Akamai Zero Trust Network Access Evaluation
Imagine a bustling city, its digital arteries humming with data, each packet a tiny vehicle carrying vital information. But lurking in the shadows are cyber threats, patiently waiting for an opportunity to exploit vulnerabilities and cause chaos. Now picture a sophisticated security system, a digital gatekeeper, meticulously verifying the identity of every vehicle before granting access, ensuring only authorized traffic flows smoothly. This is the promise of Zero Trust Network Access (ZTNA), and Akamai, a major player in the cybersecurity landscape, is being put to the test.
At its core, this article delves into the recent evaluations of Akamai's Zero Trust Network Access solution. We'll explore the findings and their implications for businesses seeking to enhance their security posture in an increasingly complex digital world.
The Rise of Zero Trust
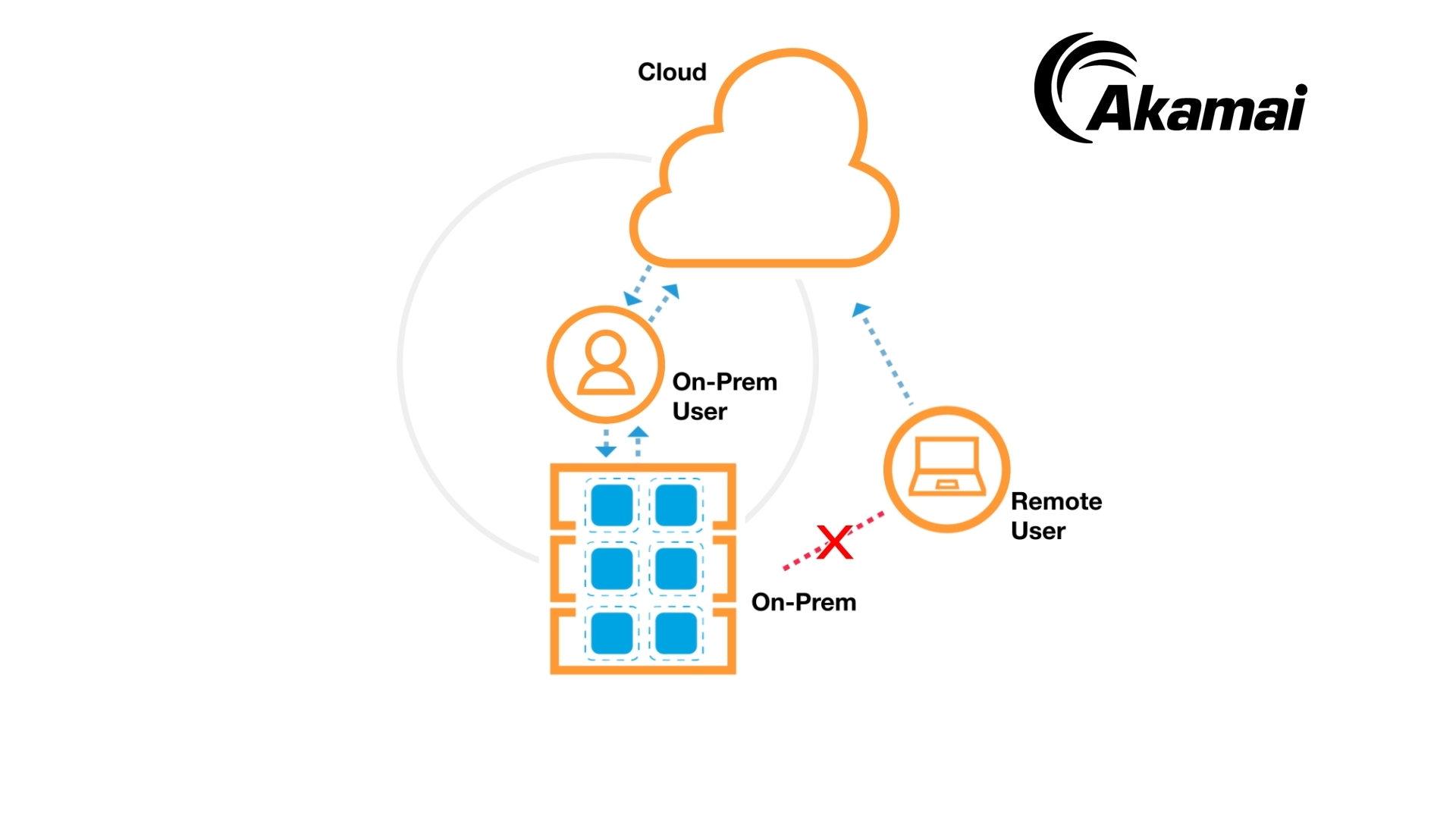
The traditional security model, often likened to a castle and moat, focuses on protecting the perimeter of a network. However, in today's world of remote work, cloud computing, and mobile devices, the perimeter has become increasingly blurred, rendering this approach inadequate.
