How Do You Transfer Crypto To Cold Storage

The specter of exchange hacks and online scams looms large in the cryptocurrency world, pushing investors to seek refuge in more secure storage solutions. As digital assets gain mainstream acceptance, the need to safeguard holdings from theft has never been more pressing. Cold storage, often touted as the gold standard for crypto security, offers a compelling solution, but understanding the process is paramount to avoiding costly errors.
This article delves into the intricacies of transferring cryptocurrency to cold storage, providing a step-by-step guide and highlighting crucial considerations. It aims to equip both novice and experienced crypto holders with the knowledge necessary to secure their digital assets effectively. The focus will be on practical implementation, common pitfalls, and best practices for a safe and successful transfer.
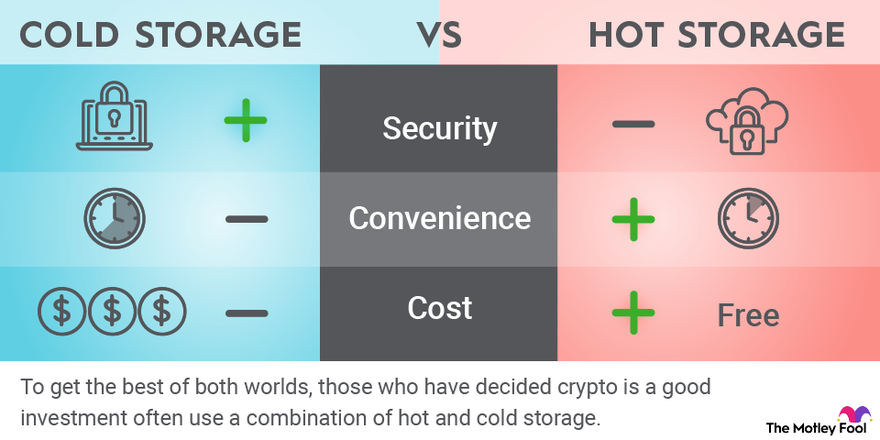
Understanding Cold Storage Options
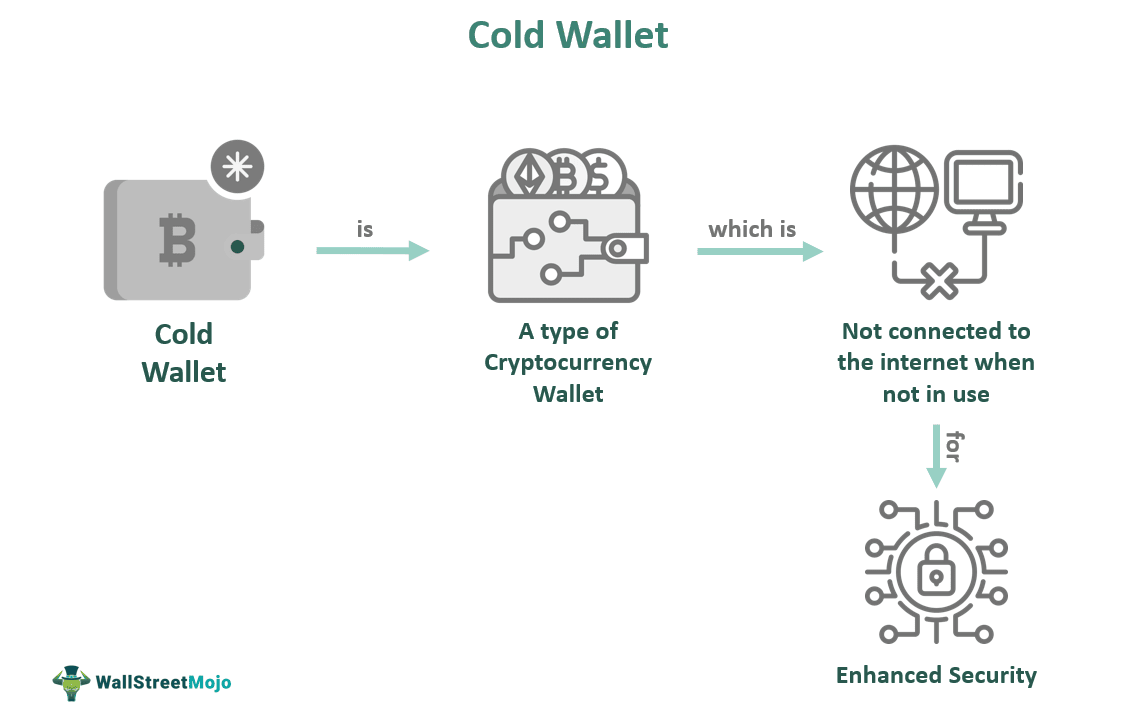
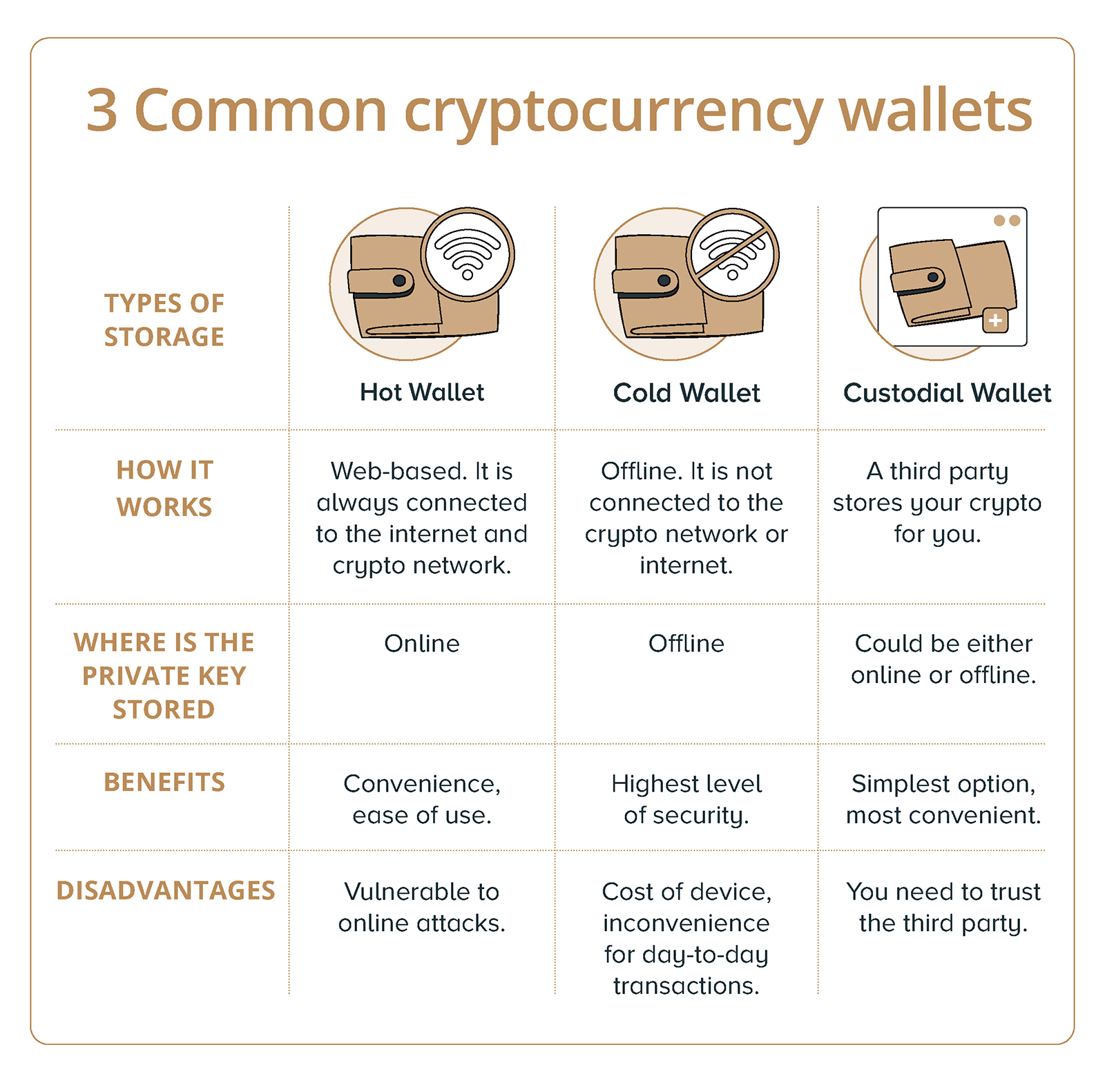
Cold storage refers to storing cryptocurrency offline, rendering it inaccessible to hackers targeting online wallets and exchanges. This generally involves keeping your private keys – the digital signatures that allow you to access and manage your crypto – on a device not connected to the internet. The most common methods include hardware wallets and paper wallets.
