Which Of The Following Is True About Insider Threats
Imagine a bustling office, the hum of keyboards a constant backdrop to whispered conversations and ringing phones. Data flows freely, powering innovation and driving growth. But lurking beneath the surface, unseen and often unexpected, is a potential threat – not from external hackers in faraway lands, but from within the very walls of the organization itself.
The question of which statement accurately describes insider threats is complex, and the answer is rarely simple. In essence, an insider threat is a risk posed by someone who has legitimate access to an organization's assets – employees, contractors, or even trusted business partners – who then misuse that access, intentionally or unintentionally, to harm the organization.
To understand the true nature of insider threats, we need to delve deeper into their motivations, manifestations, and the strategies used to mitigate them.
Understanding Insider Threats
The term "insider threat" might conjure images of disgruntled employees plotting elaborate schemes, but the reality is often far more nuanced. Intentional maliciousness is certainly a factor, but unintentional actions and negligence play a significant role as well.
According to a 2023 report by the Ponemon Institute, unintentional data breaches caused by employee mistakes are still a very significant part of all security incidents.
This highlights the need for comprehensive training and awareness programs that address not only the technical aspects of security but also the human element. A simple error, like clicking on a phishing link or mishandling sensitive data, can have devastating consequences.
The Spectrum of Insider Threats
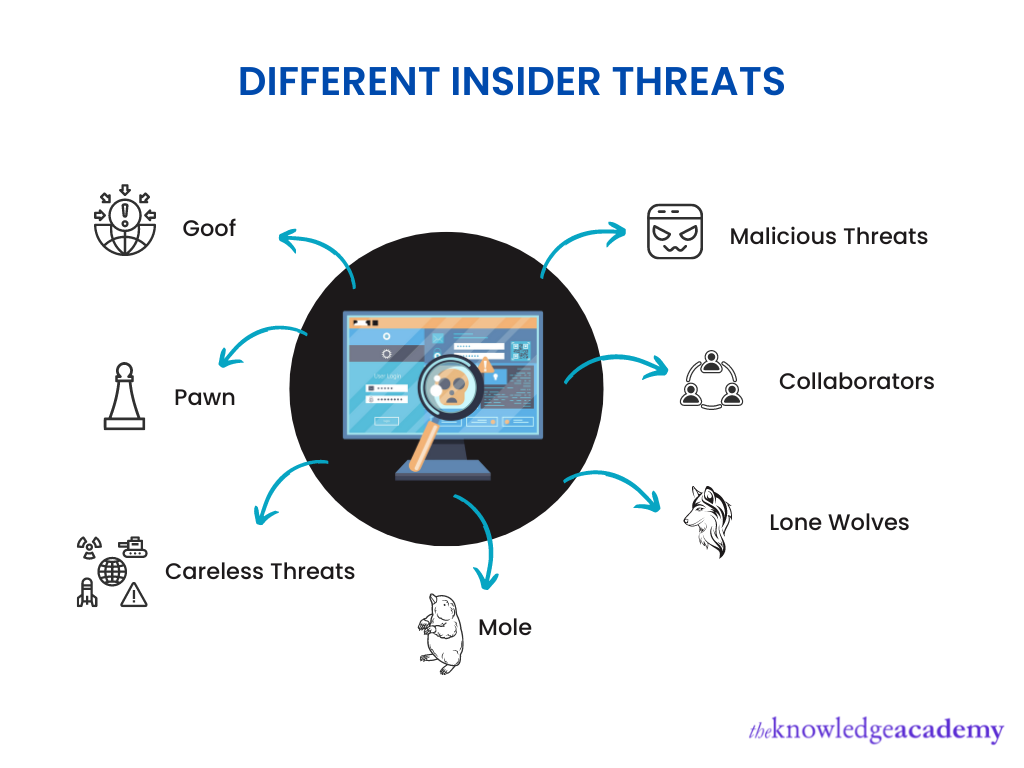
Insider threats are not a monolithic entity; they exist on a spectrum ranging from negligence to outright malice. Let's examine some key categories:
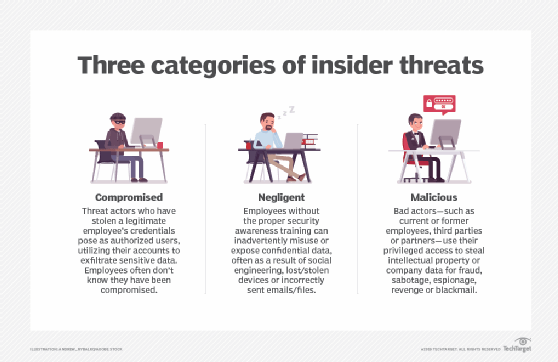
Negligent Insiders: These individuals are often unaware of security policies or best practices and make mistakes that compromise data. Examples include using weak passwords, failing to secure devices, or falling victim to social engineering attacks.