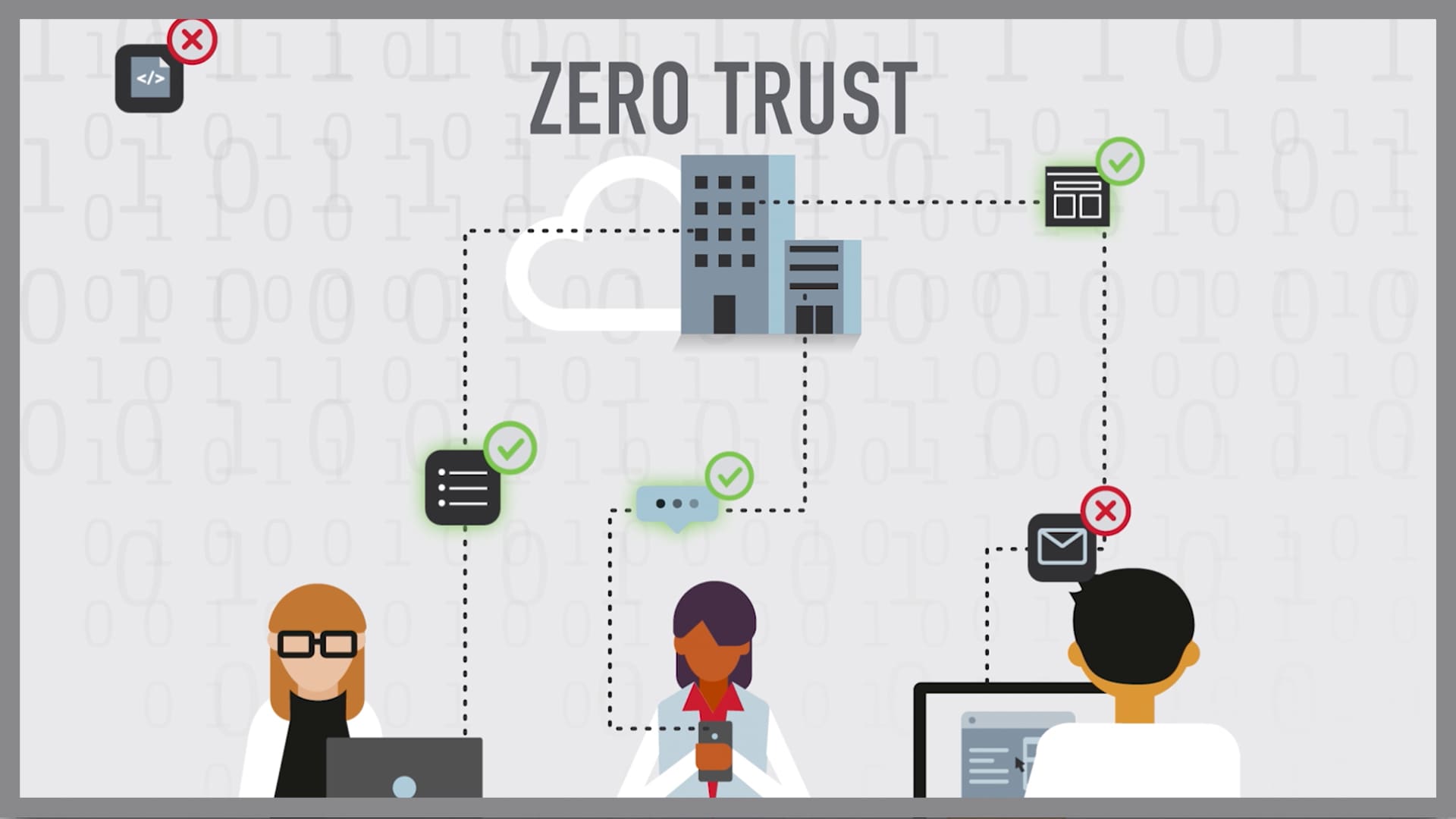
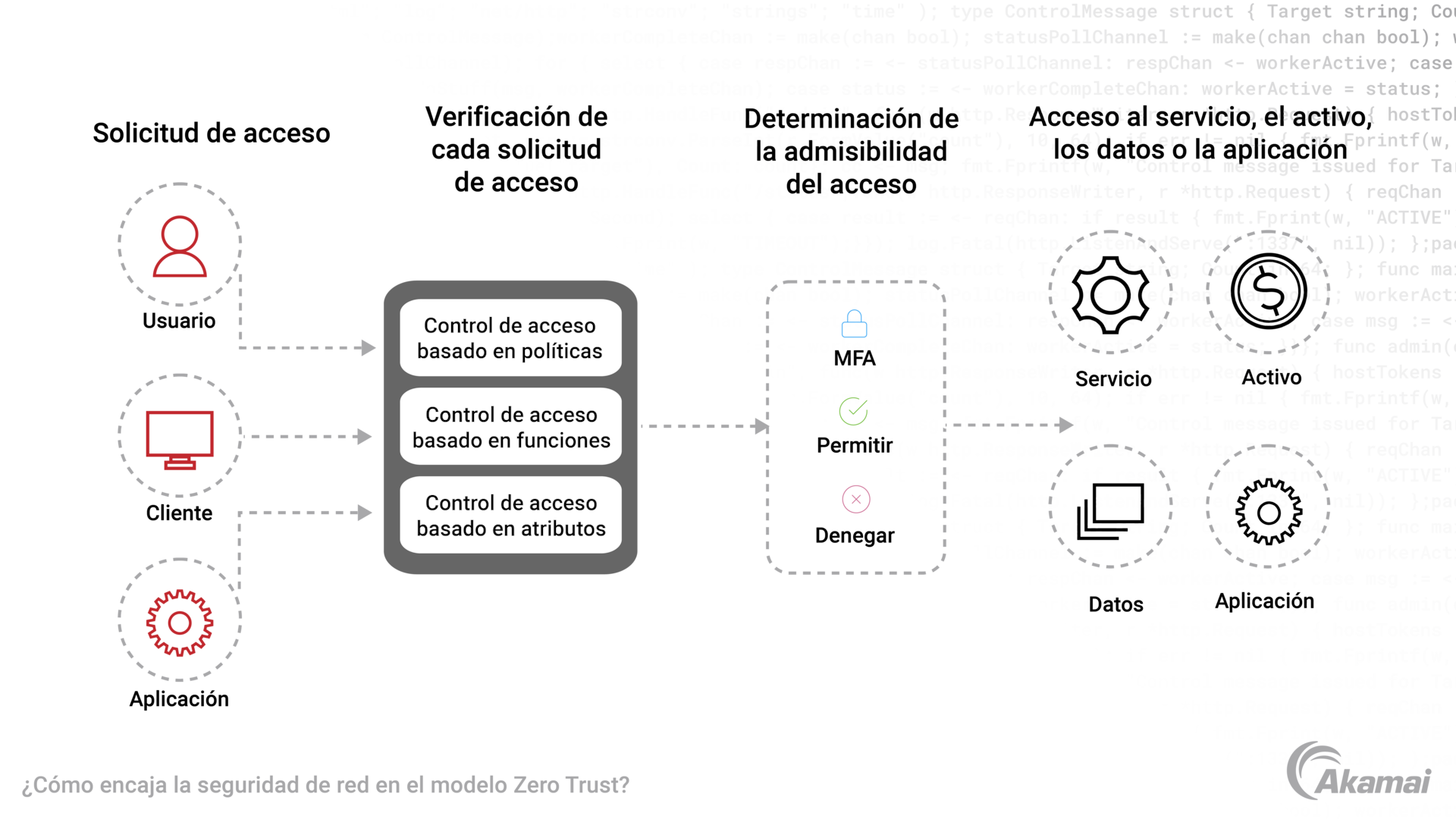
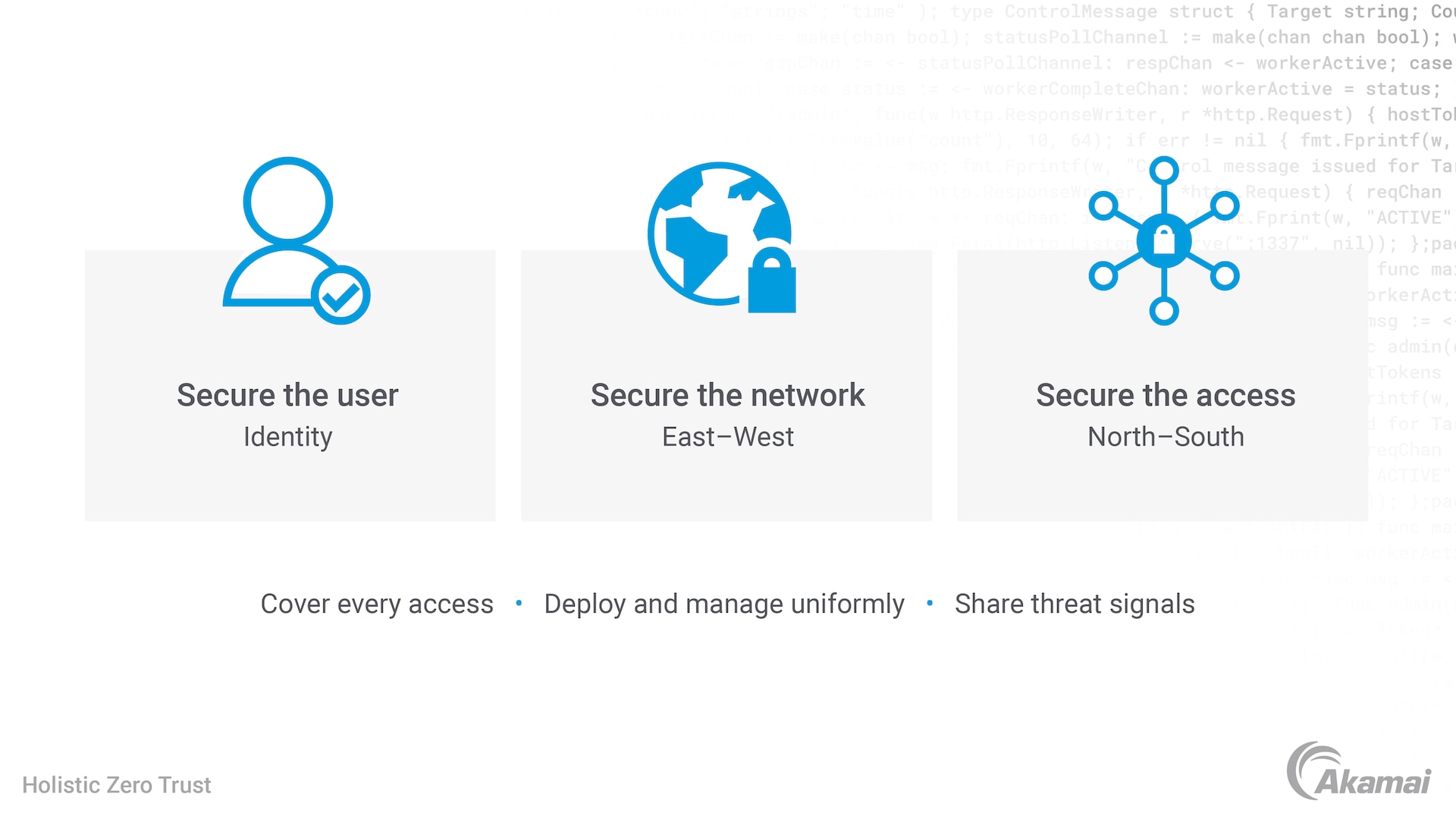
Zero Trust, on the other hand, operates on the principle of "never trust, always verify." Every user and device, regardless of location, must be authenticated and authorized before gaining access to network resources. This approach significantly reduces the risk of lateral movement by attackers who have already breached the perimeter.
