers, can be used to identify individuals. These must be removed.
12. Vehicle Identifiers and Serial Numbers, Including License Plate Numbers: These identifiers are unique to specific vehicles and can be used to trace back to the owner. Removing them protects privacy related to vehicle ownership.
13. Device Identifiers and Serial Numbers: Similar to vehicle identifiers, device identifiers and serial numbers are unique to specific devices. Their removal is necessary for de-identification.
14. URLs: Uniform Resource Locators (URLs) that link to specific individuals or their profiles must be removed. This prevents accessing identifying information through web links.
15. Internet Protocol (IP) Addresses: IP addresses can be used to identify the location and potentially the individual using a computer or device. Their removal is essential for de-identification.
16. Biometric Identifiers: This includes fingerprints, retina scans, and voiceprints. Biometric identifiers are unique to each individual and must be removed.
17. Full Face Photographic Images and Any Comparable Images: Images that can be used to identify an individual, such as full-face photographs, must be removed or altered. This can involve blurring or masking the face.
18. Any Other Unique Identifying Number, Characteristic, or Code: This is a catch-all category that includes any other data element that could potentially identify an individual. This requires careful consideration and assessment of the specific dataset.
The Expert Determination Method
The HIPAA Expert Determination method allows a qualified expert to assess the risk of re-identification. This expert uses statistical and scientific principles to determine that the risk of re-identification is very low.
This method offers more flexibility than the Safe Harbor method, as it allows for the retention of some potentially identifying information if the expert deems the risk of re-identification to be acceptable. However, it also requires a higher level of expertise and justification.
The Importance of Context
It's important to remember that de-identification is not simply about removing a list of specific data elements. The context in which the data is being used also plays a crucial role. What might be considered de-identified in one setting could potentially be re-identified in another.
For example, a combination of seemingly innocuous data points, such as age, gender, and zip code, could be used to identify an individual if combined with other publicly available information. Therefore, it's crucial to carefully consider the potential for re-identification in each specific case.
Beyond HIPAA: Emerging Considerations
While HIPAA provides a strong foundation for de-identification, new technologies and data sources are constantly emerging. This requires a continuous reassessment of best practices and the development of new techniques for protecting privacy.
For example, the increasing use of artificial intelligence (AI) and machine learning raises new challenges for de-identification. AI algorithms can potentially learn to re-identify individuals from data that was previously considered de-identified.
A Continuing Journey
The quest for effective de-identification is an ongoing journey. It requires a combination of technical expertise, ethical considerations, and a commitment to protecting individual privacy. As technology evolves and new data sources emerge, we must continue to adapt our approaches and strive to find the right balance between data utility and privacy protection.
By understanding the factors that constitute de-identified information and by embracing a responsible approach to data handling, we can unlock the immense potential of data while safeguarding the privacy of individuals.

.jpg)