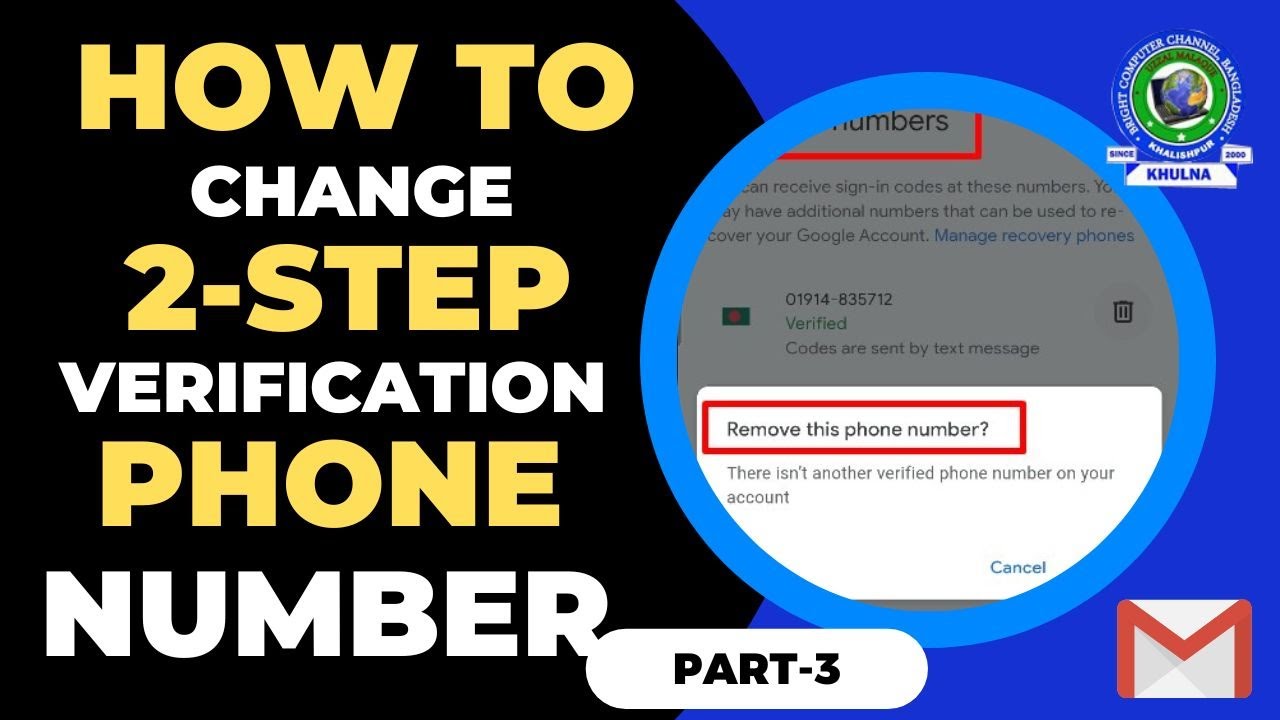
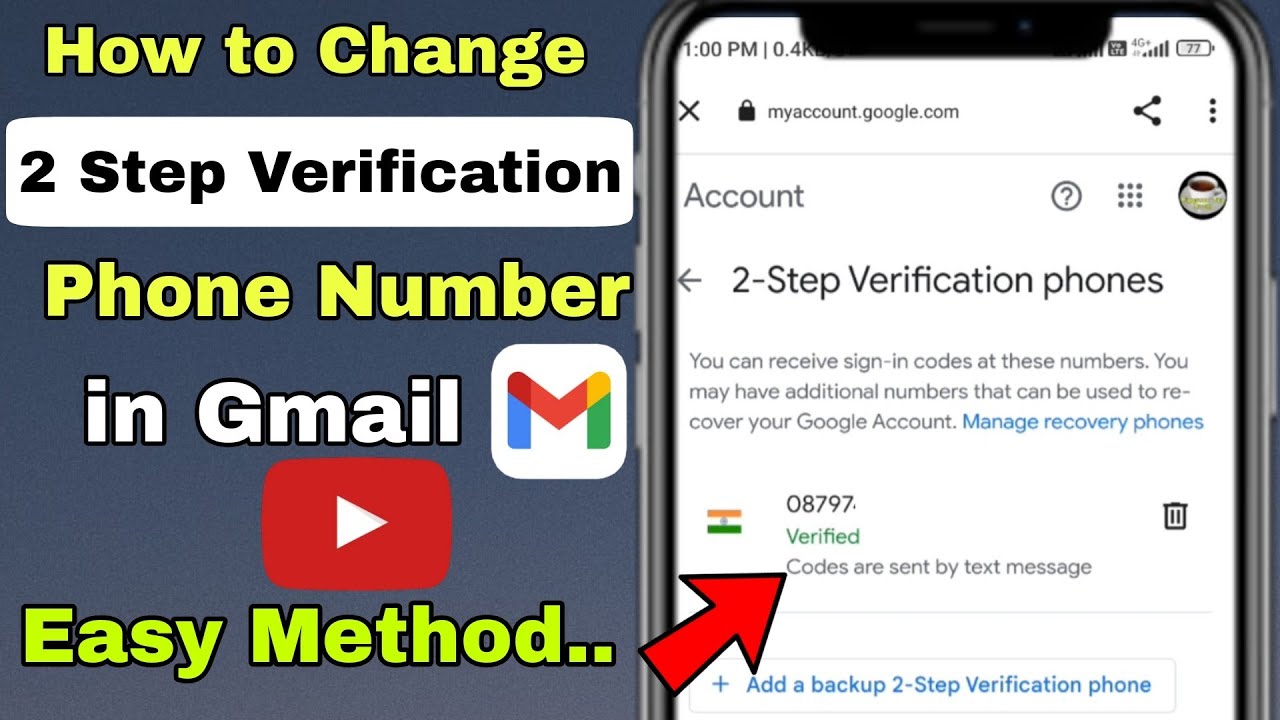
2 Step Verification Phone Number Change
The digital security landscape is constantly shifting, and with it, the methods used to protect our online accounts. One crucial defense, two-step verification (2SV), is now facing a critical vulnerability: the ease with which malicious actors can manipulate the phone number recovery process, effectively hijacking accounts even when 2SV is enabled.
This vulnerability, exploited through social engineering and weaknesses in carrier security protocols, allows attackers to change the phone number associated with an account, circumventing the intended security layer. The implications are far-reaching, potentially impacting millions of users across various platforms, from social media and banking to email and cryptocurrency exchanges.
The Mechanics of the Attack
The attack typically starts with phishing or social engineering. Attackers gather personal information about the target, such as their name, address, date of birth, and even details about their online activities.
Armed with this information, they contact the target's mobile carrier, impersonating the account holder. By leveraging the gathered personal data, they convince the carrier to port the target's phone number to a SIM card under their control.
Once the number is ported, the attacker initiates the password reset process on the target's online accounts. Since the 2SV code is now sent to the attacker's SIM card, they can easily bypass the security measure and gain unauthorized access.
Vulnerabilities in Carrier Security
A significant contributing factor to this vulnerability is the insufficient security measures employed by some mobile carriers. Many rely on easily obtainable personal information for verification, making it relatively easy for attackers to impersonate account holders.
This issue isn't new. Security experts have long warned about the risks associated with relying solely on phone numbers for authentication, highlighting the need for stronger verification methods.
As Bruce Schneier, a renowned security technologist, has stated, "Relying on phone numbers for authentication is inherently insecure because phone numbers are easily spoofed and transferred."
Real-World Impact and Examples