Key Principles of Zero Trust
Several core principles underpin the Zero Trust philosophy.
Firstly, explicit verification is paramount. Every access request is subject to rigorous authentication and authorization, ensuring the user is who they claim to be and has the necessary permissions.
Secondly, least privilege access dictates that users are granted only the minimum level of access required to perform their job functions. This limits the potential damage if an account is compromised.
Finally, continuous monitoring and validation are crucial. User activity is constantly monitored for suspicious behavior, and access rights are dynamically adjusted based on changing risk profiles.
Akamai's ZTNA Solution
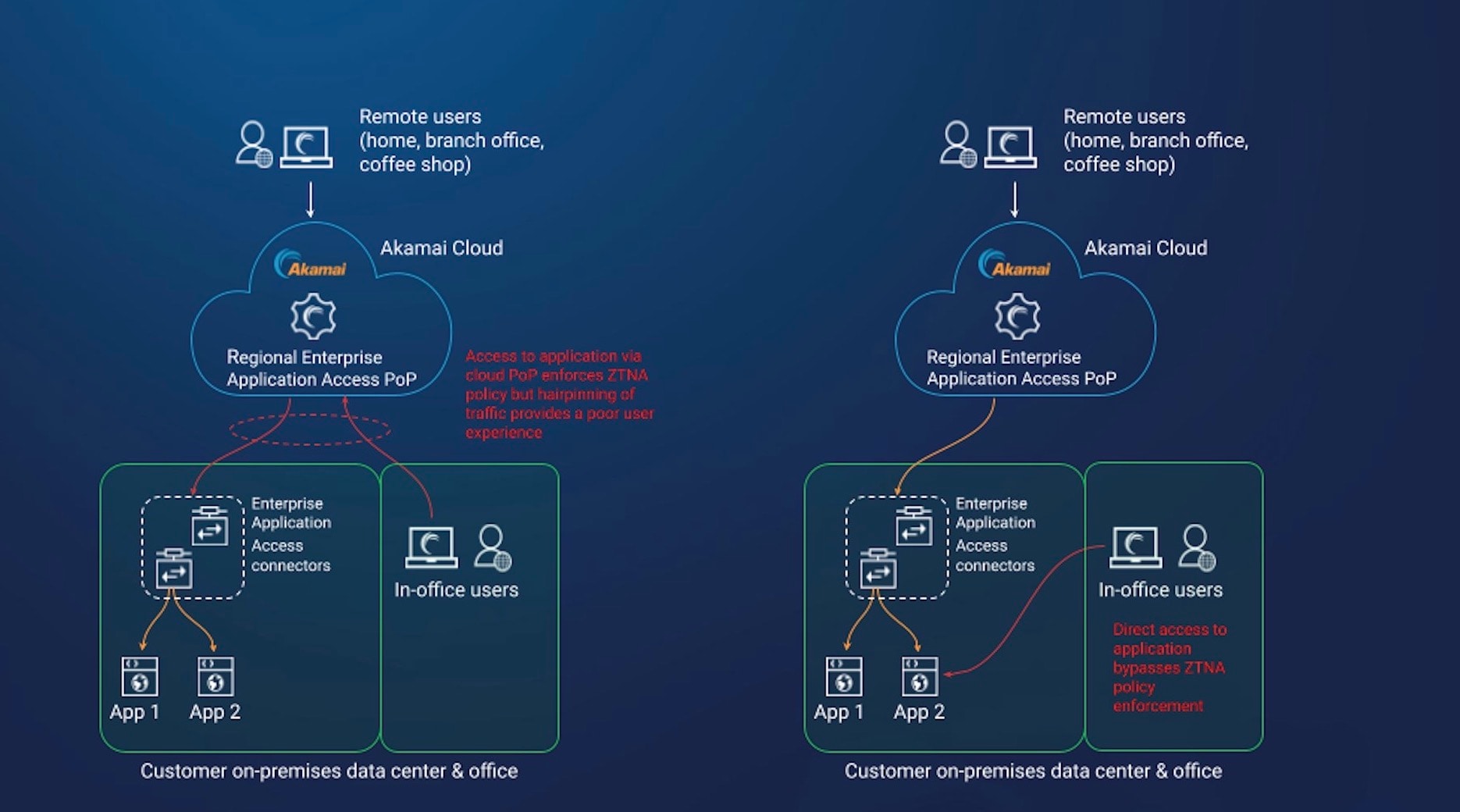
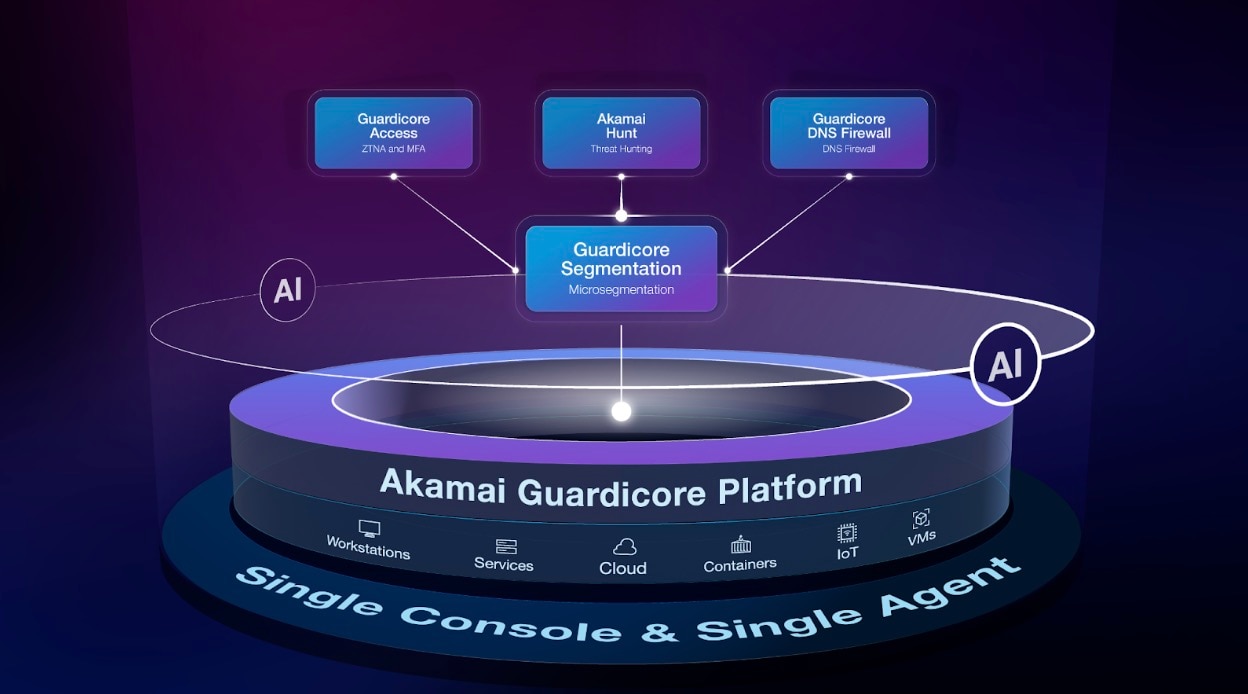
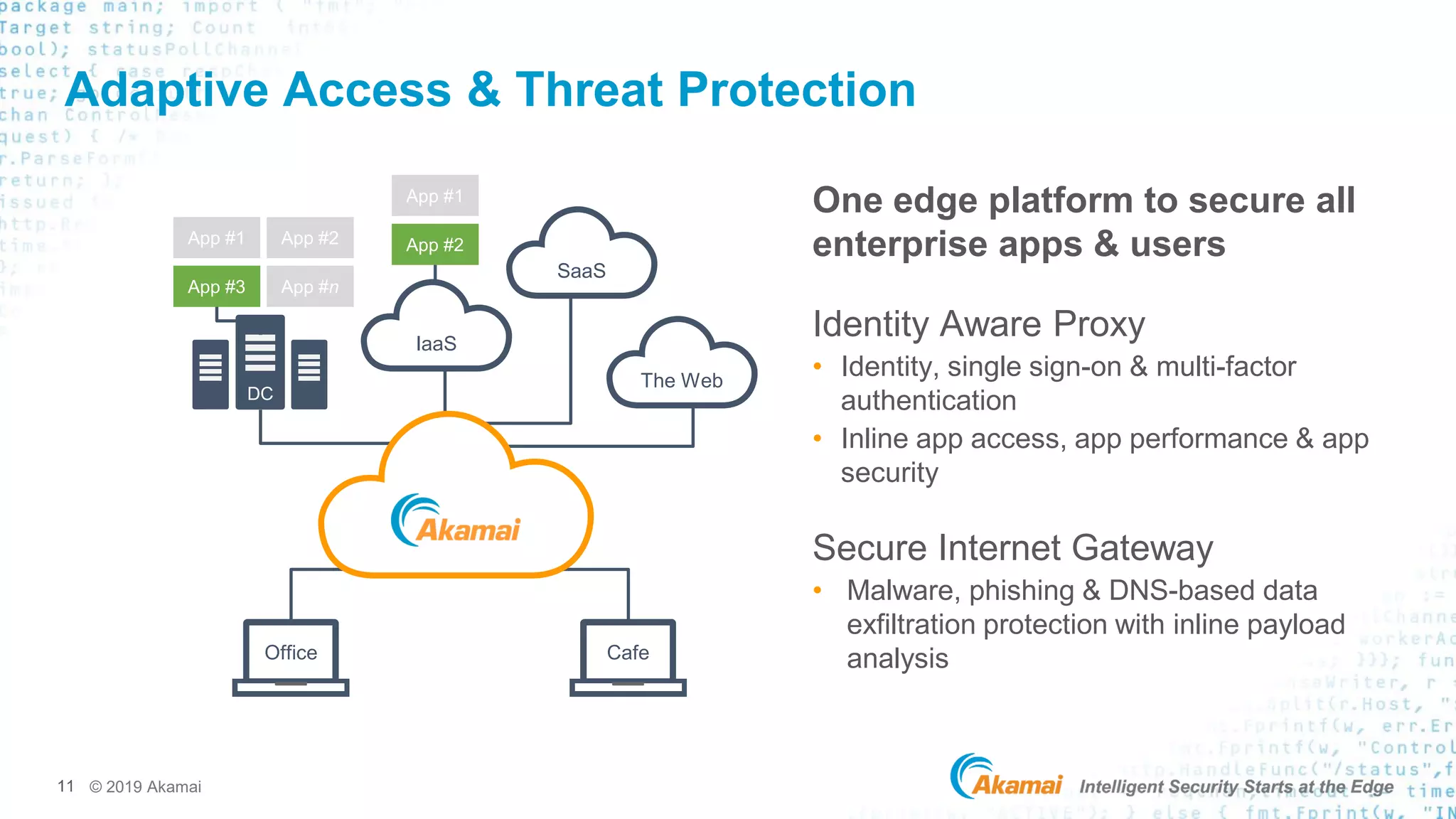
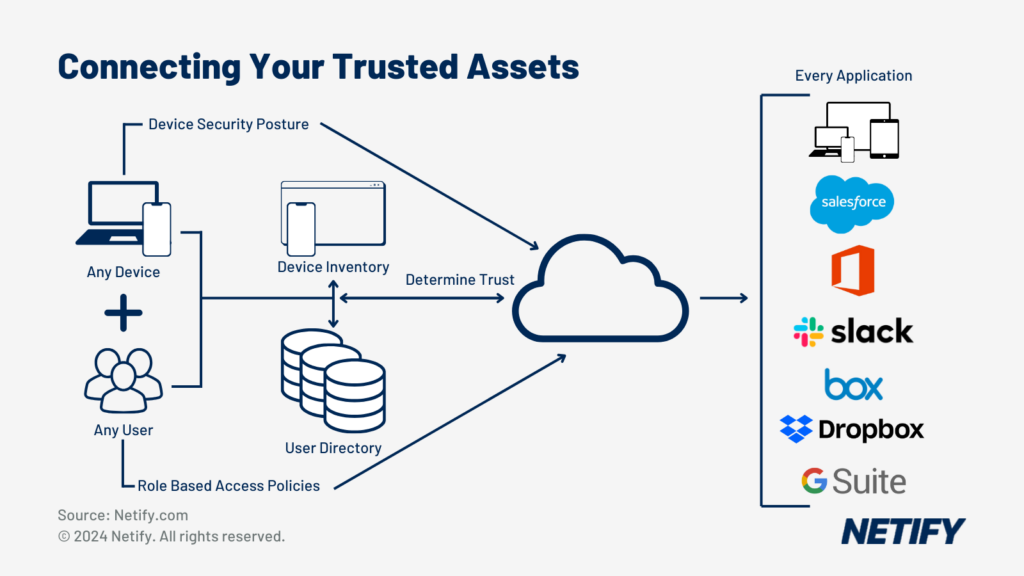
Akamai offers a comprehensive Zero Trust Network Access solution designed to help organizations implement these principles. Their solution provides secure access to applications and resources, regardless of where they are hosted or where the user is located.
It leverages Akamai's global network and intelligent security platform to deliver a seamless and secure user experience. This helps reduce the complexity and cost associated with traditional VPNs.
Akamai's approach also incorporates adaptive access controls, which dynamically adjust access policies based on user behavior, device posture, and other contextual factors.