Hardware Wallets
Hardware wallets are physical devices, resembling USB drives, designed specifically for storing cryptocurrency private keys. These devices offer a secure environment for generating and storing keys offline, and for signing transactions before broadcasting them to the blockchain. Popular brands include Ledger, Trezor, and Coldcard.
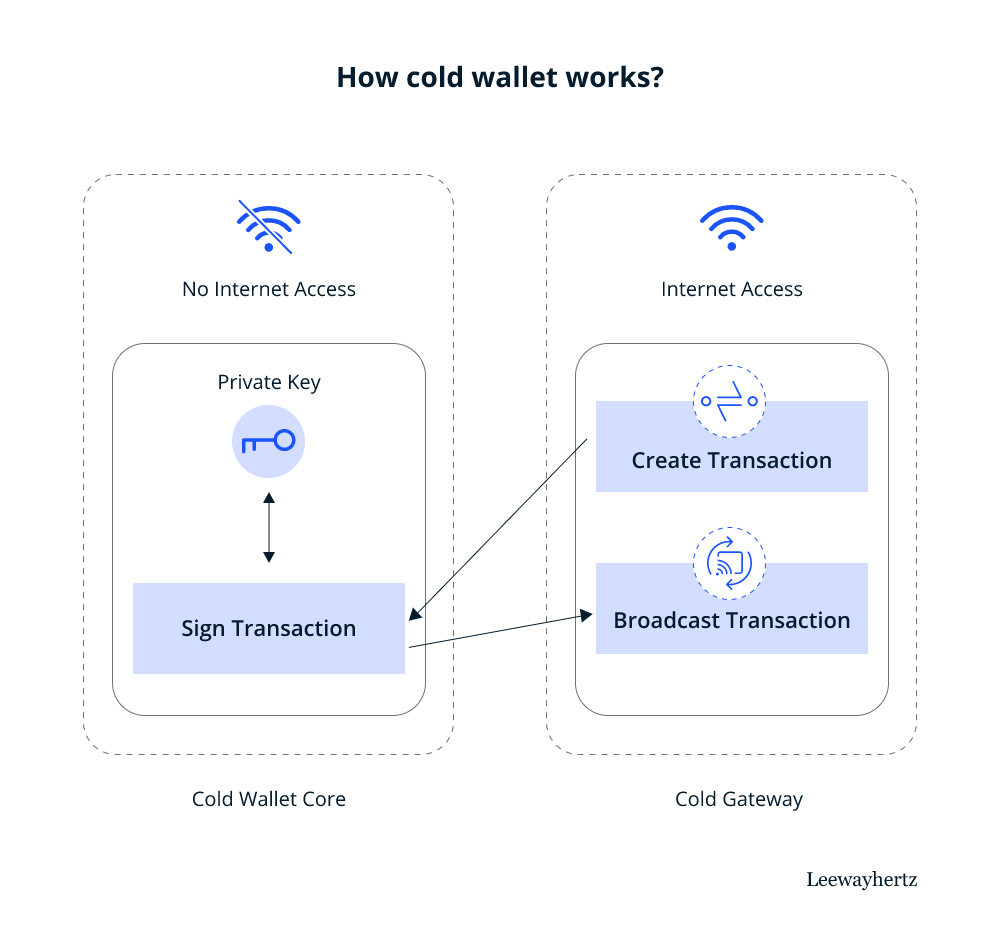
To use a hardware wallet, you typically connect it to a computer via USB. You then use the wallet's interface to manage your crypto holdings and initiate transactions. The private keys remain on the device and never touch the computer, significantly reducing the risk of compromise.
Paper Wallets
A paper wallet involves printing your private and public keys on a piece of paper. This method completely isolates your keys from the internet. However, it requires careful handling and storage to prevent loss, damage, or theft.
