Which Of The Following Is Not A Form Of Obfuscation

The question, "Which of the following is not a form of obfuscation?" has become a surprisingly common query online, sparking discussions across various fields, from cybersecurity to legal interpretation.
The interest stems from the growing awareness of obfuscation techniques used to conceal information, often with malicious intent. Understanding what doesn't constitute obfuscation is equally important in identifying and mitigating these practices.
Obfuscation, at its core, is the deliberate act of making something difficult to understand. This article explores the nuances of obfuscation and clarifies what actions fall outside its definition.
Defining Obfuscation and Its Domains
Obfuscation techniques are employed in numerous domains. They are found in software development to protect code from reverse engineering. They are also present in legal contexts to obscure the true meaning of a contract, and even in everyday communication to avoid direct answers.
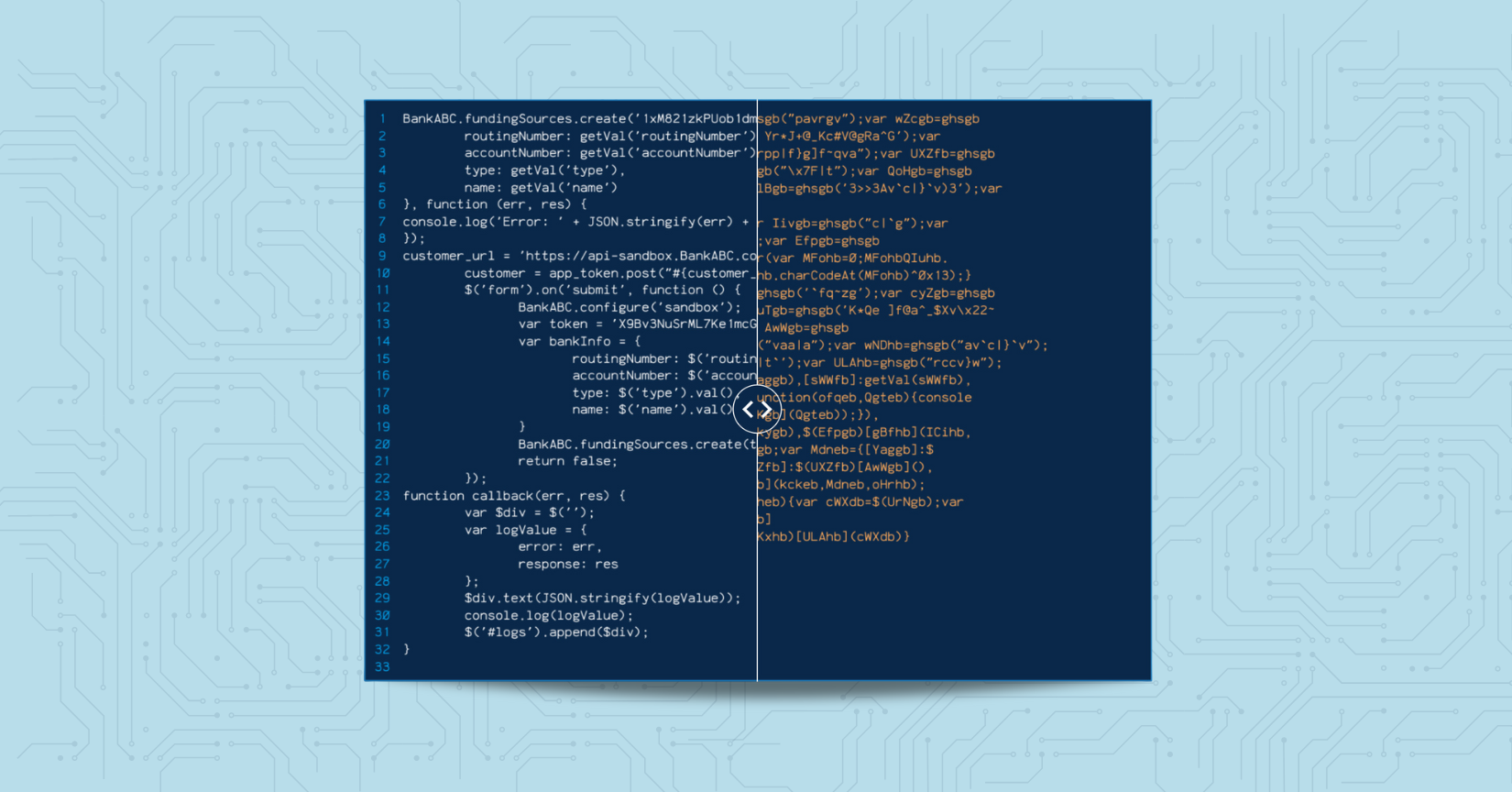
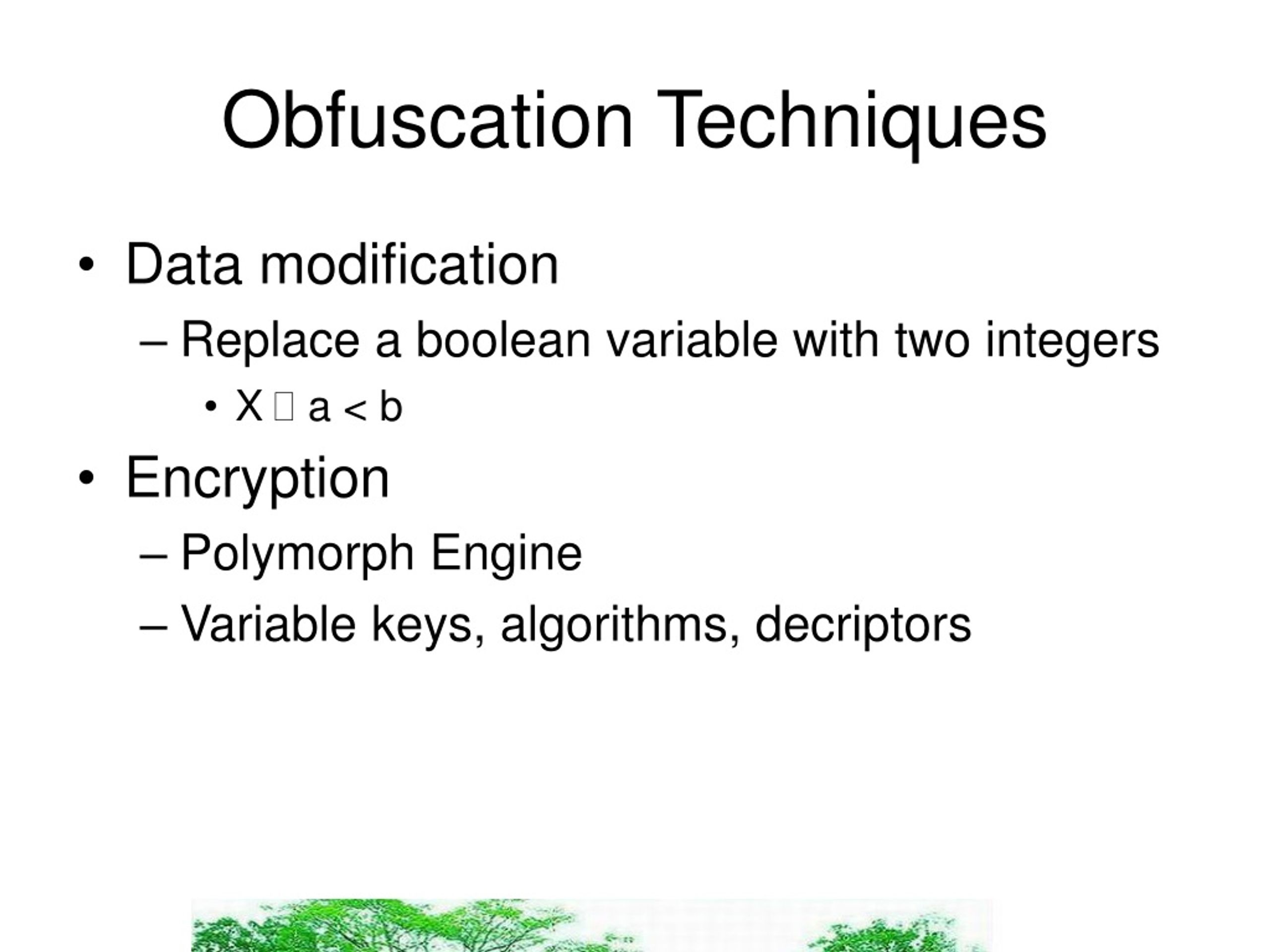
In cybersecurity, obfuscation is a key element in malware development. Cybercriminals use it to hide malicious code from antivirus software. It makes analysis and detection more challenging.
The aim is to make the code's purpose unintelligible without actually changing its functionality. This relies on creating a complex and confusing representation of something that is otherwise straightforward.
Common Methods of Obfuscation
Examples of obfuscation techniques include:
- Code transformation: Rewriting code to make it harder to understand without changing its functionality.
- Lexical obfuscation: Renaming variables and functions to nonsensical names.
- Control flow obfuscation: Altering the order of code execution to complicate analysis.
- Data obfuscation: Encoding or encrypting data to hide its meaning.
What Isn't Obfuscation?
While various actions may complicate understanding, not every action qualifies as obfuscation. Actions that are merely complex or technical without deliberate intent to deceive are not obfuscation.
Similarly, encryption, while hiding information, isn't always obfuscation. Encryption is typically used to protect confidentiality. Obfuscation, on the other hand, specifically aims to make understanding harder.