Accidental Insiders: Similar to negligent insiders, these individuals cause harm unintentionally, but often due to system errors or a lack of adequate controls, rather than personal negligence.
Malicious Insiders: These are the individuals who intentionally seek to harm the organization, whether for personal gain, revenge, or ideological reasons. They may steal confidential data, sabotage systems, or leak sensitive information to competitors.
Compromised Insiders: This category includes insiders whose accounts have been hijacked by external actors. The insider may be unaware that their credentials are being used for malicious purposes.
Why Insider Threats Matter
The impact of insider threats can be far-reaching, affecting an organization's financial stability, reputation, and competitive advantage. Data breaches resulting from insider activity can lead to significant financial losses, including regulatory fines, legal fees, and remediation costs.
Beyond the financial implications, insider threats can severely damage an organization's reputation and erode customer trust. A data breach that exposes sensitive customer information can lead to a loss of confidence and a decline in sales.
Moreover, insider threats can compromise intellectual property and trade secrets, giving competitors an unfair advantage. This can stifle innovation and lead to a decline in market share.
Mitigating Insider Threats: A Multi-Layered Approach
Combating insider threats requires a multi-layered approach that encompasses technology, policies, and human factors. No single solution is foolproof, but a combination of proactive measures can significantly reduce the risk.
Data Loss Prevention (DLP) Tools: DLP tools can monitor and control the movement of sensitive data within and outside the organization, preventing unauthorized access and exfiltration.
User and Entity Behavior Analytics (UEBA): UEBA solutions use machine learning to detect anomalous user behavior that may indicate malicious activity. By identifying deviations from normal patterns, UEBA can help security teams identify and respond to insider threats more quickly.
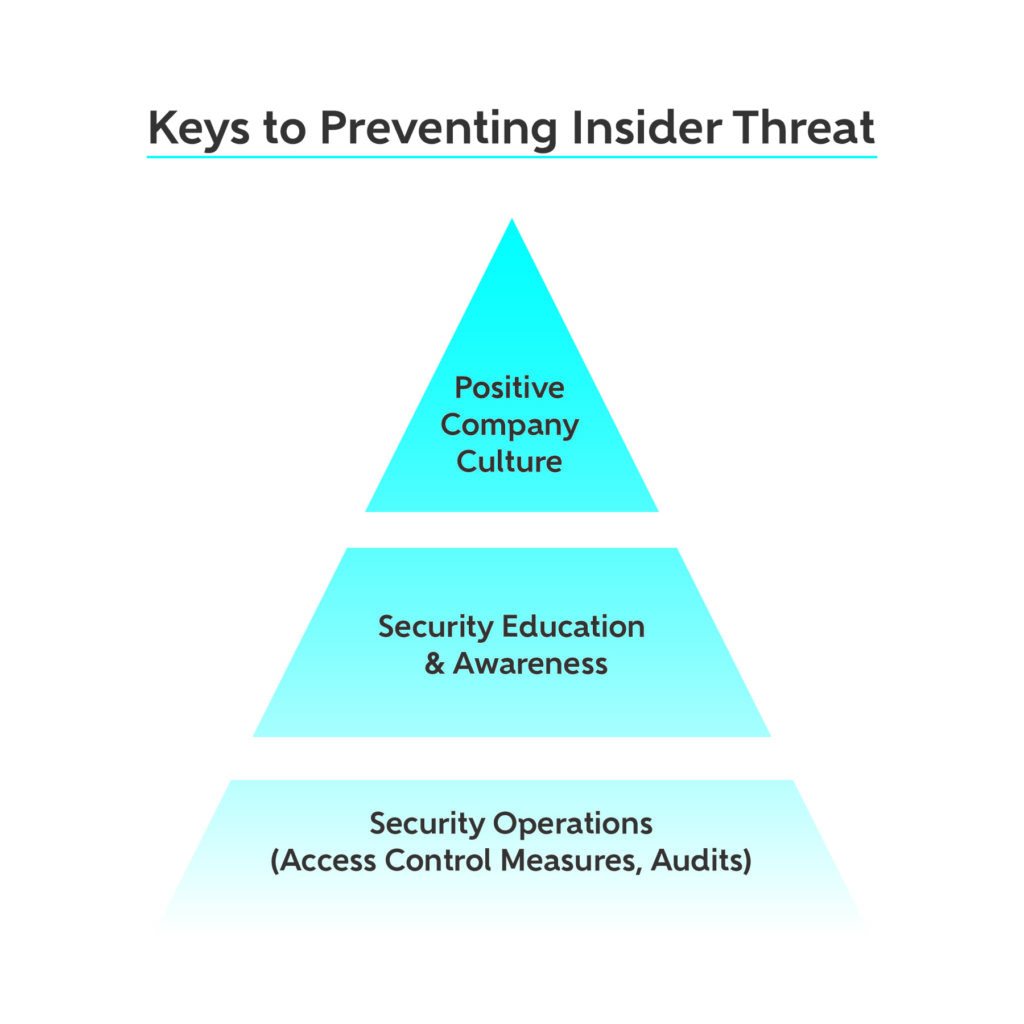
Access Control and Least Privilege: Implementing strong access controls and adhering to the principle of least privilege ensures that users only have access to the resources they need to perform their jobs. This reduces the potential damage that can be caused by a compromised or malicious insider.
Security Awareness Training: Regular security awareness training can help employees understand the risks associated with insider threats and how to identify and report suspicious activity. Training should cover topics such as phishing awareness, password security, and data handling best practices.
Background Checks and Vetting: Conducting thorough background checks and vetting procedures during the hiring process can help identify potential risks before they become a problem. This is especially important for positions that involve access to sensitive data or critical systems.
