Install Spy App On Iphone Without Jailbreak

The claim of installing spy apps on iPhones without jailbreaking has become a growing concern, sparking debate among cybersecurity experts and privacy advocates alike. The allure of monitoring digital activity without altering the device's core software presents both a tempting solution for some and a grave threat to individual privacy for others.
At the heart of this controversy lies the question of feasibility and the ethical implications. Is it truly possible to bypass Apple's stringent security measures without jailbreaking? What are the potential risks associated with such methods? And what measures can individuals take to protect their privacy in an increasingly surveilled digital landscape?
The Allure and Reality of "No-Jailbreak" Spy Apps
The market for monitoring software is substantial, driven by parental control needs, employer surveillance, and even suspicion within personal relationships. Companies promoting "no-jailbreak" spy apps often advertise ease of use and discreet operation, promising access to call logs, text messages, social media activity, location data, and more, all without the target user's knowledge.
However, the reality is often more complex and less reliable. While some software may claim to offer limited functionality without jailbreaking, these methods typically rely on obtaining iCloud credentials and accessing data through official Apple services. This approach is inherently limited and vulnerable to changes in Apple's security protocols.
According to cybersecurity firm SentinelOne, many "no-jailbreak" solutions are either outright scams or rely on exploiting vulnerabilities that are quickly patched by Apple. They emphasize that claims of complete access to an iPhone's data without jailbreaking should be treated with extreme skepticism.
Technical Considerations and Limitations
Apple's iOS operating system is designed with robust security features aimed at protecting user data. Jailbreaking, the process of removing these restrictions, traditionally opened the door for installing unauthorized software, including spy apps.
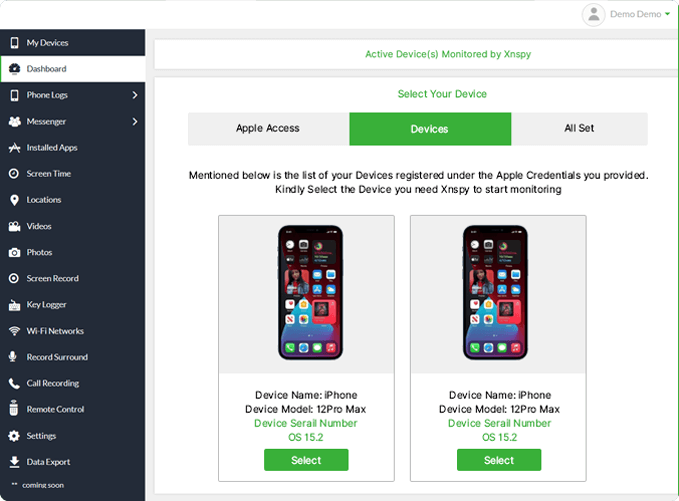
The purported "no-jailbreak" methods circumvent this process by leveraging existing Apple services or exploiting temporary loopholes. One common technique involves gaining access to a user's iCloud account. This requires either obtaining their Apple ID and password directly or employing phishing tactics.
Once access is gained, the software can potentially extract data synced to iCloud, such as contacts, calendars, photos, and backups. However, this approach is heavily dependent on the user's iCloud settings and the data they choose to store in the cloud. Furthermore, Apple regularly updates its security measures, rendering previous exploits ineffective. Apple has consistently stated its commitment to protecting user privacy and security.
Ethical and Legal Ramifications
Beyond the technical challenges, the use of spy apps, even those claiming to operate without jailbreaking, raises significant ethical and legal concerns. In many jurisdictions, secretly monitoring someone's phone activity is illegal and can result in serious penalties.
The legality of such actions often depends on factors such as the relationship between the parties involved and the intended use of the data. For instance, monitoring a child's phone may be permissible under certain circumstances, while spying on a spouse or employee without their consent is generally illegal. The Electronic Frontier Foundation (EFF) advocates for strong privacy protections and warns against the dangers of surreptitious surveillance.
Ethically, the use of spy apps can erode trust and damage relationships. Even if legal, such actions can be seen as a violation of privacy and personal autonomy. Privacy advocates argue that individuals have a right to control their own data and communications.
Protecting Your iPhone from Unauthorized Access
There are several steps individuals can take to protect their iPhones from unauthorized access and potential spying. Firstly, enabling two-factor authentication (2FA) for your Apple ID is crucial. This adds an extra layer of security, making it significantly harder for someone to access your account even if they have your password.
Secondly, be cautious about clicking on suspicious links or downloading apps from untrusted sources. Phishing scams are a common tactic used to steal iCloud credentials. Always verify the authenticity of emails and websites before entering your login information.
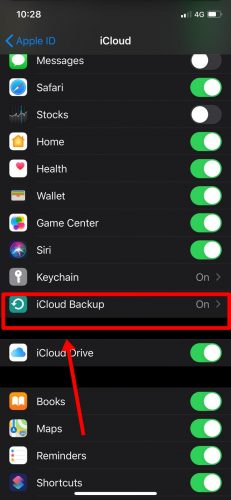
Regularly review your iCloud settings and disable syncing for data you don't want stored in the cloud. Additionally, monitor your iPhone for signs of unusual activity, such as unexpected battery drain or unfamiliar apps. Keeping your iOS software up to date ensures you have the latest security patches installed.
Looking Ahead: The Evolving Landscape of Mobile Security
The battle between security and surveillance is an ongoing one. As Apple continues to strengthen its security measures, developers of spy apps will likely seek new and innovative ways to circumvent them. The future of mobile security will depend on a combination of technological advancements, legal frameworks, and individual awareness.
Moving forward, it is essential for consumers to be informed about the risks associated with spy apps and to take proactive steps to protect their privacy. Lawmakers and regulators must also address the ethical and legal implications of these technologies, ensuring that individual rights are protected in an increasingly connected world. The Federal Trade Commission (FTC) has taken action against companies marketing deceptive surveillance products, highlighting the importance of regulatory oversight.
Ultimately, safeguarding your digital privacy requires a multi-faceted approach that combines vigilance, technological awareness, and a commitment to responsible online behavior.