Transparency, the practice of making information readily available and understandable, is fundamentally the opposite of obfuscation. Open communication and clear documentation are specifically designed to avoid confusion.
Examples of Non-Obfuscatory Practices
Consider these scenarios:
1. Using standard technical jargon in a technical document might make it difficult for a layperson to understand. However, this is not obfuscation if the jargon is used appropriately and consistently within the field.
2. Complicated algorithms in software development are not necessarily obfuscation. They could be the best or most efficient way to perform a certain task. They are obfuscation only if the code is intentionally made convoluted to hide its function.
3. A complex legal document using specific legal terminology is not necessarily obfuscation. If the document follows standard legal practices and is written to be interpreted within the legal framework, it does not meet the criteria.
The key distinction is the intent to deceive or hide the underlying meaning. If there is no such intent, it is not obfuscation.
The Significance of Distinguishing Obfuscation
The ability to differentiate obfuscation from legitimate complexity is critical for various reasons.
In cybersecurity, correctly identifying obfuscated code allows for quicker and more effective threat detection. It also enables the development of better defenses against malicious software.
In legal contexts, recognizing obfuscation can prevent unfair contractual agreements. It protects individuals from being misled by intentionally confusing language.
"Understanding the difference between complexity and obfuscation is crucial for maintaining transparency and accountability across various sectors," stated a recent report by the Cybersecurity and Infrastructure Security Agency (CISA).
Conclusion
Obfuscation is the deliberate act of making something difficult to understand, typically with the intent to deceive or conceal. Complexity, encryption (without malicious intent), and transparency are not forms of obfuscation.
The ability to distinguish obfuscation from other forms of complexity is becoming increasingly important in various fields. This includes cybersecurity, law, and even everyday communication.
By understanding what isn't obfuscation, individuals and organizations can better identify and address situations where intentional deception may be at play. This fosters greater transparency and accountability across society.