Generating a paper wallet typically involves using a website or software that creates the keys offline. You then print the keys and store them in a secure location. To access your crypto, you need to import the private key into a software or online wallet.
The Transfer Process: A Step-by-Step Guide
The process of transferring crypto to cold storage generally involves these steps. First, set up your cold storage wallet. Then, find your cold storage receiving address. Finally, send crypto from your exchange or hot wallet.
Setting Up Your Cold Storage Wallet
Hardware Wallet: Follow the manufacturer's instructions to initialize your hardware wallet. This usually involves setting up a PIN code and writing down a recovery phrase (seed phrase). This recovery phrase is crucial – it's the only way to recover your crypto if you lose or damage your device.
Paper Wallet: Generate your paper wallet using a reputable offline tool. Ensure the software is open-source and verifiable to avoid potential scams. Print the wallet and securely store the paper in a safe, dry place.
Finding Your Cold Storage Receiving Address
Hardware Wallet: Connect your hardware wallet to your computer and open the corresponding wallet application. Navigate to the "Receive" or "Deposit" section and generate a new address. Always verify the address on the hardware wallet's screen to ensure it hasn't been tampered with.
Paper Wallet: Your paper wallet will already contain your public address. This is the address you will use to receive crypto. Double-check the address against the printed version to ensure accuracy.
Sending Crypto from Your Exchange or Hot Wallet
Log in to your cryptocurrency exchange or hot wallet. Navigate to the "Withdraw" or "Send" section. Carefully paste your cold storage receiving address into the destination address field.
Double-check the address for any errors – even a single incorrect character can result in the loss of your funds. Specify the amount of crypto you wish to transfer and initiate the withdrawal. Confirm the transaction and follow any security prompts from your exchange or hot wallet.
Important Considerations and Best Practices
Several precautions are essential to ensuring a secure and successful transfer. One should always verify the address. One should also test with a small amount first. Also, secure your recovery phrase.
Address Verification
Before sending any significant amount of crypto, always verify the receiving address. Compare the address displayed on your exchange or hot wallet with the address displayed on your hardware wallet or printed on your paper wallet. Consider sending a small test transaction first to confirm the address is correct.
Test Transactions
Sending a small test transaction is a crucial step in mitigating risk. This allows you to confirm that the address is correct and that the transfer is successful. Once you've verified the test transaction, you can proceed with transferring the remaining funds.
Recovery Phrase Security
Your recovery phrase is the key to accessing your crypto in case of device loss or damage. Store it in a safe, secure location, separate from your hardware wallet or paper wallet. Consider using a metal backup for long-term storage. Never store your recovery phrase digitally, as this exposes it to online threats.
Potential Risks and Mitigation Strategies
While cold storage offers enhanced security, it's not without its risks. These include physical loss or damage, human error, and supply chain attacks. Mitigating these risks requires careful planning and execution.
Physical Loss or Damage
Hardware wallets can be lost or damaged, and paper wallets can be destroyed by fire or water. To mitigate this risk, store your cold storage devices and recovery phrases in secure, fireproof, and waterproof locations. Consider using multiple backups stored in different locations.
Human Error
Incorrectly entering addresses or losing recovery phrases are common mistakes that can lead to the loss of funds. Pay meticulous attention to detail when entering addresses and storing recovery phrases. Consider using a password manager to securely store your recovery phrase, but only if you trust the password manager's security.
Supply Chain Attacks
There have been instances of compromised hardware wallets that were pre-loaded with malicious software. To mitigate this risk, purchase hardware wallets directly from the manufacturer or authorized resellers. Verify the authenticity of the device upon arrival and avoid purchasing used or tampered-with devices. Always ensure you are buying from reputable sources.
The Future of Crypto Security
As the cryptocurrency landscape evolves, so too will the methods for securing digital assets. Multi-signature wallets, which require multiple private keys to authorize a transaction, are gaining popularity. Advanced cryptographic techniques are also being explored to enhance the security of cold storage solutions.
The transition to more sophisticated security measures underscores the ongoing importance of protecting digital assets. While cold storage remains a cornerstone of crypto security, staying informed about emerging threats and adopting best practices is crucial for safeguarding your investments in the long term. The future of crypto security lies in a layered approach that combines technical innovation with user education and responsible practices.