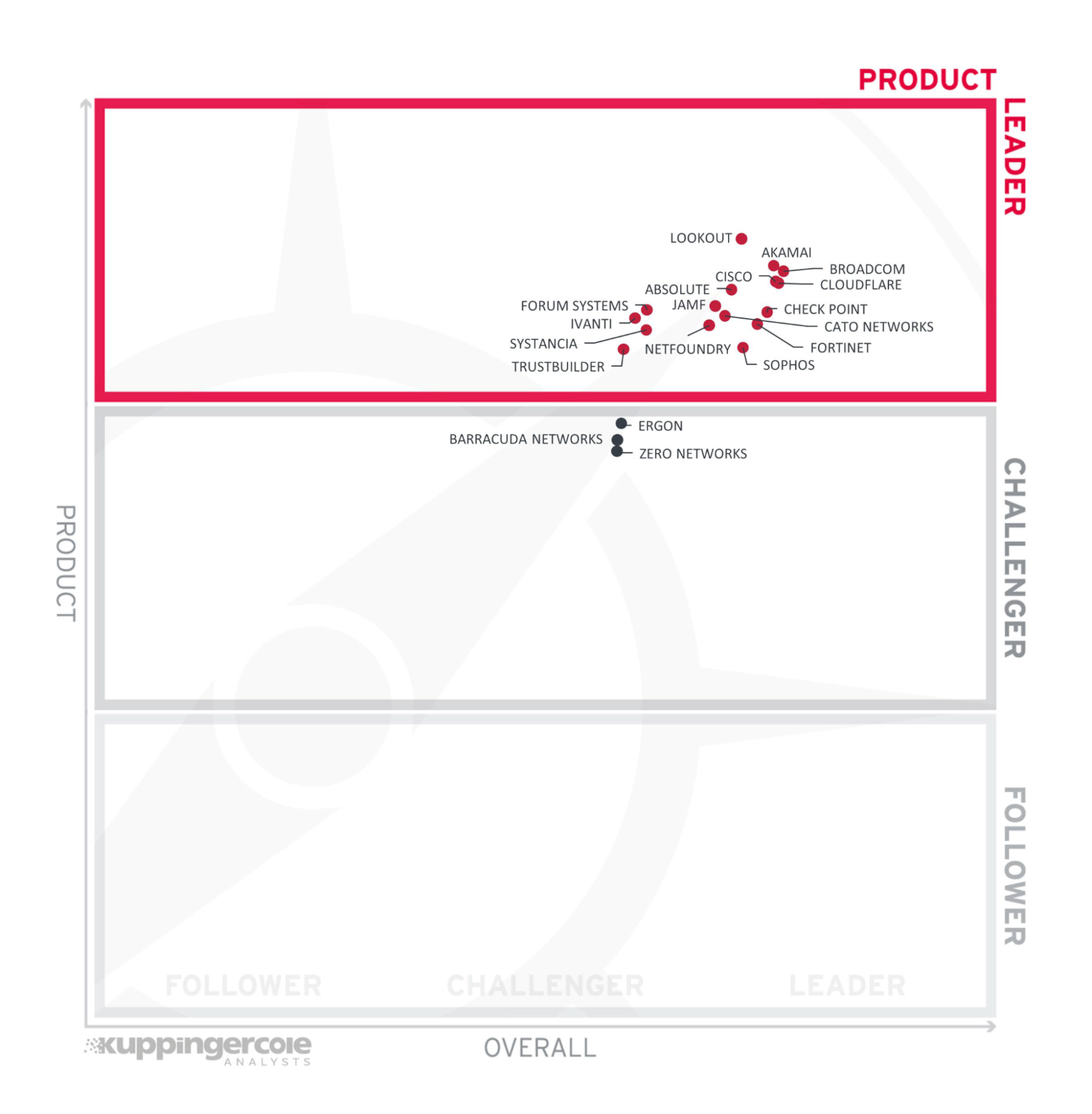
Independent Evaluations and Industry Recognition
Several independent evaluations have assessed Akamai's ZTNA solution, highlighting its strengths and areas for improvement.
Industry analysts at firms like Gartner and Forrester have consistently recognized Akamai as a leader in the ZTNA market. These recognitions are based on a thorough assessment of Akamai's product capabilities, market presence, and customer satisfaction.
Many reviews praise Akamai's scalability, robust security features, and seamless integration with other security tools. Some evaluations also point to the complexity of initial setup and configuration as an area for potential improvement.
"Akamai has demonstrated a commitment to innovation in the Zero Trust space, continuously enhancing its platform to meet the evolving needs of its customers," said a leading industry analyst.
Customer Feedback and Real-World Applications
Ultimately, the true measure of any security solution lies in its ability to protect organizations in the real world.
Numerous case studies demonstrate how Akamai's ZTNA solution has helped organizations reduce their risk exposure, improve their security posture, and simplify their IT operations. Organizations across various industries, including finance, healthcare, and retail, are adopting Akamai's ZTNA to secure their remote workforce and protect their critical assets.
For instance, a global financial institution implemented Akamai's ZTNA to secure access to its sensitive data and applications, enabling its employees to work securely from anywhere in the world. A healthcare provider used Akamai's solution to protect patient data and ensure compliance with industry regulations.
Benefits and Challenges
Implementing Zero Trust Network Access offers numerous benefits, including improved security, reduced risk, and enhanced user experience. However, it also presents certain challenges.
One of the biggest challenges is the complexity of implementation. ZTNA requires a fundamental shift in mindset and a thorough understanding of an organization's network infrastructure and security requirements.
Another challenge is the need for ongoing monitoring and maintenance. Organizations must continuously monitor user activity, update access policies, and adapt to evolving threats. Despite these challenges, the benefits of ZTNA far outweigh the risks for most organizations.
The Future of Zero Trust and Akamai's Role
As cyber threats continue to evolve and become more sophisticated, the importance of Zero Trust will only increase.
Akamai is well-positioned to play a leading role in the future of Zero Trust. Their global network, intelligent security platform, and commitment to innovation make them a valuable partner for organizations seeking to implement a Zero Trust architecture.