The consequences of a successful 2SV bypass can be devastating. Victims have reported losing access to their email accounts, social media profiles, banking information, and even cryptocurrency wallets.
In some cases, attackers have used the compromised accounts to spread misinformation, commit fraud, or extort money from the victim's contacts. A recent report by the Federal Trade Commission (FTC) highlights a surge in SIM swapping attacks, resulting in significant financial losses for consumers.
For example, a highly publicized case involved a tech executive who lost over $1 million in cryptocurrency after his phone number was ported and his 2SV was bypassed.
Mitigation Strategies for Users
While the risk is real, users can take steps to mitigate the threat. Enabling stronger authentication methods is crucial.
Consider using a hardware security key like a YubiKey or Google Titan Security Key. These devices provide a much higher level of security compared to SMS-based 2SV.
Furthermore, enable 2FA apps such as Google Authenticator or Authy. Regularly review your account security settings and be wary of suspicious emails or phone calls requesting personal information.
Industry Response and Future Directions
The industry is slowly responding to the growing threat. Some platforms are phasing out SMS-based 2SV altogether, encouraging users to adopt more secure authentication methods.
Mobile carriers are also under pressure to improve their security protocols and implement stricter verification procedures. The National Institute of Standards and Technology (NIST) has issued guidelines recommending against relying solely on SMS for authentication.
Looking ahead, the future of online security may involve biometric authentication, decentralized identity solutions, and other advanced technologies that are less vulnerable to social engineering and SIM swapping attacks.
Conclusion
The vulnerability surrounding 2SV phone number changes is a serious issue that demands immediate attention. While 2SV still offers a significant layer of protection compared to passwords alone, it's crucial to be aware of its limitations and take proactive steps to enhance account security.
By adopting stronger authentication methods, staying informed about emerging threats, and advocating for improved security protocols, we can collectively work towards a more secure online environment.