Incident Response Plan: Having a well-defined incident response plan in place is essential for responding effectively to insider threat incidents. The plan should outline the steps to be taken to contain the damage, investigate the incident, and remediate the vulnerabilities.
Employee Monitoring: Depending on the context, ethical and legal considerations must be reviewed prior implementation, Employee monitoring can be part of the solution in the case that monitoring is done in transparency to the employees, while respecting privacy and following internal policies.
The Human Element: Cultivating a Security-Conscious Culture
While technology plays a crucial role in mitigating insider threats, it's equally important to cultivate a security-conscious culture within the organization. This involves creating an environment where employees feel empowered to report suspicious activity without fear of reprisal, and where security is seen as everyone's responsibility.
Fostering open communication and collaboration between security teams and employees can help break down silos and improve threat detection. Encourage employees to ask questions and voice concerns about security issues.
Furthermore, recognize and reward employees who demonstrate good security practices. This can help reinforce positive behaviors and create a culture of security awareness.
Regular communication from upper management on the importance of security helps foster a secure culture. This will trickle down through the organization.
The Future of Insider Threat Management
As technology evolves and the threat landscape becomes more complex, insider threat management strategies must adapt to stay ahead of the curve. Artificial intelligence (AI) and machine learning (ML) are playing an increasingly important role in detecting and preventing insider threats.
AI-powered solutions can analyze vast amounts of data to identify subtle patterns and anomalies that might be missed by human analysts. This can help organizations detect insider threats earlier and respond more effectively.
However, it's important to remember that AI and ML are tools, not silver bullets. They require careful configuration and ongoing monitoring to ensure they are effective and accurate. And of course, the human element remains paramount.
The question "Which of the following is true about insider threats?" may not have a simple, one-size-fits-all answer, but here’s one: A proactive, multi-faceted approach, combining technology, policies, and a strong security culture, is essential for mitigating the risks posed by insider threats and protecting an organization's valuable assets.
By acknowledging the multifaceted nature of the problem and adopting a holistic approach to security, organizations can transform potential vulnerabilities into strengths, fostering a resilient and secure environment where innovation can thrive.