Looking ahead, Akamai is likely to focus on further simplifying the implementation and management of ZTNA, as well as enhancing its capabilities to address emerging threats.
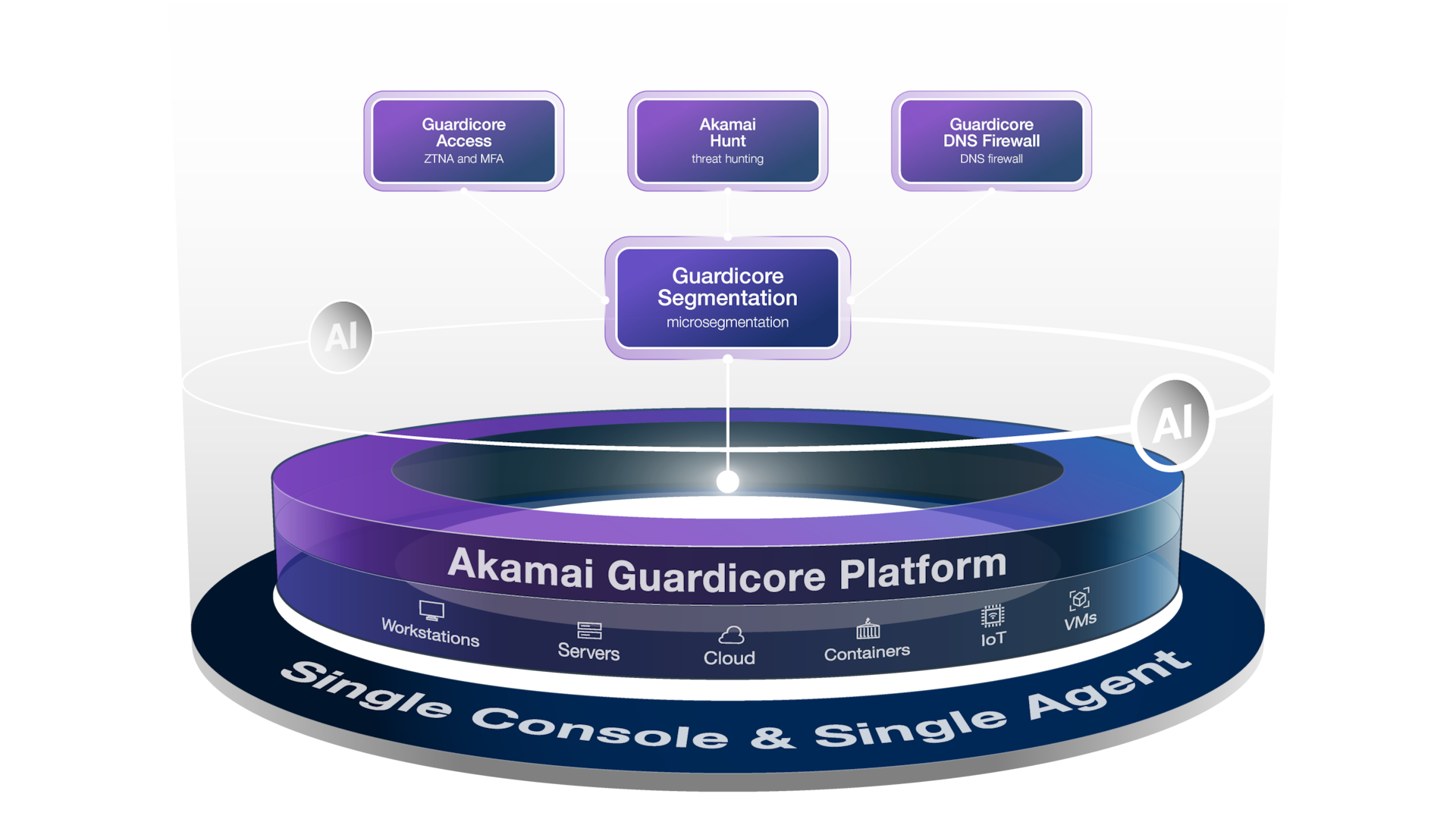
The development of AI-powered threat detection and response will be key to providing more autonomous and intelligent security solutions. The company is also poised to integrate ZTNA with other security technologies, such as endpoint detection and response (EDR) and security information and event management (SIEM), to provide a more comprehensive security posture.
This holistic approach will give businesses greater visibility and control over their security landscape, streamlining incident response and reducing the dwell time of attackers.
Conclusion
The journey towards Zero Trust is not a destination but a continuous process. Akamai's Zero Trust Network Access solution represents a significant step forward in helping organizations achieve a more secure and resilient digital environment. While challenges remain, the potential benefits are undeniable.
By embracing the principles of Zero Trust and leveraging solutions like Akamai's, organizations can better protect themselves from the ever-growing threat landscape and confidently navigate the digital future.
Ultimately, the effectiveness of any security solution depends on a combination of technology, people, and processes. Organizations must invest in training and education to ensure that their security teams have the skills and knowledge necessary to implement and manage ZTNA effectively. They need to also foster a culture of security awareness throughout the organization, emphasizing the importance of following security best practices.